Performance analysis of AODV And OLSR
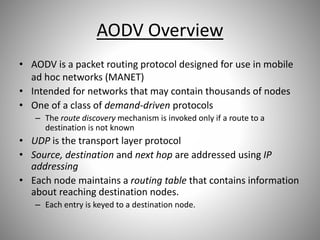
- 1. AODV Overview • AODV is a packet routing protocol designed for use in mobile ad hoc networks (MANET) • Intended for networks that may contain thousands of nodes • One of a class of demand-driven protocols – The route discovery mechanism is invoked only if a route to a destination is not known • UDP is the transport layer protocol • Source, destination and next hop are addressed using IP addressing • Each node maintains a routing table that contains information about reaching destination nodes. – Each entry is keyed to a destination node.
- 2. Routing Table Fields • Destination IP address • Destination Sequence Number • Valid Destination Sequence Number Flag • Other state and routing flags • Network Interface • Hop Count (needed to reach destination) • Next Hop • Precursor List • Lifetime (route expiration or deletion time)
- 3. Overview (continued) • Routing table size is minimized by only including next hop information, not the entire route to a destination node. • Sequence numbers for both destination and source are used. • Managing the sequence number is the key to efficient routing and route maintenance – Sequence numbers are used to indicate the relative freshness of routing information – Updated by an originating node, e.g., at initiation of route discovery or a route reply. – Observed by other nodes to determine freshness.
- 4. Overview (continued) • The basic message set consists of: – RREQ – Route request – RREP – Route reply – RERR – Route error – HELLO – For link status monitoring
- 5. AODV Operation – Message Types • RREQ Messages – While communication routes between nodes are valid, AODV does not play any role. – A RREQ message is broadcasted when a node needs to discover a route to a destination. – As a RREQ propagates through the network, intermediate nodes use it to update their routing tables (in the direction of the source node). – The RREQ also contains the most recent sequence number for the destination. – A valid destination route must have a sequence number at least as great as that contained in the RREQ.
- 7. AODV Operation – Message Types • RREP Messages – When a RREQ reaches a destination node, the destination route is made available by unicasting a RREP back to the source route. – A node generates a RREP if: • It is itself the destination. • It has an active route to the destination. Ex: an intermediate node may also respond with an RREP if it has a “fresh enough” route to the destination. – As the RREP propagates back to the source node, intermediate nodes update their routing tables (in the direction of the destination node).
- 9. AODV Operation – Message Types • RERR Messages – This message is broadcast for broken links – Generated directly by a node or passed on when received from another node
- 11. AODV Routing • There are two phases – Route Discovery. – Route Maintenance. • Each node maintains a routing table with knowledge about the network. • AODV deals with route table management. • Route information maintained even for short lived routes – reverse pointers.
- 12. Entries in Routing Table • Destination IP Address • Destination Sequence Number • Valid Destination Sequence Number flag • Other state and routing flags (e.g., valid, invalid, repairable, being repaired) • Network Interface • Hop Count (number of hops needed to reach destination) • Next Hop • List of Precursors • Lifetime (expiration or deletion time of the route) • DSR maintains additional table entries, causing a larger memory overhead
- 13. Discovery • Broadcast RREQ messages. • Intermediate nodes update their routing table • Forward the RREQ if it is not the destination. • Maintain back-pointer to the originator. • Destination generates RREQ message. • RREQ sent back to source using the reverse pointer set up by the intermediate nodes. • RREQ reaches destination, communication starts.
- 14. Algorithm for Discovery • @Originator • If a route to the destination is available, start sending data. • Else generate a RREQ packet. Increment the RREQID by 1.Increment the sequence number by 1.Destination IP address ,currently available sequence number included. • @Intermediate Node • Generate route reply, if a 'fresh enough' route is a valid route entry for the destination whose associated sequence number is at least as great as that contained in the RREQ. Change the sequence number of the destination node if stale, increment the hop count by 1 and forward. • @Destination 1.Increment sequence number of the destination. 2.Generate a RREQ message and sent back to Originator.
- 15. Maintenance • Hello messages broadcast by active nodes periodically HELLO_INTERVAL. • No hello message from a neighbor in DELETE_PERIOD,link failure identified. • A local route repair to that next hop initiated. • After a timeout ,error propagated both to originator and destination. • Entries based on the node invalidated.
- 16. RERR Messages – Message is broadcasted when: i. A node detects that a link with adjacent neighbor is broken (destination no longer reachable). ii. If it gets a data packet destined to a node for which it does not have an active route and is not repairing. iii. If it receives a RERR from a neighbor for one or more active routes.
