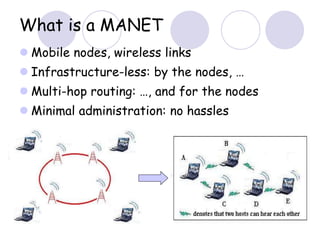
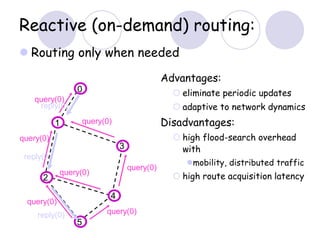
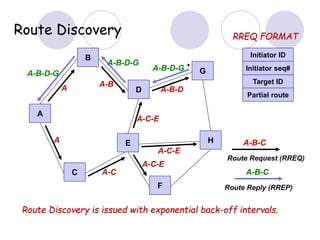
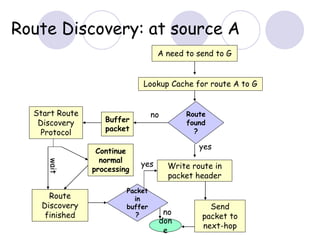
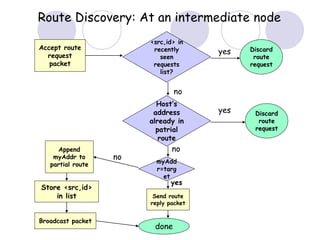
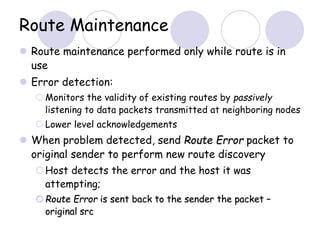
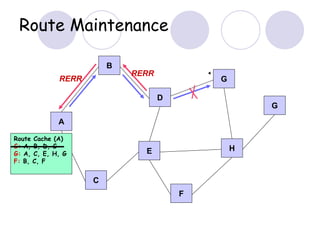
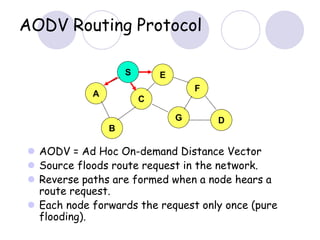
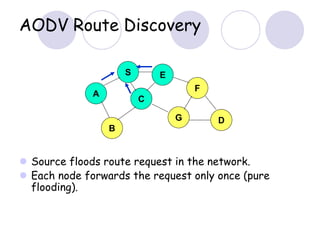
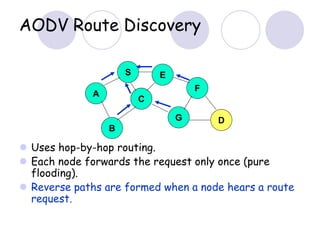
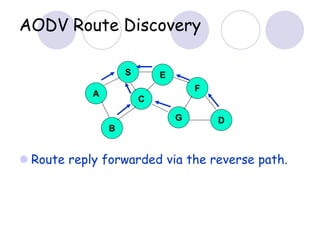
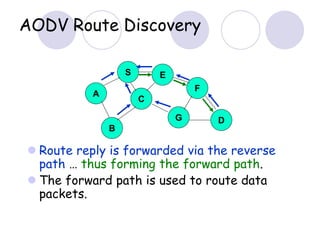
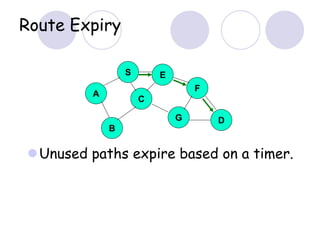
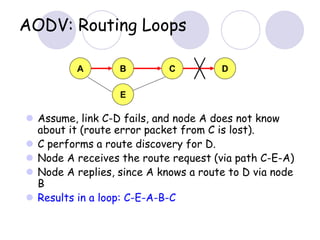
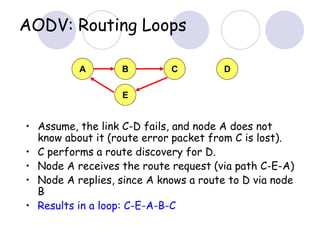
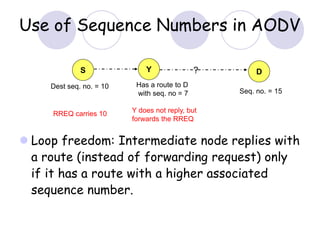
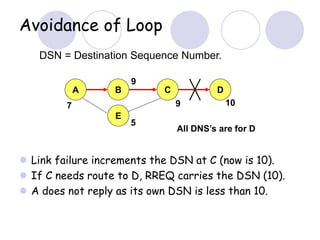
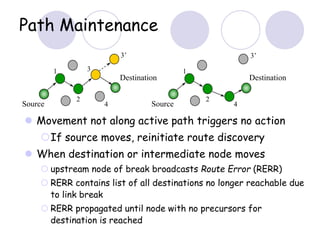
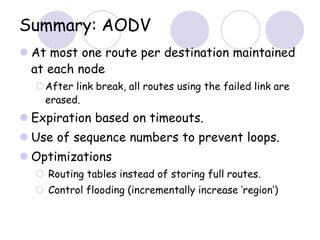
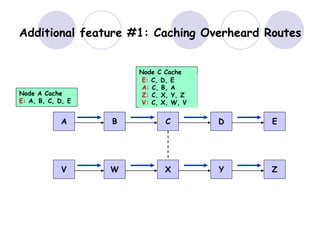
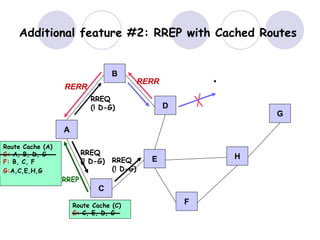
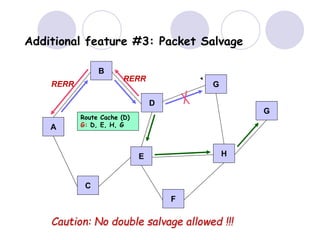
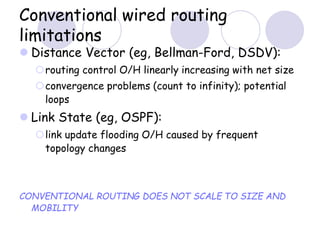
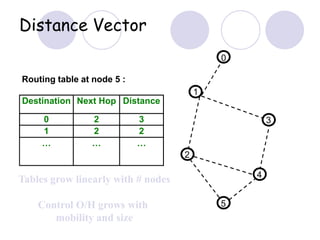
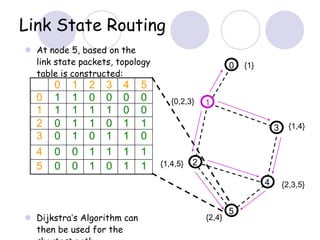
The document discusses routing protocols for mobile ad hoc networks (MANETs). It begins by defining MANETs and their unique characteristics, such as moving nodes, wireless links, and power constraints. Some key challenges for MANET routing protocols are the need for dynamic routing due to frequent topology changes and minimizing routing overhead. The document then discusses various categories of MANET routing protocols, including reactive protocols like DSR and AODV, proactive protocols, and hybrid and location-based protocols. It provides more detailed explanations of the route discovery and maintenance processes for DSR and AODV.