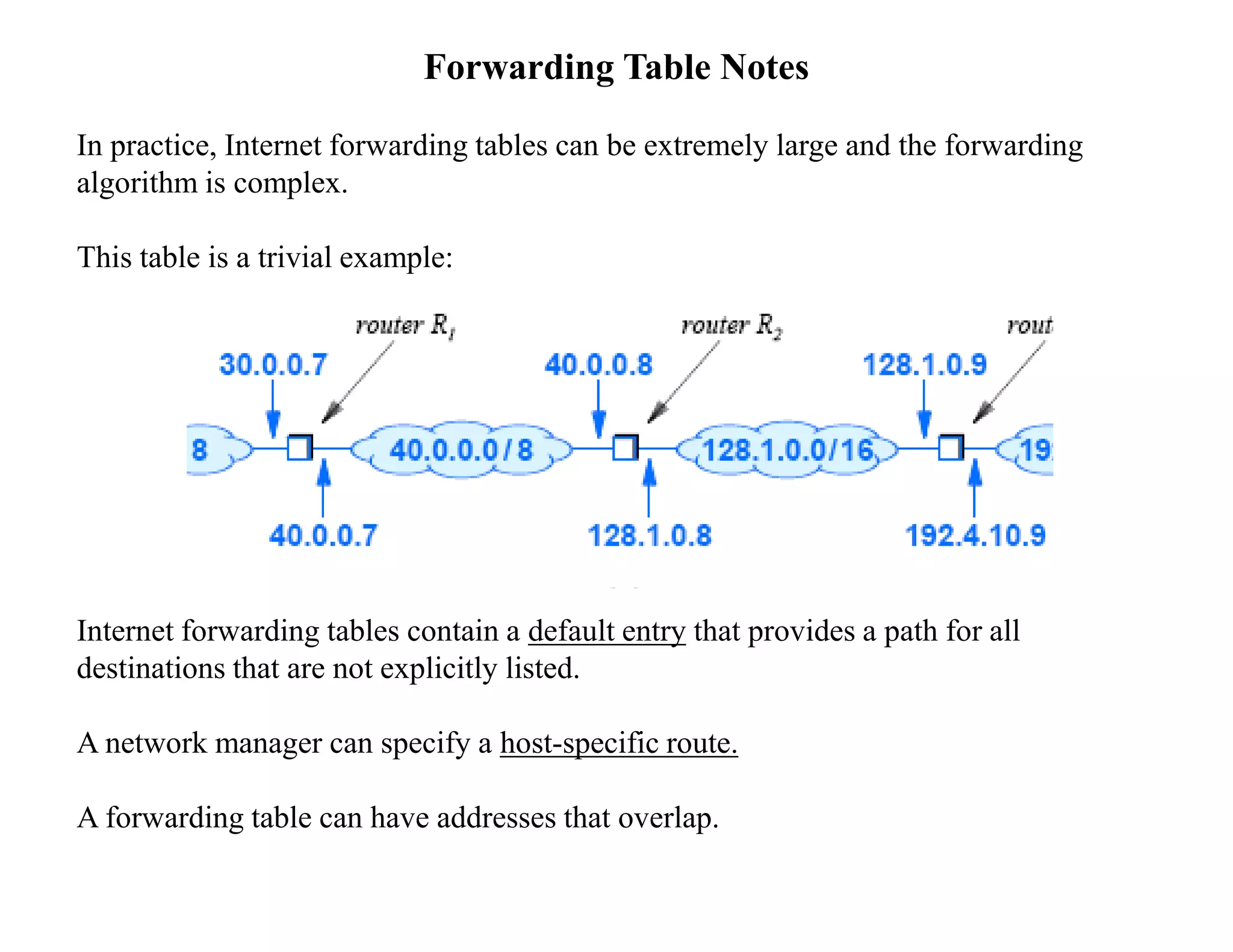
