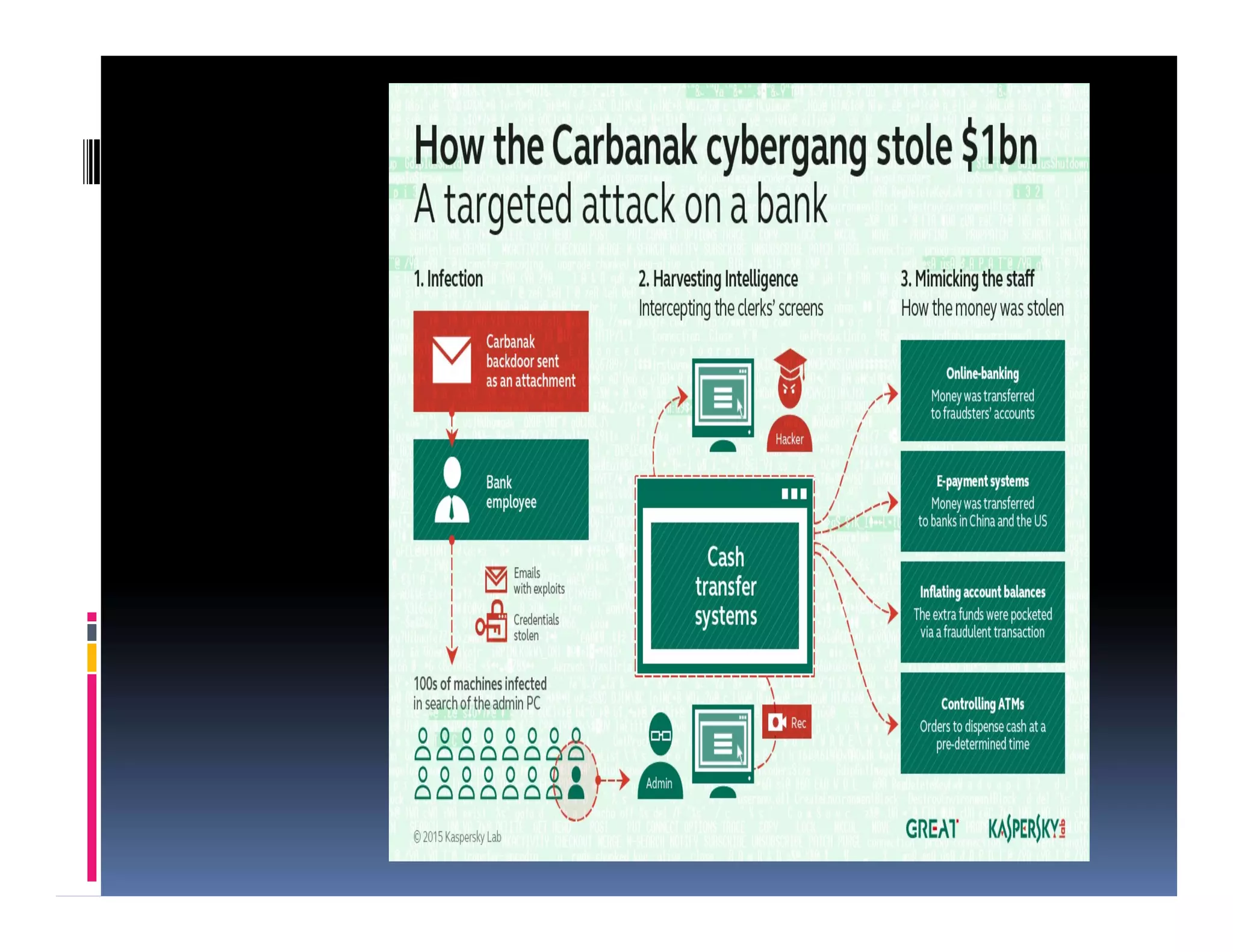
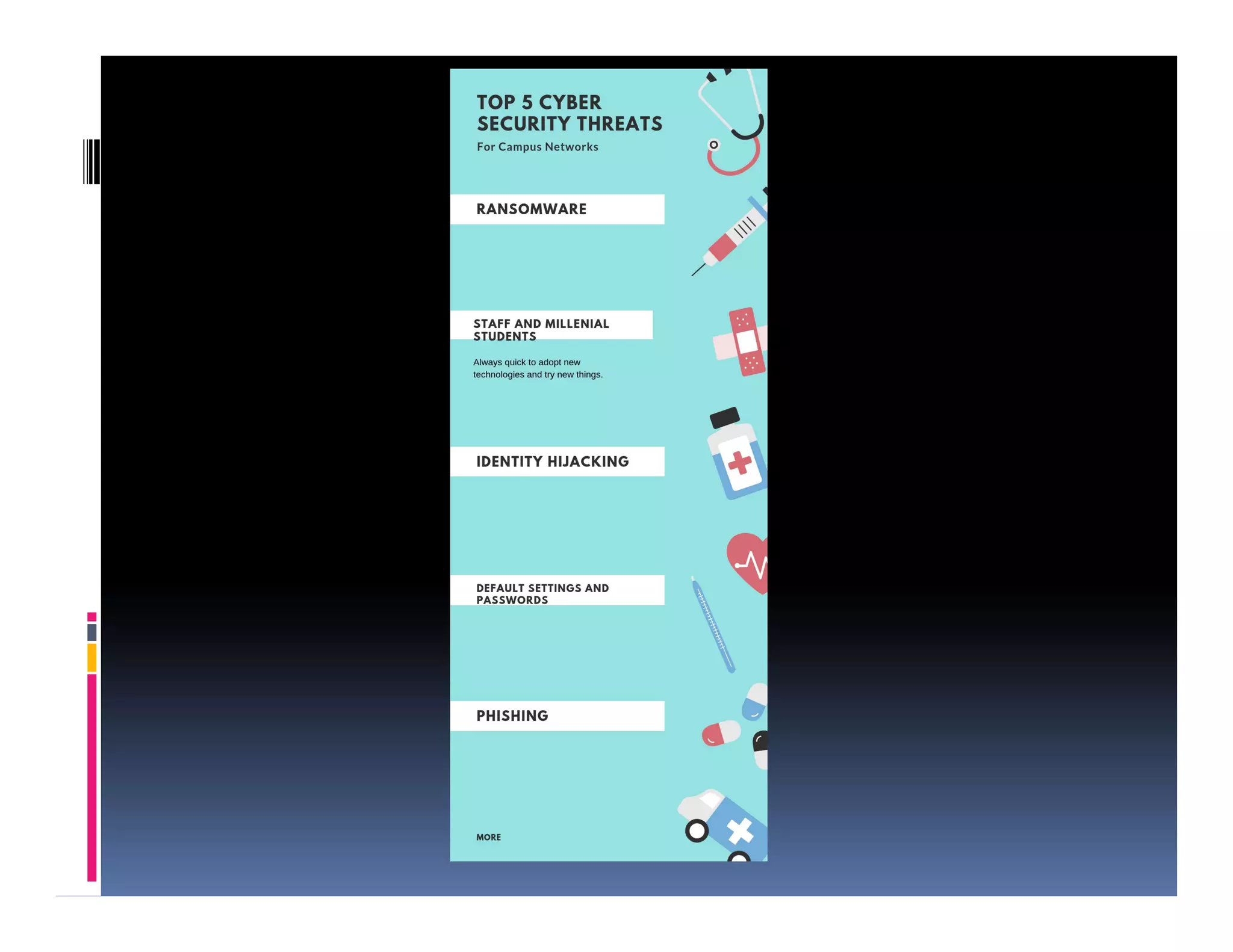
The presentation by Morakinyo Animasaun of NetPlus Ltd discusses the evolving threat of cybercrime, emphasizing its organization and economic impact, particularly in Nigeria. It advocates for the necessity of preparedness against attacks, highlighting the need for proactive measures, incident management, and comprehensive awareness among organizations. The document outlines strategies for enhancing cybersecurity capabilities through visibility, awareness, and response, urging business leaders to take ownership of cyber risks.