The document provides an overview of operating systems, including their definition, types, history and a comparison of Linux and Windows. It discusses how an operating system manages computer hardware and software resources, provides common services and acts as an intermediary between programs and hardware. Examples of popular operating systems are given for different types including real-time, multi-user, multi-tasking, distributed and embedded. A brief history of operating system development from the 1940s to modern times is also provided. The document concludes with a table comparing key aspects of Linux and Windows such as cost, manufacturer, usage, development and security considerations.








![11
o Renaming a file
o Seeing the processes of a CPU
o Creating newly formatted ext4 partition
o Text File editors like vi, emacs and nano
o Copying a large file/folder with progress bar
o Keeping track of free and available memory
o Backup a mysql database
o Make difficult to guess – random password
o Merge two text files
o List of all the opened files
Part III – 20 Advanced Commands for Linux Experts
Writing this article and the list of command that needs to go with the article was a little cumbersome. We
chose 20 commands with each article and hence gave a lot of thought for which command should be
included and which should be excluded from the particular post. I personally selected the commands on
the basis of their usability (as I use and get used to) from a user point of view and an Administrator point
of view.
This Articles aims to concatenate all the articles of its series and provide you with all the functionality in
commands you can perform in our this very series of articles.
There are too long lists of commands available in Linux. But we provided the list of 60 commands which
is generally and most commonly used and a user having knowledge of these 60 commands as a whole
can work in terminal very much smoothly.
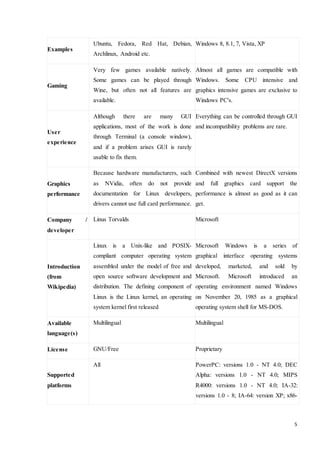
Command Description
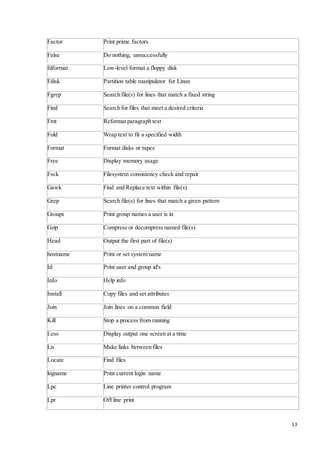
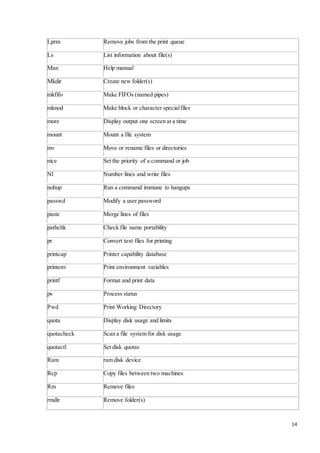
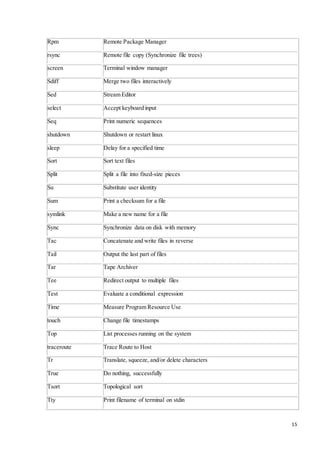
adduser Add a new user
arch Print machine architecture
awk Find and Replace text within file(s)
bc An arbitrary precision calculator language
cal Display a calendar
Cat Concatenate files and print on the standard output
Chdir Change working directory
Chgrp Change the group ownership of files
chkconfig Tool for maintaining the /etc/rc[0-6].d directory hierarchy
chmod Change the access permissions of files and directories](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-11-320.jpg)

![17
Command syntax:
chmod [options] mode[,mode] file1 [file2 ...]