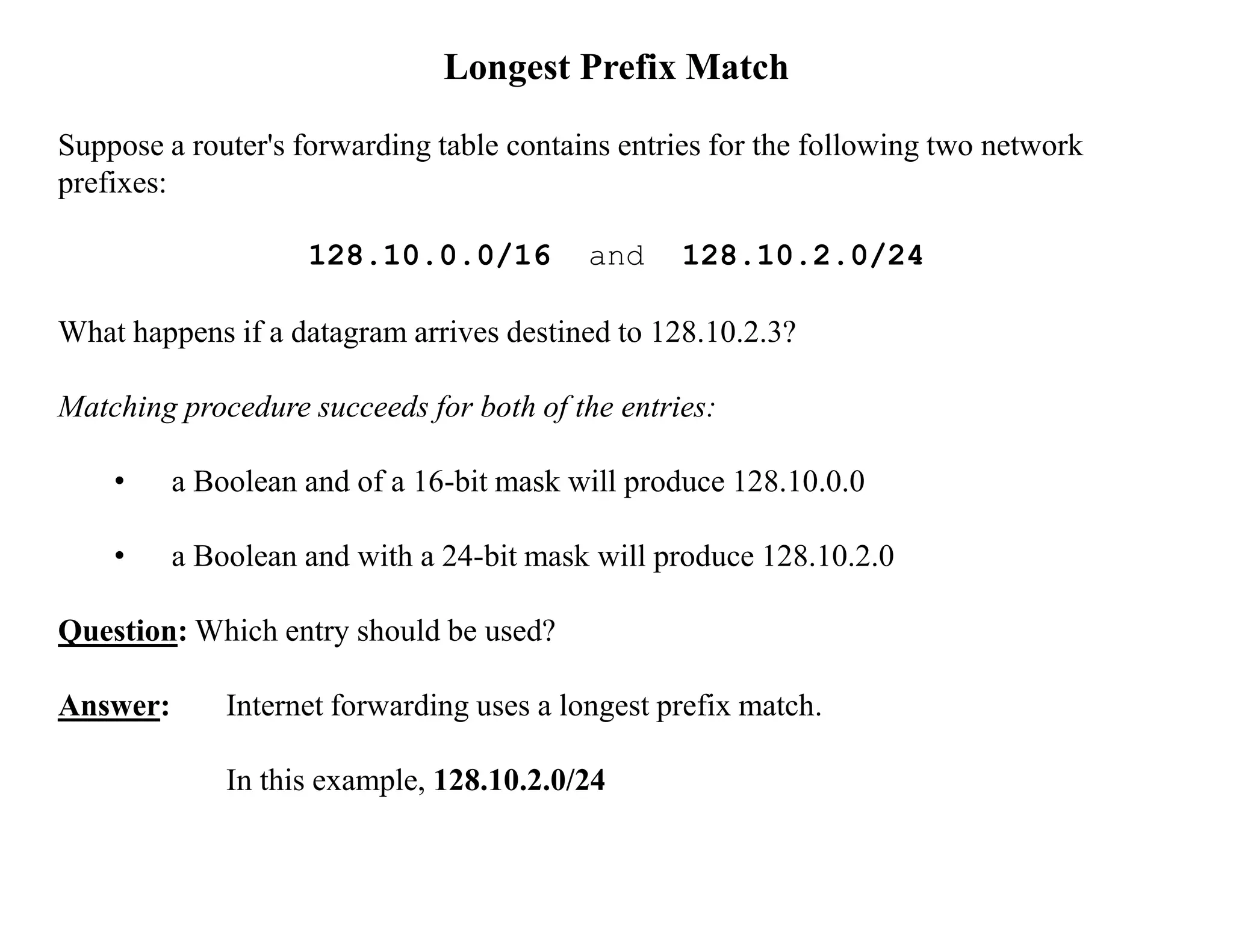
