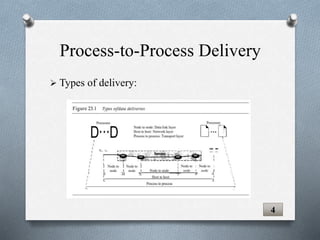
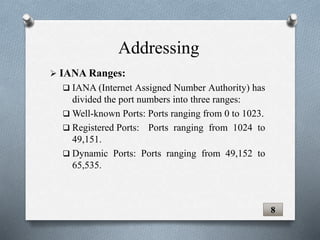
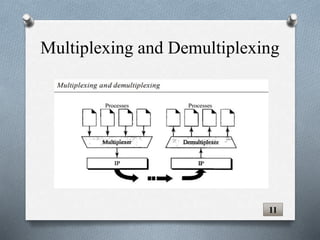
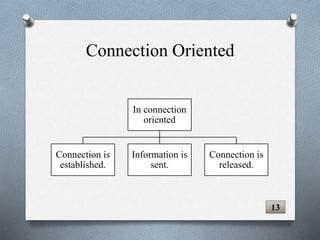
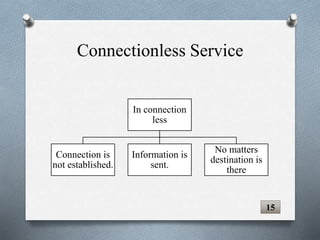
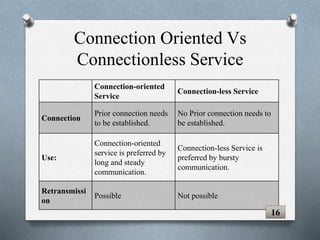
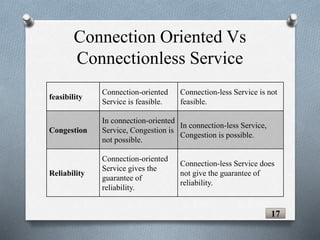
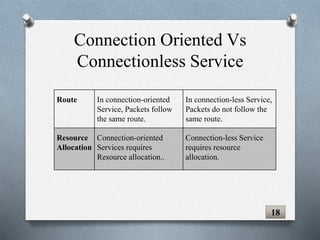
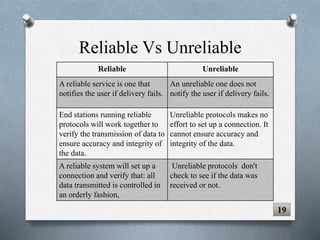
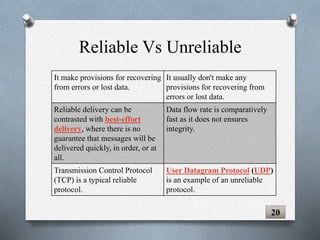
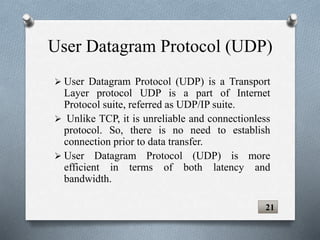
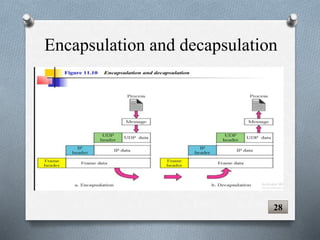
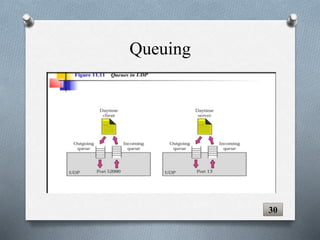
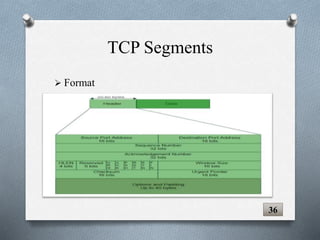
The document discusses transport layer protocols. It provides an overview of process-to-process delivery and addressing at the transport layer. Key points covered include connection-oriented vs connectionless services, reliable vs unreliable protocols, User Datagram Protocol (UDP), and Transmission Control Protocol (TCP). UDP is described as a connectionless and unreliable protocol, while TCP provides connection-oriented and reliable data transfer with features like flow control, error control, and numbering systems.