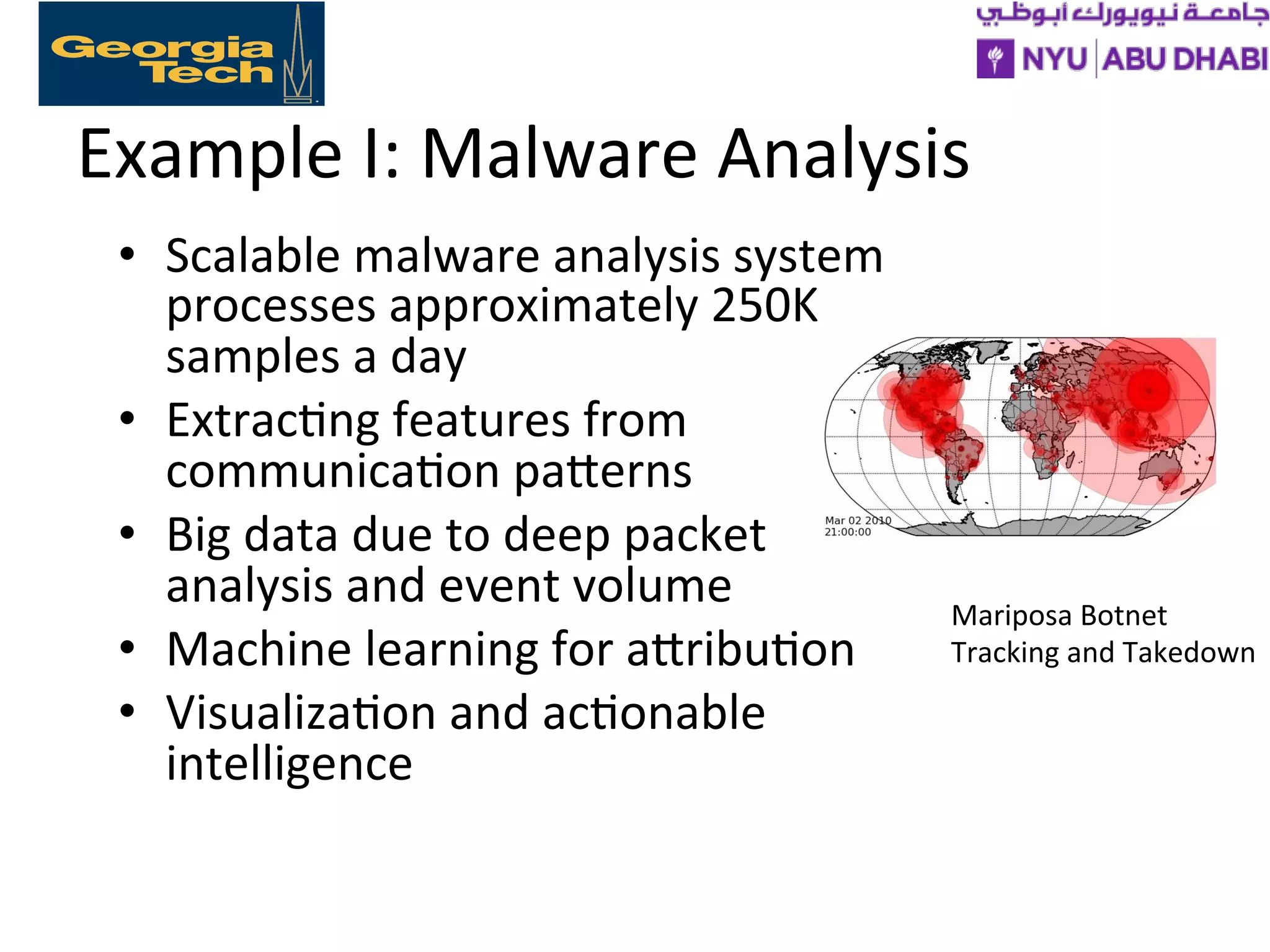
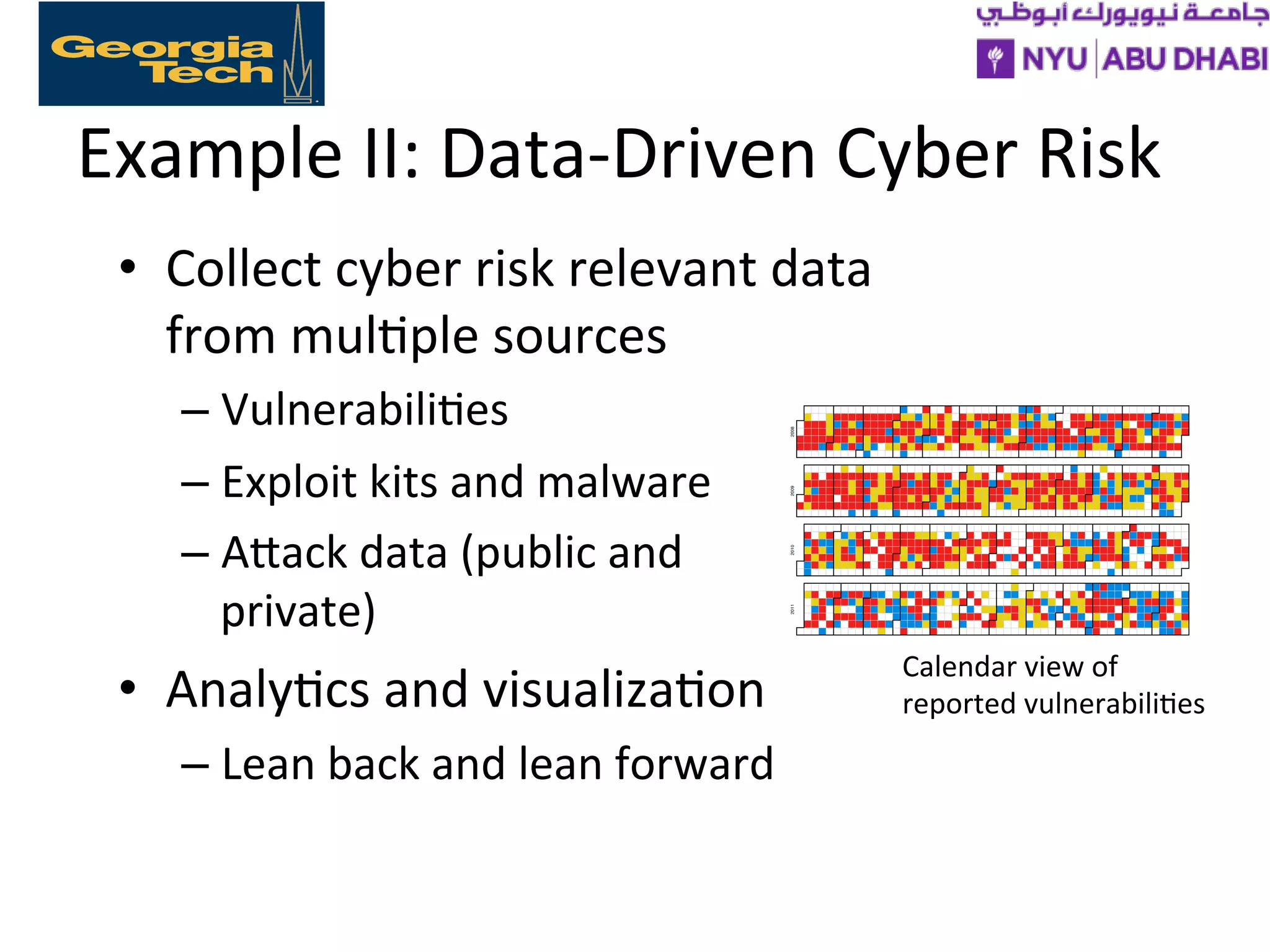
The document discusses the growing challenges of cybersecurity faced by individuals, businesses, and governments, emphasizing the complexity of the threat landscape, including cyber crimes costing significant financial losses. It outlines strategies to address these challenges through education, research, policy development, and collaboration among various stakeholders to enhance cybersecurity readiness. The importance of building capacity, supporting cybersecurity education and research, and integrating security into existing curricula is highlighted as essential for a robust national response to cyber threats.