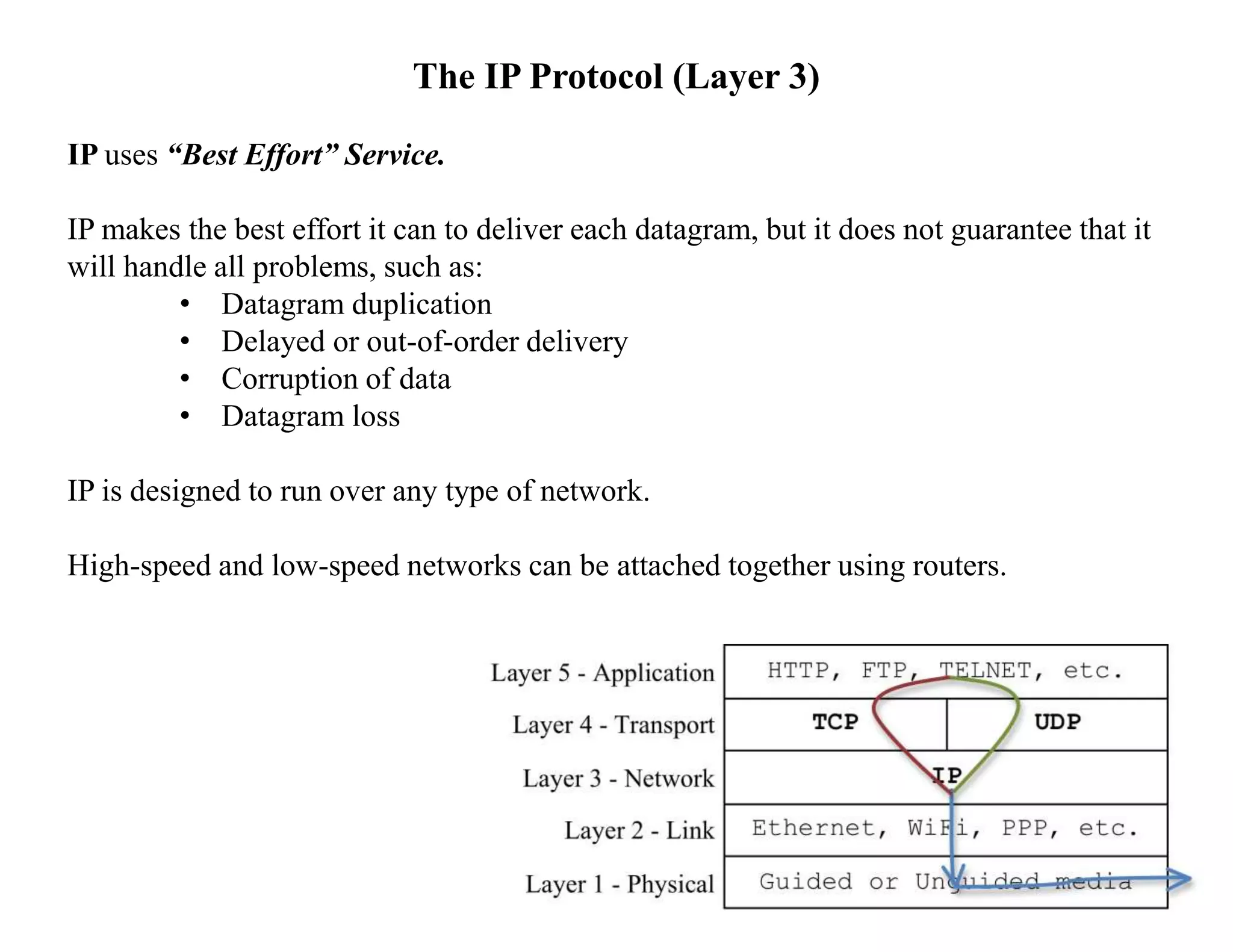
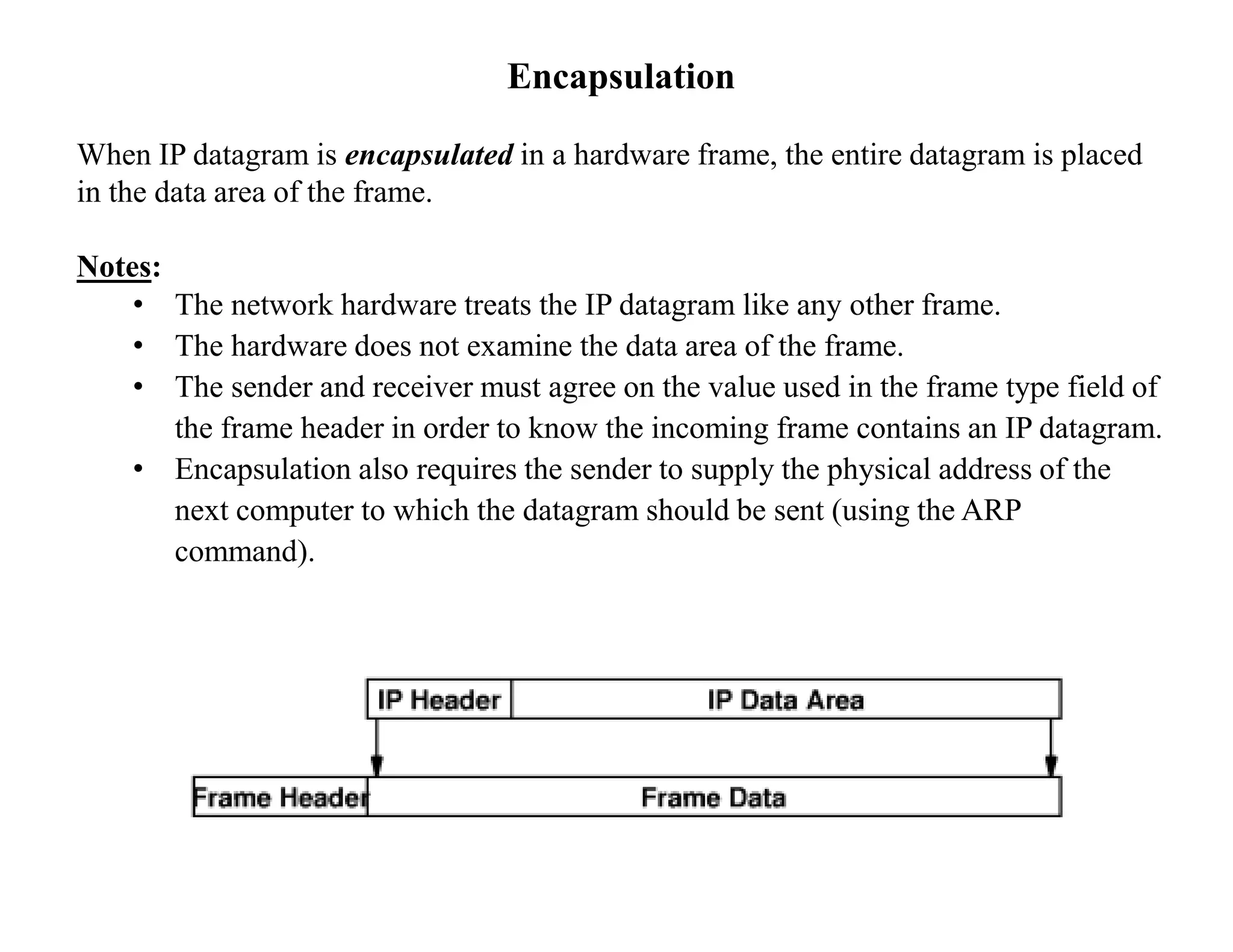
