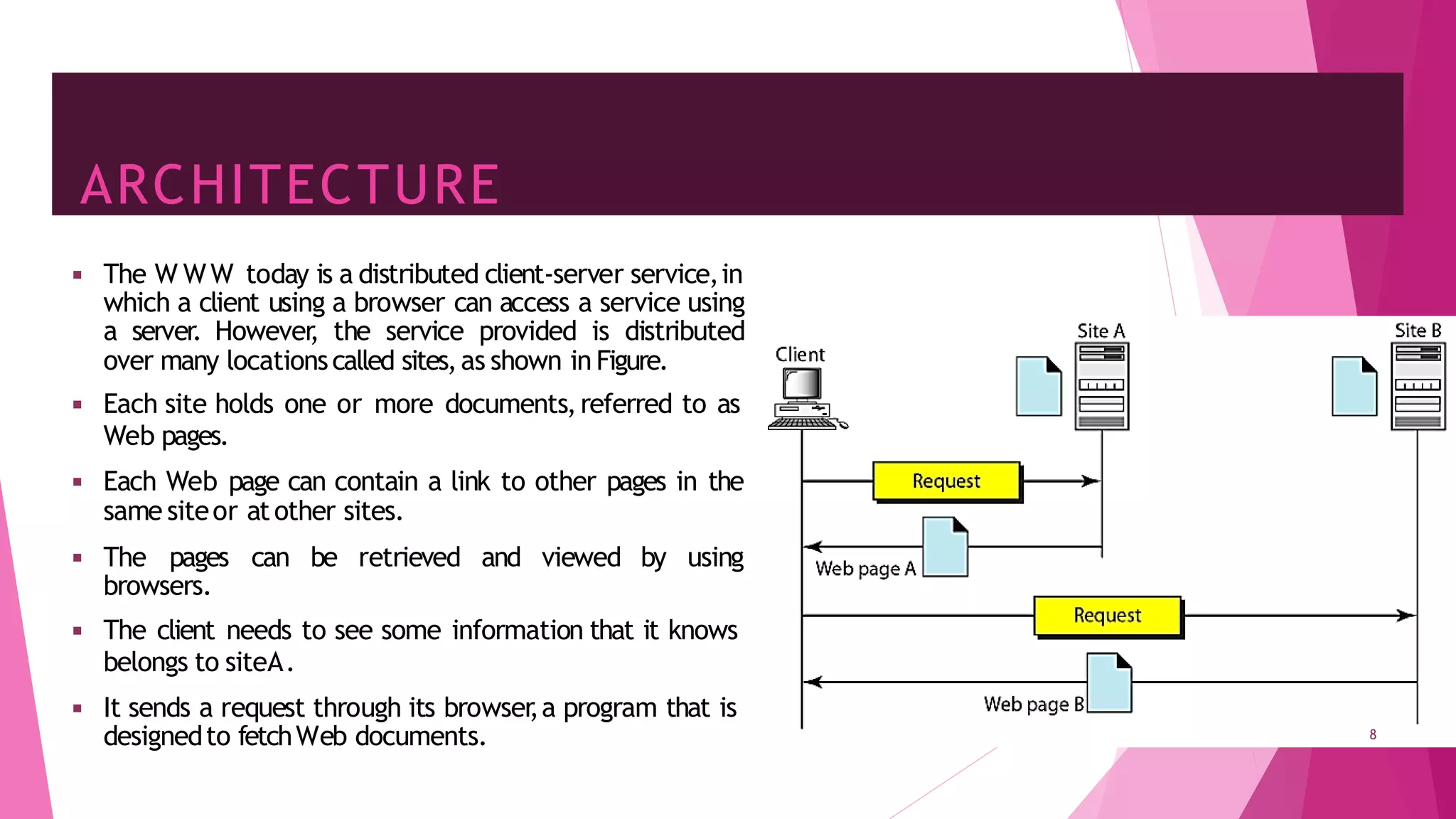
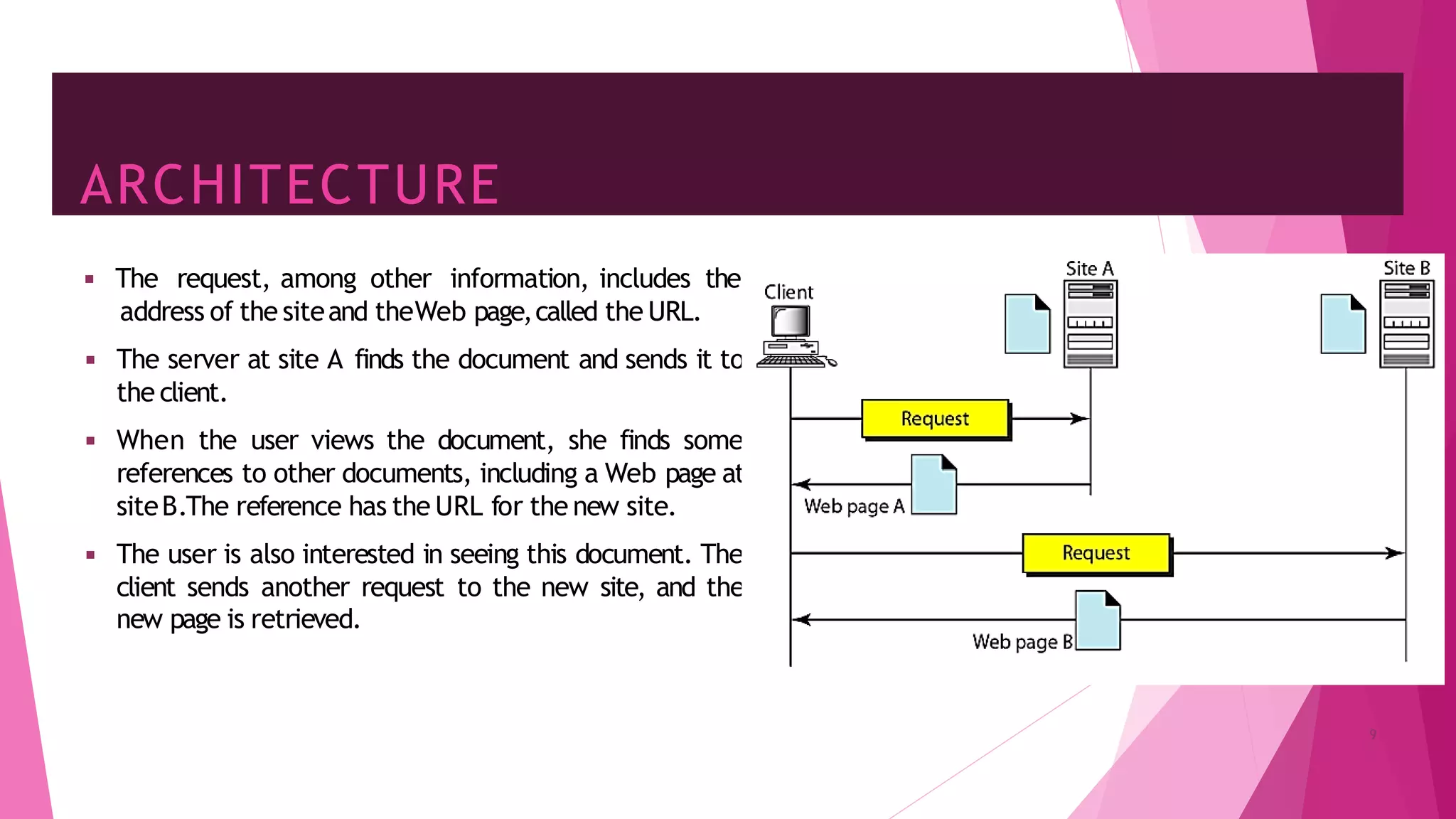
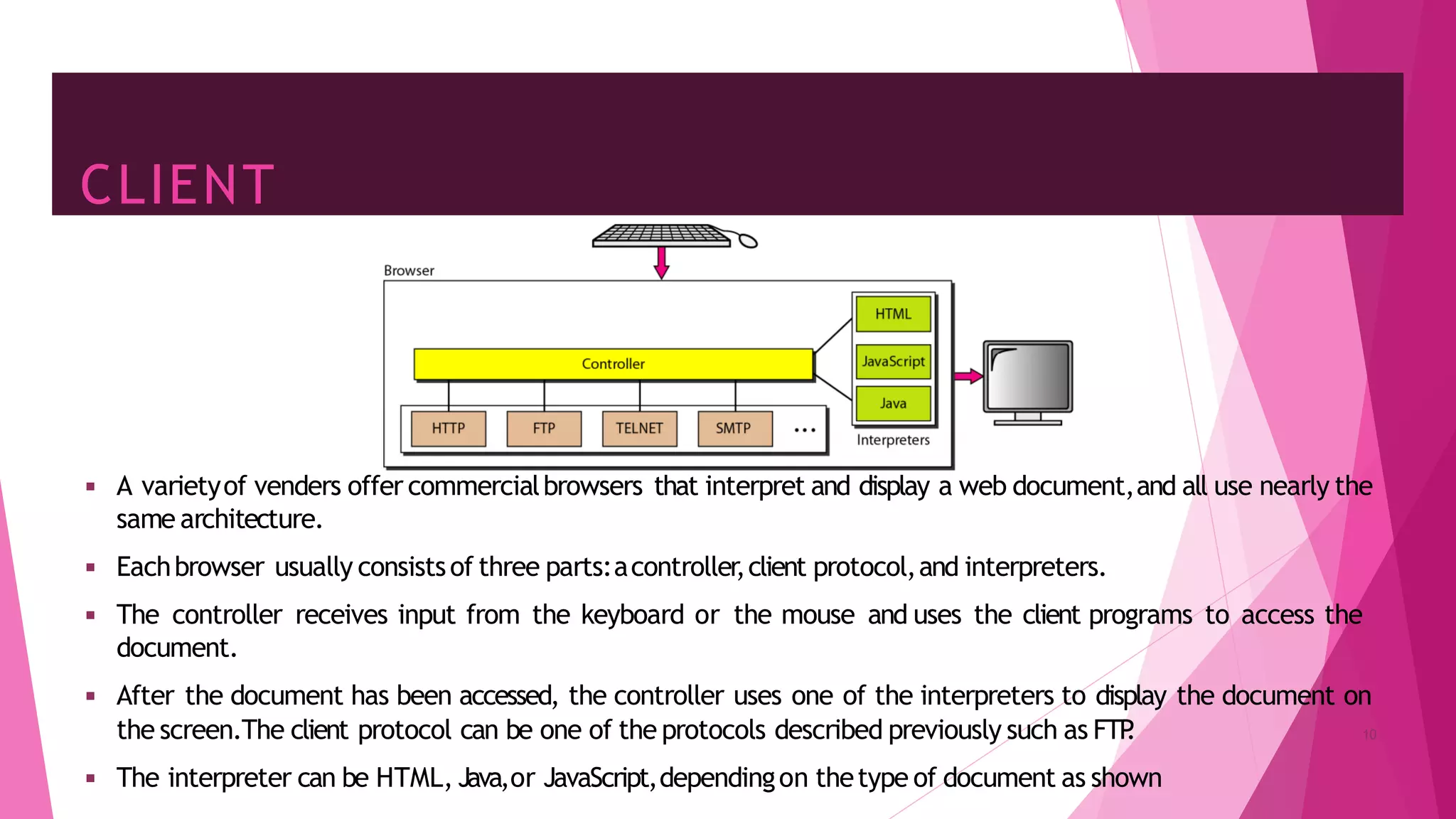
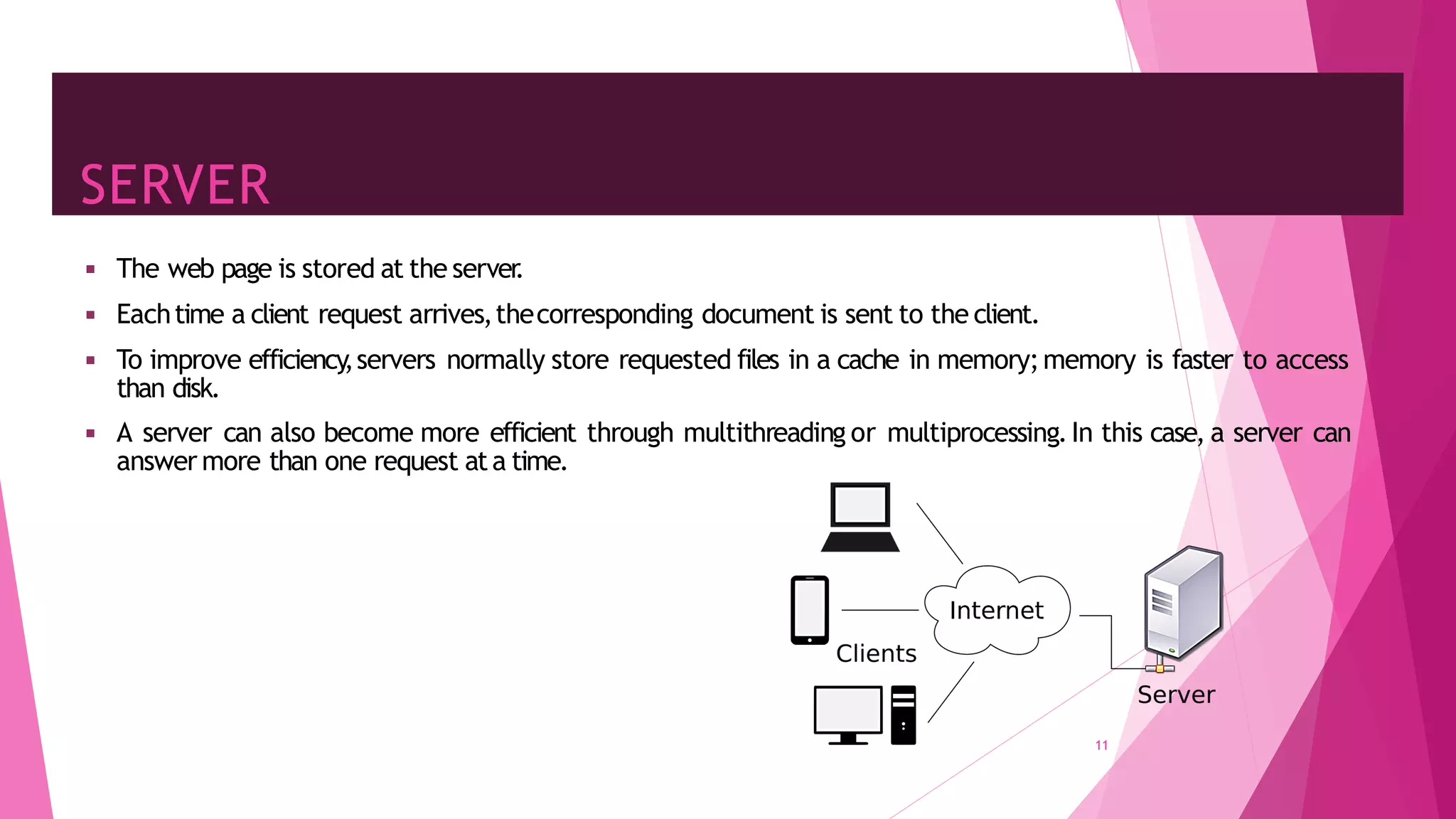
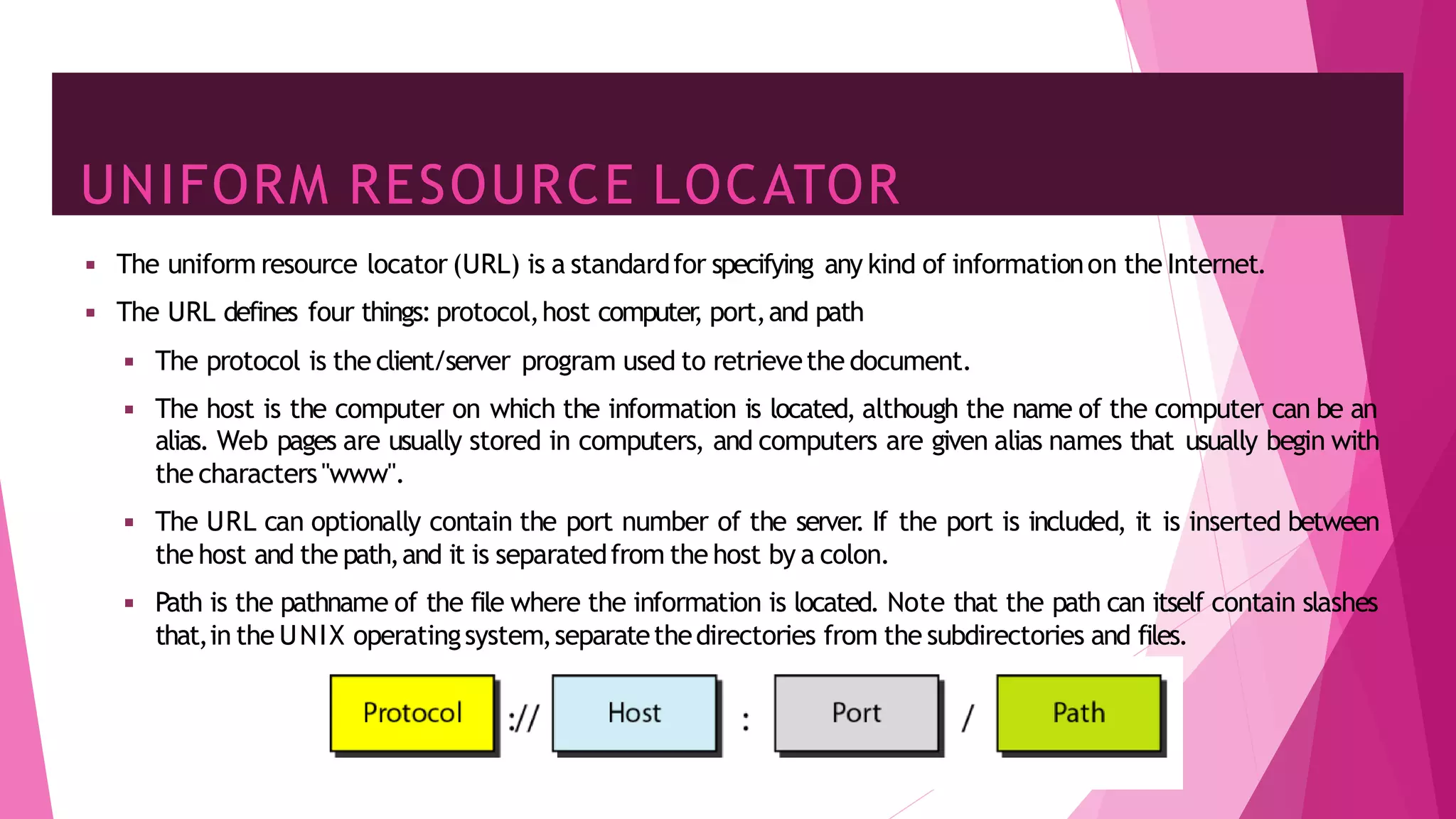
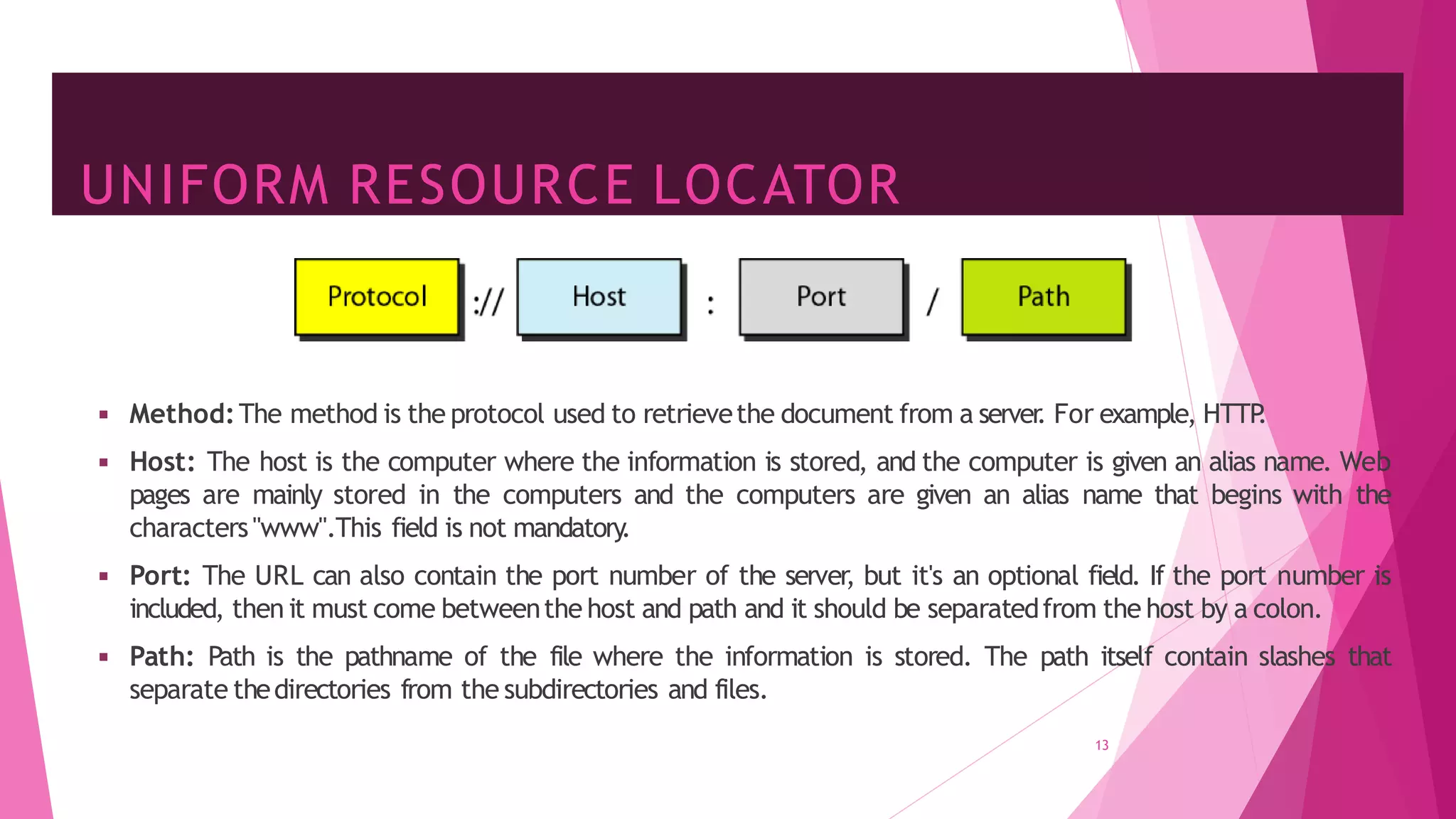
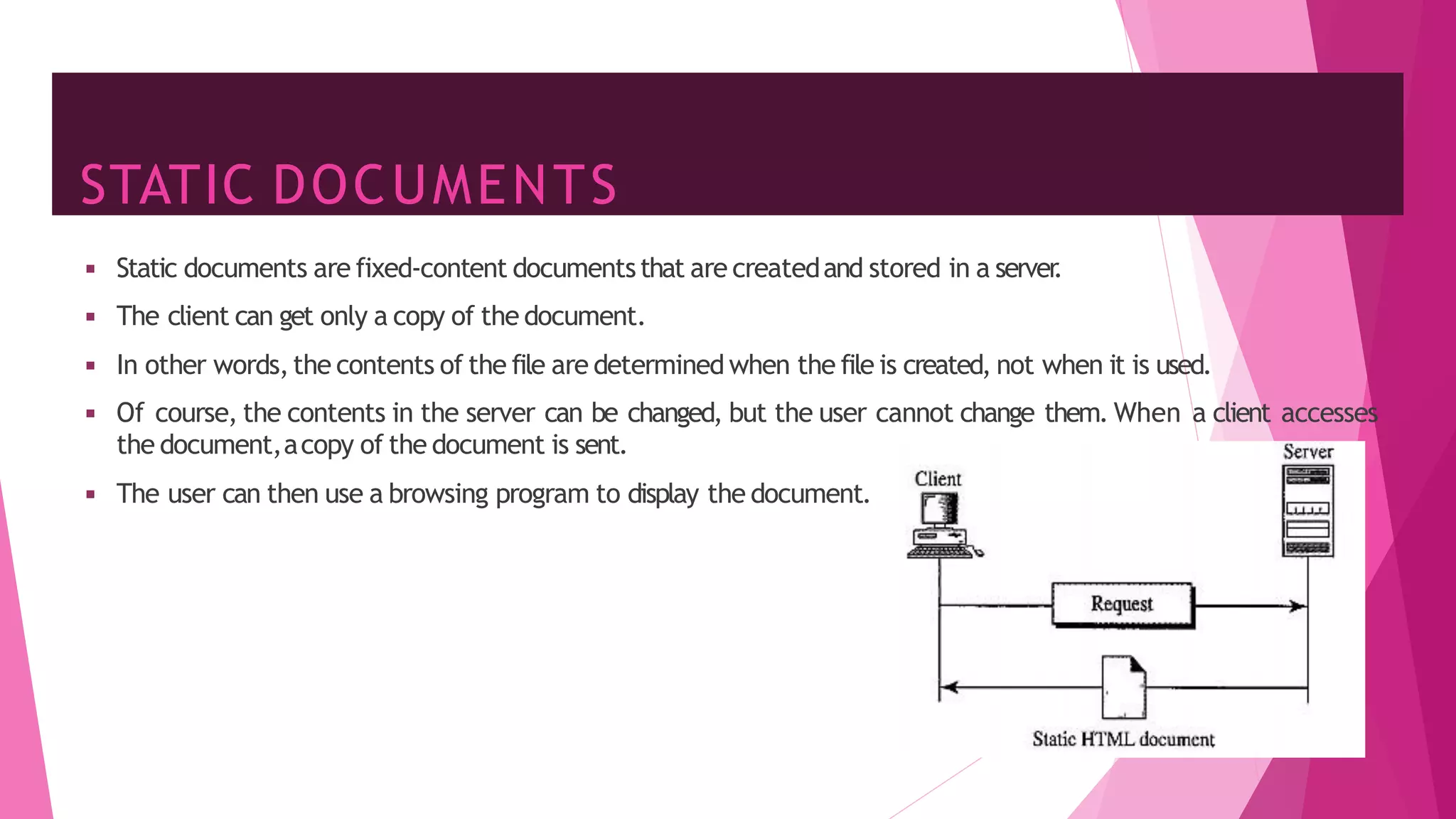
