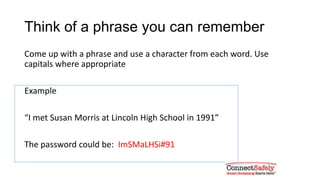
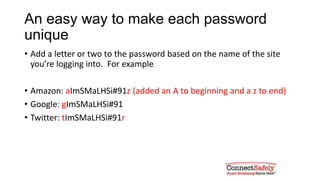
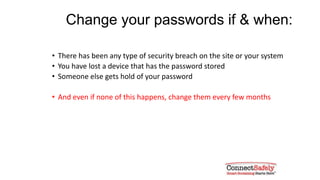
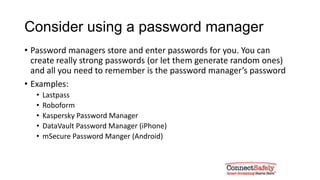
This document provides tips for creating strong and unique passwords. It recommends passwords be at least 8 characters long and contain a mix of uppercase letters, numbers, and symbols. It suggests using phrases and modifying them slightly for different sites. The document also advises using two-factor authentication when available and warns against sharing passwords or entering them based on links in emails.