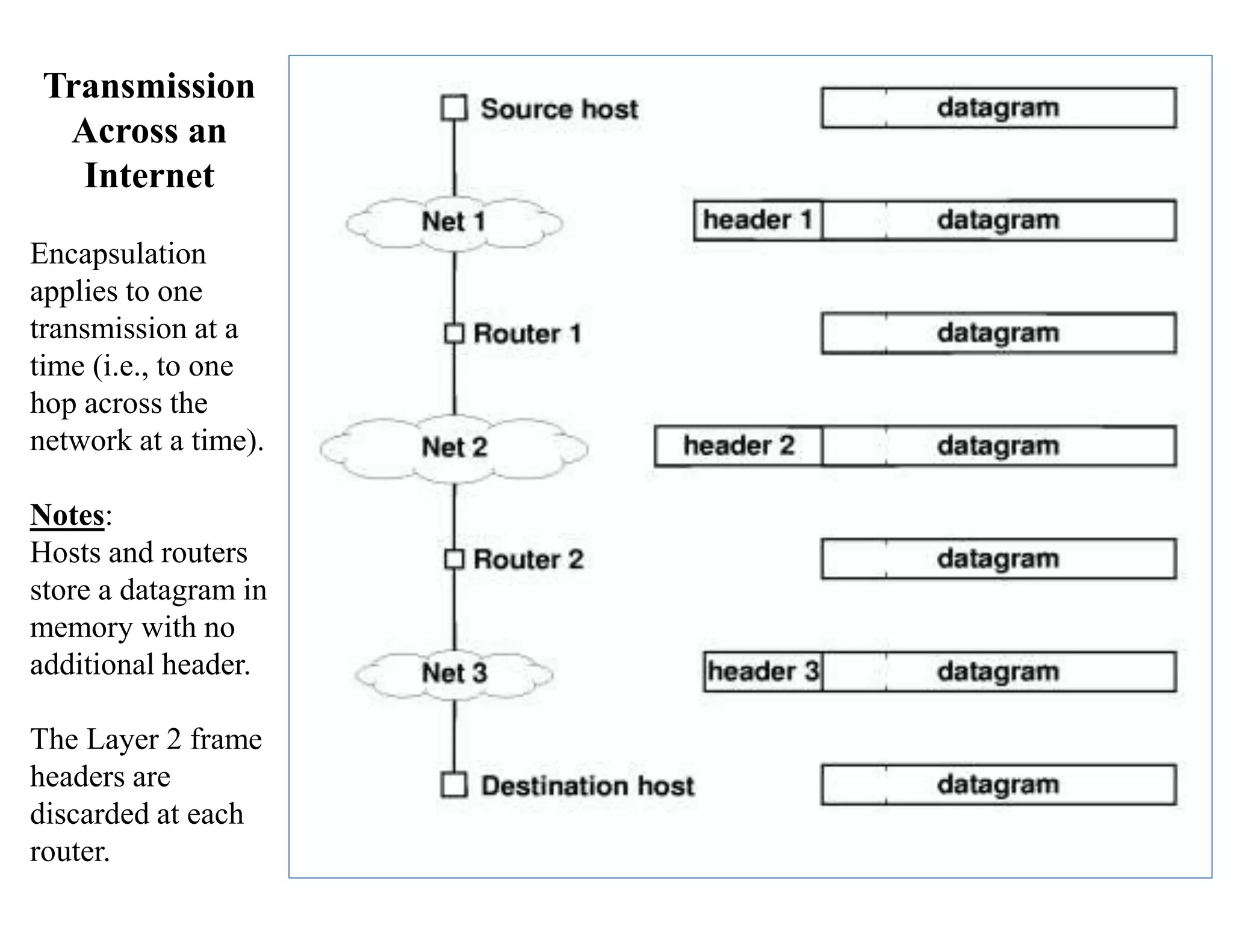
