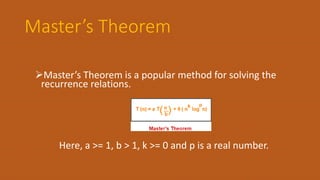
The document discusses the divide and conquer algorithm design paradigm. It begins by defining divide and conquer as recursively breaking down a problem into smaller sub-problems, solving the sub-problems, and then combining the solutions to solve the original problem. Some examples of problems that can be solved using divide and conquer include binary search, quicksort, merge sort, and the fast Fourier transform algorithm. The document then discusses control abstraction, efficiency analysis, and uses divide and conquer to provide algorithms for large integer multiplication and merge sort. It concludes by defining the convex hull problem and providing an example input and output.












![2. Divide and Conquer
Using Divide and Conquer, we can multiply two
integers in less time complexity. We divide the
given numbers in two halves. Let the given
numbers be X and Y.
For simplicity let us assume that n is even
The product XY can be written as following.
X = Xl*2n/2 + Xr [Xl and Xr contain leftmost and rightmost n/2 bits of X]
Y = Yl*2n/2 + Yr [Yl and Yr contain leftmost and rightmost n/2 bits of Y]
XY = (Xl*2n/2 + Xr)(Yl*2n/2 + Yr)
= 2n XlYl + 2n/2(XlYr + XrYl) + XrYr](https://image.slidesharecdn.com/unit3-191002094323/85/Divide-and-Conquer-14-320.jpg)
![If we take a look at the above formula, there are four
multiplications of size n/2, so we basically divided the
problem of size n into four sub-problems of size n/2.
But that doesn’t help because solution of recurrence
T(n) = 4T(n/2) + O(n) is O(n^2). The tricky part of this
algorithm is to change the middle two terms to some
other form so that only one extra multiplication would
be sufficient. The following is tricky expression for
middle two terms.
So the final value of XY becomes :
XY = 2n XlYl + 2n/2 * [(Xl + Xr)(Yl + Yr) - XlYl - XrYr] + XrYr](https://image.slidesharecdn.com/unit3-191002094323/85/Divide-and-Conquer-15-320.jpg)
![Merge Sort
The merge() function is used for merging two
halves. The merge(arr, l, m, r) is key process that
assumes that arr[l..m] and arr[m+1..r] are sorted
and merges the two sorted sub-arrays into one.
MergeSort(arr[], l, r) If r > l
1. Find the middle point to divide the array into two
halves: middle m = (l+r)/2
2. Call mergeSort for first half: Call mergeSort(arr, l, m)
3. Call mergeSort for second half: Call mergeSort(arr, m+1,
r)
4. Merge the two halves sorted in step 2 and 3:
Call merge(arr, l, m, r)](https://image.slidesharecdn.com/unit3-191002094323/85/Divide-and-Conquer-16-320.jpg)
![Convex Hull
A convex hull is the smallest convex polygon containing all
the given points.
Input is an array of points specified by their x and y
coordinates. The output is the convex hull of this set of
points.
Input : points[] = {(0, 0), (0, 4), (-4, 0), (5, 0), (0, -6), (1, 0)};
Output : (-4, 0), (5, 0), (0, -6), (0, 4)](https://image.slidesharecdn.com/unit3-191002094323/85/Divide-and-Conquer-18-320.jpg)