Usual implemented options include:
-R recursive, i.e. include objects in subdirectories
-f force, forge ahead with all objects even if errors occur
-v verbose, show objects processed
If a symbolic link is specified, the target object is affected. File modes directly associated with symbolic
links themselves are typically never used.
To view the file mode, the ls or stat commands may be used:
$ ls -l findPhoneNumbers.sh
-rwxr-xr-- 1 dgerman staff 823 Dec 16 15:03 findPhoneNumbers.sh
$ stat -c %a findPhoneNumbers.sh
The r, w, and x specify the read, write, and execute access, respectively. This script can be read, written
to, and executed by the user, read and executed by other members of the staff group and can also be read
by others.
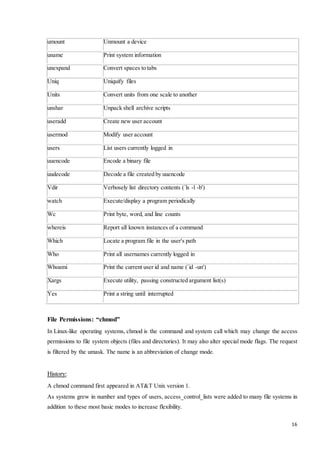
Octal modes:
The chmod numeric format accepts up to four octal digits. The rightmost three refer to permissions for
the file owner, the group, and other users. The optional next digit (fourth from the right) specifies
special setuid, setgid, and sticky flags.
Numerical permissions:
# Permission rwx
7 read, write and execute 111
6 read and write 110
5 read and execute 101
4 read only 100
3 write and execute 011
2 write only 010
1 execute only 001](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-17-320.jpg)
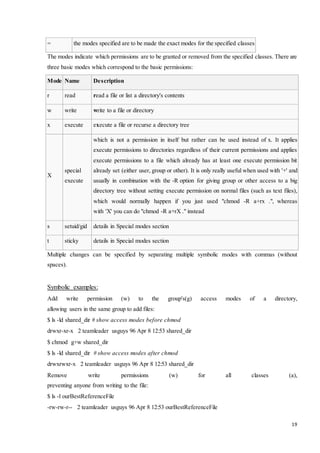
![18
0 None 000
Numeric example:
In order to permit all users who are members of the programmers group to update a file
$ ls -l sharedFile
-rw-r--r-- 1 jsmith programmers 57 Jul 3 10:13 sharedFile
$ chmod 664 sharedFile
$ ls -l sharedFile
-rw-rw-r-- 1 jsmith programmers 57 Jul 3 10:13 sharedFile
Since the setuid, setgid and sticky bits are not specified, this is equivalent to:
$ chmod 0664 sharedFile.
Symbolic modes:
The chmod command also accepts a finer-grained symbolic notation, which allows modifying specific
modes while leaving other modes untouched. The symbolic mode is composed of three components,
which are combined to form a single string of text:
$ chmod [references][operator][modes] file ...
The references (or classes) are used to distinguish the users to whom the permissions apply. If no
references are specified it defaults to “all” but modifies only the permissions allowed by the unmask. The
references are represented by one or more of the following letters:
Reference Class Description
U user the owner of the file
G group users who are members of the file's group
O others users who are neither the owner of the file nor members of the file's group
A all all three of the above, same as ugo
The chmod program uses an operator to specify how the modes of a file should be adjusted. The
following operators are accepted:
Operator Description
+ adds the specified modes to the specified classes
- removes the specified modes from the specified classes](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-18-320.jpg)




![symmetric multitasking systems such as Windows 3.1 relied on each running process to voluntary
relinquish control of the processor. If an application in this system hung or stalled, the entire computer
system stalled. By making use of an additional component to pre-empt each process when its “turn” is
up, stalled programs do not affect the overall flow of the operating system.
Each “turn” is called a time slice, and each time slice is only a fraction of a second long. It is this rapid
switching from process to process that allows a computer to “appear’ to be doing two things at once, in
much the same way a movie “appears” to be a continuous picture.
26
Types of Processes:
There are generally two types of processes that run on Linux. Interactive processes are those processes
that are invoked by a user and can interact with the user. VI is an example of an interactive process.