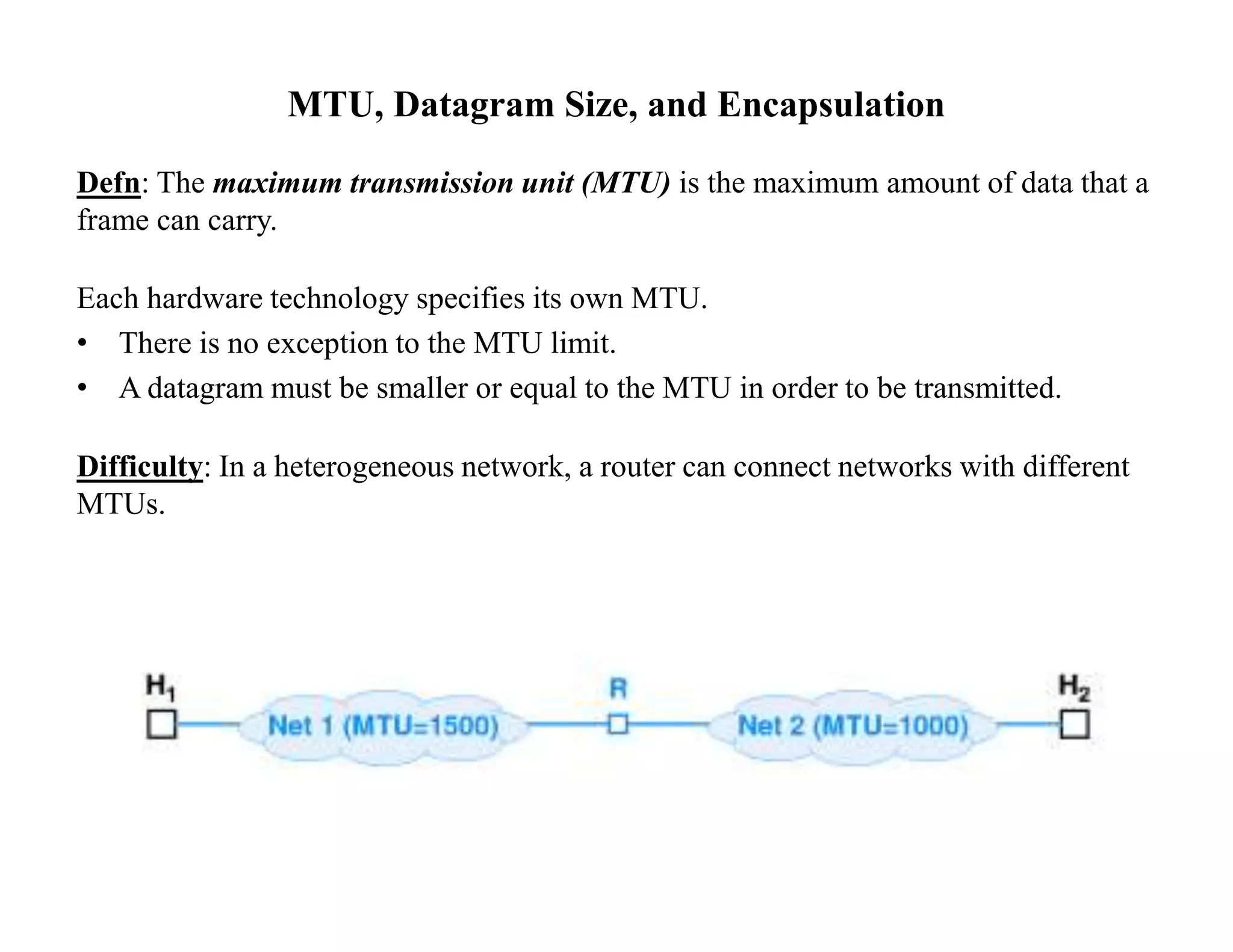
