1. The document analyzes the risks of using SMS-based two-factor authentication for user authentication and transaction authentication.
2. It outlines threats including eavesdropping, man-in-the-middle attacks, SMS delays and losses, lack of coverage, and increasing costs.
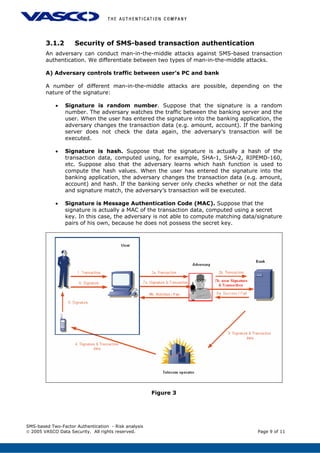
3. The document recommends using message authentication codes instead of random numbers or hashes for signatures to protect against attacks. It also suggests verifying transaction data is unchanged when signatures are submitted.