Interactive processes can be classified into foreground and background processes. The foreground
process is the process that you are currently interacting with, and is using the terminal as its stdin
(standard input) and stdout (standard output). A background process is not interacting with the user and
can be in one of two states – paused or running.
The following exercise will illustrate foreground and background processes.
1. Logon as root.
2. Run [cd ]
3. Run [vi]
4. Press [ctrl + z]. This will pause vi
5. Type [jobs]
6. Notice vi is running in the background
7. Type [fg %1]. This will bring the first background process to the foreground.
8. Close vi.
The second general type of process that runs on Linux is a system process or Daemon (day-mon).
Daemon is the term used to refer to process’ that are running on the computer and provide services but
do not interact with the console. Most server software is implemented as a daemon. Apache, Samba, and
inn are all examples of daemons.
Any process can become a daemon as long as it is run in the background, and does not interact with the
user. A simple example of this can be achieved using the [ls –R] command. This will list all
subdirectories on the computer, and is similar to the [dir /s] command on Windows. This command can
be set to run in the background by typing [ls –R &], and although technically you have control over the
shell prompt, you will be able to do little work as the screen displays the output of the process that you
have running in the background. You will also notice that the standard pause (ctrl+z) and kill (ctrl+c)
commands do little to help you.](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-26-320.jpg)



![30
A short int may use fewer bits than a regular int, thereby saving storage space.
o ( The C standard only specifies that a short int cannot use more bits than a regular int.
On many machines short ints use the same number of bits as regular ints. )
printf and scanf replace %d or %i with %hd or%hi to indicate the use of a short int.
short int may also be specified as just short.
unsigned ints
Unless otherwise specified, all of the aforementioned int types are signed numbers.
Any of the above may be preceded by the keyword "unsigned" to indicate that they are unsigned.
o e.g. "unsigned int", "unsigned long int", "unsigned long", etc.
o "unsigned" by itself implies "unsigned int"
The format specifier for unsigned integers in decimal form is %u. The u may be preceded by l, ll, or
h for long, long long, and short unsigned types respectively.
Unsigned integers can also be printed or scanned in octal or hexidecimal form using the %o, %x, or
%X format specifiers in place of %u.
char
Normally chars are interpreted as characters ( see below )
Technically the char data type is an integral type, always having exactly 8 bits, ( known as a byte. )
Signed chars can have values from -128 to +127, and can be printed as integers using %d or %i
format specifiers
chars can also be specified as unsigned, giving them a range from 0 to+255.
o Unsigned chars can be printed using %u, %o, %x, or %X format specifiers.
Integral Constants
int constants in decimal form must begin with a digit from 1 to 9, and can be followed by additional
digits from 0 to 9.
o in octal form they must begin with a 0, and following digits must be in the range from 0 to 7.
o in hexidecimal form they begin with 0x. Followng digits must be in the range 0 to 9, or A to
F, or a to f.
Any of the above may be preceded by a minus sign.
int constants may be followed by a u, l, or ll to indicate unsigned, long, or long long constants
respectively.
Allowable formats are as follows, where the [ square brackets ] denote optional characters:
Decimal: [±]1-9[0-9...][Ll][Uu]
Octal: [±]0[0-7...][Ll][Uu]
Hexadecimal: [±]0x[0-9a-fA-F...][Ll][Uu]
Integer Overflow](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-30-320.jpg)

![ The double data type is the preferred floating point type for most scientific and engineering
32
calculations.
long double
The long double type is guaranteed to have more bits than a double, but the exact number my
vary from one hardware platform to another. The most typical implementations are either 80 or 128
bits.
The IEEE standard for quadruple precision floating point numbers is 128 bits consisting of:
o one sign bit
o 112 bits ( plus one implied ) for digits, working out to about 34 decimal digits of precision
o 15 bits for the exponent, giving a range from about 10^-4932 to 10^4932
Floating point constants
Floating-point constants are normally indicated by the presence of a decimal point, and are normally
doubles.
o Floating point constants may be followed by either an "F" to indicate an ordinary float, or an
"L" to indicate a long double.
o Floating point constants can also be expressed in scientific notation
o Allowable formats are as follows:
o [±]1-9[0-9...].[0-9...][Ee[±]0-9...][FfLl]
o [±][0].[0-9...][Ee[±]0-9...][FfLl]
o [±]1-9[0-9...]Ee[±]0-9...[FfLl]
[±]1-9[0-9...]Ff[Ll]
Characters:
Although the char data type is technically a small integer ( see above ), its most common use is to
hold numeric codes representing ( ASCII ) characters.