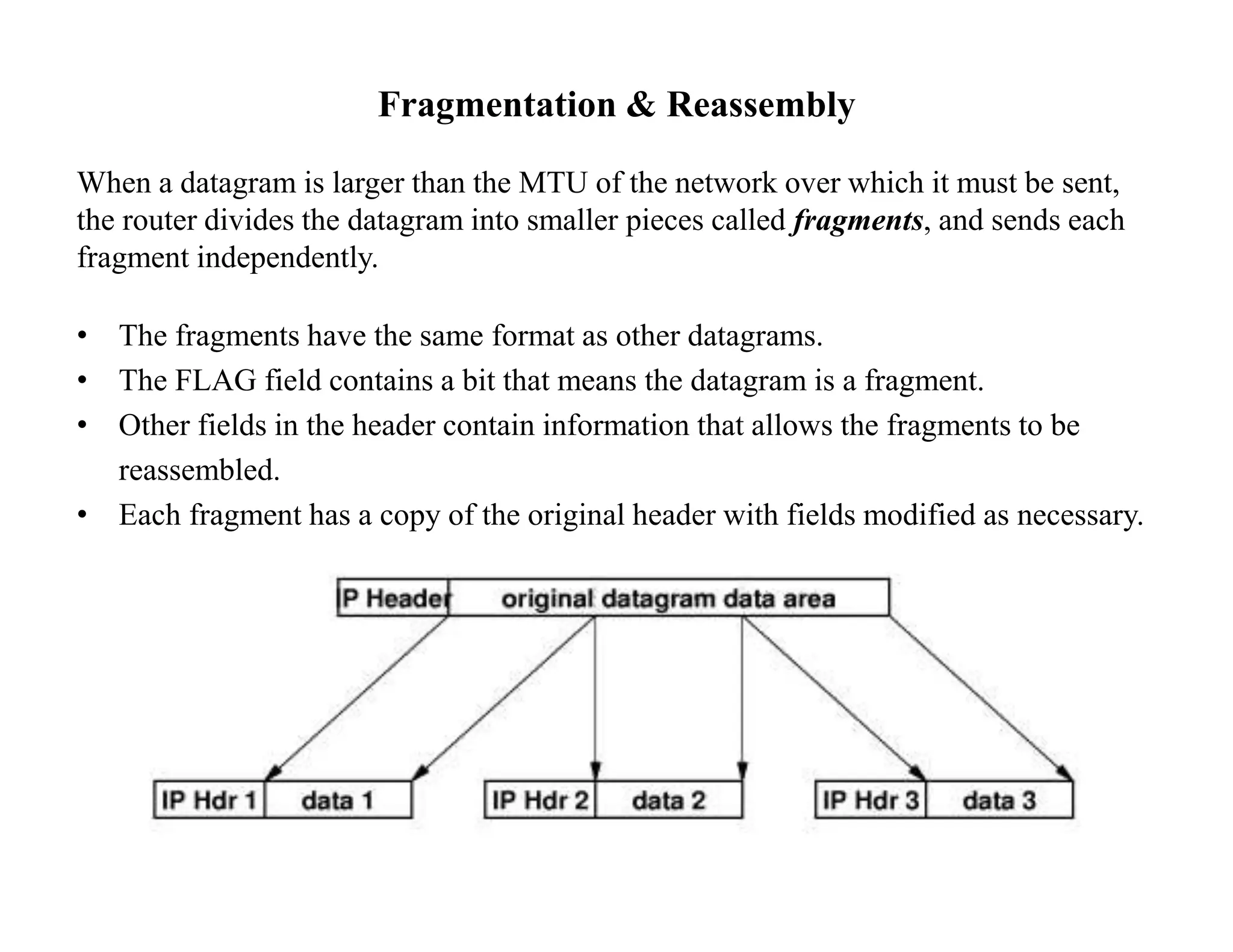
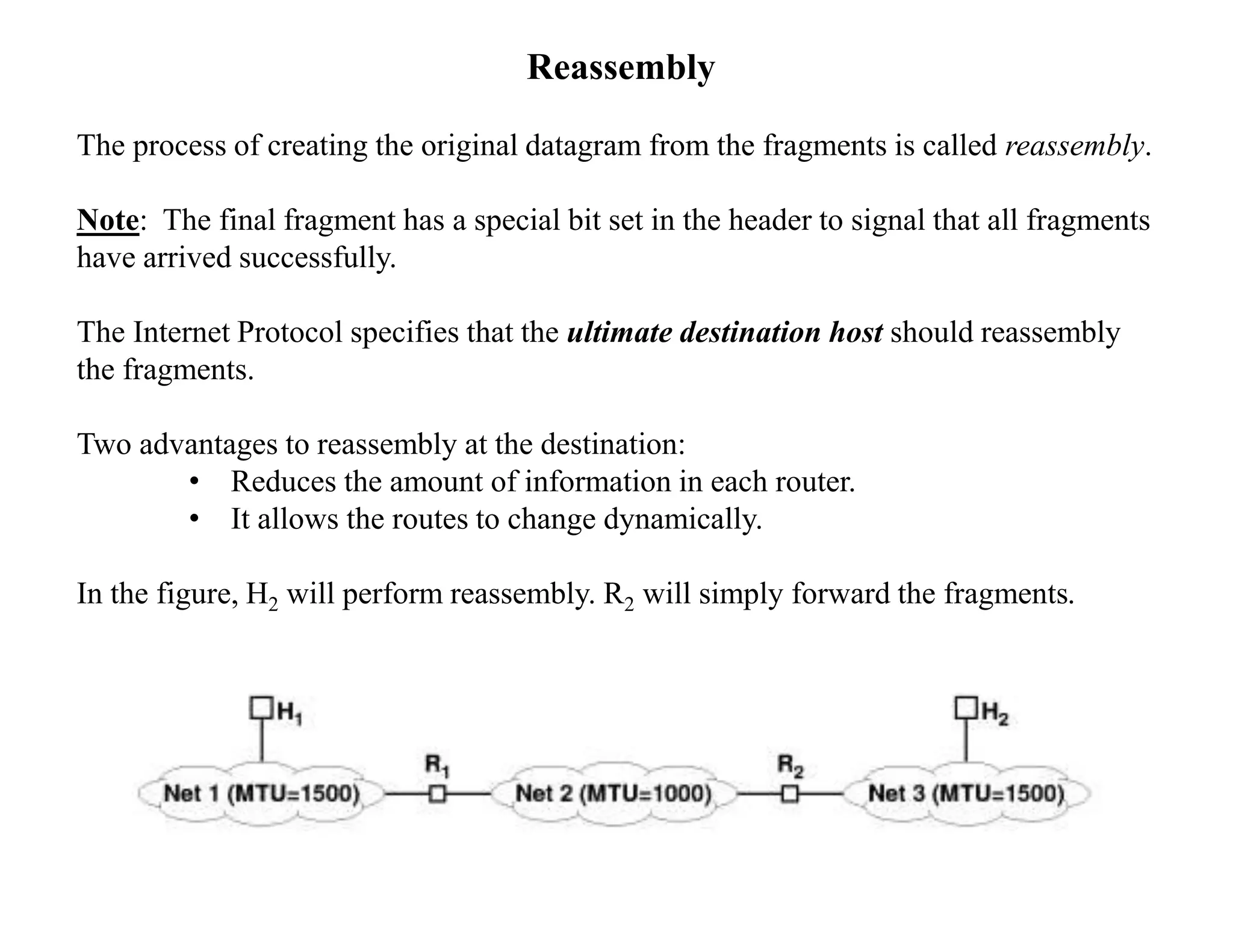