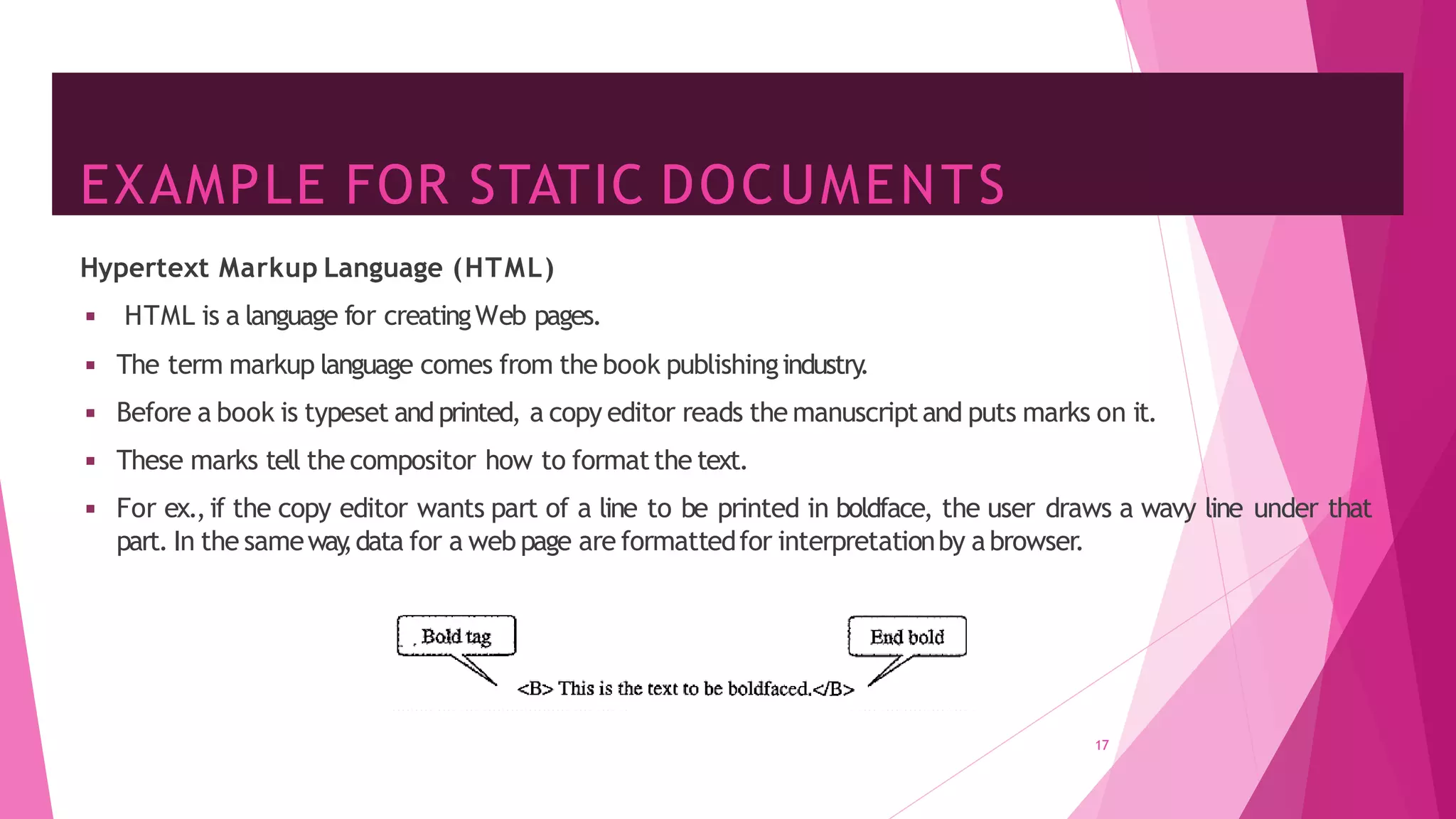
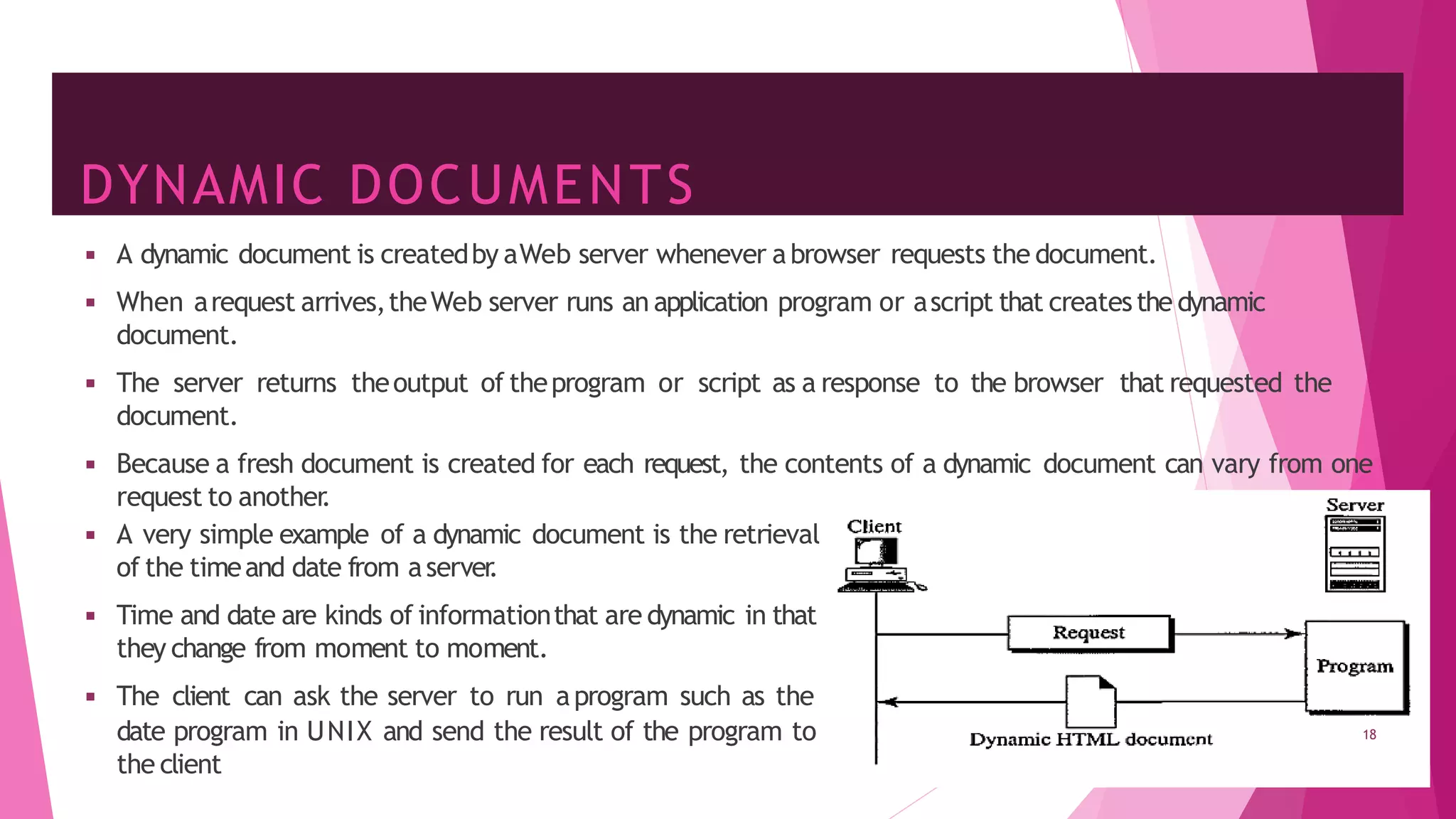
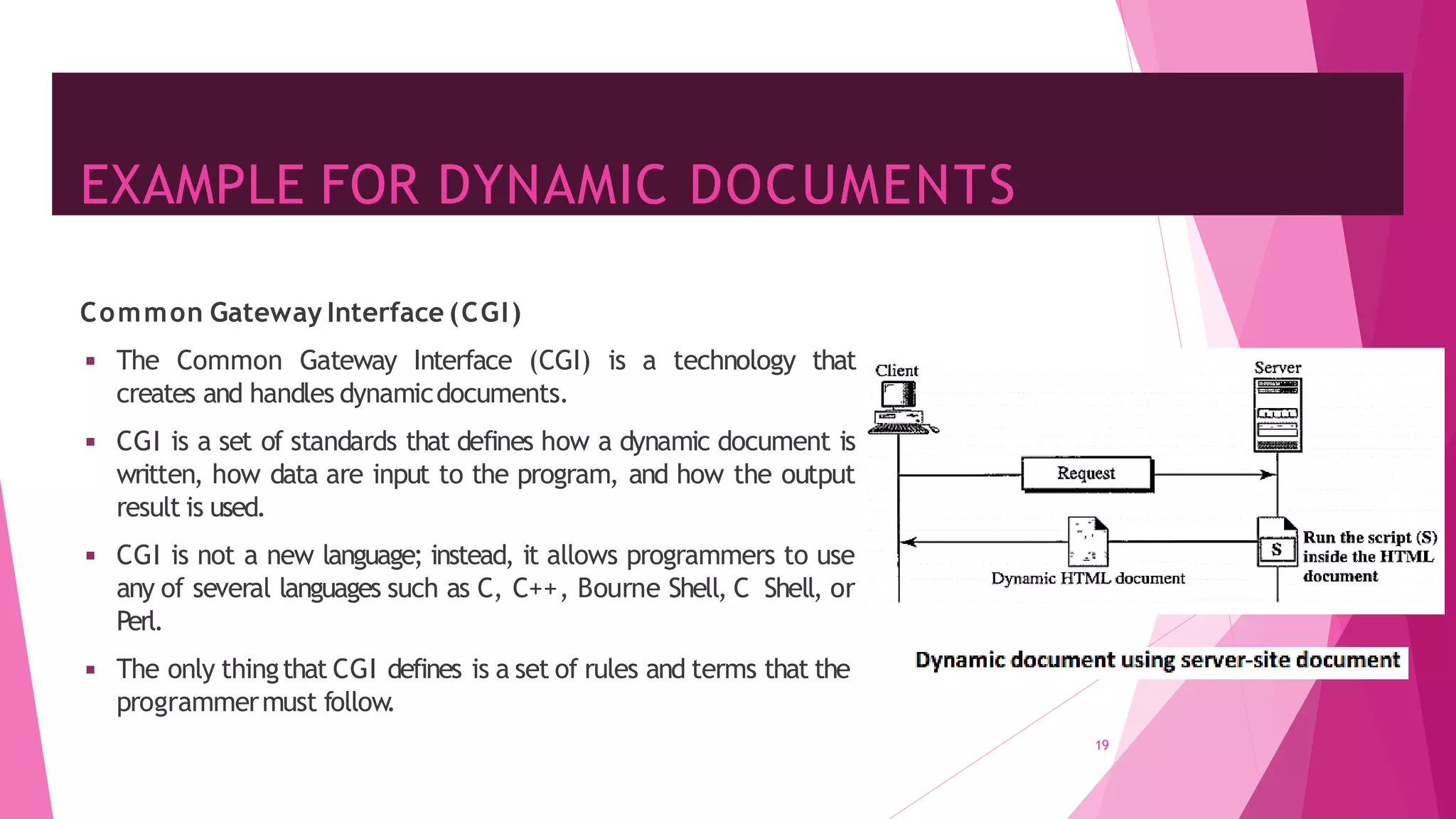
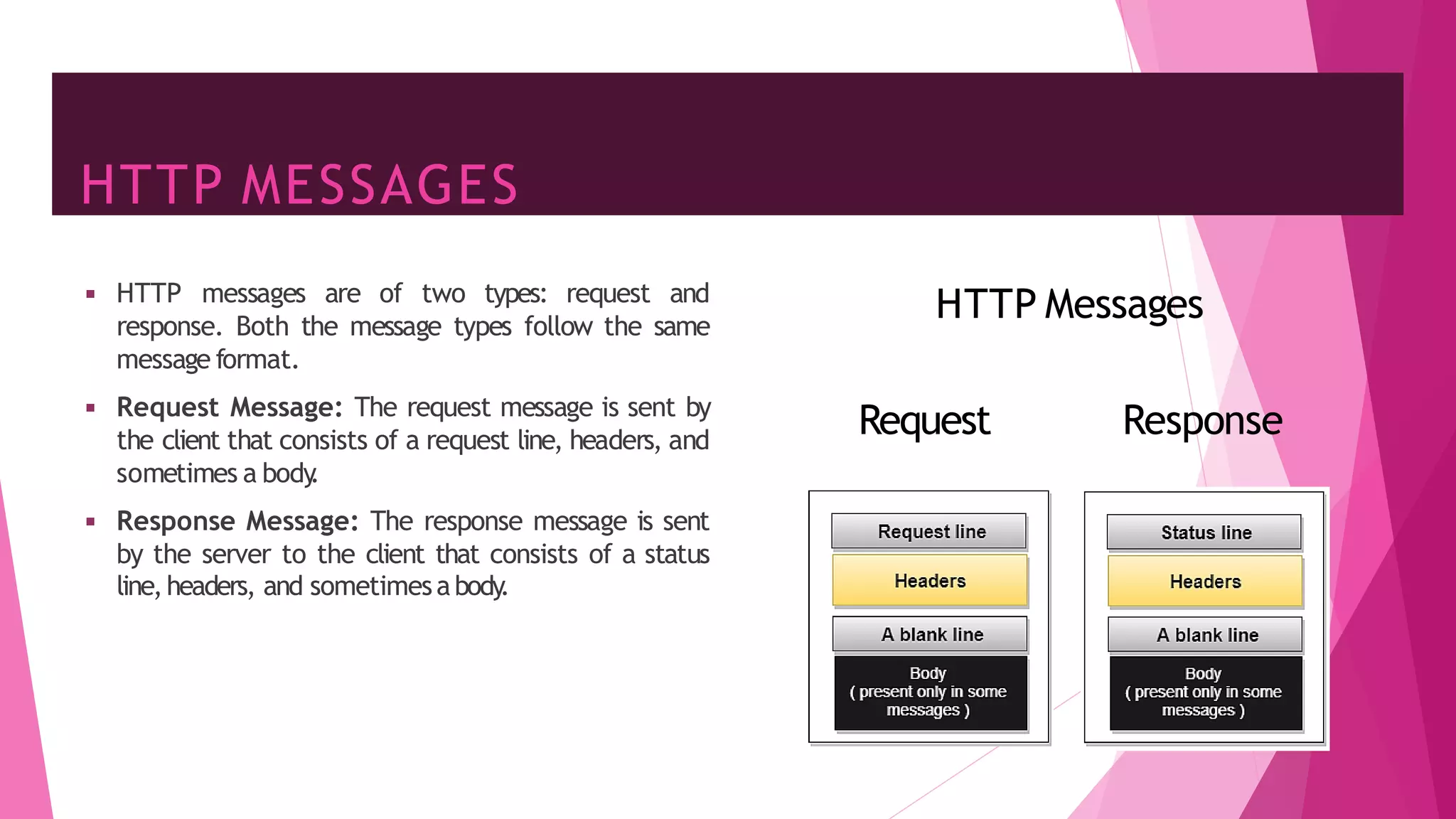
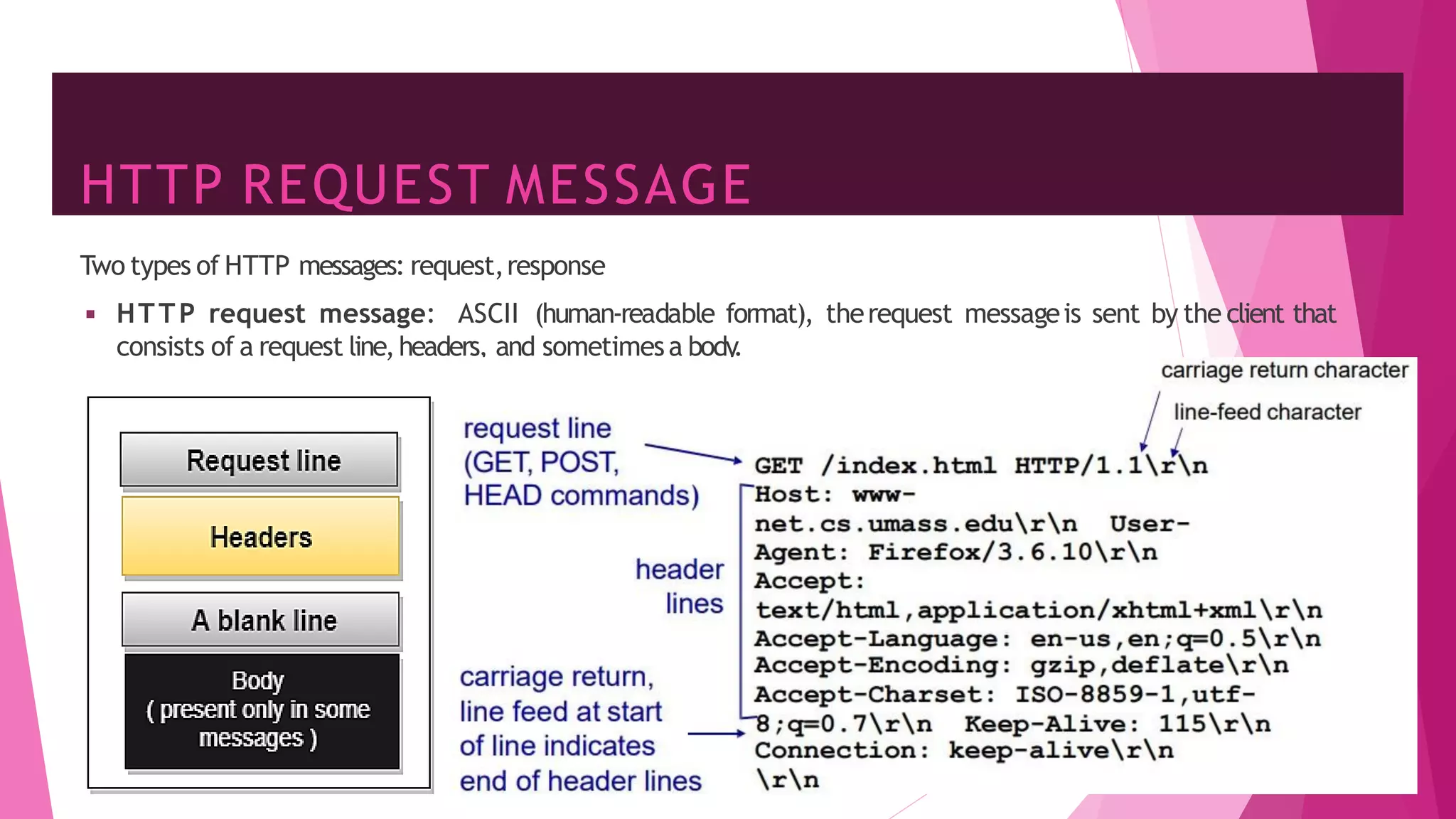
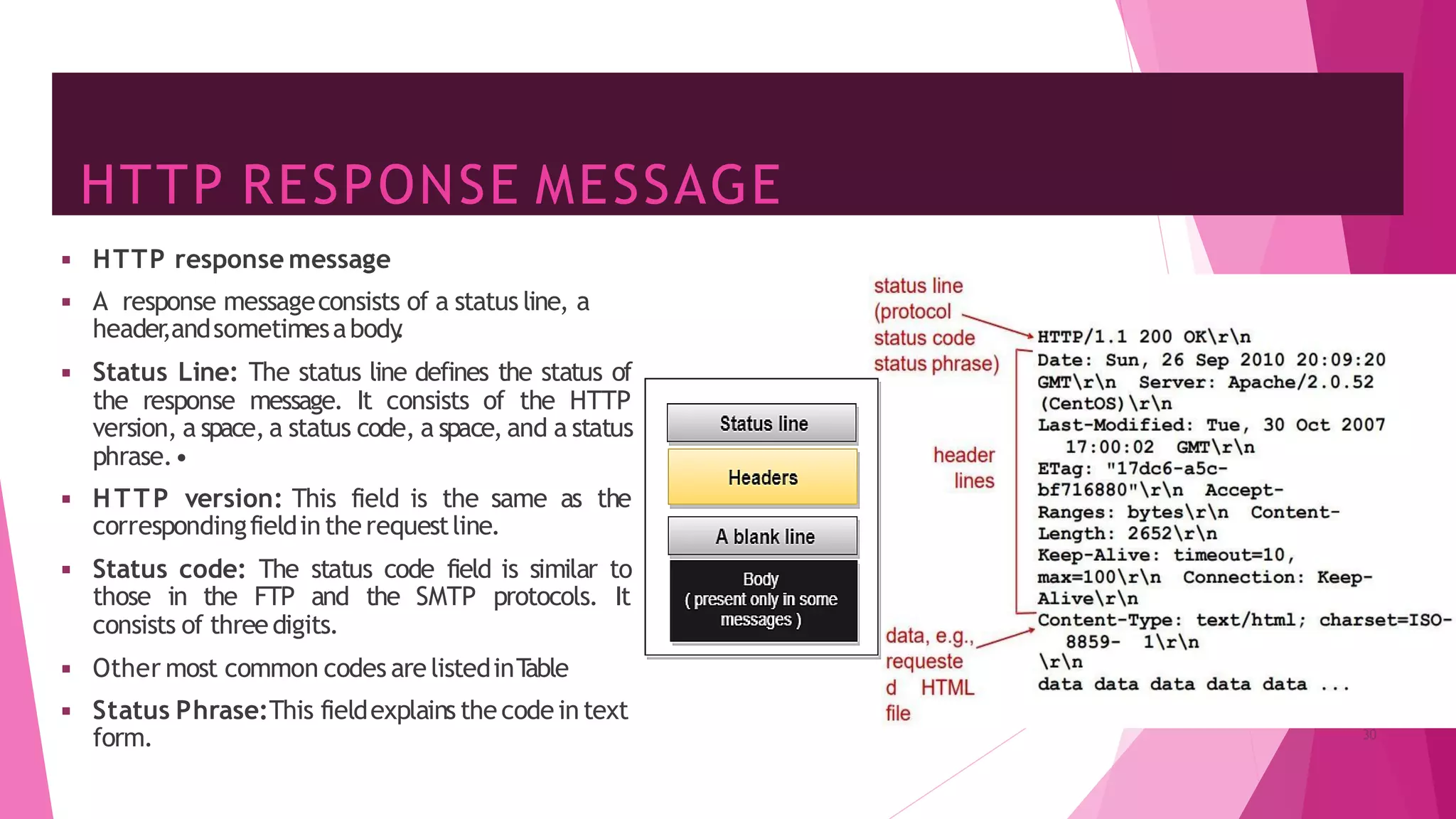