For example, the ASCII code for the capital letter 'A' is 65.
Note that the character '9' is not the same as the integer value 9.
o In this case the ASCII code for the character '9' is 57.
o The numerical value 9 in the ASCII code set happens to represent a horizontal tab character.
Character Constants
Character constants are enclosed in single quotes, such as 'A'.
Character constants may also include escape characters such as 'n' or 't', as shown here:](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-32-320.jpg)






![39
‘t’ horizontal tab
‘r’ carriage return
Variables:
Definition:
A variable is a data name that may be used to store a data value. A variable may take
different values at different times of execution and may be chosen by the programmer in a
meaningful way. It may consist of letters, digits and underscore character.
Eg: 1) Average
2) Height
Rules for defining variables
They must begin with a letter. Some systems permit underscore as the first character.
ANSI standard recognizes a length of 31 characters. However, the length should not
be normally more than eight characters.
Uppercase and lowercase are significant.
The variable name should not be a keyword.
White space is not allowed.
Arrays in C
In C programming, one of the frequently arising problem is to handle similar types of data. For example:
If the user want to store marks of 100 students. This can be done by creating 100 variable individually
but, this process is rather tedious and impracticable. These type of problem can be handled in C
programming using arrays.
An array is a sequence of data item of homogeneous value(same type).
Arrays are of two types:
1. One-dimensional arrays
2. Multidimensional arrays
Declaration of one-dimensional array
data_type array_name[array_size];
For example:
int age[5];](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-39-320.jpg)
![Here, the name of array is age. The size of array is 5,i.e., there are 5 items(elements) of array age. All
element in an array are of the same type (int, in this case).
Array elements
Size of array defines the number of elements in an array. Each element of array can be accessed and used
by user according to the need of program. For example:
int age[5];
Note that, the first element is numbered 0 and so on.
Here, the size of array age is 5 times the size of int because there are 5 elements.
Suppose, the starting address of age[0] is 2120d and the size of int be 4 bytes. Then, the next address
(address of a[1]) will be 2124d, address of a[2] will be 2128d and so on.
Initialization of one-dimensional array:
Arrays can be initialized at declaration time in this source code as:
40
int age[5]={2,4,34,3,4};
It is not necessary to define the size of arrays during initialization.
int age[]={2,4,34,3,4};
In this case, the compiler determines the size of array by calculating the number of elements of an array.
Accessing array elements
In C programming, arrays can be accessed and treated like variables in C.
For example:
scanf("%d",&age[2]);
/* statement to insert value in the third element of array age[]. */
scanf("%d",&age[i]);
/* Statement to insert value in (i+1)th element of array age[]. */
/* Because, the first element of array is age[0], second is age[1], ith is age[i-1] and (i+1)th is age[i]. */
printf("%d",age[0]);
/* statement to print first element of an array. */](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-40-320.jpg)
![41
printf("%d",age[i]);
/* statement to print (i+1)th element of an array. */
Example of array in C programming
/* C program to find the sum marks of n students using arrays */
#include <stdio.h>
int main(){
int marks[10],i,n,sum=0;
printf("Enter number of students: ");
scanf("%d",&n);
for(i=0;i<n;++i){
printf("Enter marks of student%d: ",i+1);
scanf("%d",&marks[i]);
sum+=marks[i];
}
printf("Sum= %d",sum);
return 0;
}
Output
Enter number of students: 3
Enter marks of student1: 12
Enter marks of student2: 31
Enter marks of student3: 2
sum=45
Important thing to remember in C arrays
Suppose, you declared the array of 10 students. For example: arr[10]. You can use array members
from arr[0] to arr[9]. But, what if you want to use element arr[10], arr[13] etc. Compiler may not show
error using these elements but, may cause fatal error during program execution.
