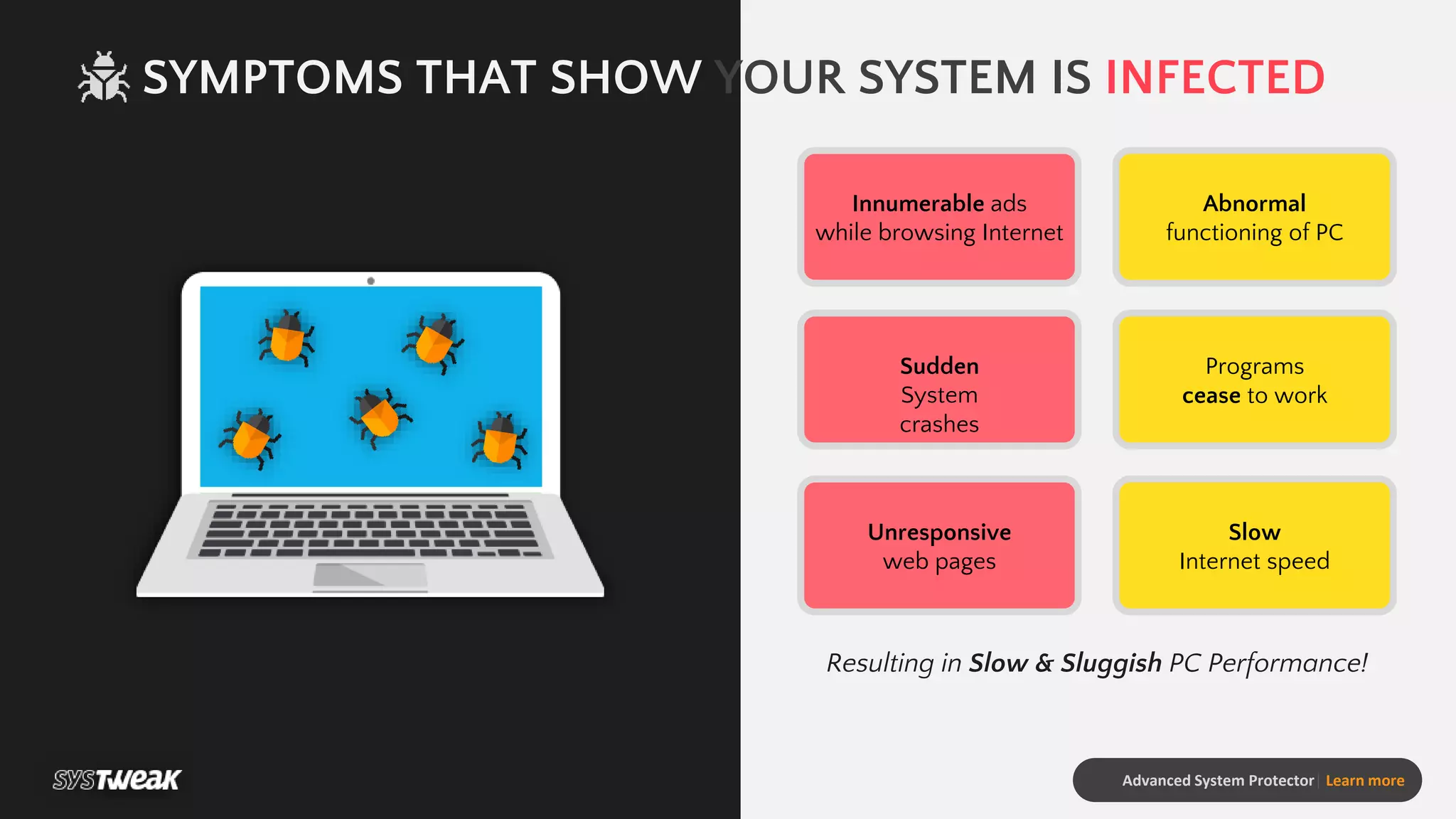
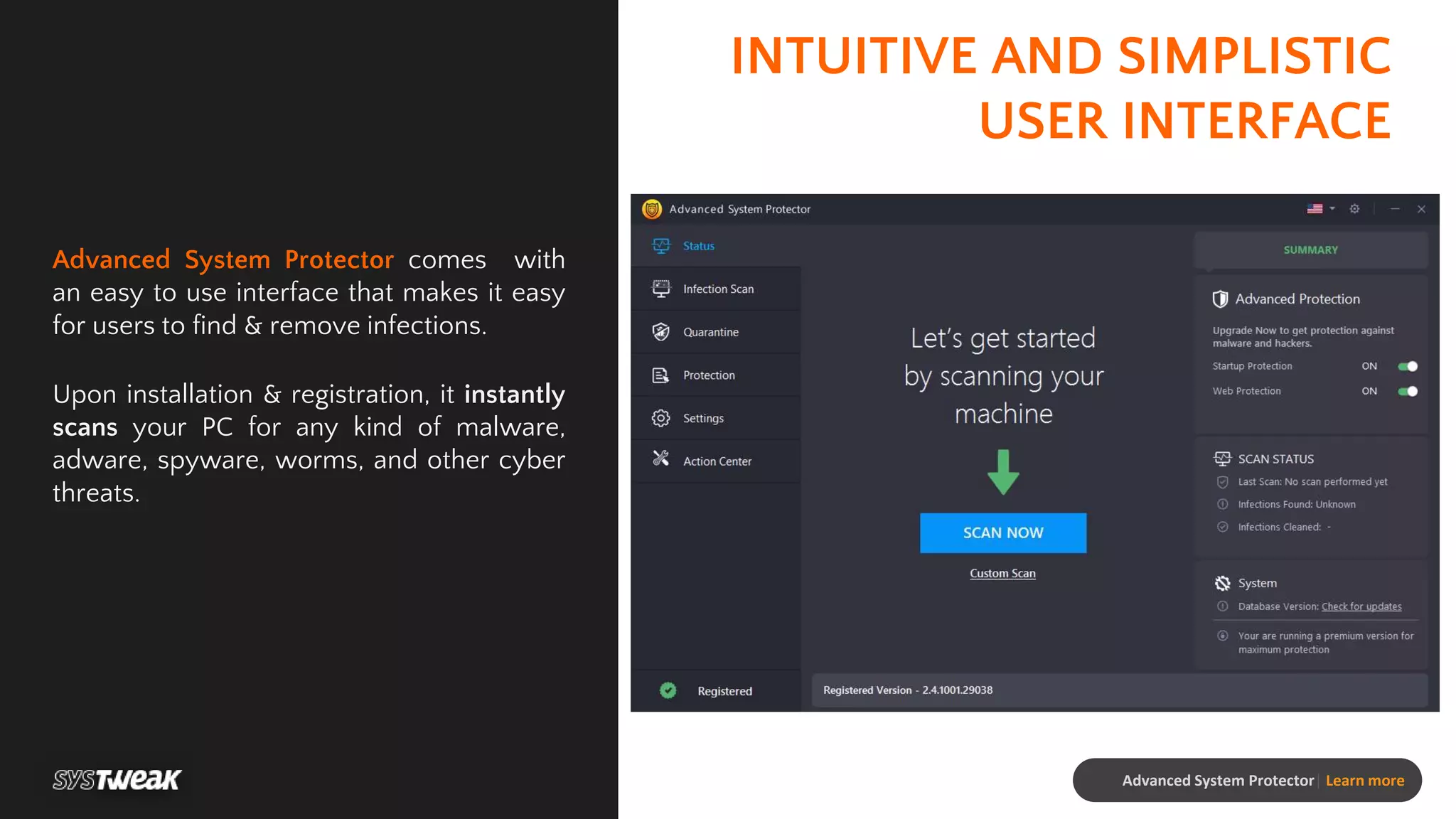
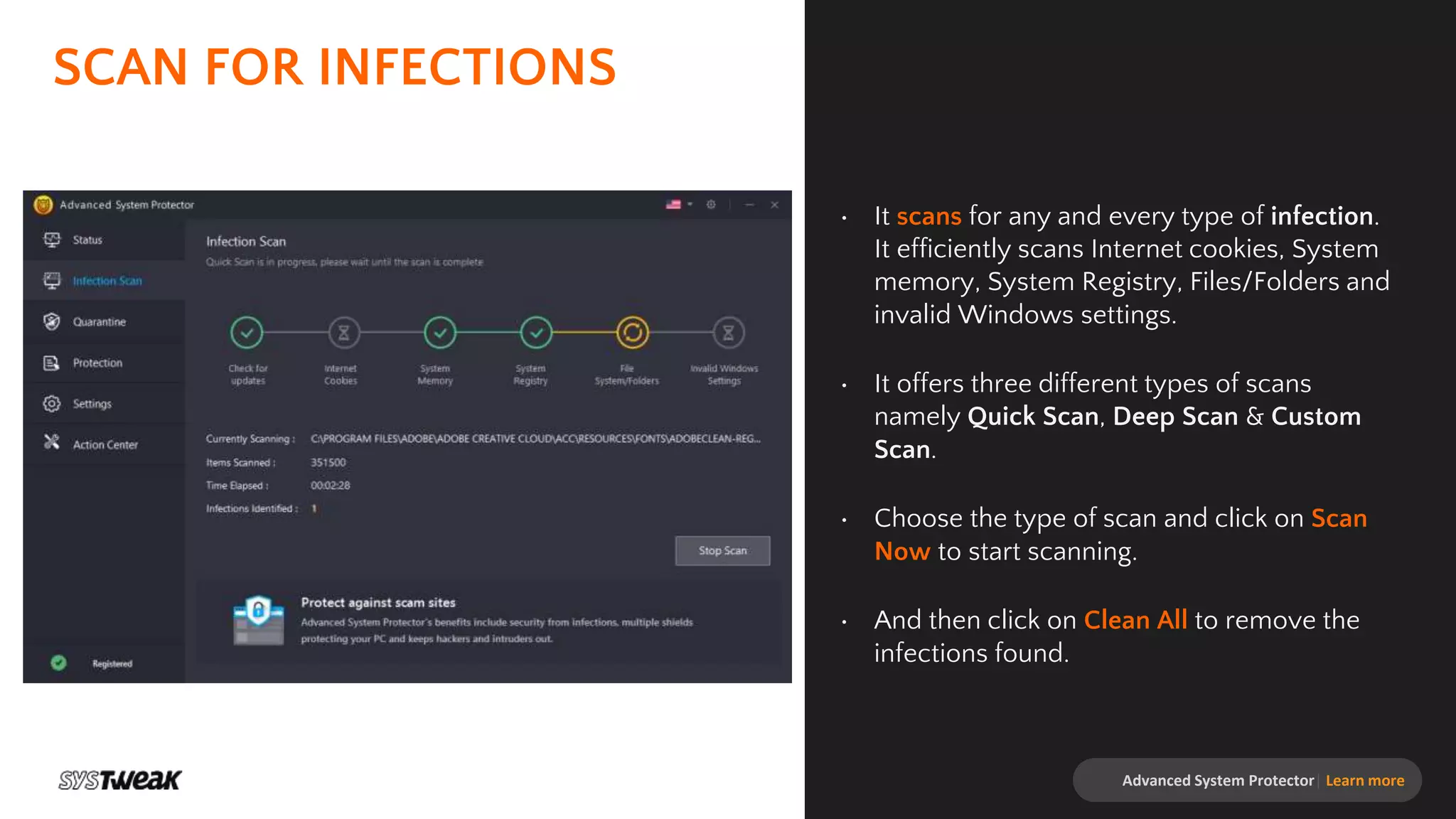