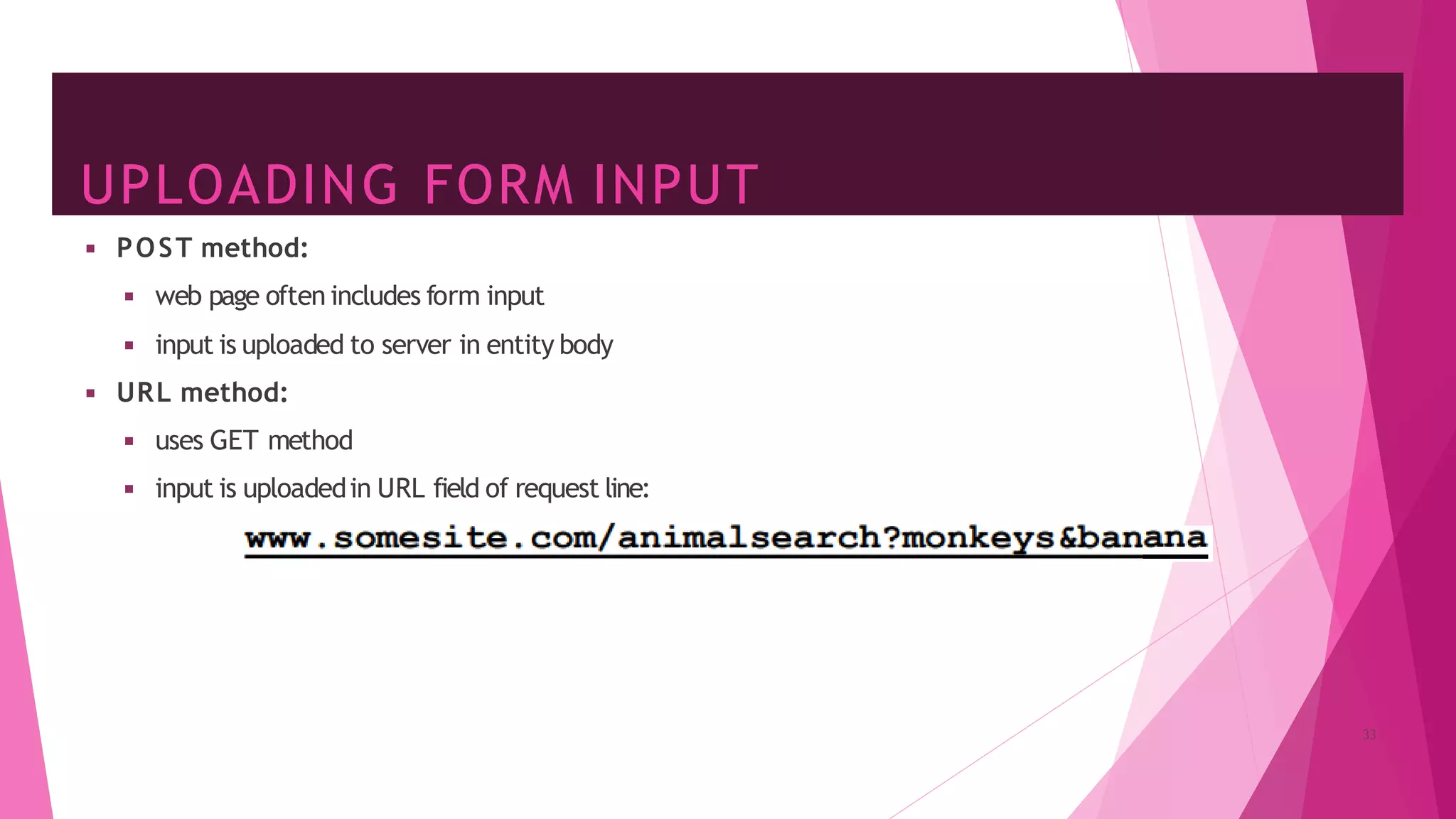
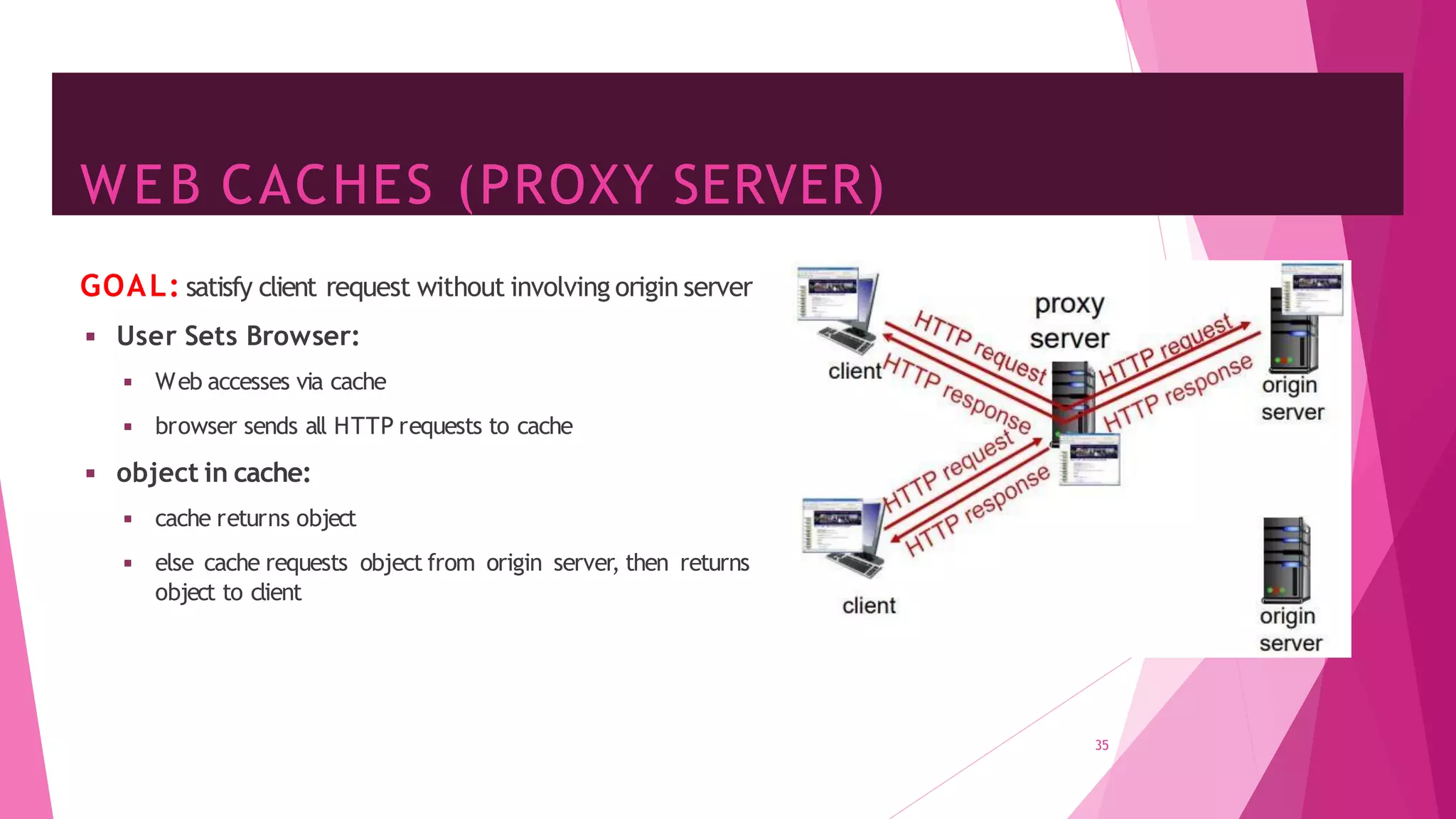
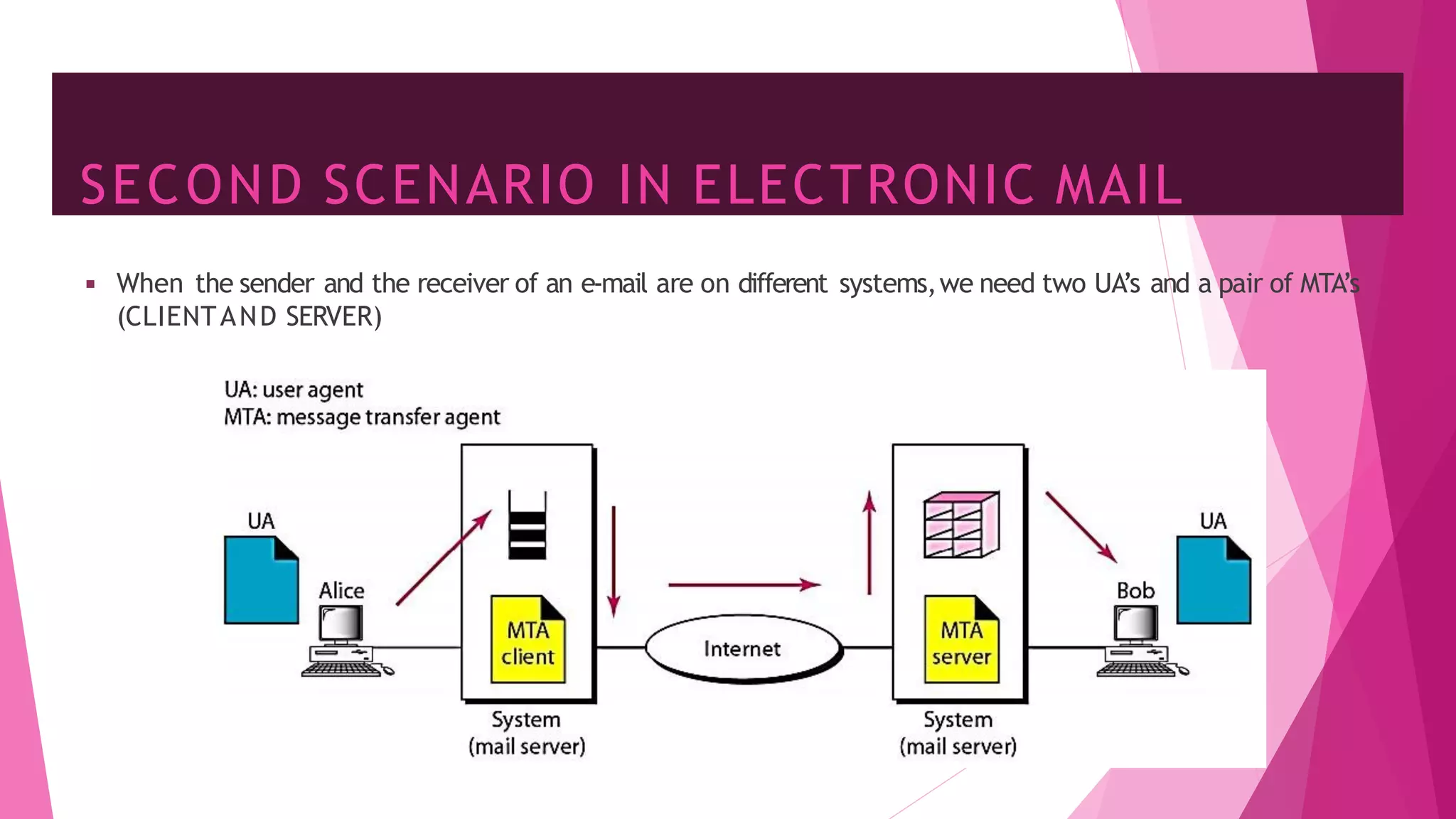
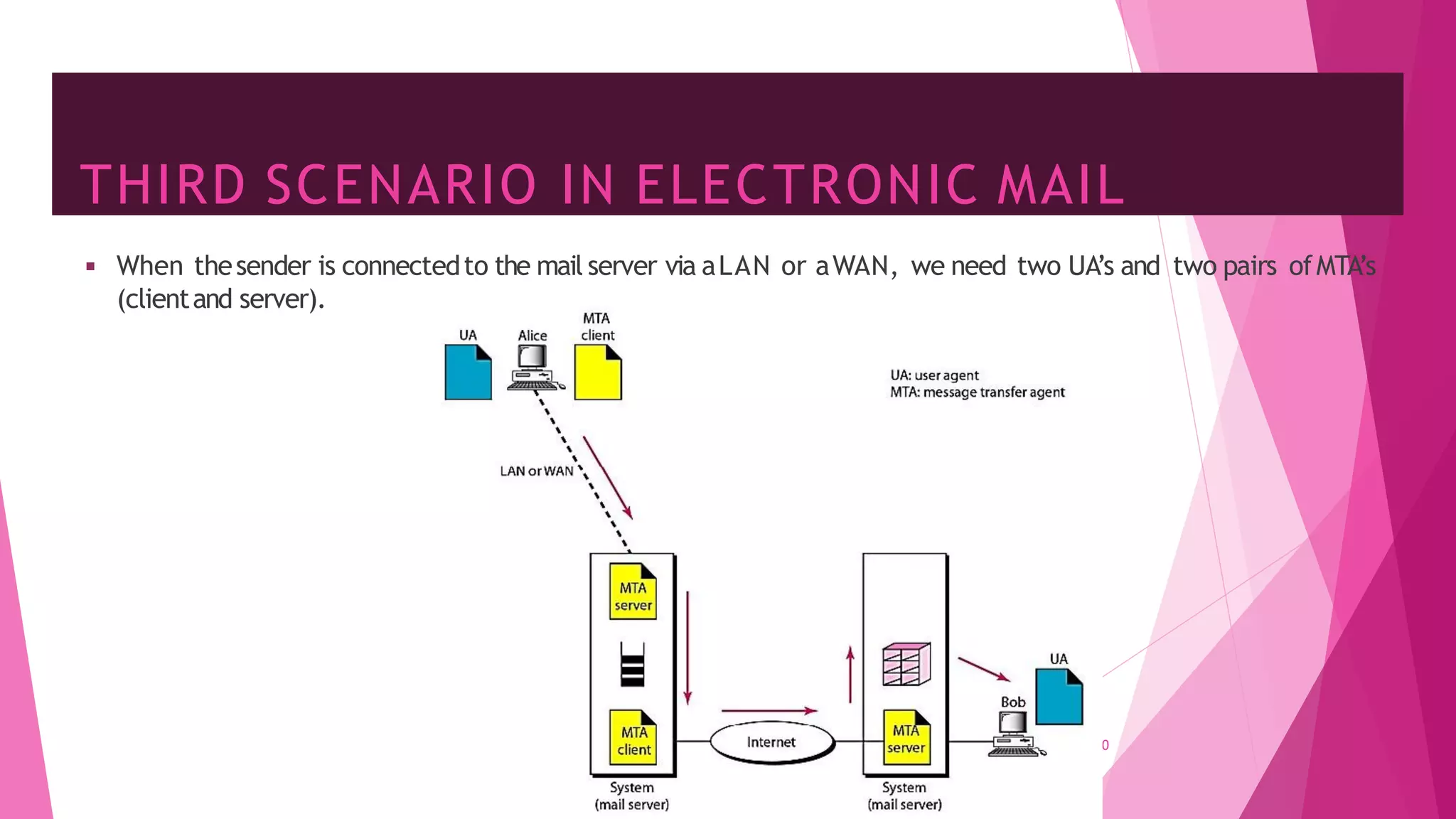
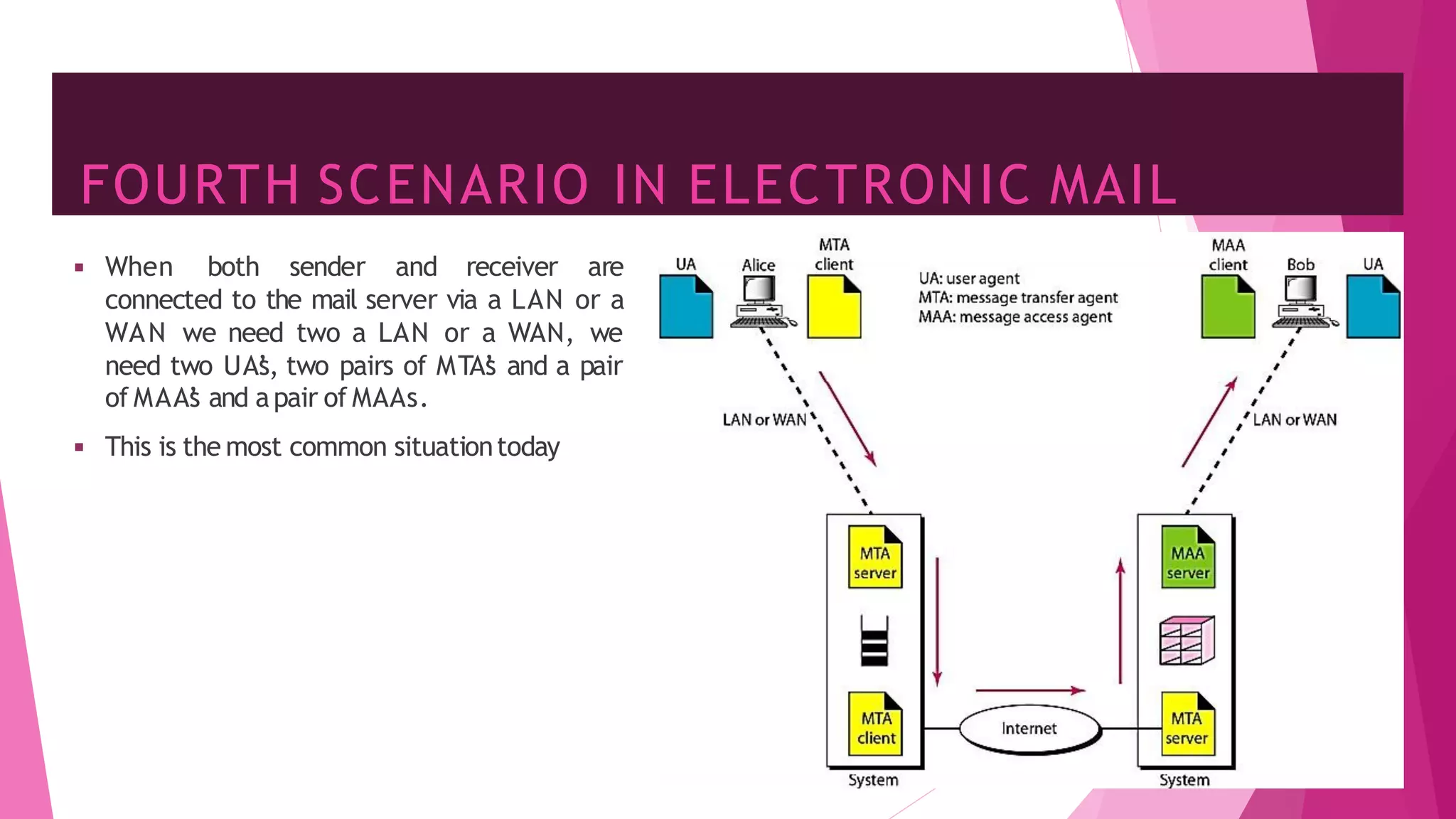
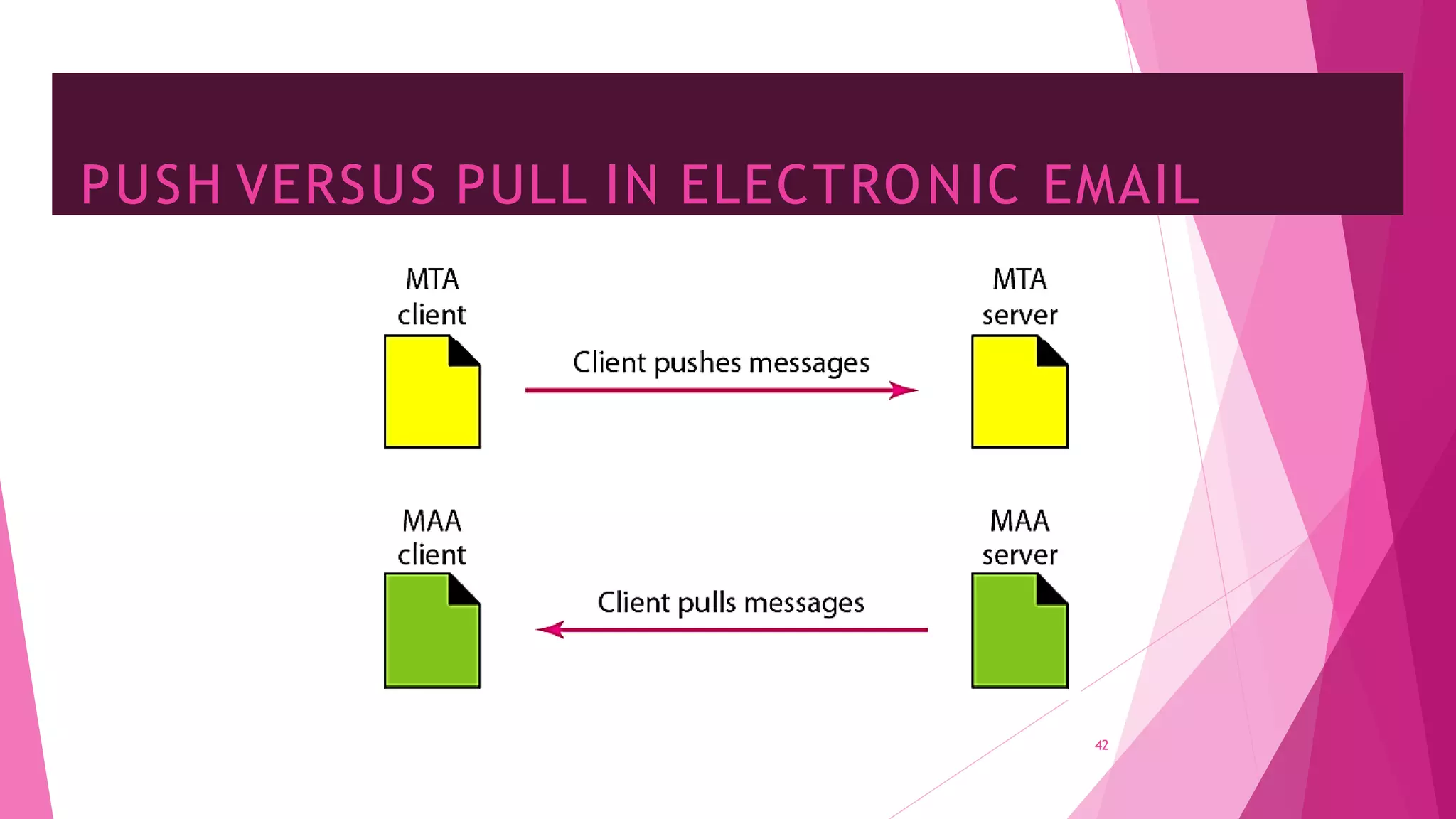
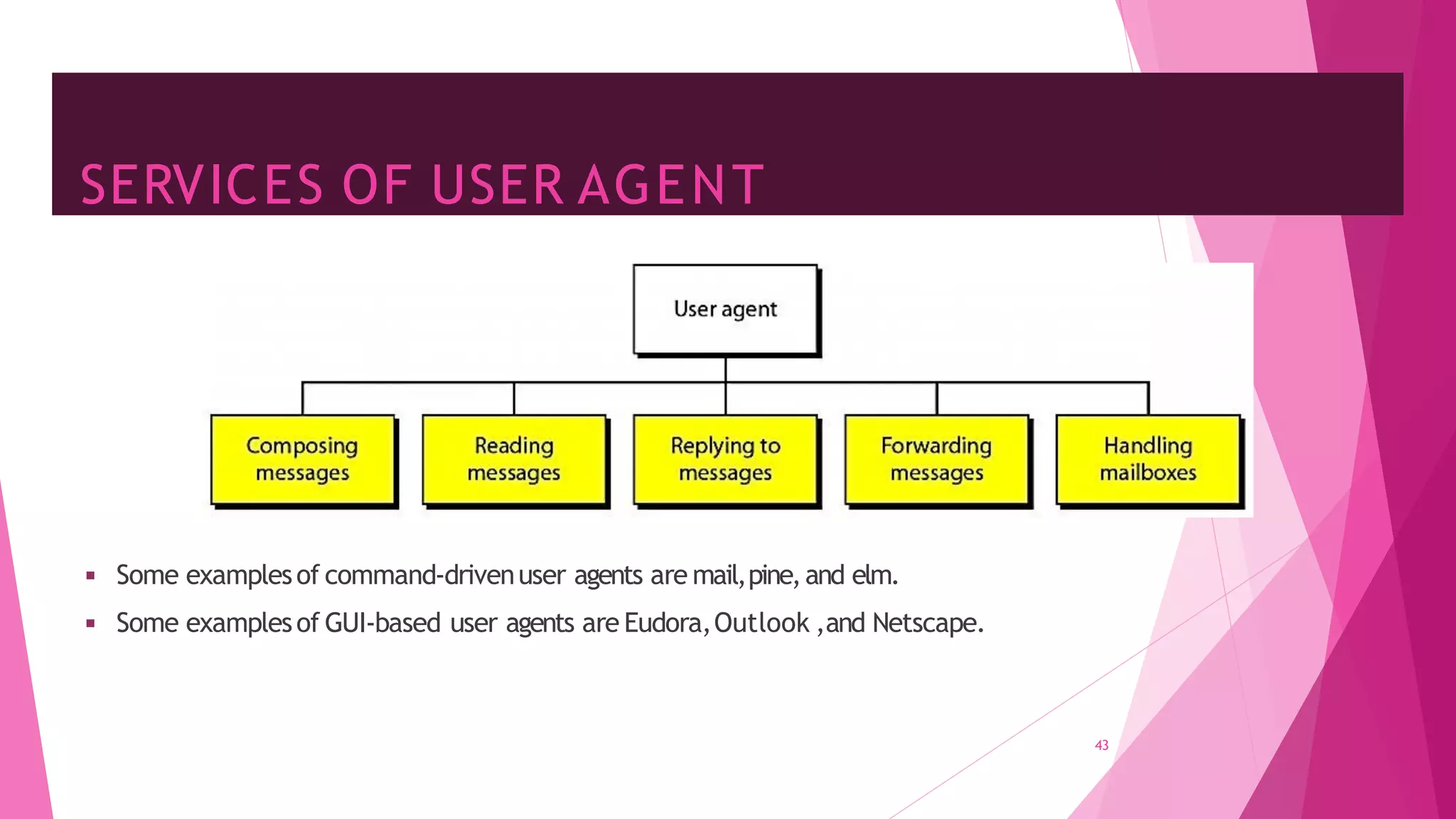