C programming language allows programmer to create arrays of arrays known as multidimensional
arrays. For example:
float a[2][6];](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-41-320.jpg)
![Here, a is an array of two dimension, which is an example of multidimensional array. This array has 2
rows and 6 columns
For better understanding of multidimensional arrays, array elements of above example can be thinked of
as below:
42
Initialization of Multidimensional Arrays
In C, multidimensional arrays can be initialized in different number of ways.
int c[2][3]={{1,3,0}, {-1,5,9}};
OR
int c[][3]={{1,3,0}, {-1,5,9}};
OR
int c[2][3]={1,3,0,-1,5,9};
Initialization Of three-dimensional Array
double cprogram[3][2][4]={
{{-0.1, 0.22, 0.3, 4.3}, {2.3, 4.7, -0.9, 2}},
{{0.9, 3.6, 4.5, 4}, {1.2, 2.4, 0.22, -1}},
{{8.2, 3.12, 34.2, 0.1}, {2.1, 3.2, 4.3, -2.0}}
};
Suppose there is a multidimensional array arr[i][j][k][m]. Then this array can hold i*j*k*m numbers of
data.
Similarly, the array of any dimension can be initialized in C programming.
Example of Multidimensional Array In C
Write a C program to find sum of two matrix of order 2*2 using multidimensional arrays where,
elements of matrix are entered by user.
#include <stdio.h>
int main(){
float a[2][2], b[2][2], c[2][2];
int i,j;
printf("Enter the elements of 1st matrixn");](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-42-320.jpg)
![/* Reading two dimensional Array with the help of two for loop. If there was an array of 'n' dimension,
'n' numbers of loops are needed for inserting data to array.*/
for(i=0;i<2;++i)
43
for(j=0;j<2;++j){
printf("Enter a%d%d: ",i+1,j+1);
scanf("%f",&a[i][j]);
}
printf("Enter the elements of 2nd matrixn");
for(i=0;i<2;++i)
for(j=0;j<2;++j){
printf("Enter b%d%d: ",i+1,j+1);
scanf("%f",&b[i][j]);
}
for(i=0;i<2;++i)
for(j=0;j<2;++j){
/* Writing the elements of multidimensional array using loop. */
c[i][j]=a[i][j]+b[i][j]; /* Sum of corresponding elements of two arrays. */
}
printf("nSum Of Matrix:");
for(i=0;i<2;++i)
for(j=0;j<2;++j){
printf("%.1ft",c[i][j]);
if(j==1) /* To display matrix sum in order. */
printf("n");
}
return 0;
}
Ouput
Enter the elements of 1st matrix
Enter a11: 2;
Enter a12: 0.5;
Enter a21: -1.1;
Enter a22: 2;
Enter the elements of 2nd matrix](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-43-320.jpg)


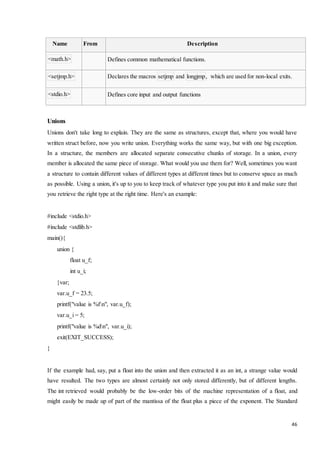



![50
3. unsigned char temp_coeff ;
4. unsigned char span ;
5. unsigned char amp_gain ;
The concept of a structure is based on this idea of generalized "template" for related data. In this case, a
structure template (or "component list") describing any of the manufacturer's sensors would be declared:
1. struct SENSOR_DESC
2. {
3. unsigned char gain ;
4. unsigned char offset ;
5. unsigned char temp_coeff ;
6. unsigned char span ;
7. unsigned char amp_gain ;
8. } ;
This does not physically do anything to memory. At this stage it merely creates a template which can
now be used to put real data into memory.
This is achieved by:
1. struct SENSOR_DESC sensor_database ;
This reads as "use the template SENSOR_DESC to layout an area of memory named sensor_database,
reflecting the mix of data types stated in the template". Thus a group of 5 unsigned chars will be created
in the form of a structure.