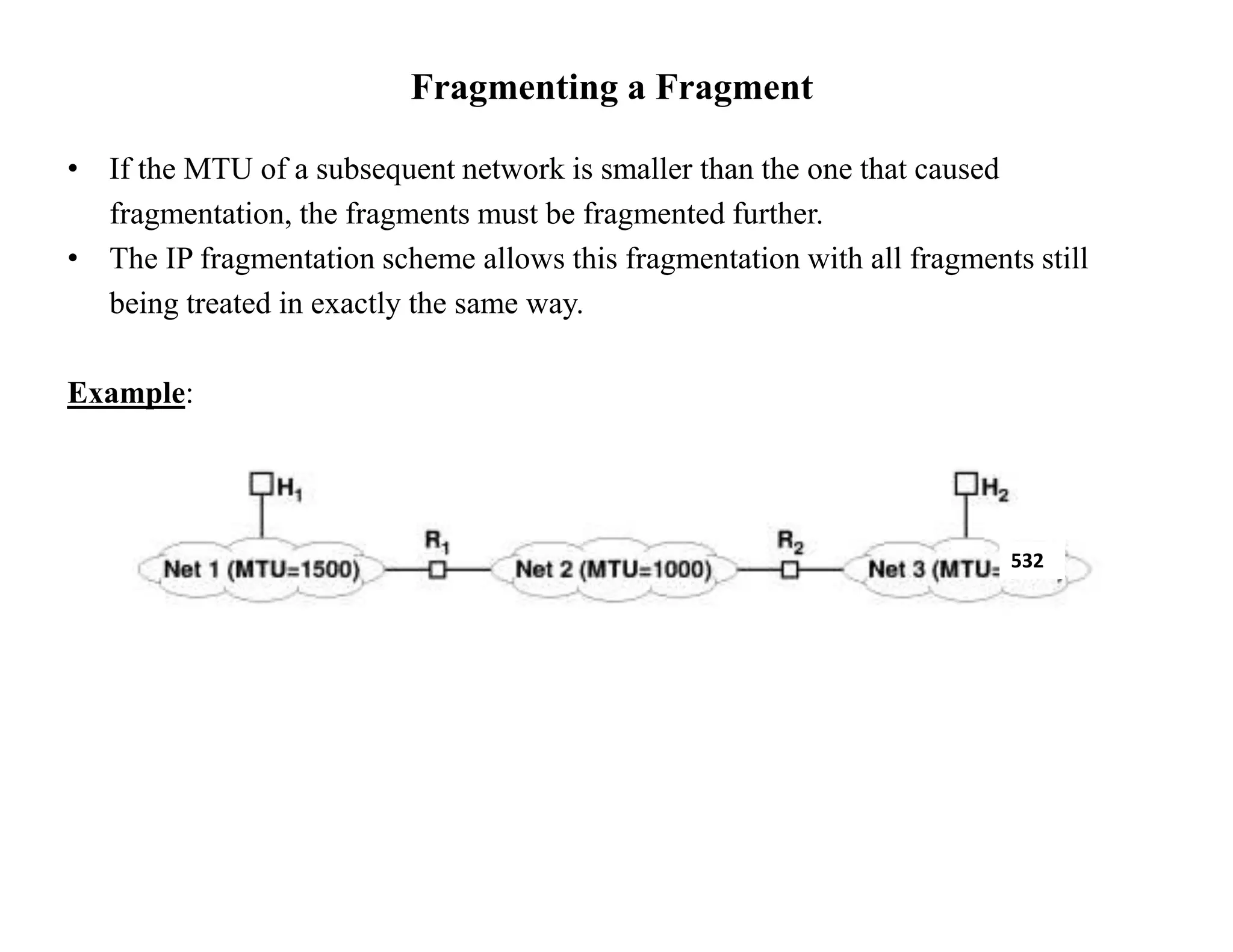
