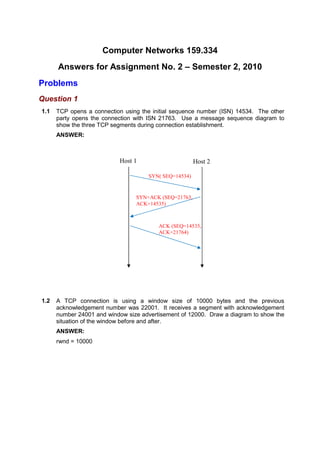
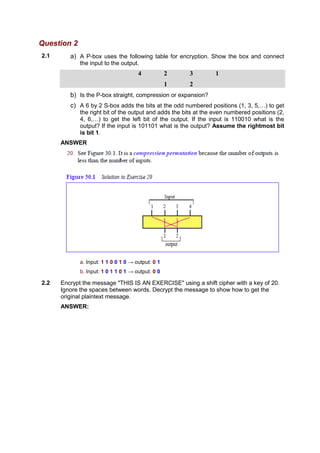
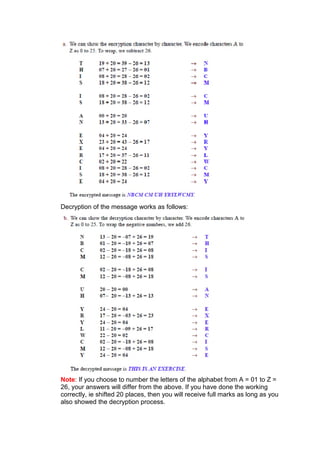
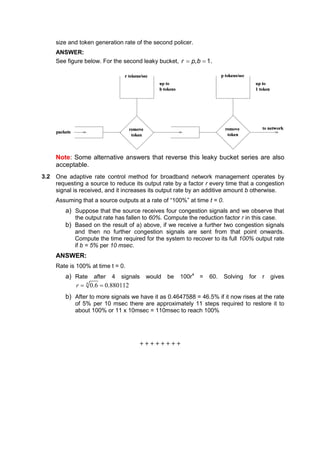
This document contains answers to assignment questions about computer networks. Question 1 involves drawing diagrams to illustrate TCP connection establishment and window sizes. Question 2 covers encryption techniques like P-boxes, shift ciphers, and RSA algorithms. Question 3 discusses using leaky bucket policers to control average, peak, and burst rates for congestion control.