The individual elements of the structure can now be accessed as:
1. sensor_database.gain = 0x30 ;
2. sensor_database.offset = 0x50 ;
3. sensor_database.temp_coeff = 0x60 ;
4. sensor_database.span = 0xC4 ;
5. sensor_database.amp_gain = 0x21 ;
Arrays Of Structures
In the example though, information on many sensors is required and, as with individual chars and ints, it
is possible to declare an array of structures. This allows many similar groups of data to have different
sets of values.
1. struct SENSOR_DESC sensor_database[4] ;](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-50-320.jpg)
![This creates four identical structures in memory, each with an internal layout determined by the structure
template. Accessing this array is performed simply by appending an array index to the structure name:
1. /*Operate On Elements In First Structure Describing */
51
2. /*Sensor 0 */
3. sensor_database[0].gain = 0x30 ;
4. sensor_database[0].offset = 0x50 ;
5. sensor_database[0].temp_coeff = 0x60 ;
6. sensor_database[0].span = 0xC4 ;
7. sensor_database[0].amp_gain = 0x21 ;
8. /* Operate On Elements In First Structure Describing */
9. /*Sensor 1 */
10. sensor_database[1].gain = 0x32 ;
11. sensor_database[1].offset = 0x56 ;
12. sensor_database[1].temp_coeff = 0x56 ;
13. sensor_database[1].span = 0xC5 ;
14. sensor_database[1].amp_gain = 0x28 ;
15. // and so on...
C Preprocessor
Including files:
One of the most common uses of the preprocessor is to include another file:
#include <stdio.h>
int main(void)
{
printf("Hello, world!n");
return 0;
}
The preprocessor replaces the line #include <stdio.h> with the text of the file 'stdio.h', which declares
the printf() function among other things.
This can also be written using double quotes, e.g. #include "stdio.h". If the filename is enclosed within
angle brackets, the file is searched for in the standard compiler include paths. If the filename is enclosed
within double quotes, the search path is expanded to include the current source directory. C compilers](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-51-320.jpg)


![#define RADTODEG(x) ((x) * 57.29578)
This defines a radians-to-degrees conversion which can be inserted in the code where required,
i.e., RADTODEG(34). This is expanded in-place, so that repeated multiplication by the constant is not
shown throughout the code. The macro here is written as all uppercase to emphasize that it is a macro,
not a compiled function.
The second x is enclosed in its own pair of parentheses to avoid the possibility of incorrect order of
operations when it is an expression instead of a single value. For example, the
expression RADTODEG(r + 1) expands correctly as ((r + 1) * 57.29578) — without
parentheses, (r + 1 * 57.29578) gives precedence to the multiplication.
Similarly, the outer pair of parentheses maintain correct order of operation. For
example, 1 / RADTODEG(r) expands to 1 / ((r) * 57.29578) — without
parentheses, 1 /(r) * 57.29578 gives precedence to the division.
54
Special macros and directives:
Certain symbols are required to be defined by an implementation during preprocessing. These
include __FILE__ and __LINE__, predefined by the preprocessor itself, which expand into the current
file and line number. For instance the following:
// debugging macros so we can pin down message origin at a glance
#define WHERESTR "[file %s, line %d]: "
#define WHEREARG __FILE__, __LINE__
#define DEBUGPRINT2(...) fprintf(stderr, __VA_ARGS__)
#define DEBUGPRINT(_fmt, ...) DEBUGPRINT2(WHERESTR _fmt, WHEREARG,
__VA_ARGS__)
//...
DEBUGPRINT("hey, x=%dn", x);
prints the value of x, preceded by the file and line number to the error stream, allowing quick access to
which line the message was produced on. Note that the WHERESTRargument is concatenated with the
string following it. The values of __FILE__ and __LINE__ can be manipulated with the #line directive.
The #line directive determines the line number and the file name of the line below. E.g.:
#line 314 "pi.c"
puts("line=" #__LINE__ " file=" __FILE__);
generates the puts function:](https://image.slidesharecdn.com/4thyeartrainingreport-141129122422-conversion-gate02/85/training-report-54-320.jpg)