- 17. RERR Processing (for above broadcasts) – Build Affected Destination Listing i. List unreachable destinations containing unreachable neighbor & destination using unreachable as next hop ii. Only one unreachable destination, which node already has. iii. List of nodes where RERR is next hop – Update information – Transmit RERR for each item listed
- 18. RERR – information update – Destination Sequence # - Update sequence # for case i and ii - Copy sequence # for case iii – Invalidate route entry – Update Lifetime field as (currtime + DELETE_PERIOD) – Only now may route entry be deleted
- 19. RERR message transmission – Unicast - Send RERR to single recipient – Unicast iteritive - Send RERR to a number of recipients individually – Broadcast - Notify multiple recipients simultaniously - Broadcast via 255.255.255.255 TTL = 1
- 20. RERR message transmission – Unicast • A node detects that a link with adjacent neighbor is broken (destination no longer reachable). • If it gets a data packet destined to a node for which it does not have an active route and is not repairing. • If it receives a RERR from a neighbor for one or more active routes. – Unicast iteritive – Broadcast
- 21. OLSR Concepts • Proactive (table-driven) routing protocol – A route is available immediately when needed • Based on the link-state algorithm – Traditionally, all nodes flood neighbor information in a link-state protocol, but not in OLSR • Nodes advertise information only about links with neighbors who are in its multipoint relay selector set – Reduces size of control packets • Reduces flooding by using only multipoint relay nodes to send information in the network – Reduces number of control packets by reducing duplicate transmissions
- 22. OLSR Concepts (2) • Does not require reliable transfer, since updates are sent periodically • Does not need in-order delivery, since sequence numbers are used to prevent out-of- date information from being misinterpreted • Uses hop-by-hop routing – Routes are based on dynamic table entries maintained at intermediate nodes
- 23. Multipoint Relays • Each node N in the network selects a set of neighbor nodes as multipoint relays, MPR(N), that retransmit control packets from N – Neighbors not in MPR(N) process control packets from N, but they do not forward the packets • MPR(N) is selected such that all two-hop neighbors of N are covered by (one-hop neighbors) of MPR(N) 1 4 3 5 2 6 7 One optimal set for Node 4: MPR(4) = { 3, 6 } Is there another optimal MPR(4)?
- 24. Multipoint Relay Selector Set • The multipoint relay selector set for Node N, MS(N), is the set of nodes that choose Node N in their multipoint relay set – Only links N-M, for all M such that NMS(M) will be advertised in control messages MS(3) = {…, 4, …} MS(6) = {…, 4, …} (Assuming bidirectional links) 1 4 3 5 2 6 7
- 25. HELLO Messages (1) • Each node uses HELLO messages to determine its MPR set • All nodes periodically broadcast HELLO messages to their one-hop neighbors (bidirectional links) • HELLO messages are not forwarded 1 4 3 5 2 6 7 HELLO: NBR(4) = {1,3,5,6}
- 26. HELLO Messages (2) • Using the neighbor list in received HELLO messages, nodes can determine their two-hop neighborhood and an optimal (or near-optimal) MPR set • A sequence number is associated with this MPR set – Sequence number is incremented each time a new set is calculated 1 4 3 5 2 6 7 At Node 4: NBR(1) = {2} NBR(3) = {2,5} NBR(5) = {3,6} NBR(6) = {5,7} MPR(4) = {3,6}
- 27. HELLO Messages (3) • Subsequent HELLO messages also indicate neighbors that are in the node’s MPR set • MPR set is recalculated when a change in the one-hop or two-hop neighborhood is detected 1 4 3 5 2 6 7 HELLO: NBR(4) = {1,3,5,6}, MPR(4) = {3,6} MS(6) = {…, 4,…} MS(3) = {…, 4,…}
- 28. TC Messages • Nodes send topology information in Topology Control (TC) messages – List of advertised neighbors (link information) – Sequence number (to prevent use of stale information) • A node generates TC messages only for those neighbors in its MS set – Only MPR nodes generate TC messages – Not all links are advertised • A nodes processes all received TC messages, but only forwards TC messages if the sender is in its MS set – Only MPR nodes propagate TC messages
- 29. OLSR Example (1) 1 4 3 5 2 6 7 MPR(1) = { 4 } MPR(2) = { 3 } MPR(3) = { 4 } MPR(4) = { 3, 6 } MPR(5) = { 3, 4, 6 } MPR(6) = { 4 } MPR(7) = { 6 } MS(1) = { } MS(2) = { } MS(3) = { 2, 4, 5 } MS(4) = { 1, 3, 5, 6 } MS(5) = { } MS(6) = { 4, 5, 7 } MS(7) = { }
- 30. OLSR Example (2) • Node 3 generates a TC message advertising nodes in MS(3) = {2, 4, 5} • Node 4 forwards Node 3’s TC message since Node 3 MS(4) = {1, 3, 5, 6} • Node 6 forwards TC(3) since Node 4 MS(6) 1 4 3 5 2 6 7 TC(3) = <2,4,5>
- 31. OLSR Example (3) • Node 4 generates a TC message advertising nodes in MS(4) = {1, 3, 5, 6} • Nodes 3 and 6 forward TC(4) since Node 4 MS(3) and Node 4 MS(6) 1 4 3 5 2 6 7 TC(4) = <1,3,5,6>
- 32. OLSR Example (4) • Node 6 generates a TC message advertising nodes in MS(6) = {4, 5, 7} • Node 4 forwards TC(6) from Node 6 and Node 3 forwards TC(6) from Node 4 • After Nodes 3, 4, and 6 have generated TC messages, all nodes have link-state information to route to any node 1 4 3 5 2 6 7 TC(6) = <4,5,7>
- 33. OLSR Example (5) • Given TC information, each node forms a topology table • A routing table is calculated from the topology table • Note that Link 1-2 is not visible except to Nodes 2 and 3 TC(3) = <2,4,5> TC(4) = <1,3,5,6> TC(6) = <4,5,7> 1 3 5 2 6 7 4 Dest Next Hops 1 4 2 2 2 1 4 4 1 5 5 1 6 4 (5) 2 7 4 (5) 3
