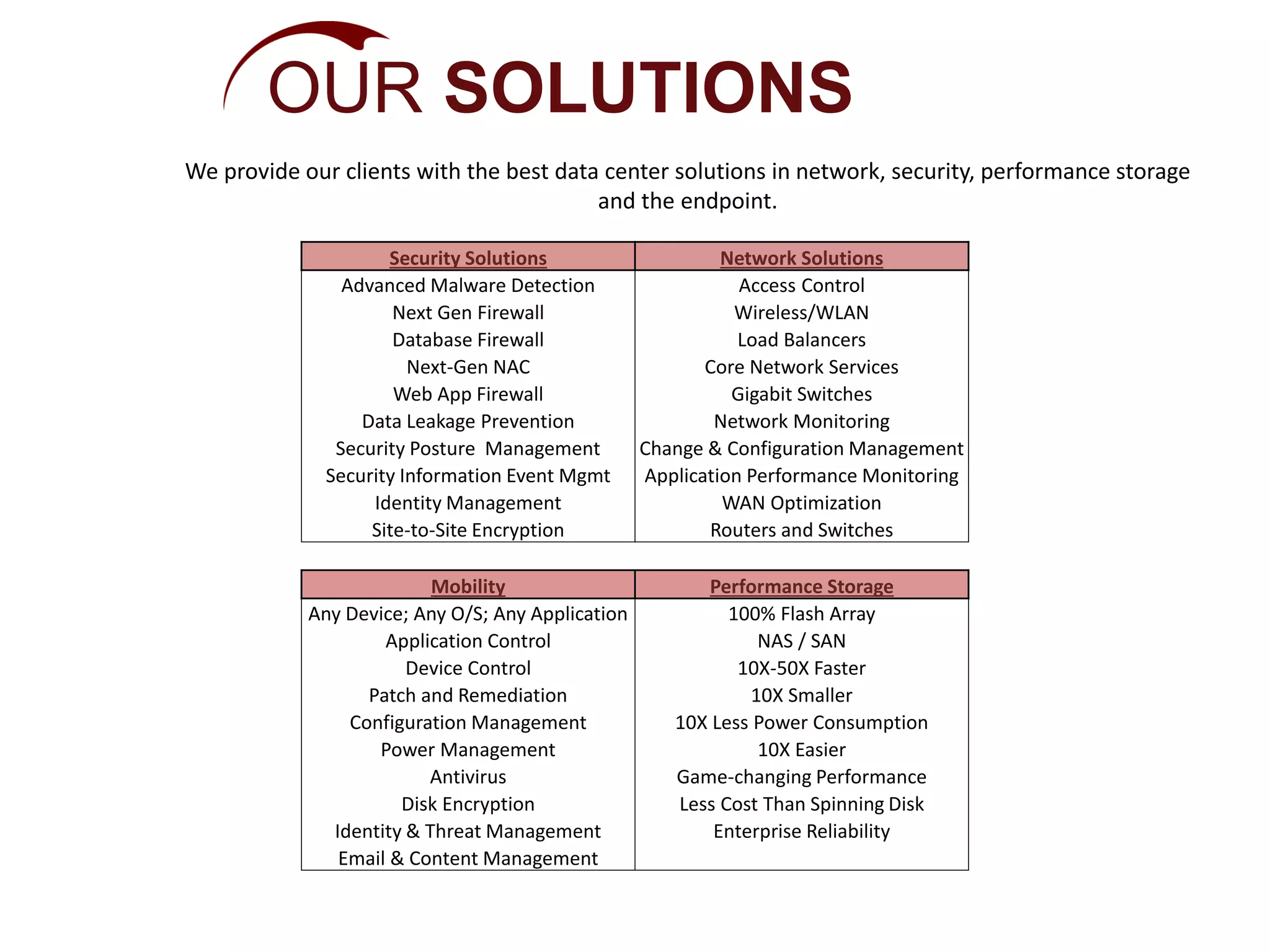
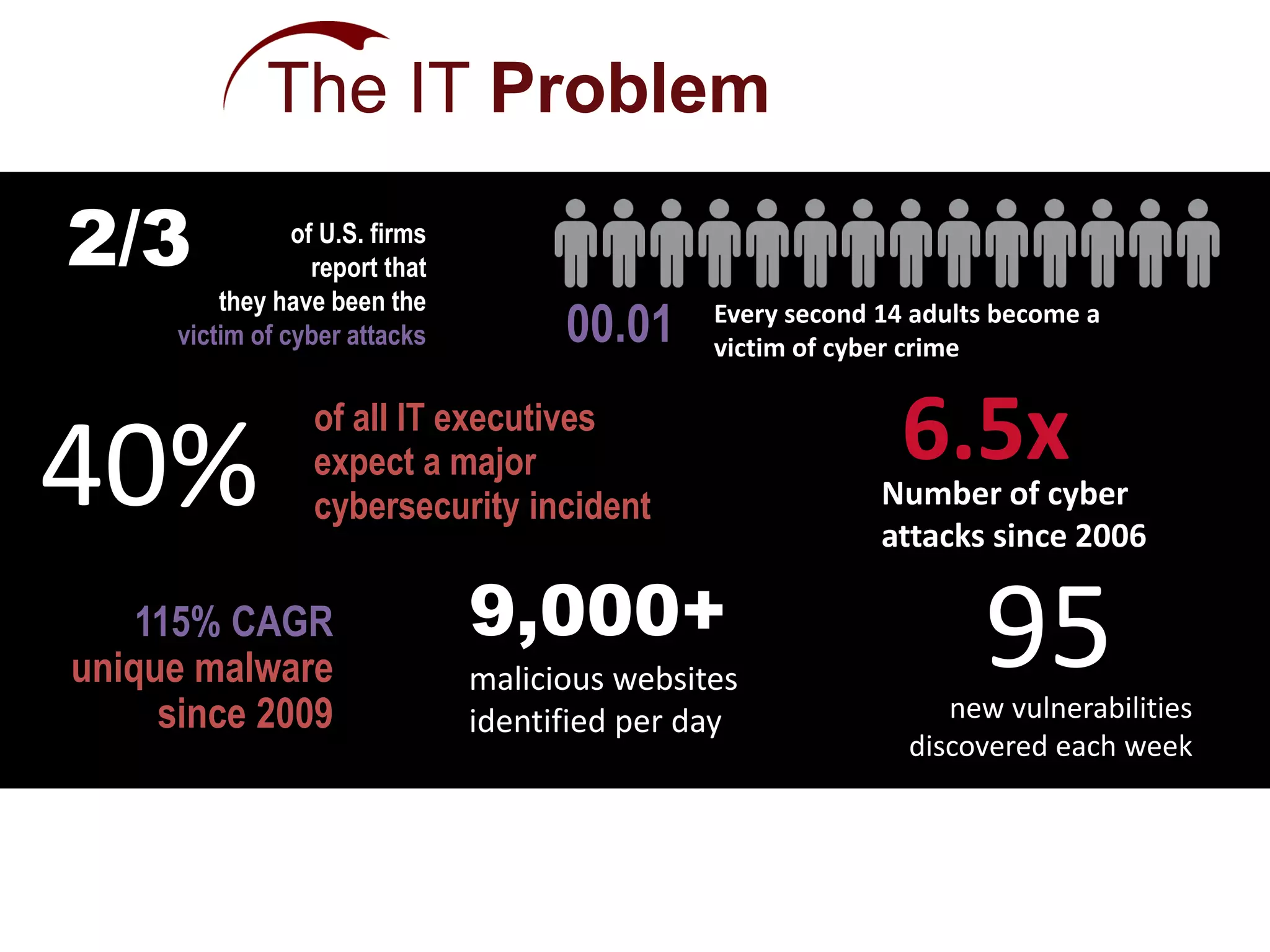
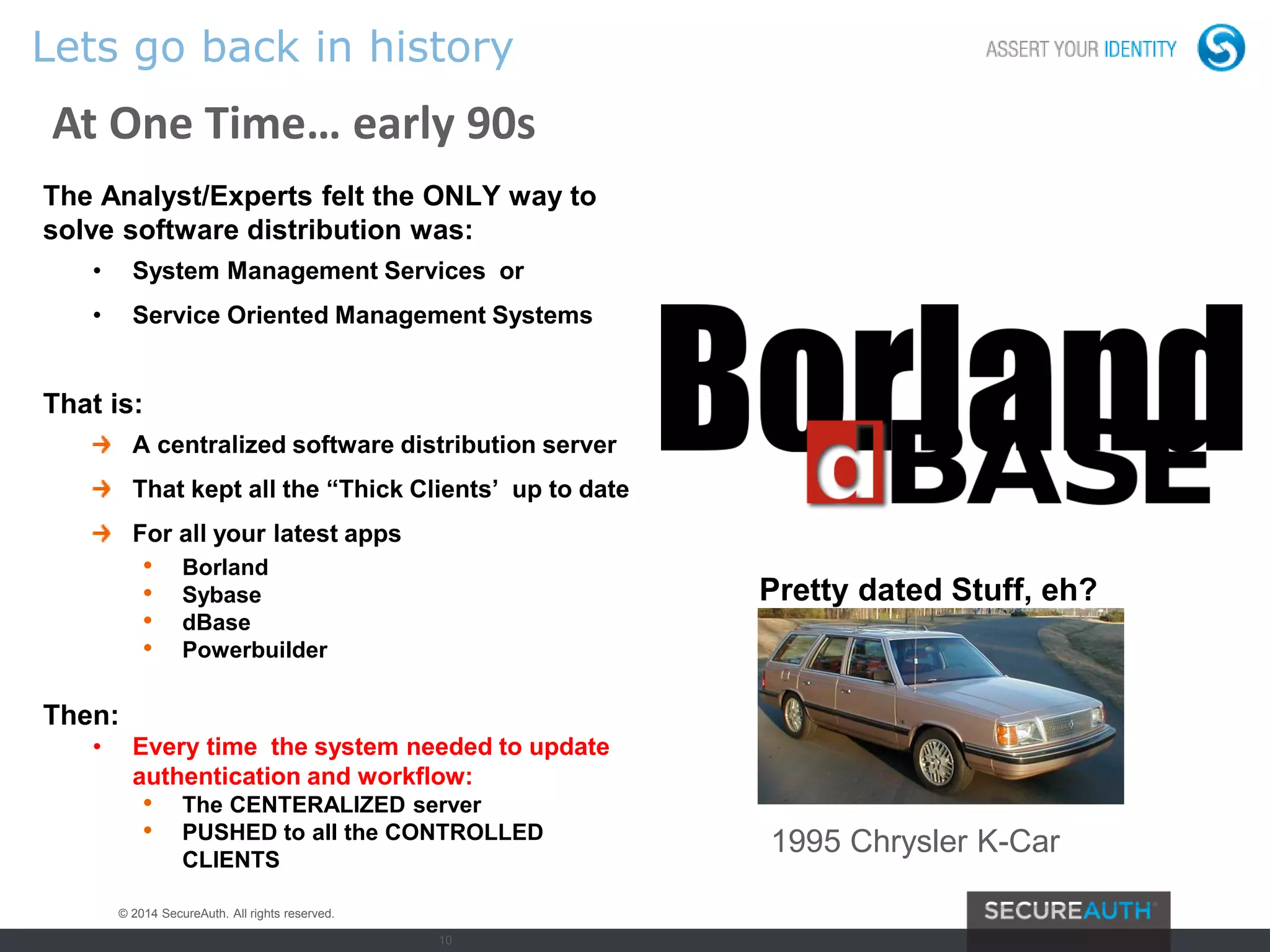
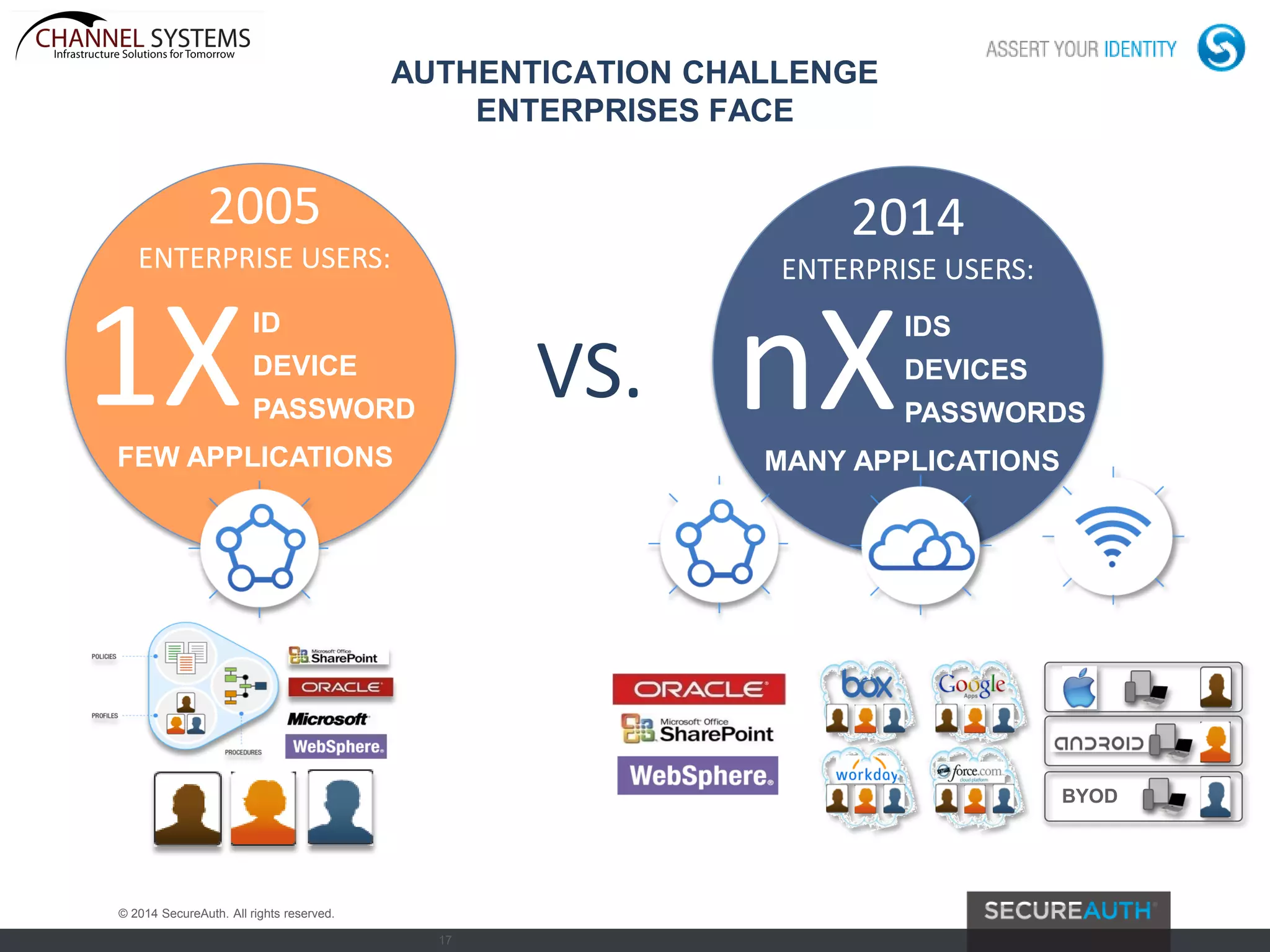
