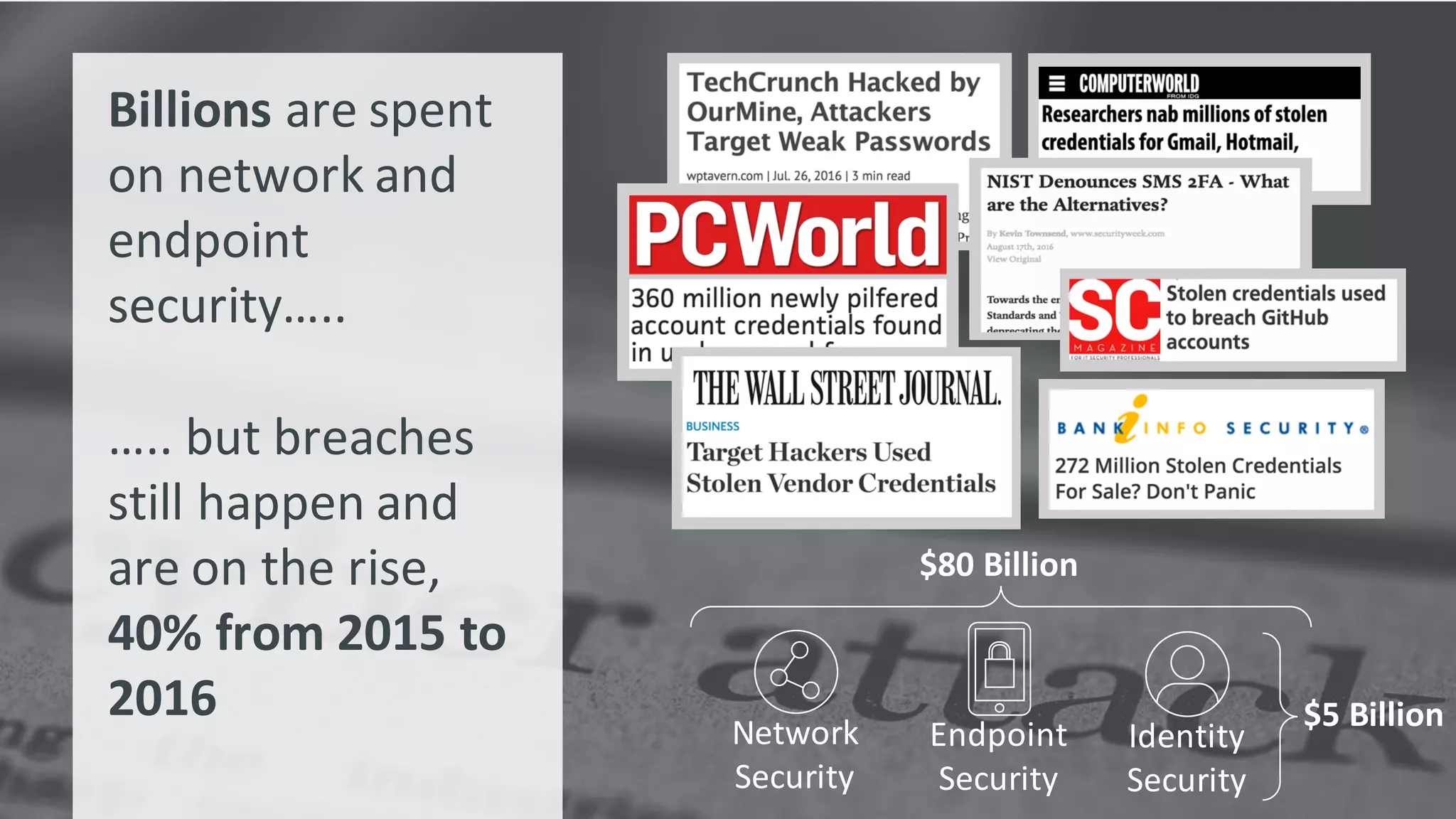
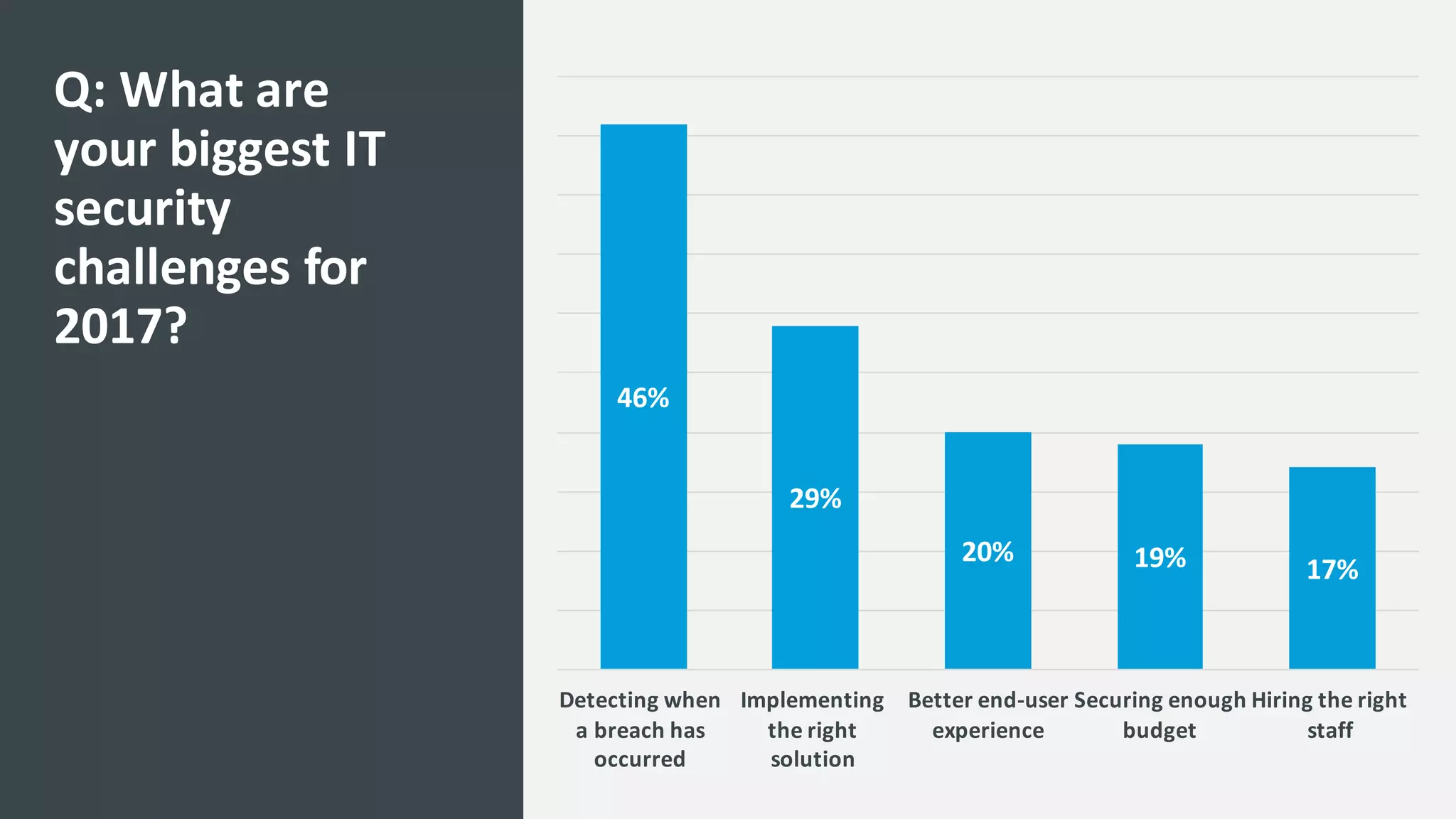
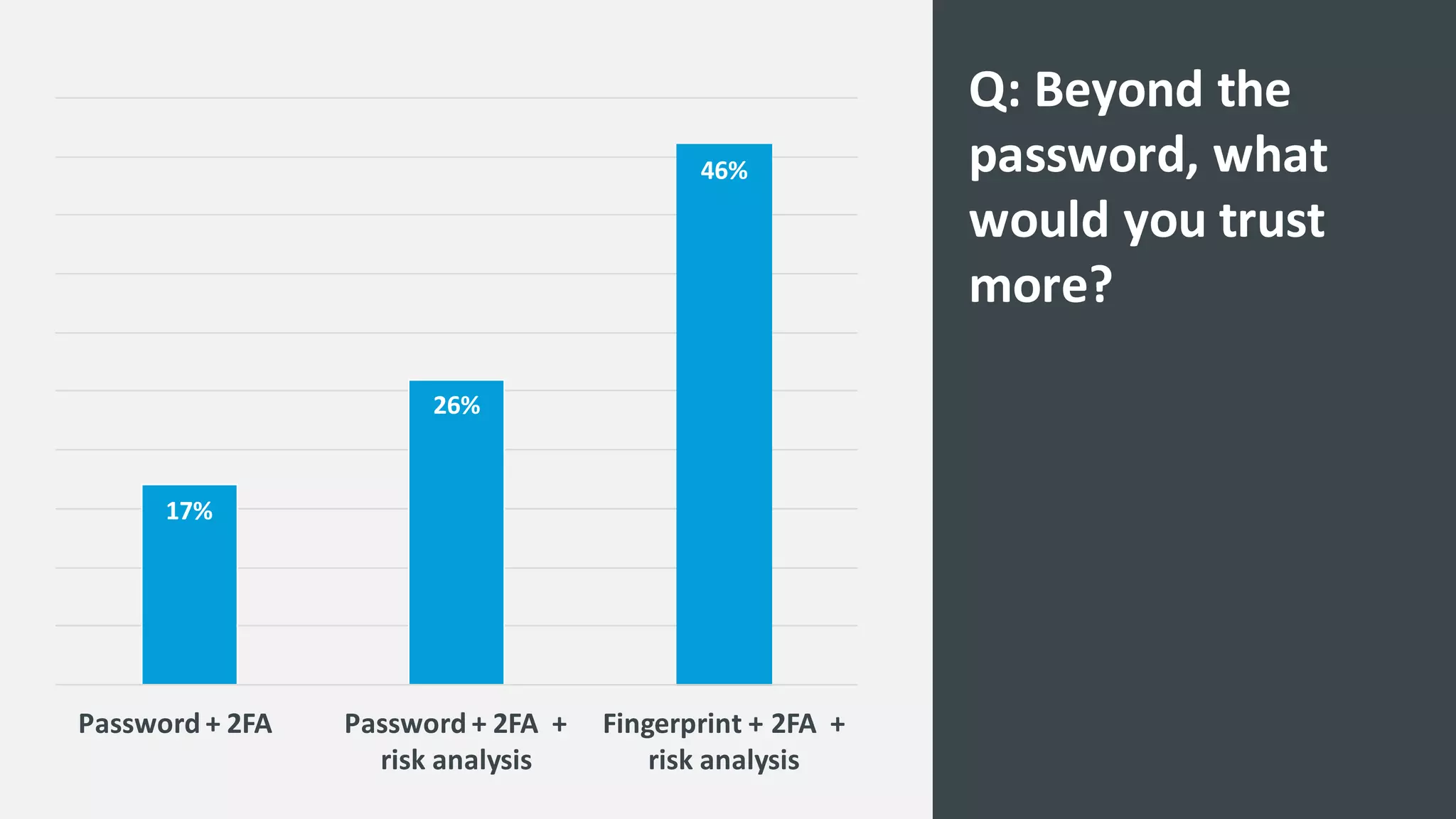
