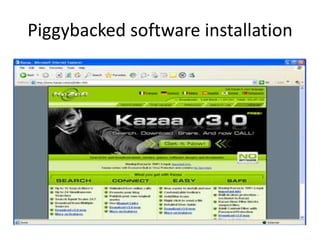
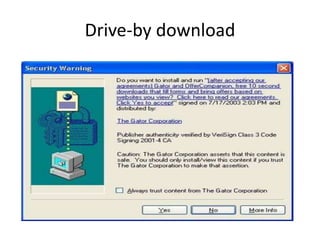
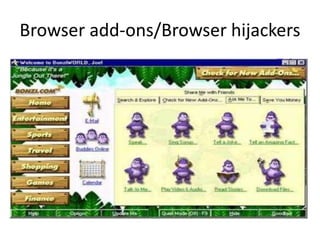
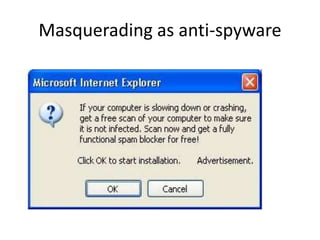
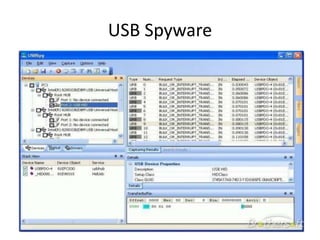
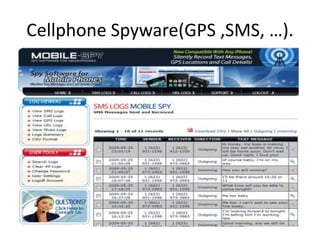
Spyware is software that collects information about a user's activities without their consent. It can gather personal data like internet browsing habits, logins, and financial information. Spyware spreads through piggybacking on other software installations, drive-by downloads, browser hijacking, and browser vulnerabilities. It comes in different forms like domestic, commercial, USB, audio/video, and cellphone spyware. Users can prevent spyware infection by carefully reviewing software agreements, avoiding using uncontrolled systems, updating software, and using firewalls and safe browsing/downloading practices.