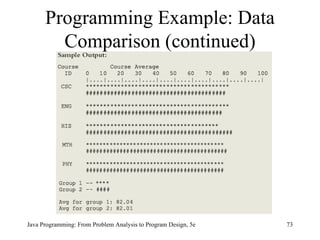
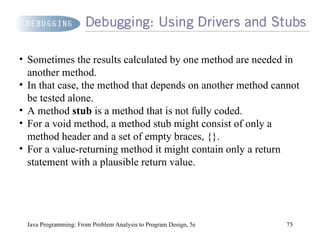
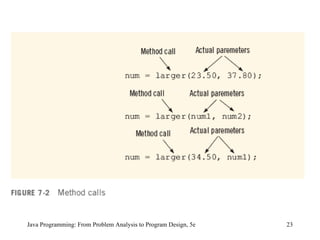
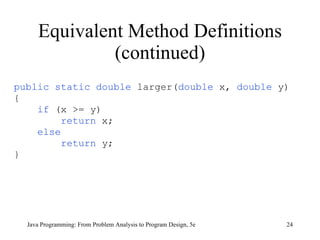
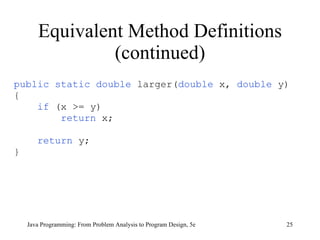
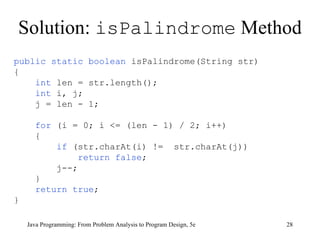
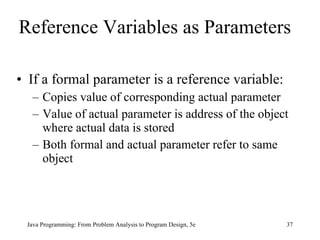
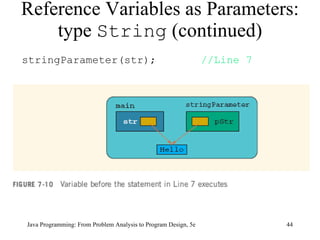
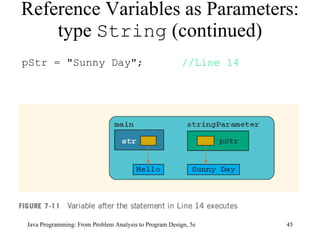
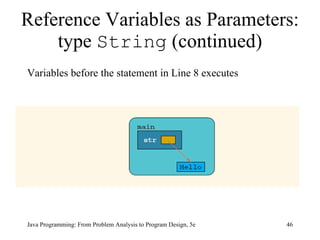
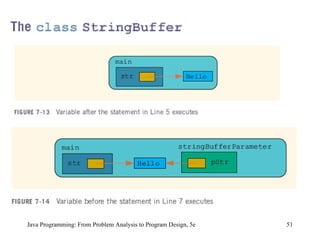
The document discusses user-defined methods in Java programming. It covers key concepts like value-returning and void methods, parameters, scope of identifiers, and method overloading. Examples are provided to illustrate how to define and call methods to perform tasks like finding the largest number in a data set. Reference variables can be used as parameters to allow methods to modify the values of objects in the caller's scope.




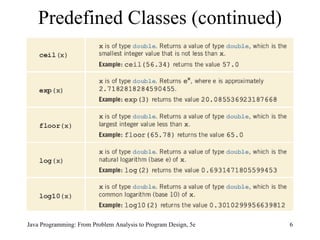
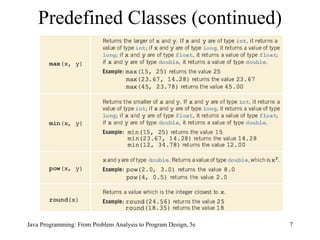
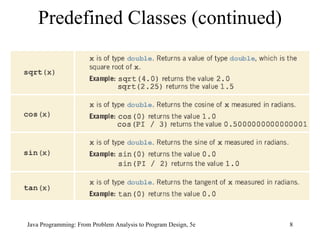
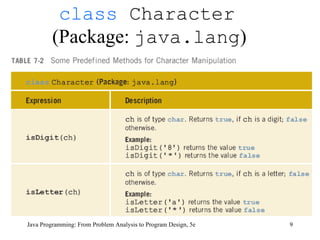









![Solution: Largest Number Java Programming: From Problem Analysis to Program Design, 5e static Scanner console = new Scanner(System.in); public static void main(String[] args) { double num; double max; int count; System.out.println("Enter 10 numbers."); num = console.nextDouble(); max = num; for (count = 1; count < 10; count++) { num = console.nextDouble(); max = larger(max, num); } System.out.println("The largest number is " + max); }](https://image.slidesharecdn.com/9781111530532pptch07-111003182017-phpapp01/85/9781111530532-ppt-ch07-31-320.jpg)


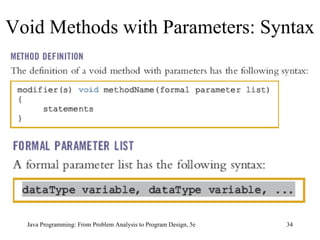
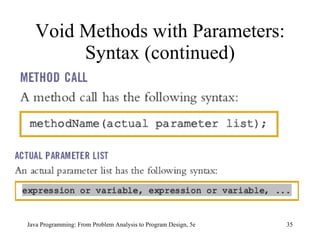

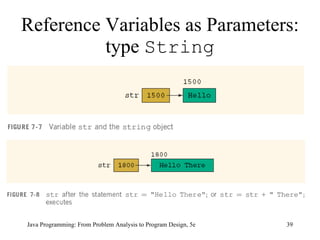
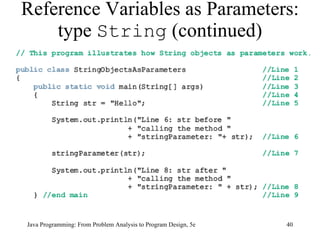
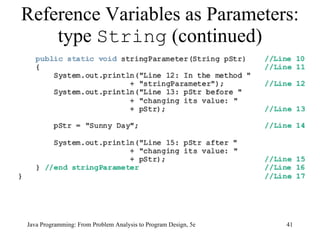

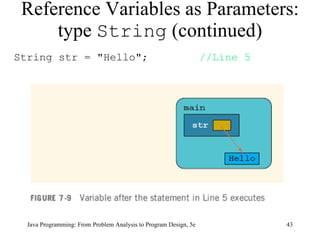




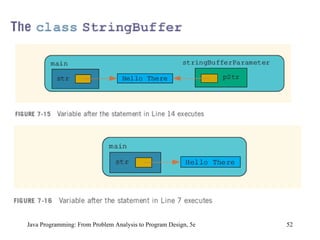




![Example 7-11 public class ScopeRules { static final double rate = 10.50; static int z; static double t; public static void main(String[] args) { int num; double x, z; char ch; //... } public static void one( int x, char y) { //... } Scope Rules (continued) Java Programming: From Problem Analysis to Program Design, 5e](https://image.slidesharecdn.com/9781111530532pptch07-111003182017-phpapp01/85/9781111530532-ppt-ch07-61-320.jpg)