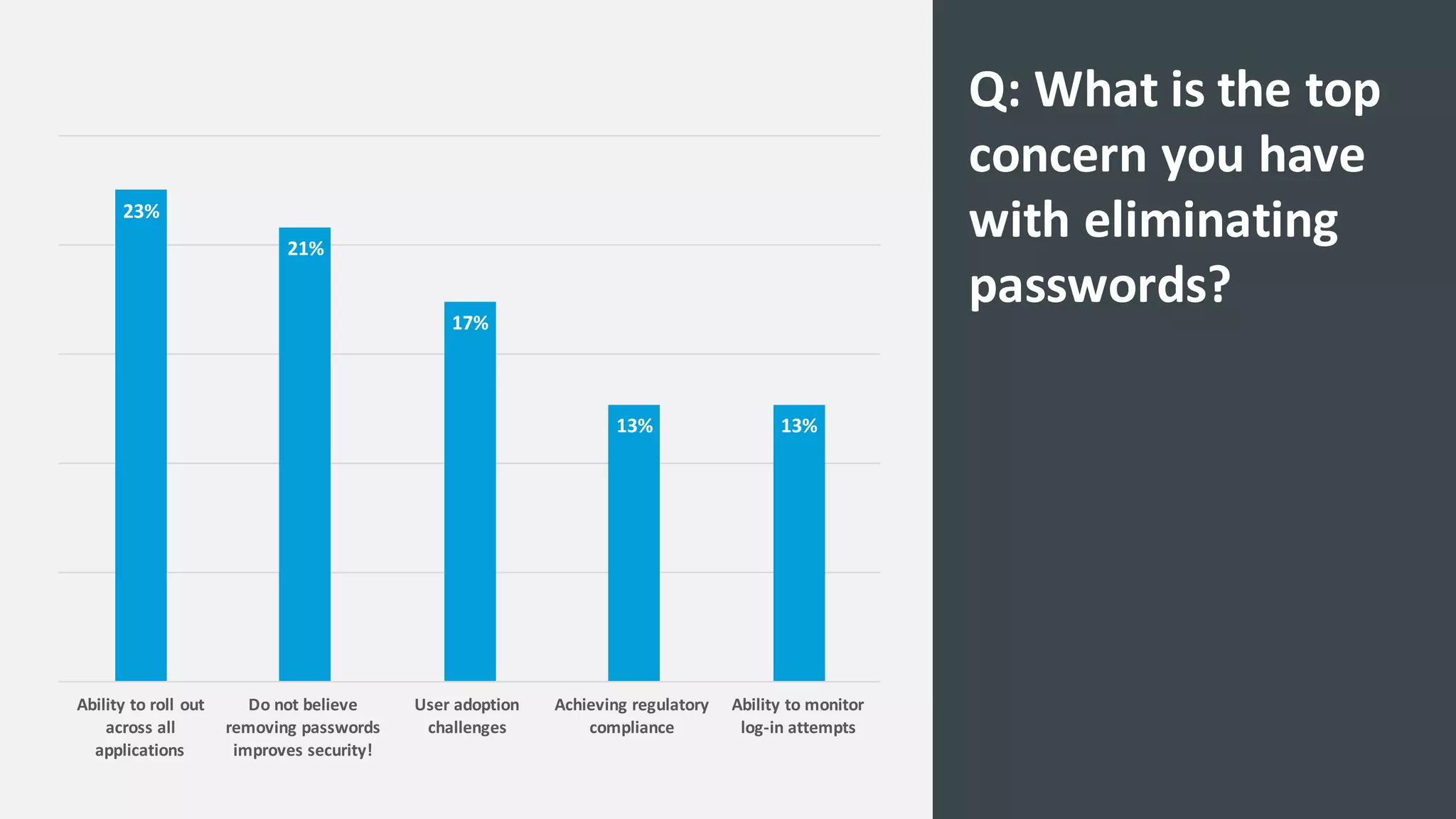
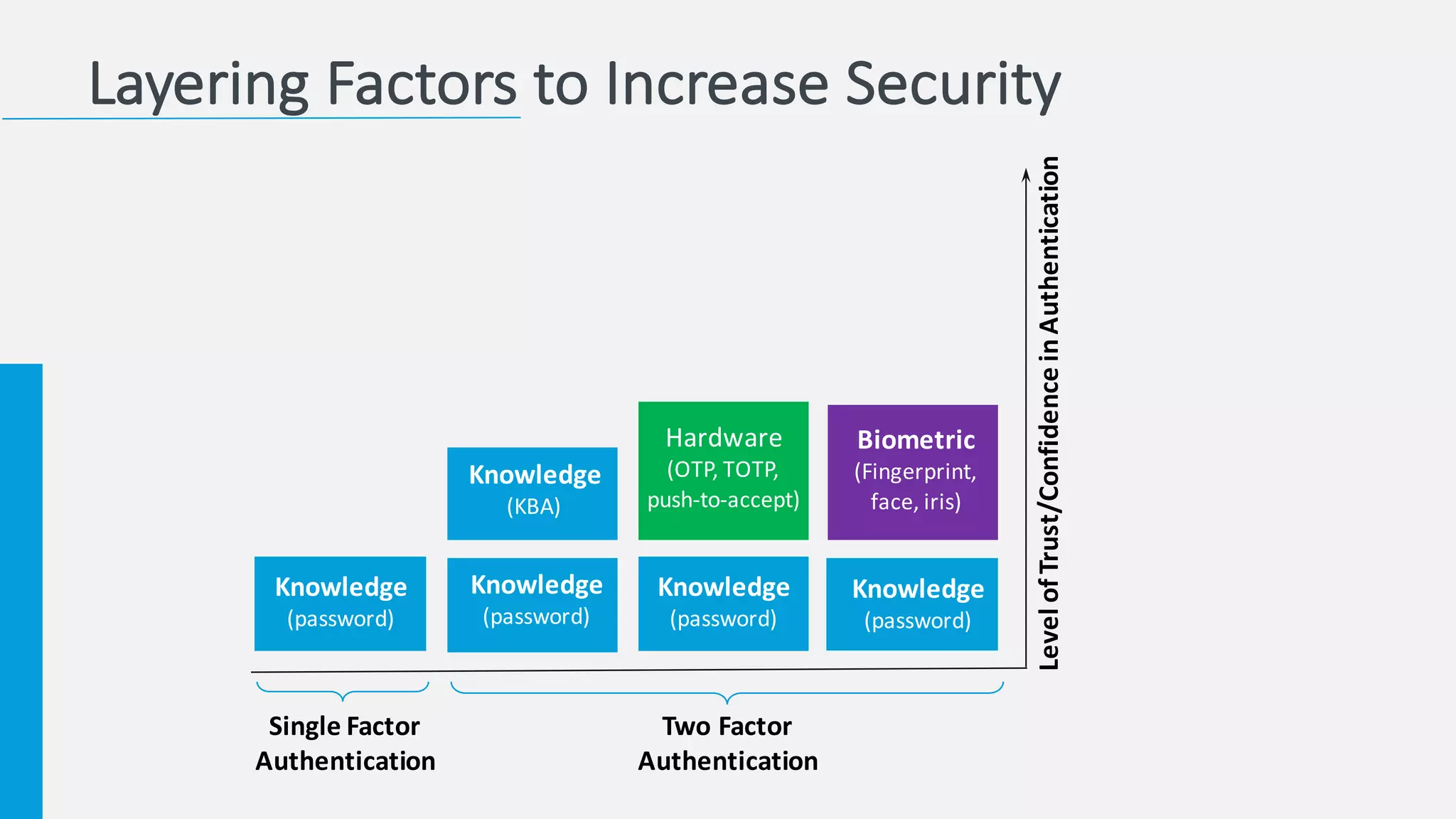
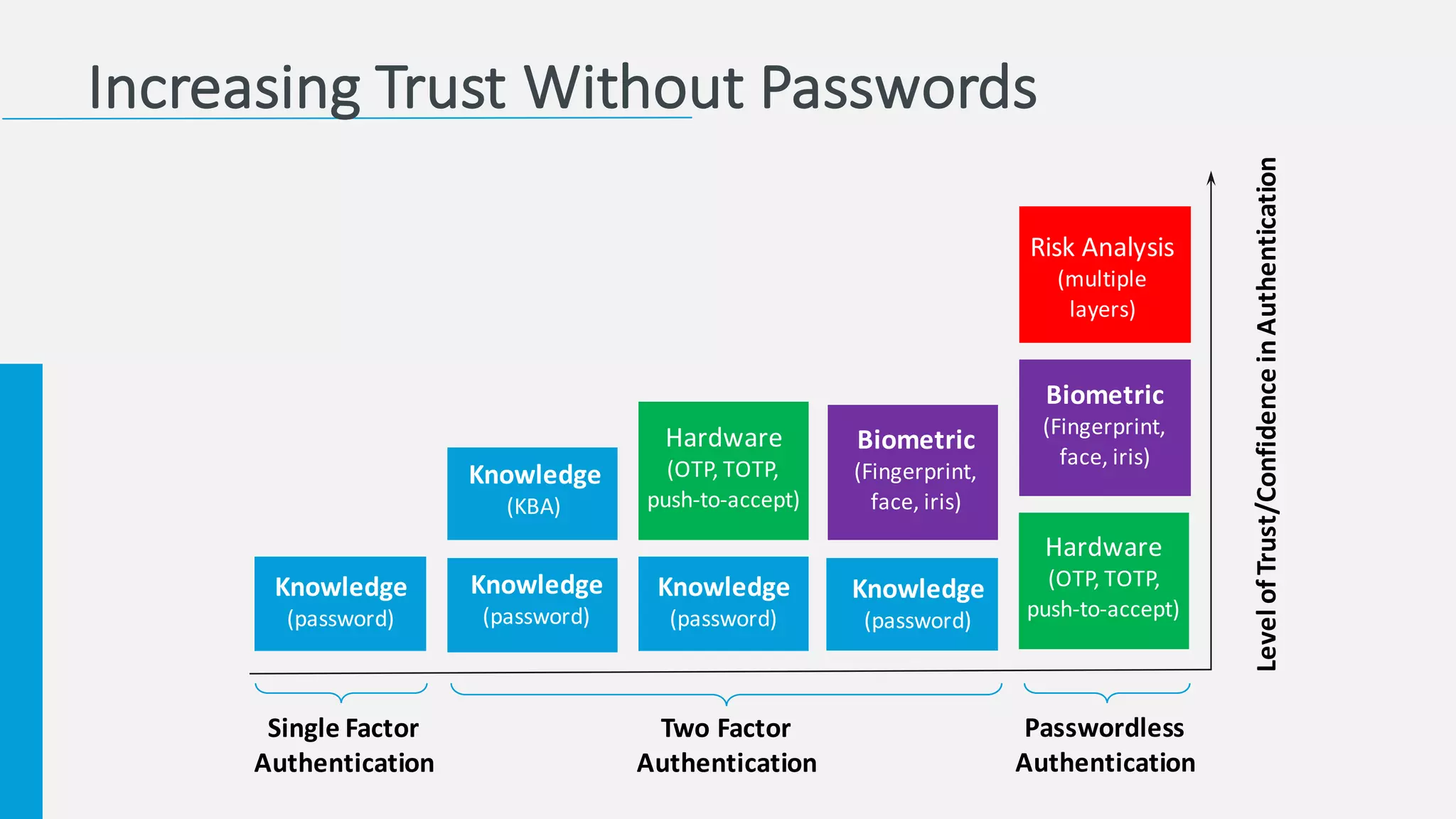
