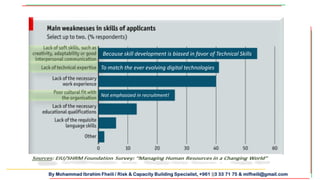
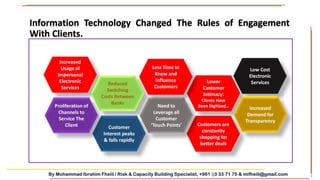
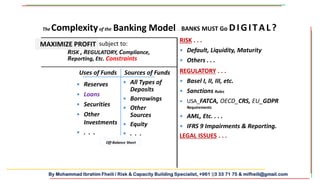
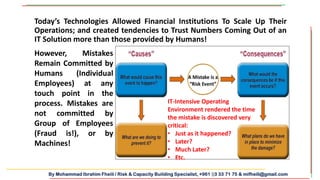
The document discusses the importance of integrating cybersecurity into the business development mindset, emphasizing the communication breakdown between IT and business leaders as a major risk factor. It highlights the need for trust in cybersecurity initiatives, the necessity for both technical and soft skills among employees, and the requirement for banks to comply with evolving regulations while managing emerging risks. Additionally, it underscores the importance of a strong cybersecurity strategy that differentiates protection based on the value of data and assets.
















































![By Mohammad Ibrahim Fheili / Risk & Capacity Building Specialist, +961 03 33 71 75 & mifheili@gmail.com
• Cyber-Risk changes as often as
technologies change! We all admit that technologies
[outside] are evolving daily. How is Your Technology [inside]
changing?!
• Risk appetite and Tolerance need to be
high on any Board's agenda and is a core
consideration of an enterprise risk
management approach.
The Board of Directors’ Oversight . . .](https://image.slidesharecdn.com/cybersecurityonebankersperspective-190918181124/85/Cyber-security-one-banker-s-perspective-57-320.jpg)


