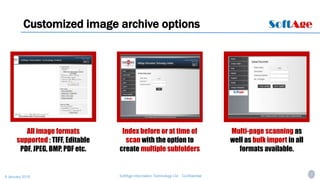
The document introduces CloudDocu, a cloud-based document management system created by SoftAge Information Technology Ltd. to provide secure, cost-effective, and easy access to documents. It describes current challenges with using email and hard drives for document storage, which causes inefficiency, security risks, and limited collaboration. CloudDocu offers features like strong security with password authentication and activity auditing, flexible indexing and searching options, support for various file formats, and easy integration into existing workflows. It also provides on-request client access licenses and value-added services like document archiving and support.