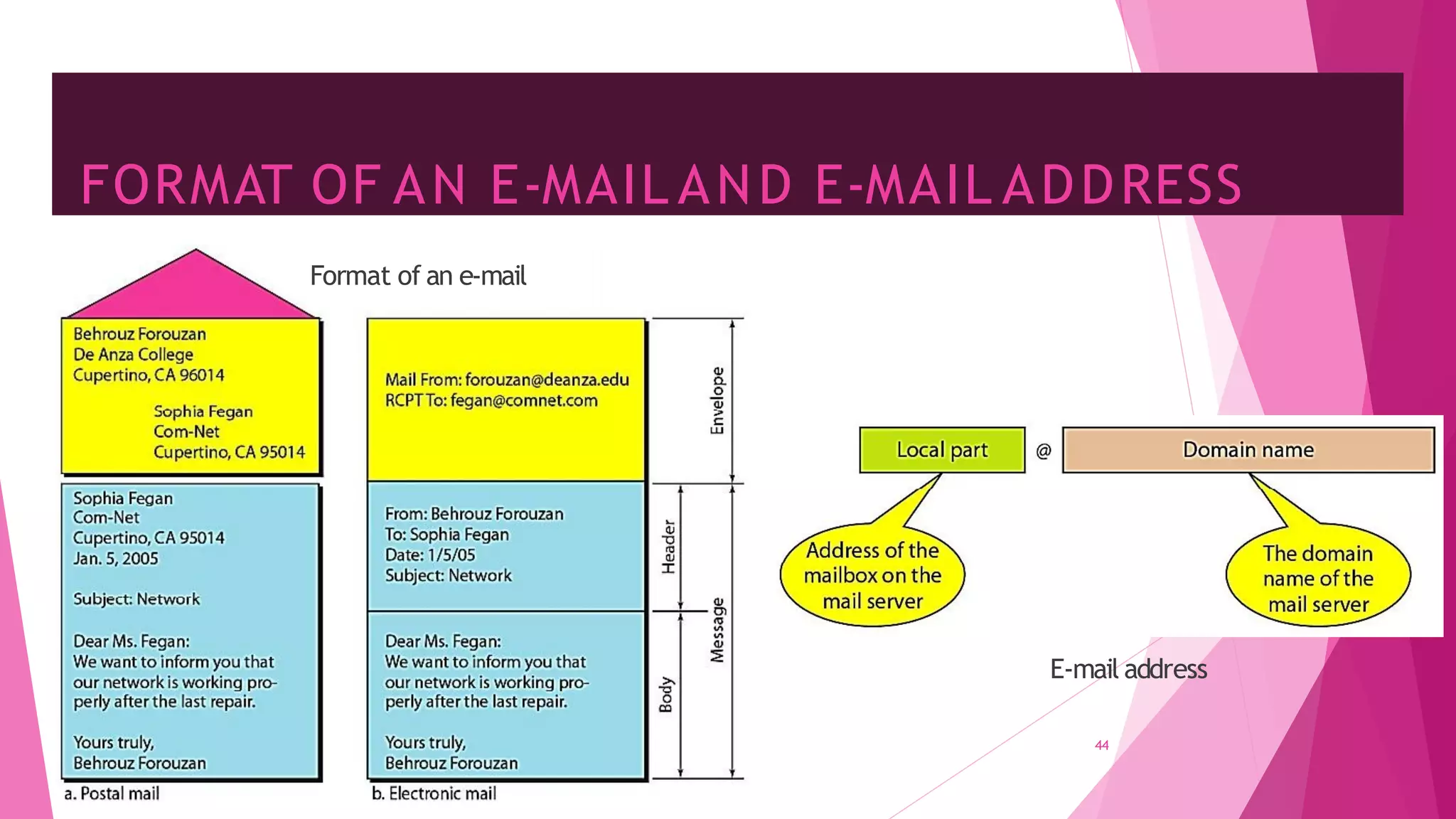
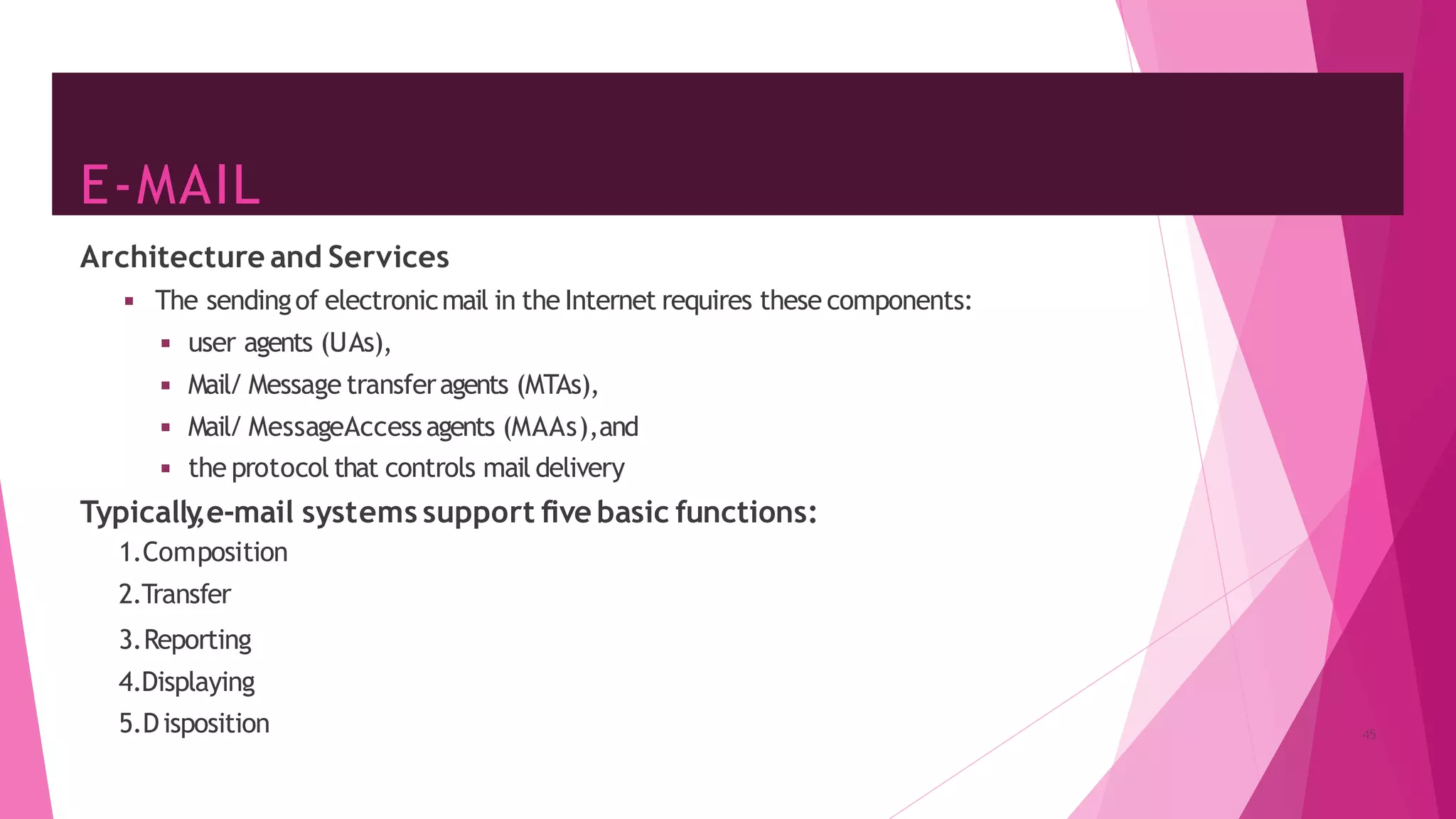
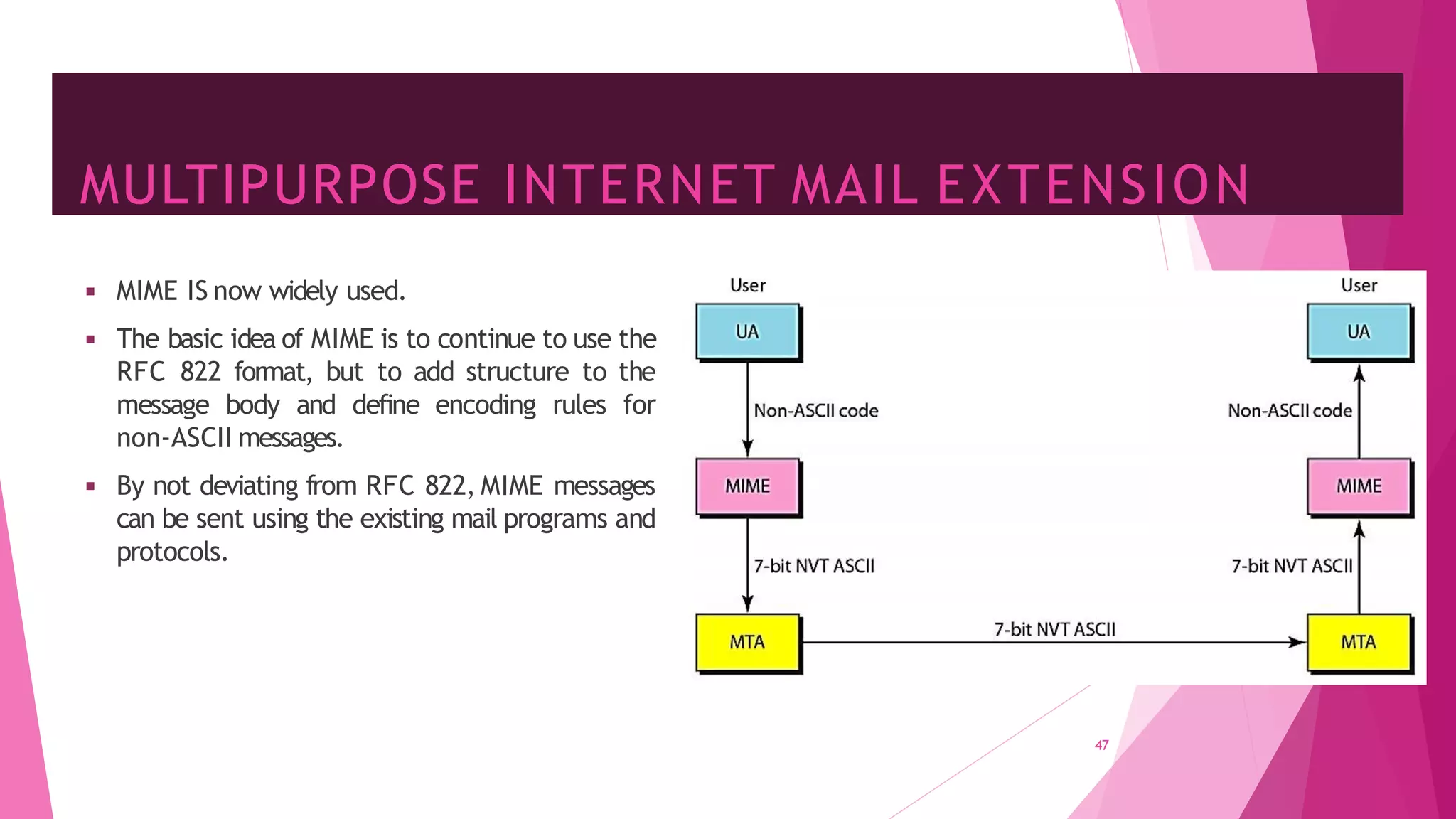
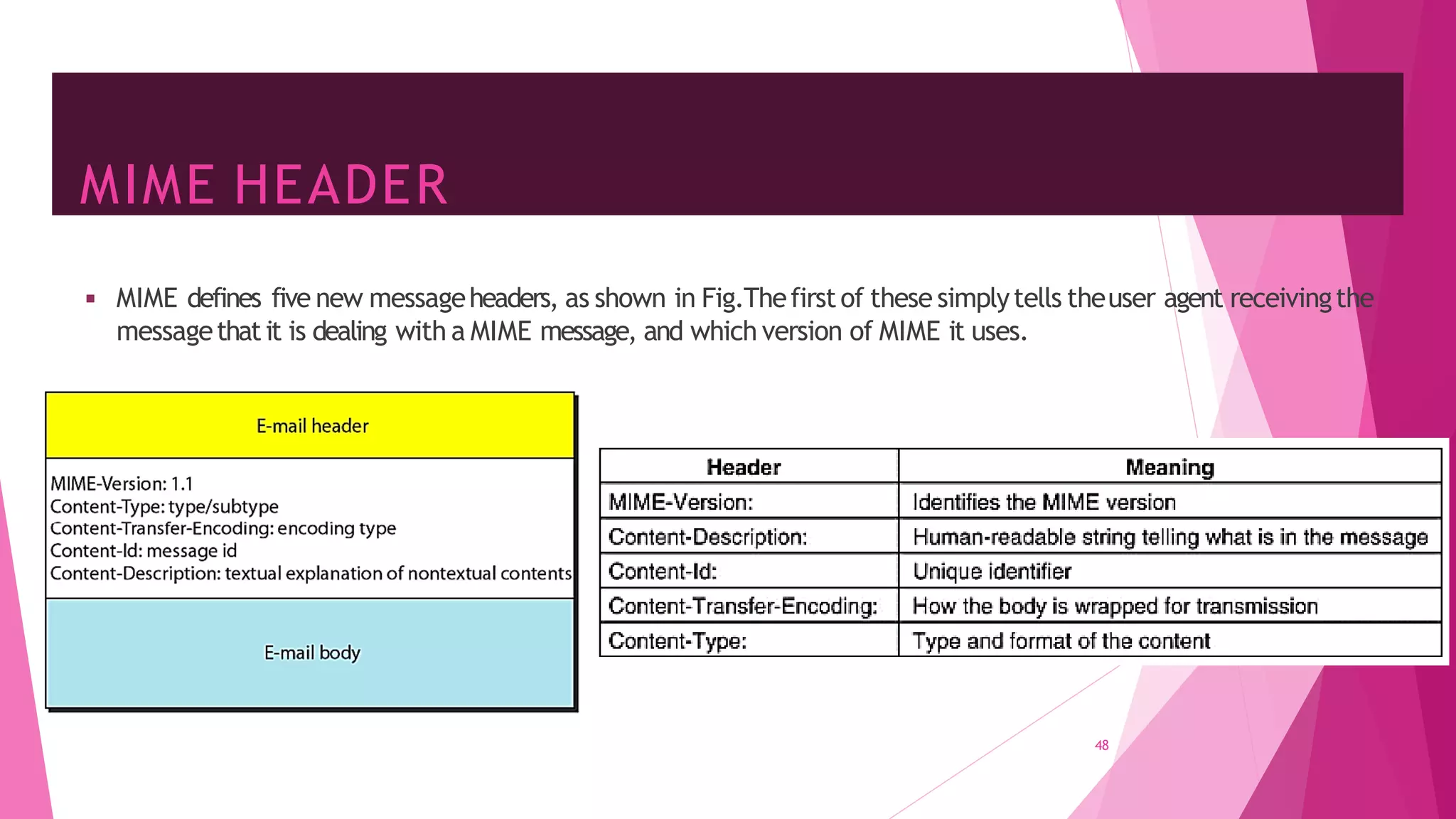
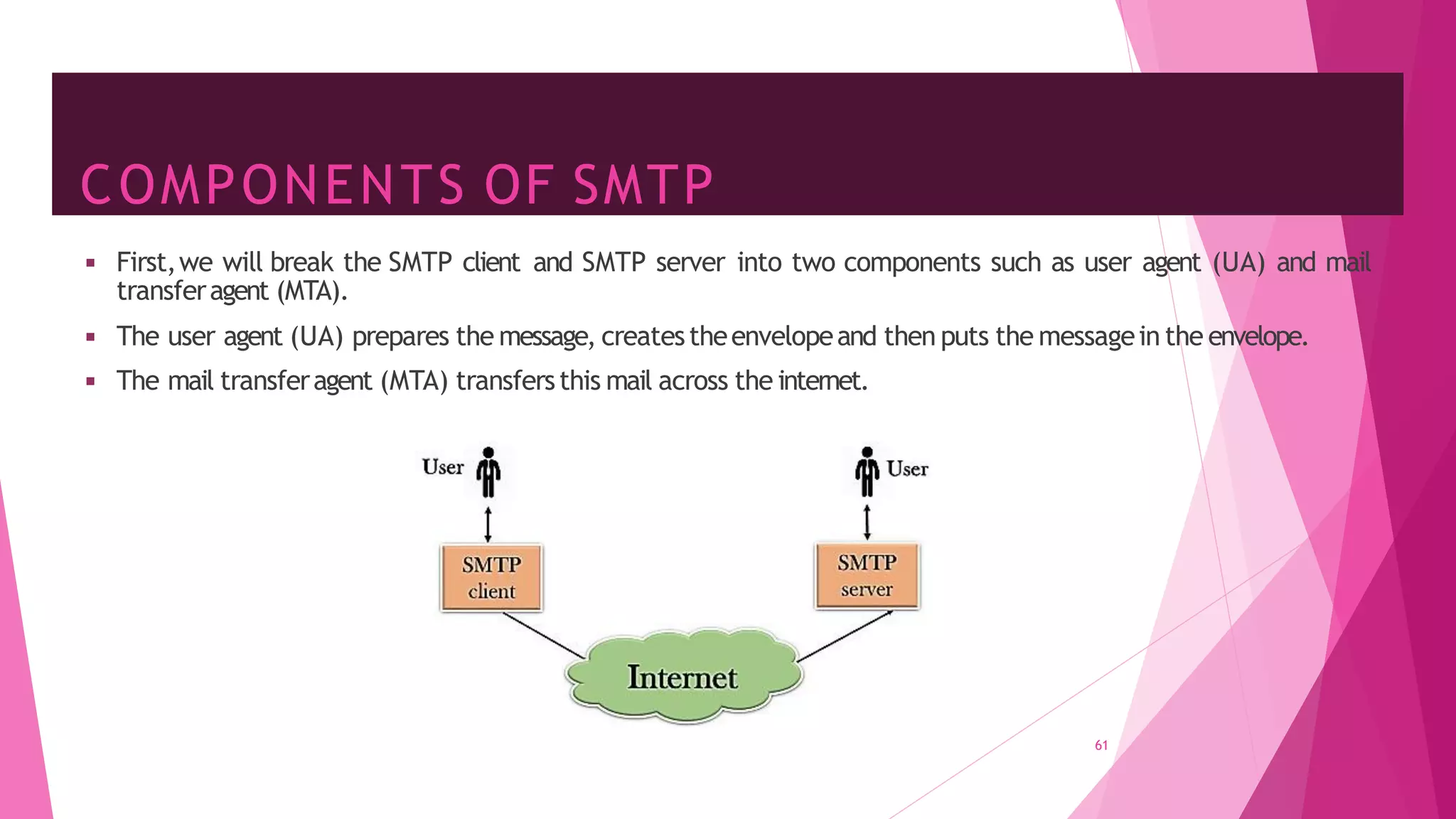
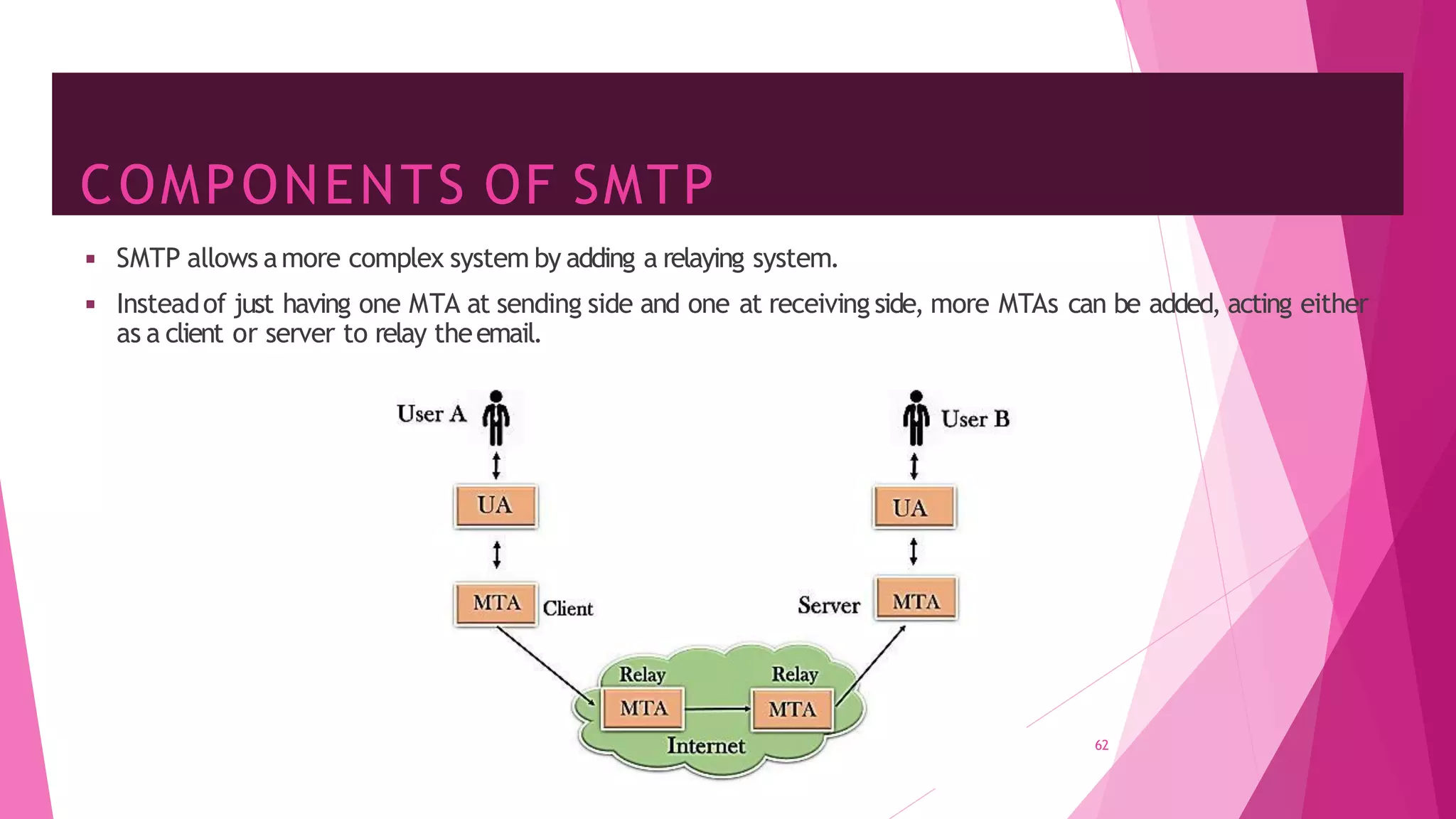