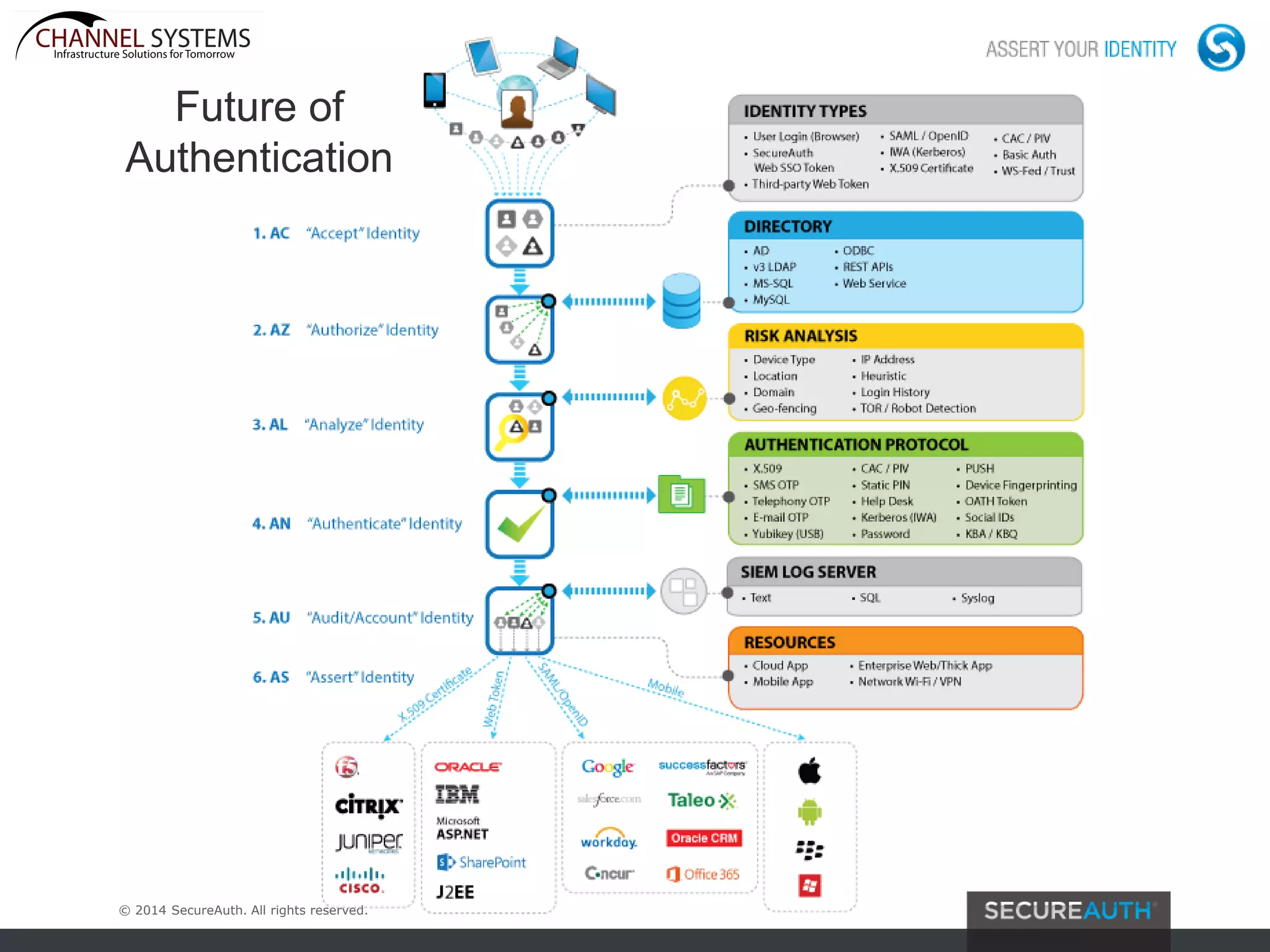
The document discusses the evolving landscape of authentication and cybersecurity, highlighting the need for advanced solutions to address increasing threats such as dynamic malware and multi-vector attacks. It outlines the transition from traditional software update methods to more modern, server-controlled clientless solutions, while emphasizing the challenges of integration and user management. The content also touches on future developments in authentication, including risk analysis and cloud-hosted data services.