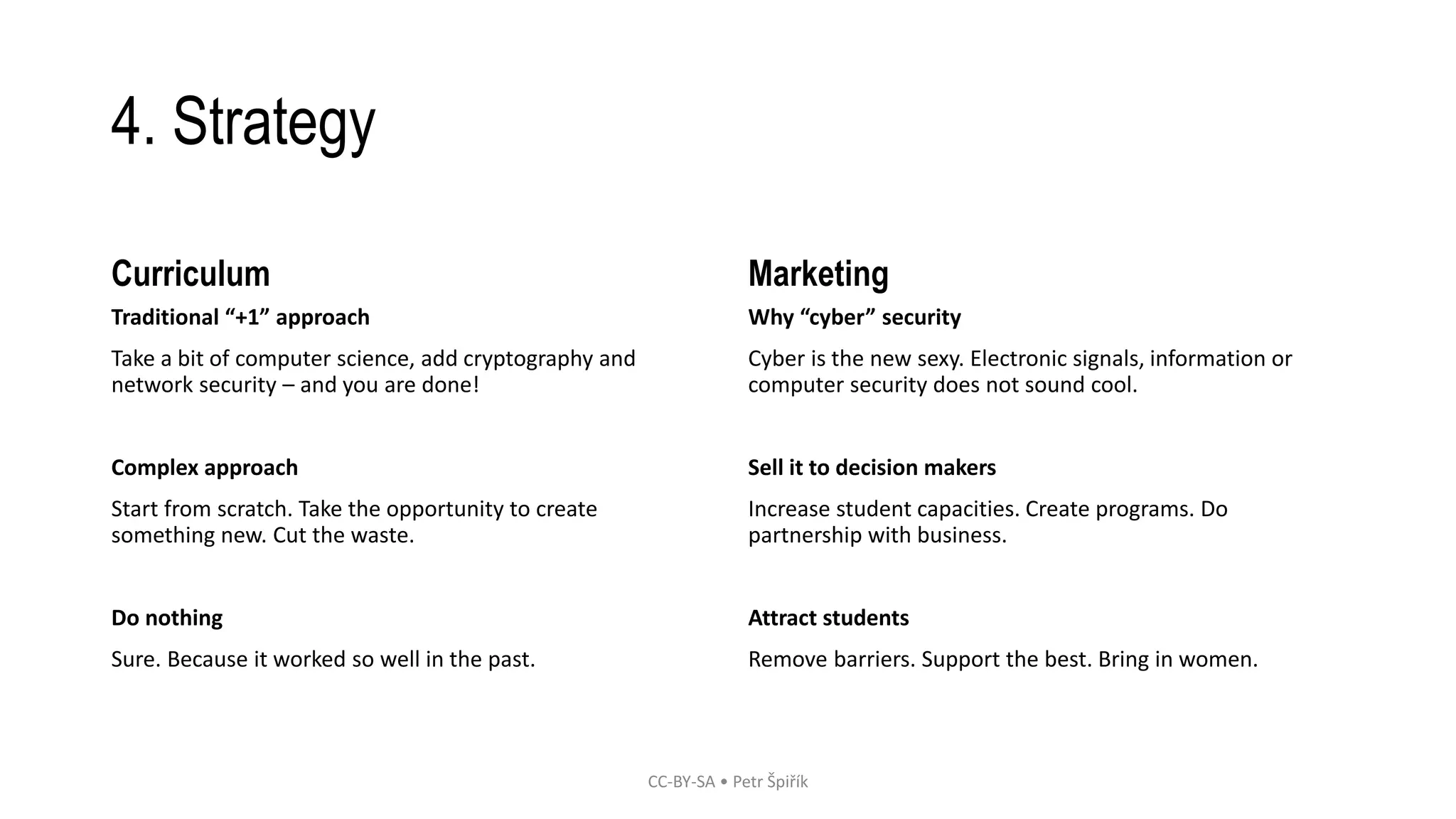
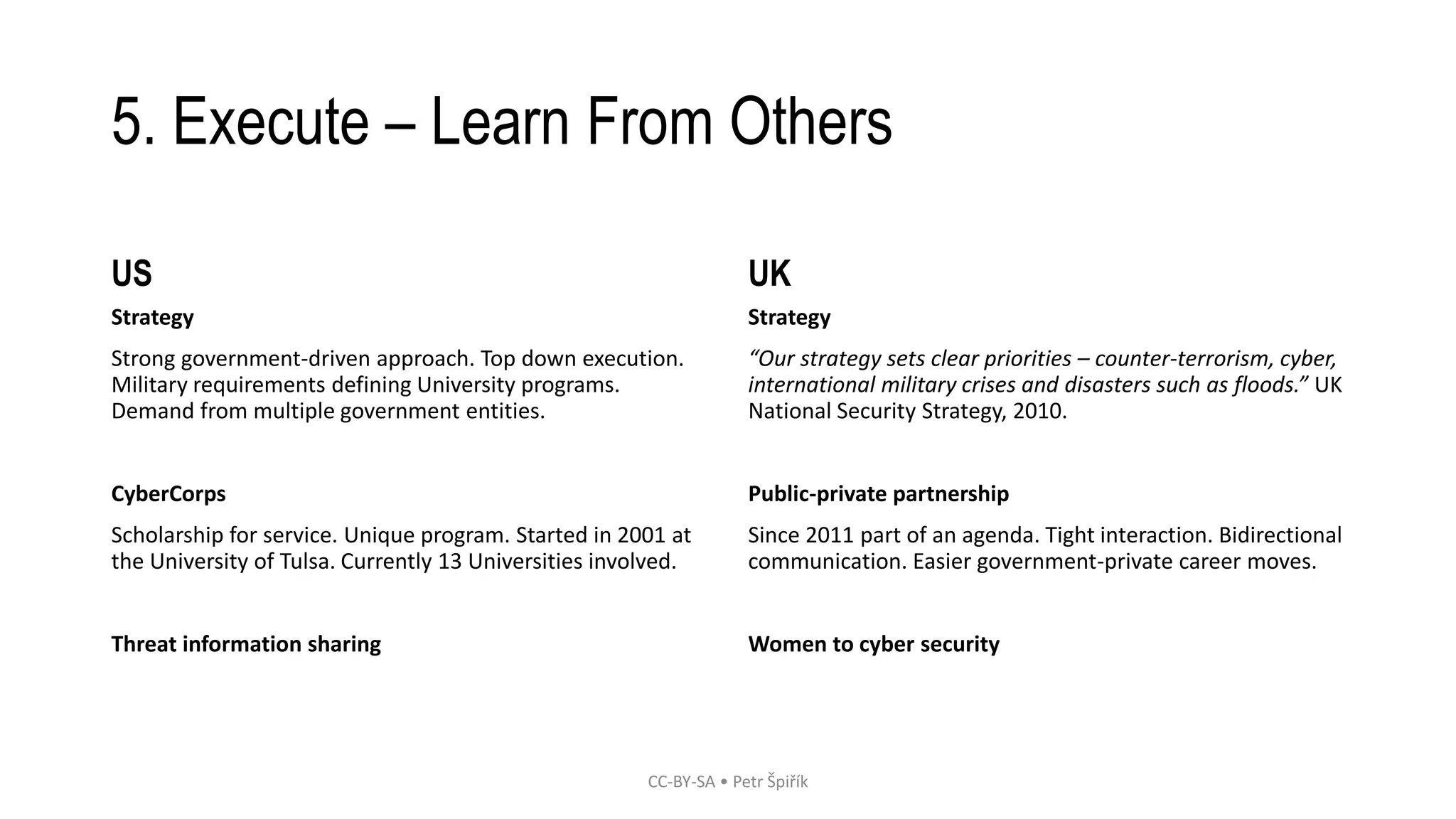
This document outlines a proposed solution to address the shortage of cybersecurity experts through education. It identifies the problem of not enough cybersecurity professionals to meet demand. The solution involves defining objectives like attracting more people to the field, and developing a strategy that includes creating new university cybersecurity programs, marketing cybersecurity as an appealing career, and learning from other countries' approaches to grow their cybersecurity workforce through public-private partnerships and scholarship programs. The strategy would aim to develop a complex curriculum approach to cybersecurity education from the ground up rather than just adding it onto existing computer science programs.