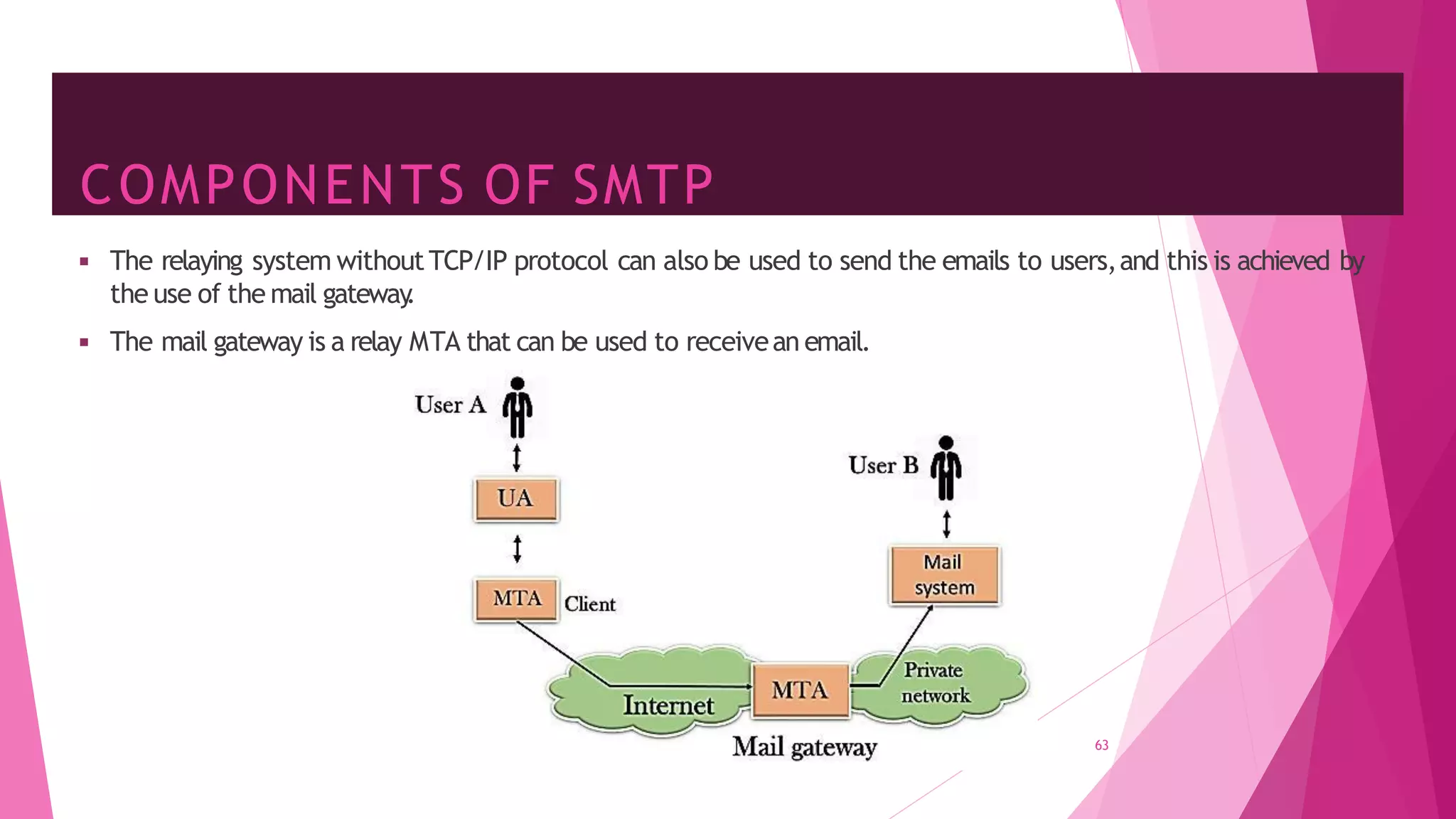
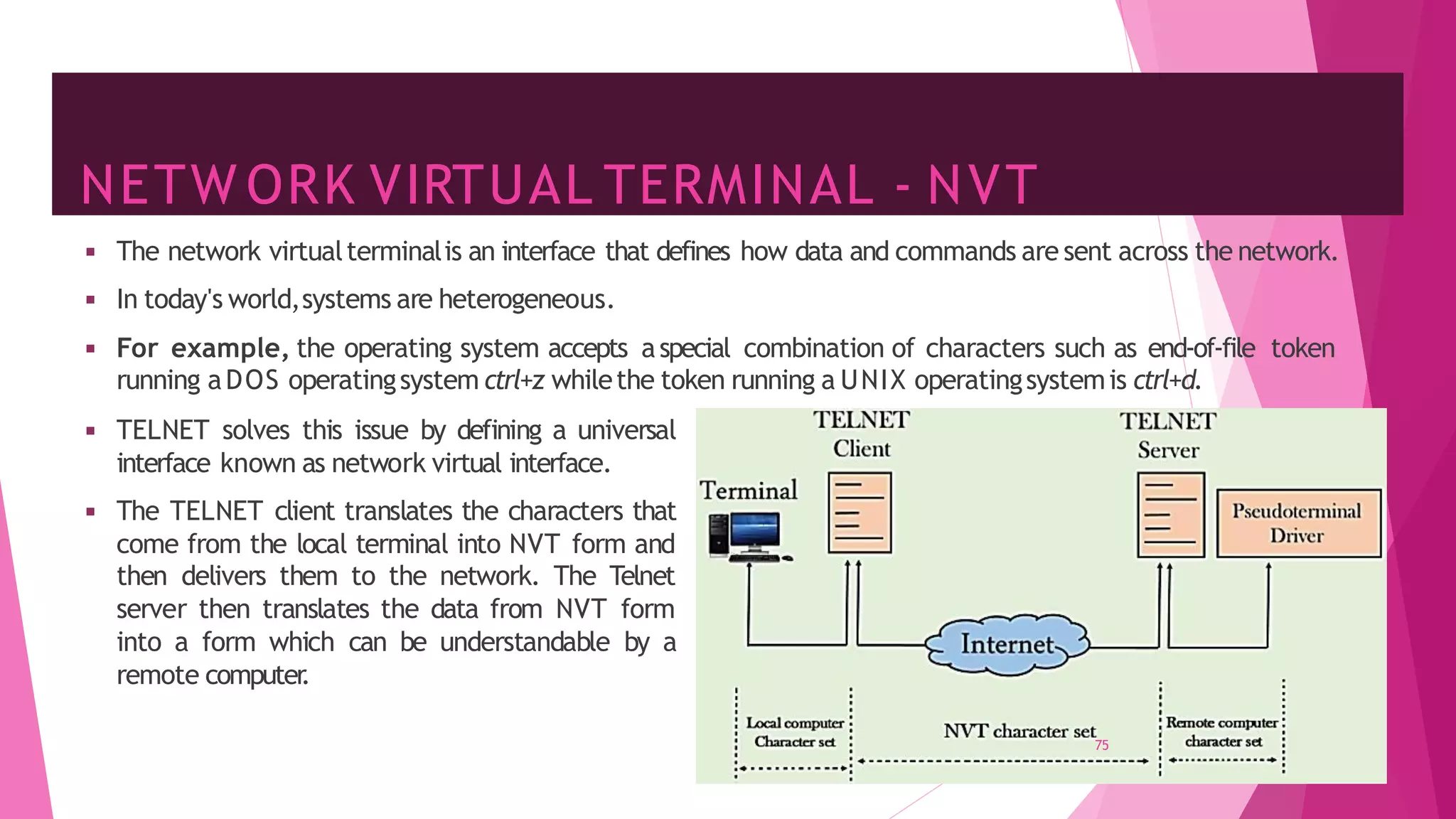
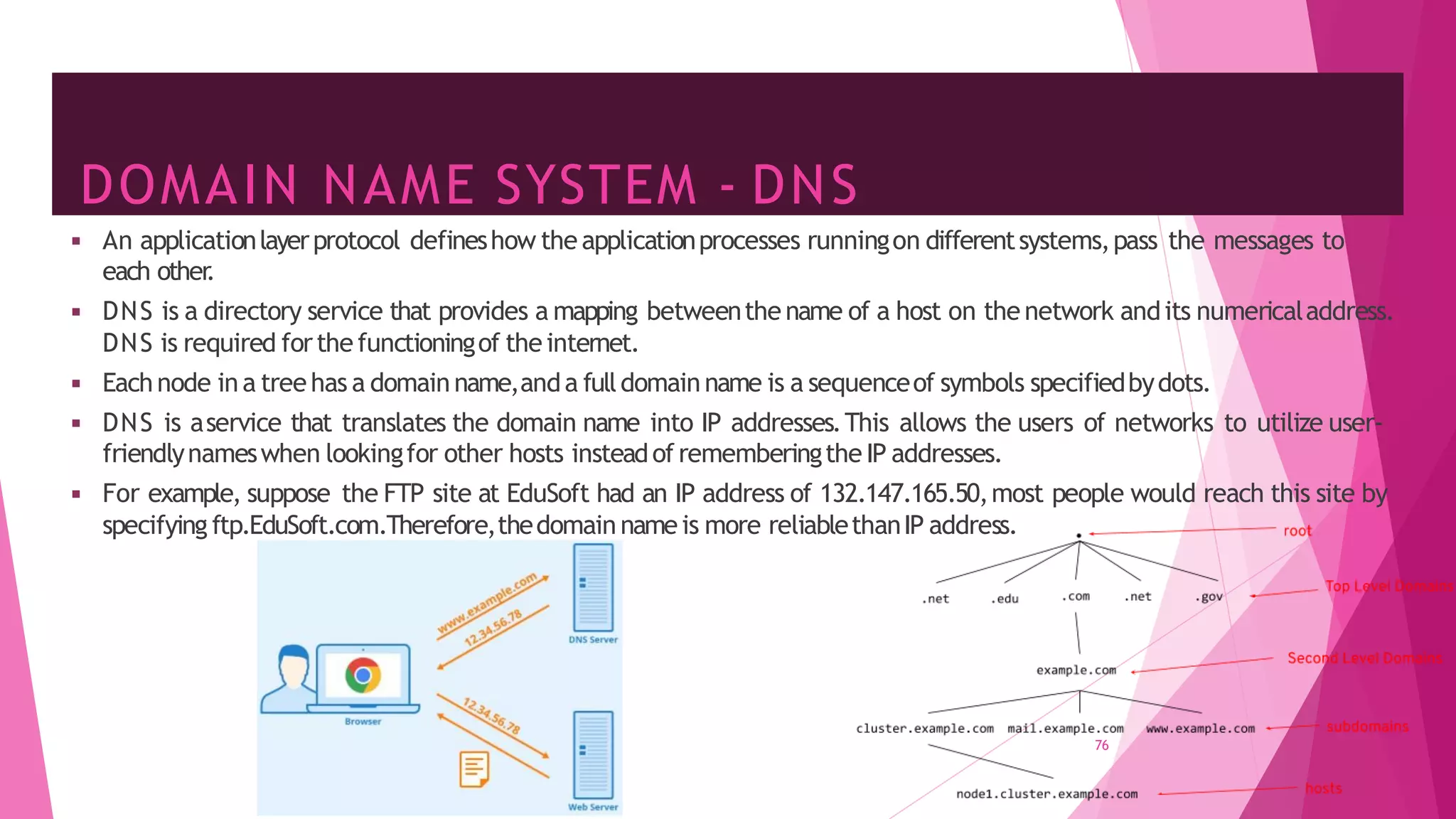
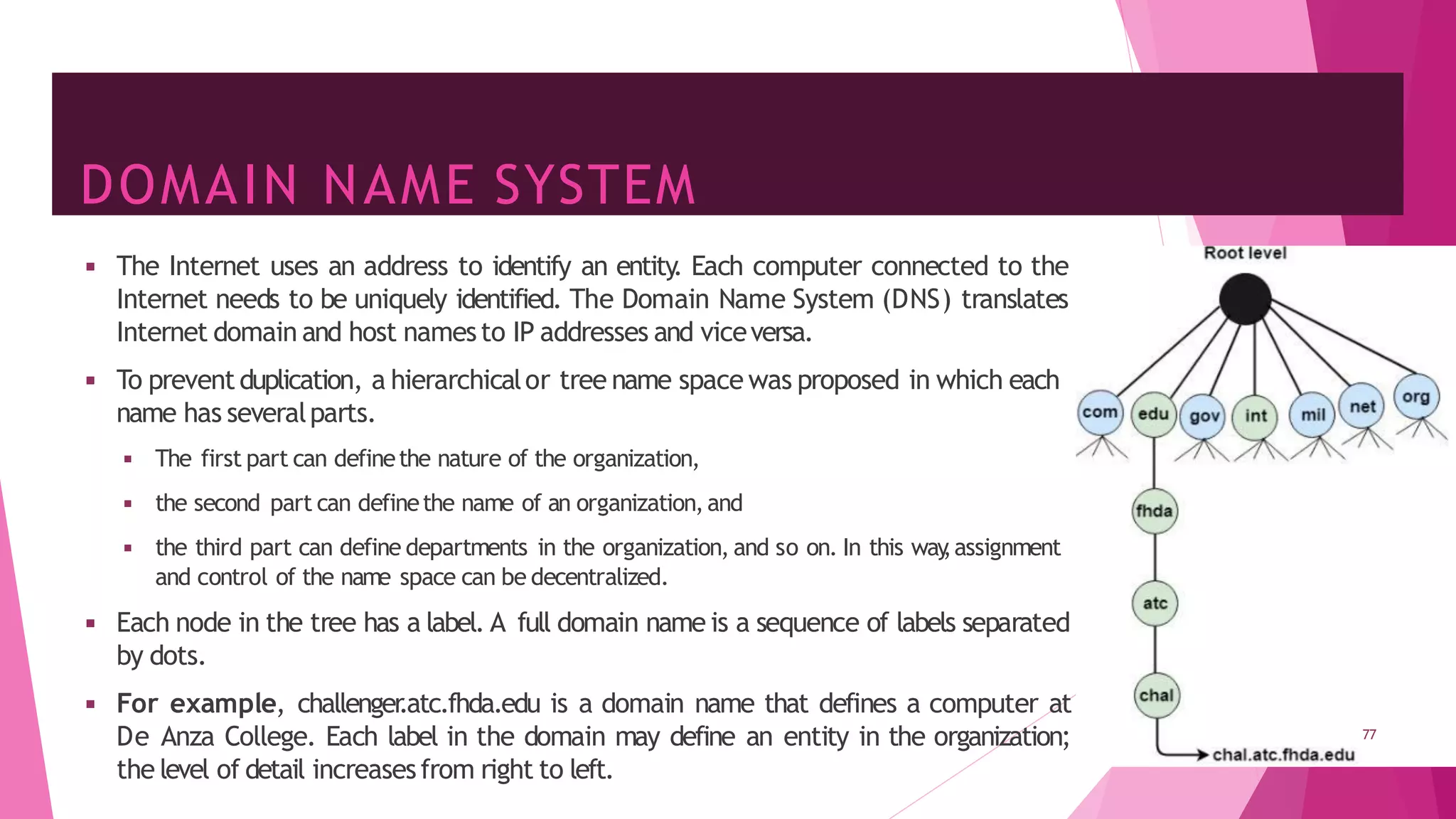
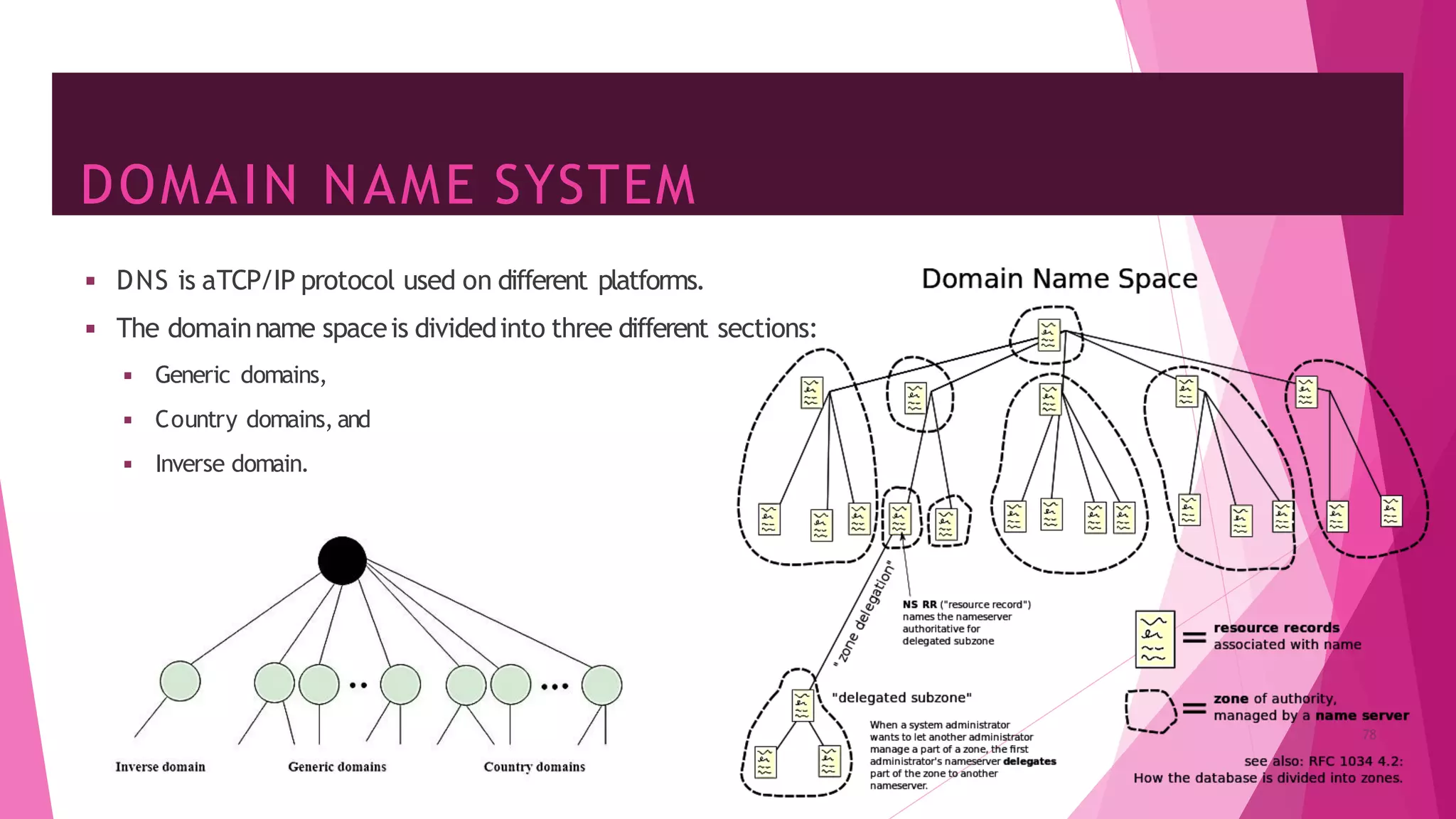
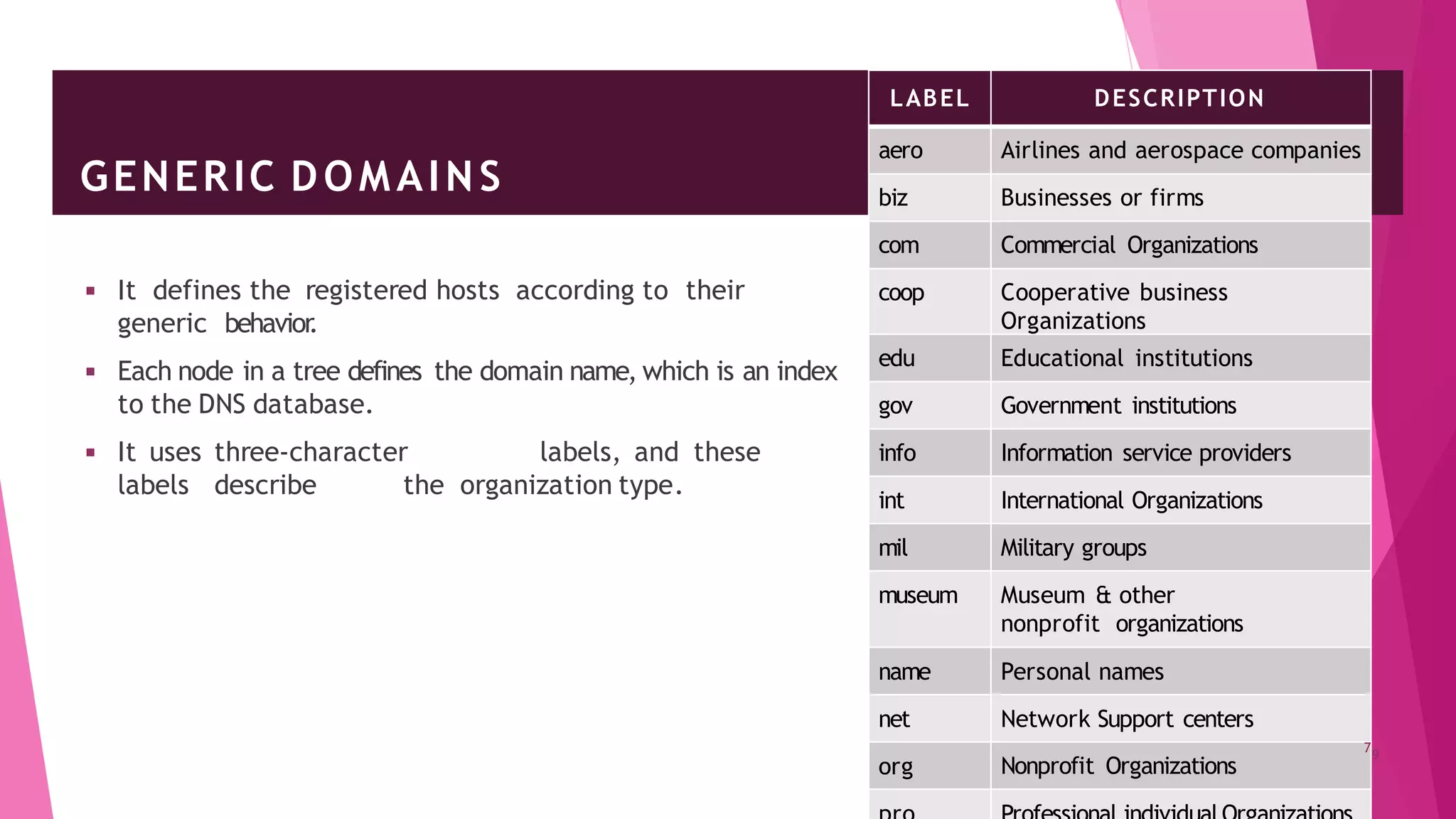
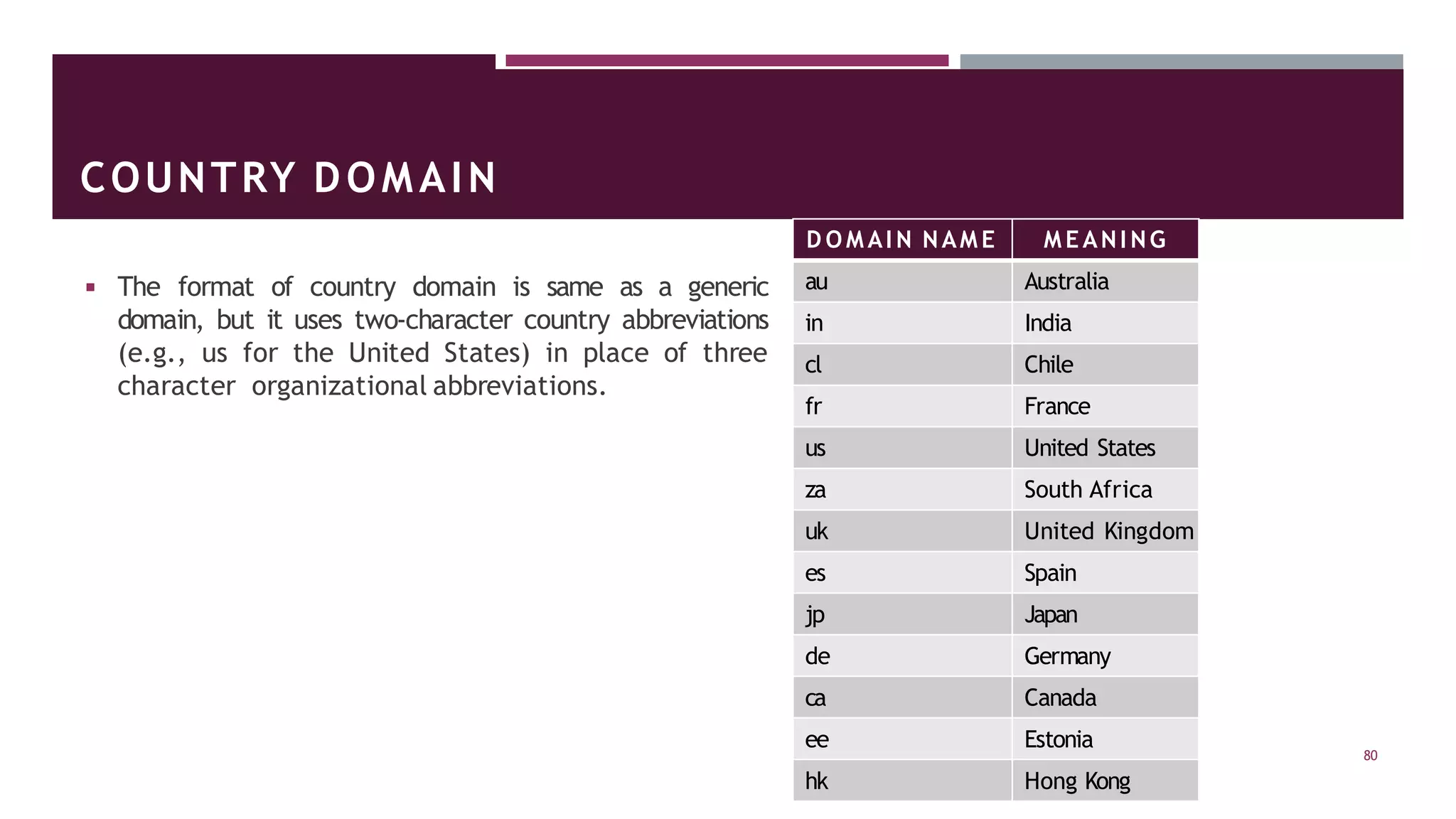
