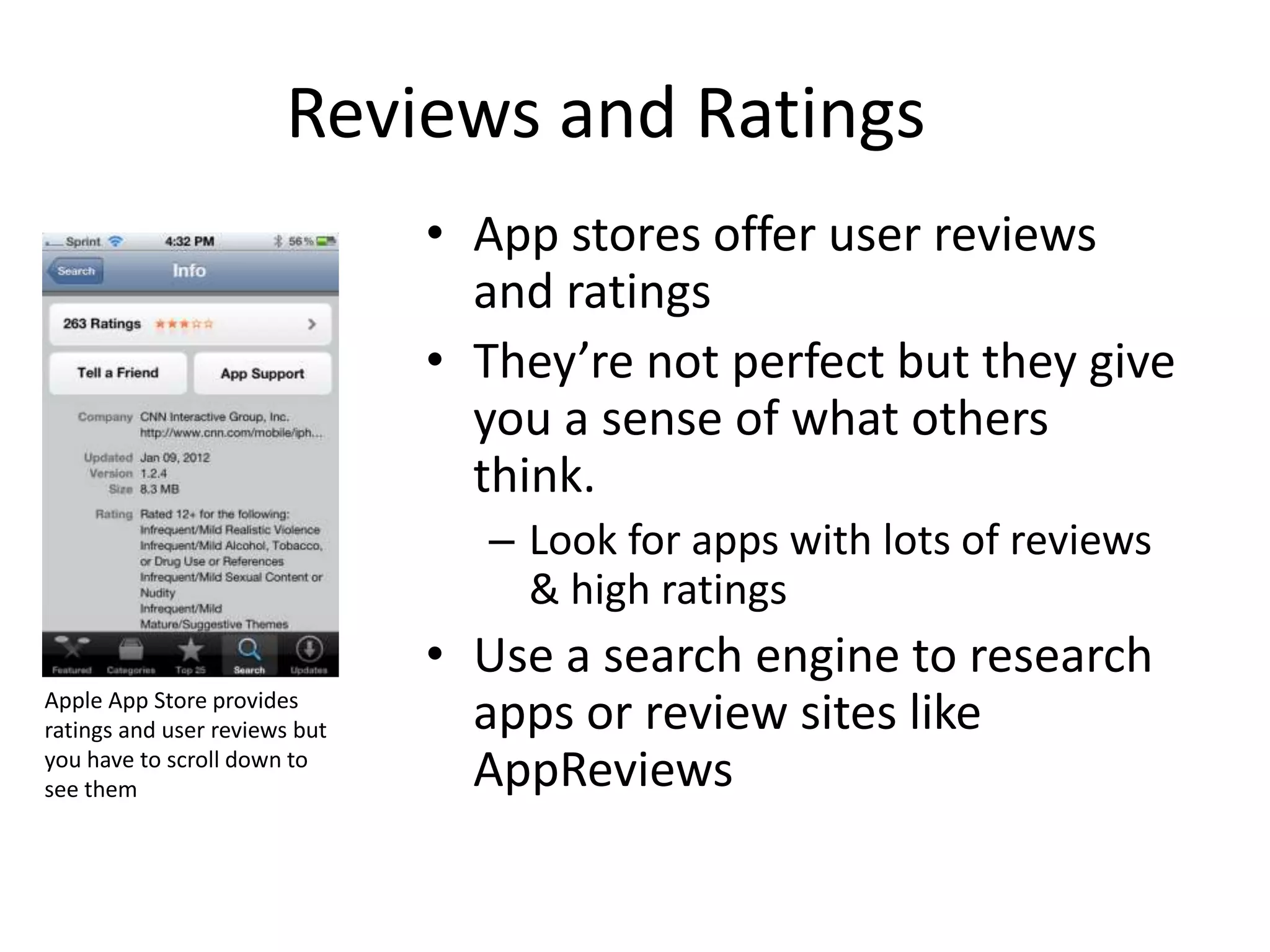
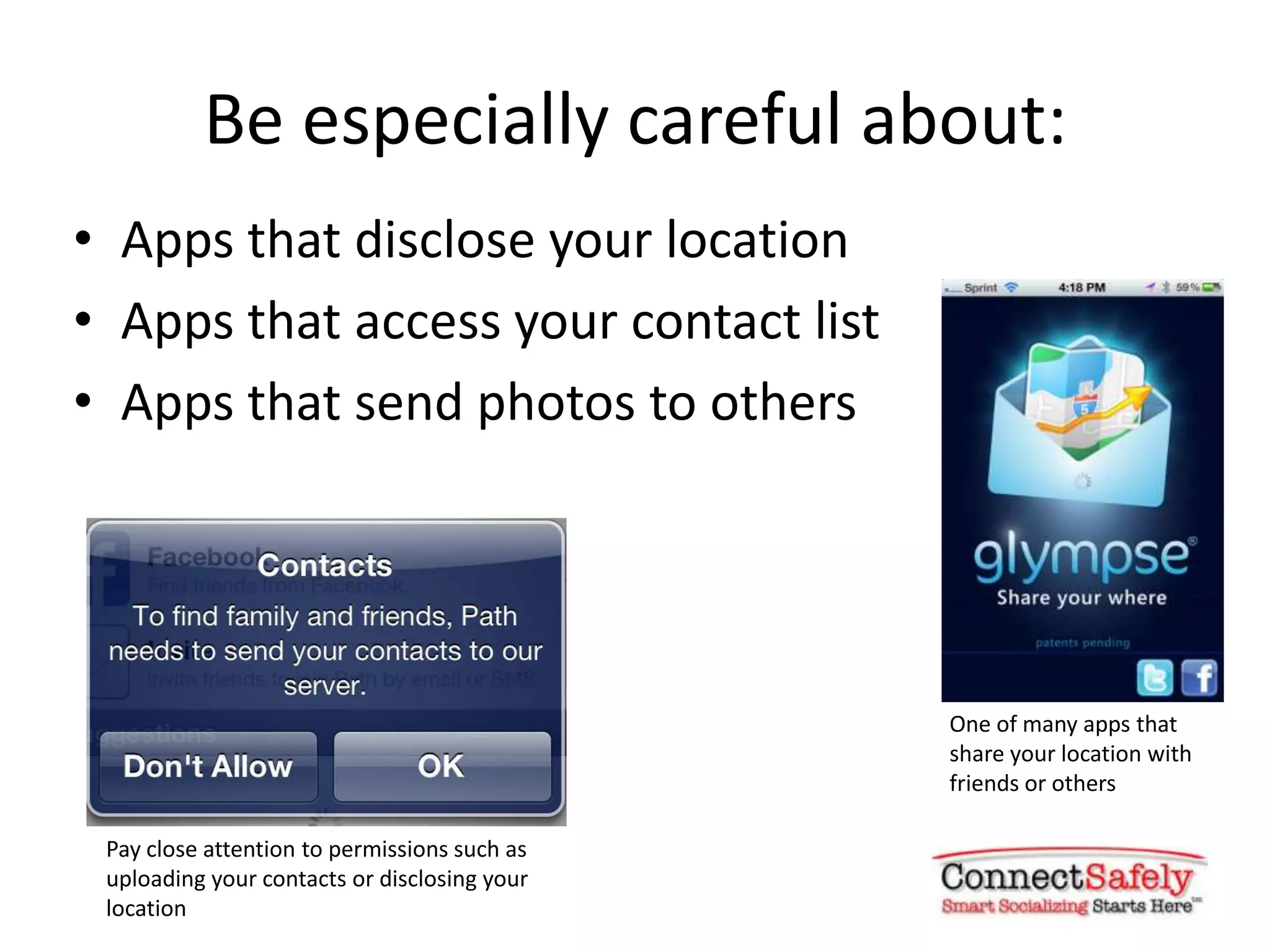
This document summarizes privacy concerns regarding mobile apps and provides tips for users. It notes that there are over 1 million apps across platforms and that apps can theoretically access personal data and device functions without permission. While app stores provide ratings and reviews, developers are not perfectly policed. The document advises users to carefully review what permissions apps request and only install reputable apps from official stores. It also discusses new policies requiring privacy disclosures and a proposed "Consumer Privacy Bill of Rights."