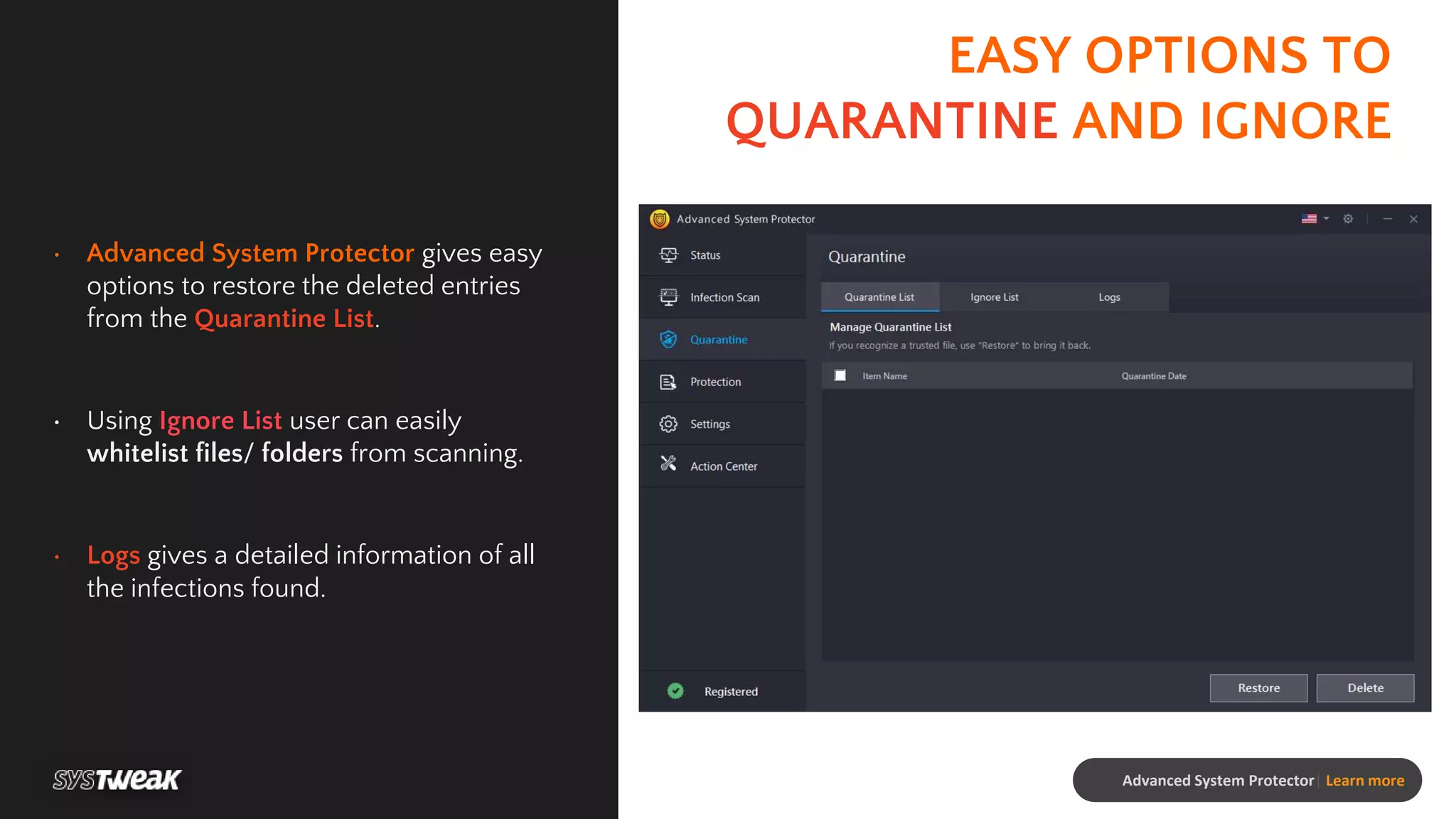
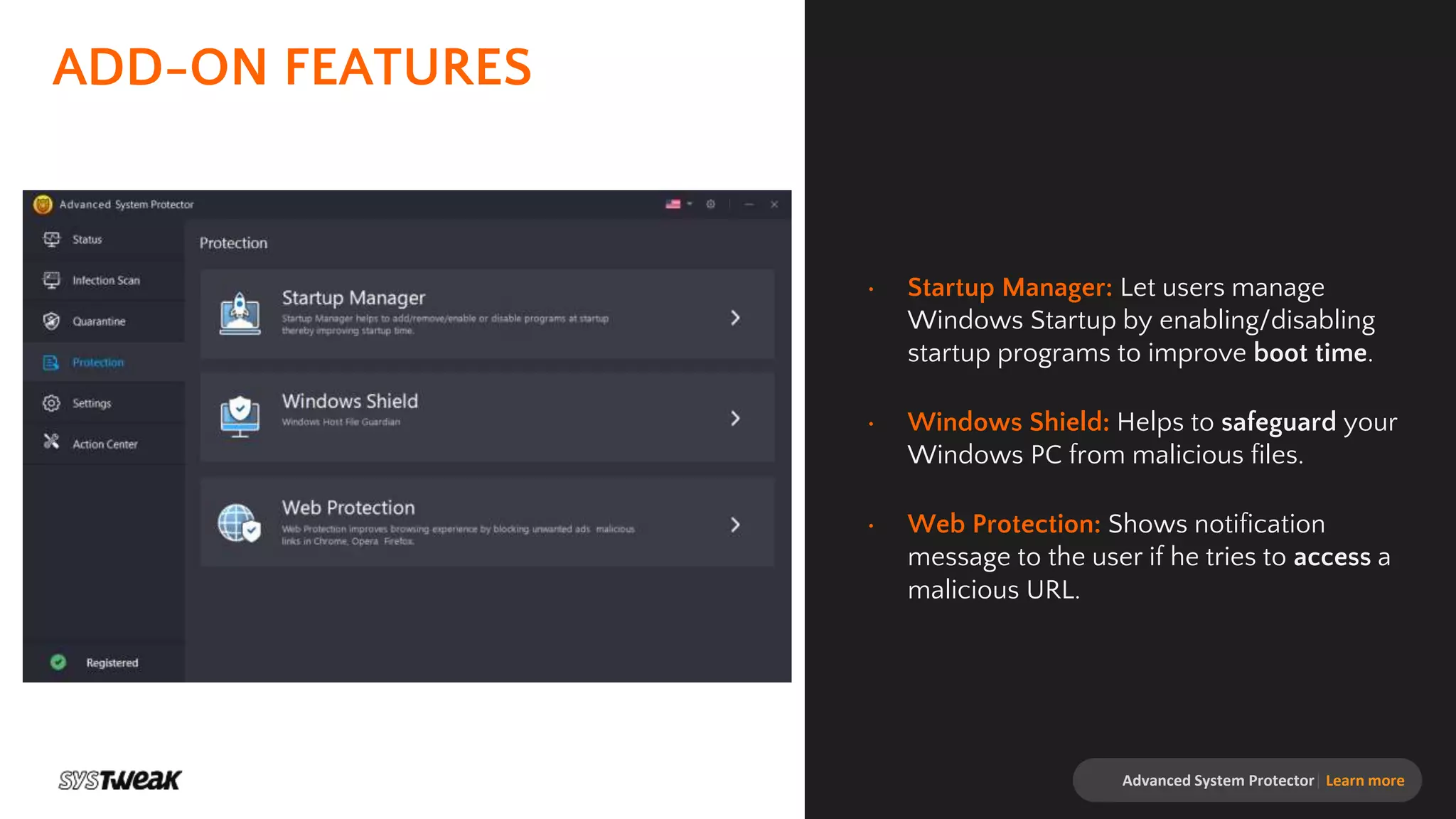
Advanced System Protector is a malware protection tool designed to safeguard PCs from various cyber threats such as viruses, adware, and spyware. It features an advanced scan engine that identifies and removes infections, offers different types of scans, and provides real-time protection against suspicious websites. Additional functionalities include a startup manager and web protection to enhance overall system security.