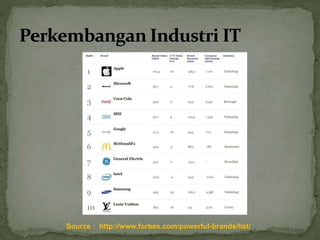
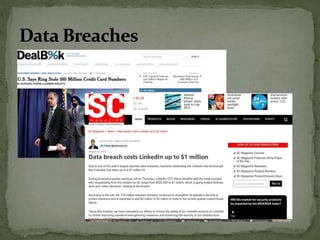
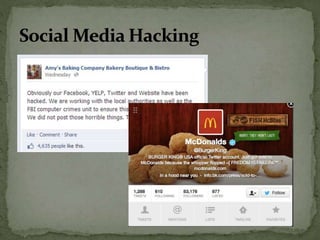
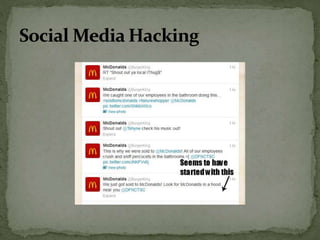
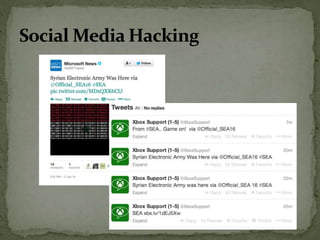
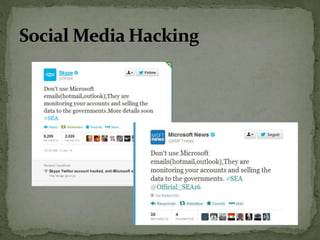
The document discusses the importance of information security amidst the rapid development of information and communication technology. It notes that security experts must always adapt to emerging threats like data breaches, social media hacking, mobile device threats, and advanced malware. Specific threats include the disclosure of sensitive personal and financial information online and through mobile apps. The rise of advanced persistent threats sponsored by governments to achieve political, economic, military and technical objectives is also examined. The document stresses the importance of organizations and individuals implementing proper security measures, policies and awareness programs.