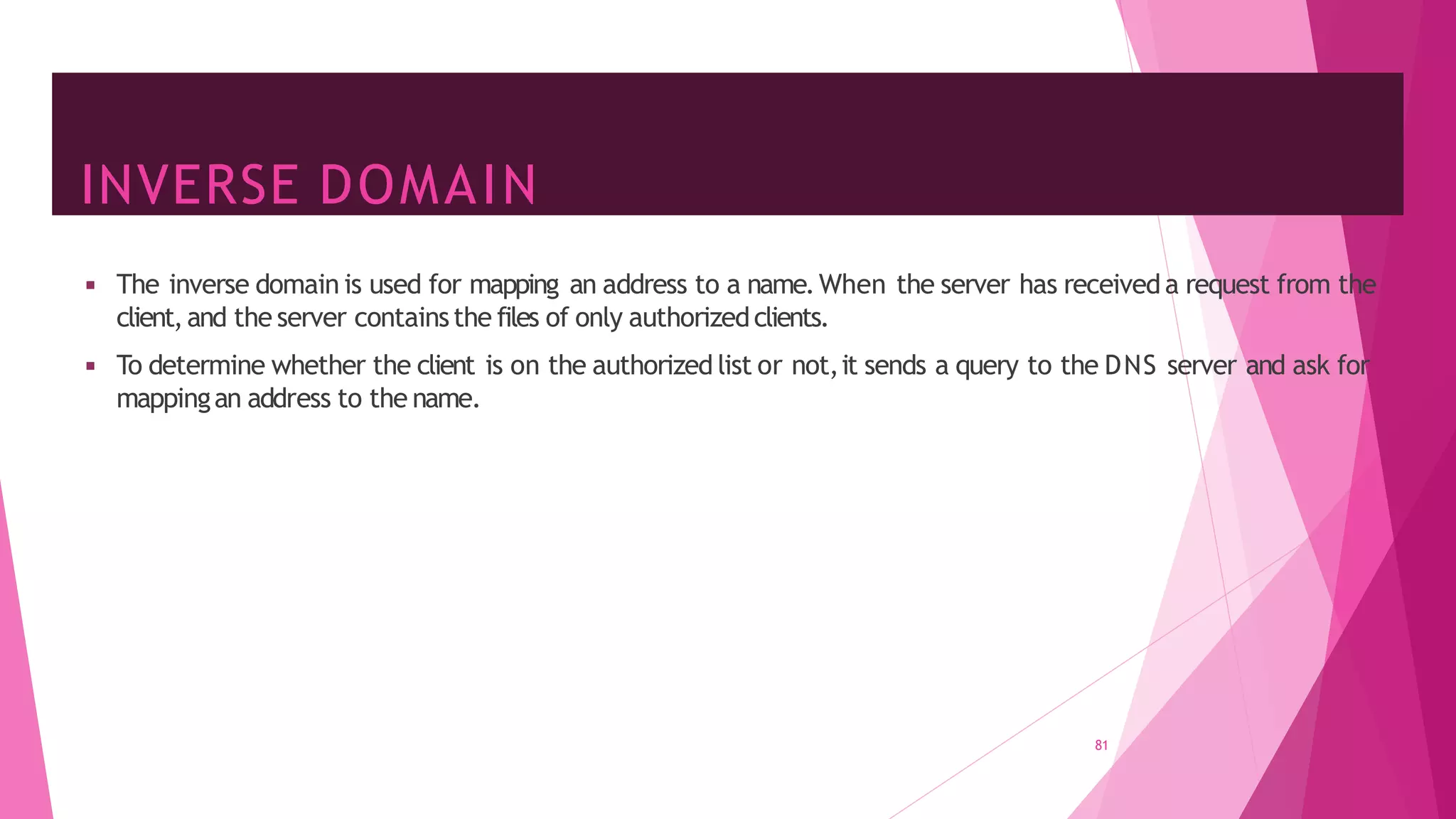
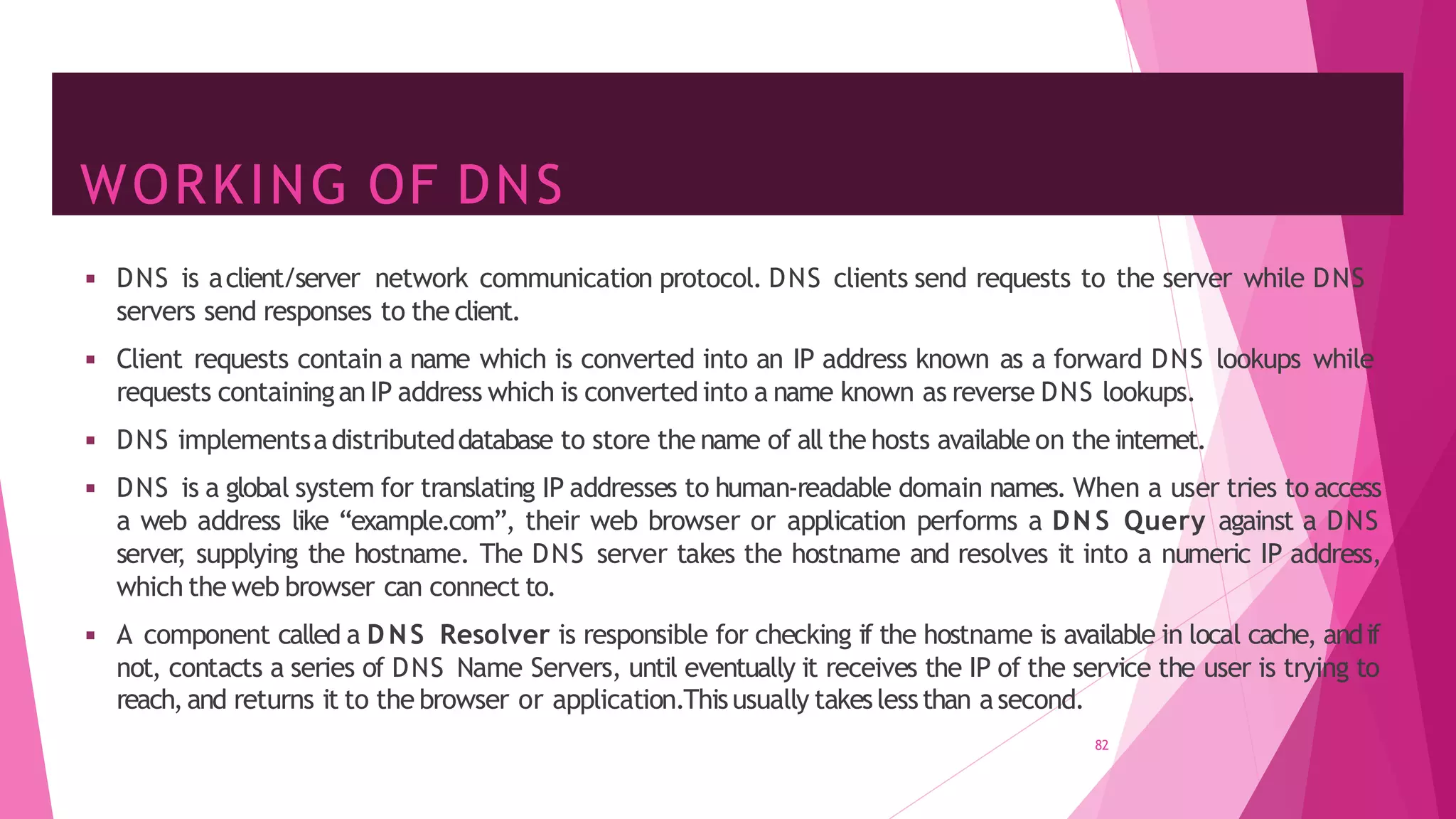
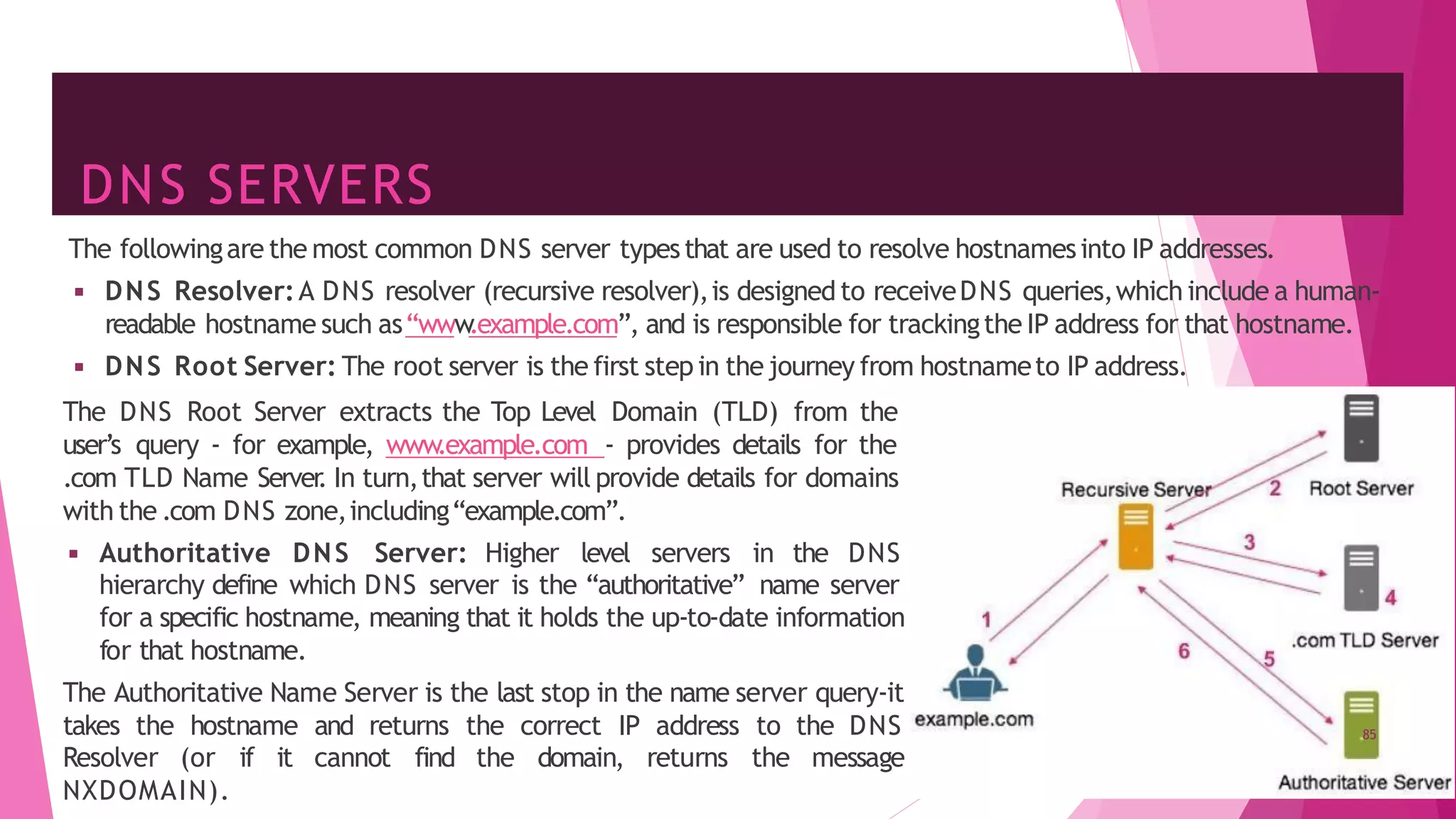
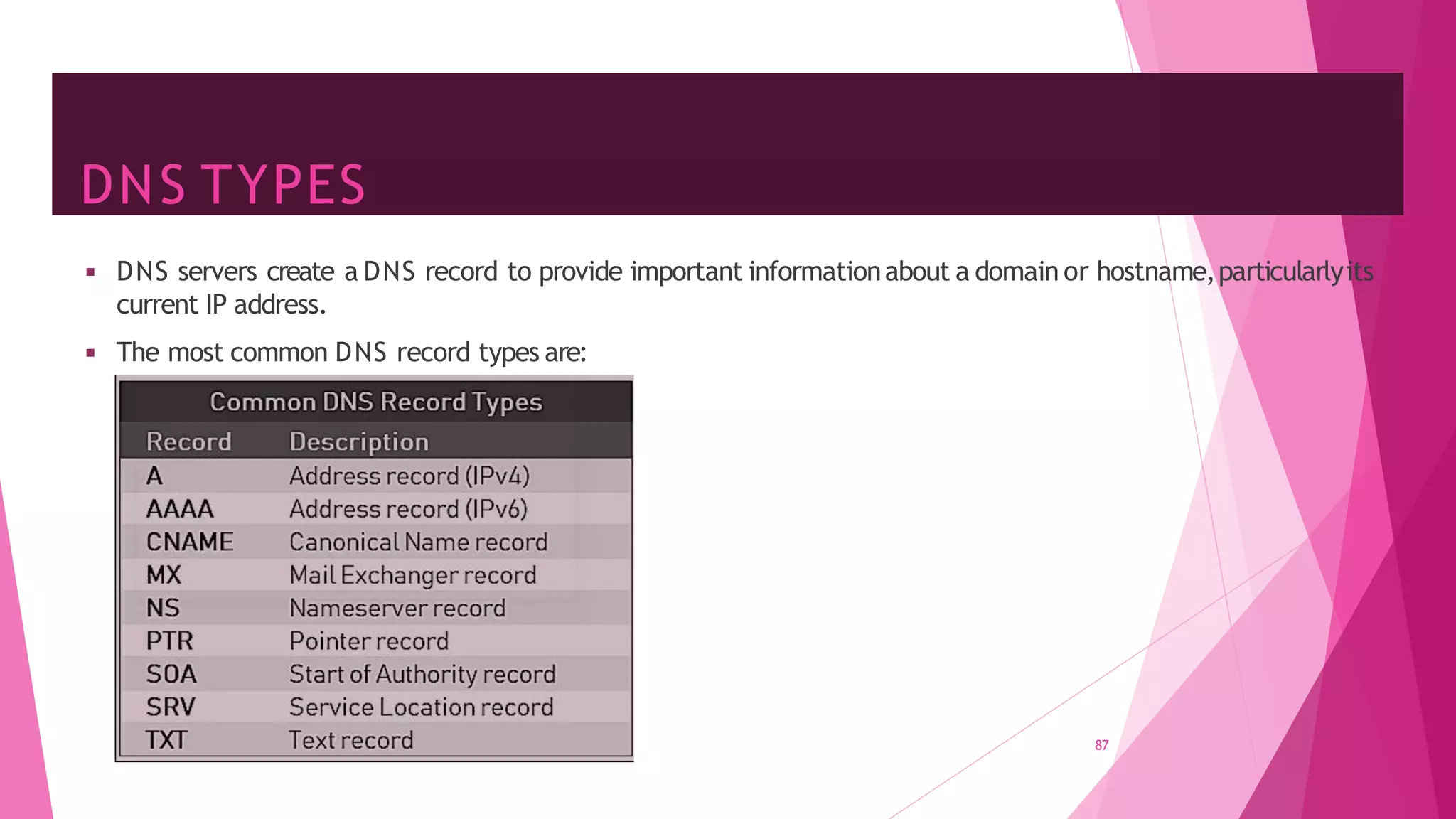
The document discusses principles of network applications and the application layer. It covers transport services available to applications like reliable data transfer, throughput, timing and security. It also discusses application architecture like client-server and peer-to-peer models. Application layer protocols define message types, syntax, semantics and process communication rules. The Internet provides TCP for reliable connection-oriented transfer and UDP for unreliable connectionless transfer. Processes communicate by exchanging messages, with clients initiating sessions and servers waiting to be contacted.