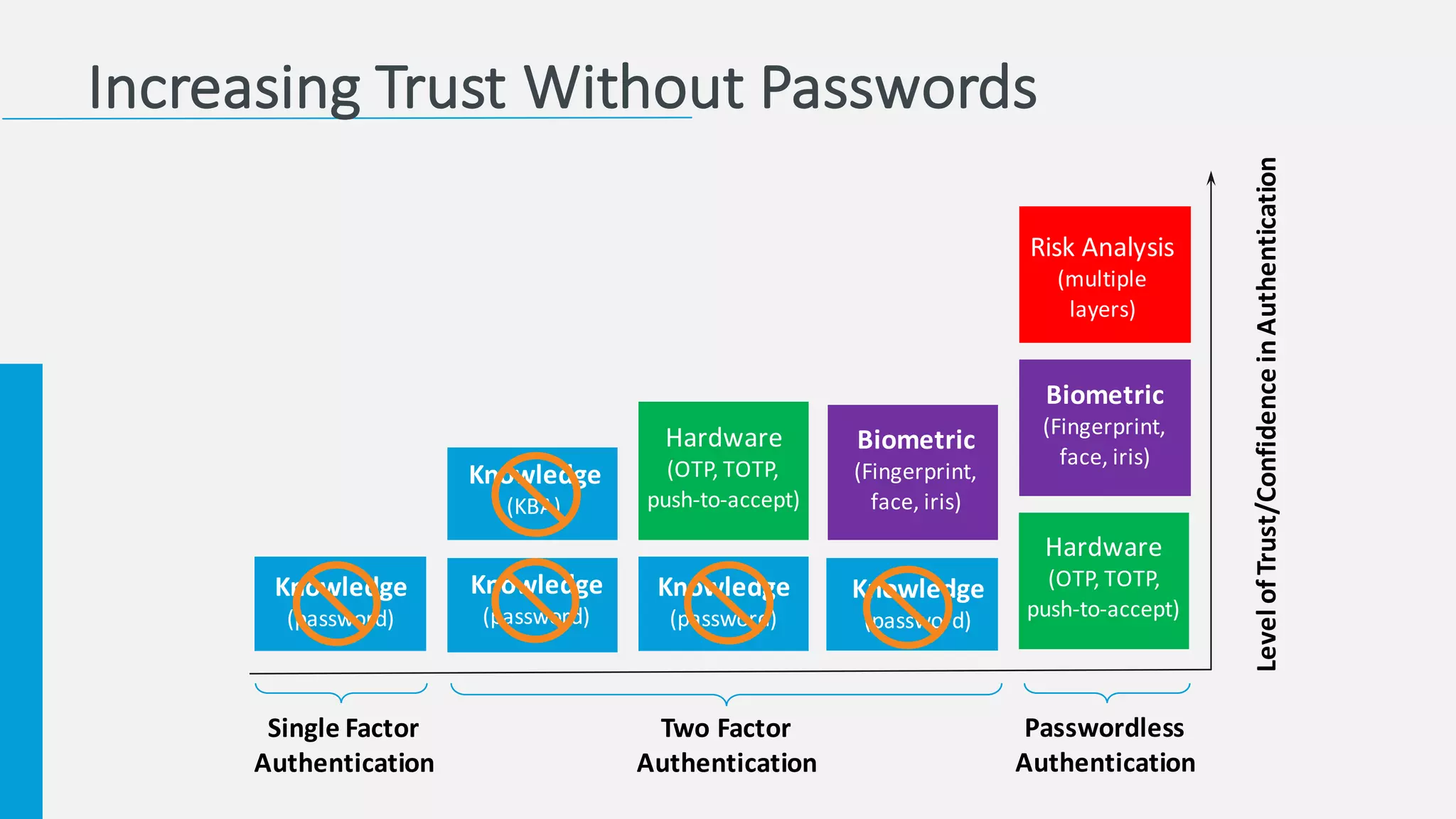
The document discusses the increasing challenges associated with password security, highlighting that 81% of breaches involved stolen credentials. It presents survey results indicating a growing interest in passwordless authentication solutions, with 57% believing this can enhance security and user experience. The document emphasizes the importance of implementing layered security measures, such as biometric authentication and two-factor authentication, to reduce risk and improve identity confidence.