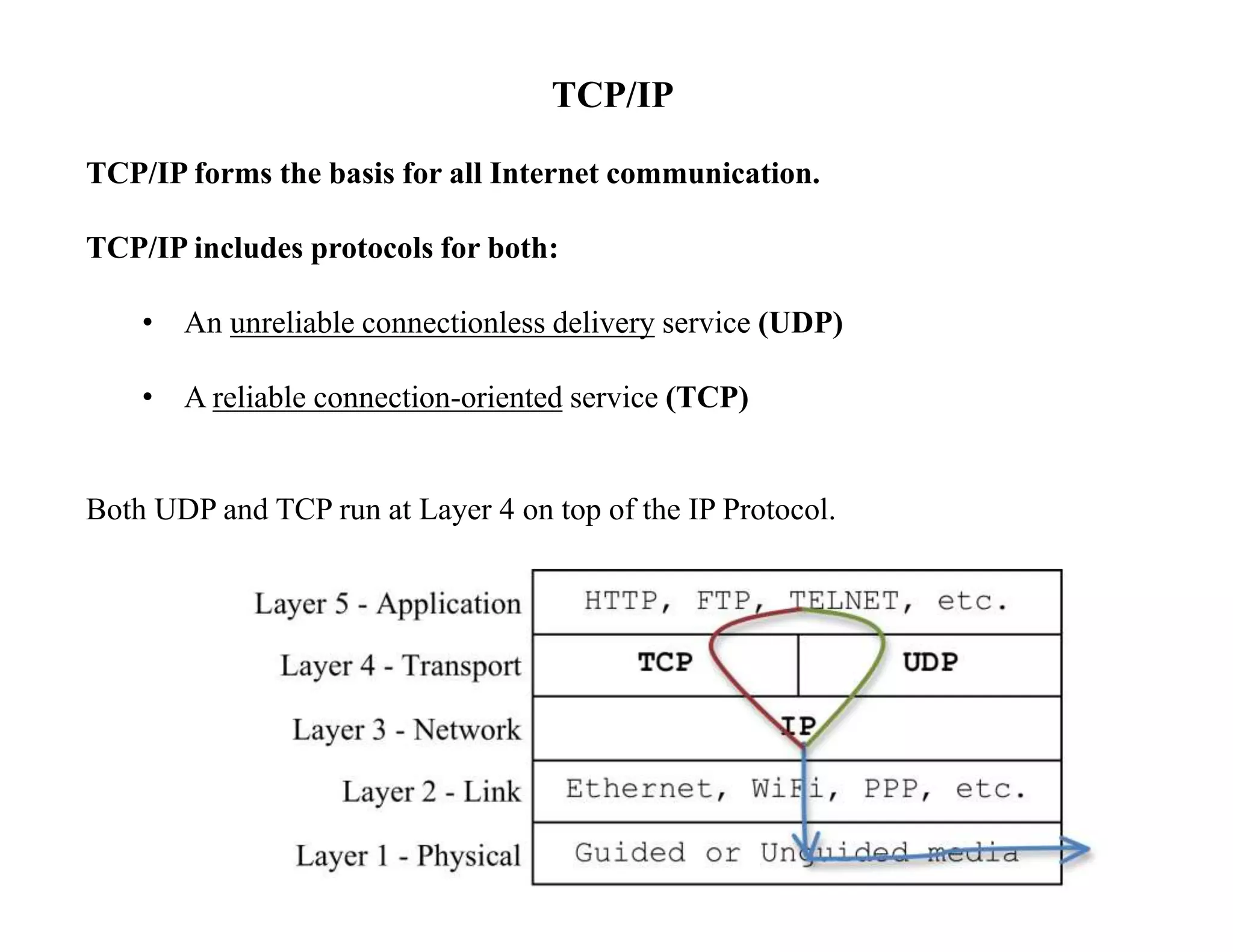
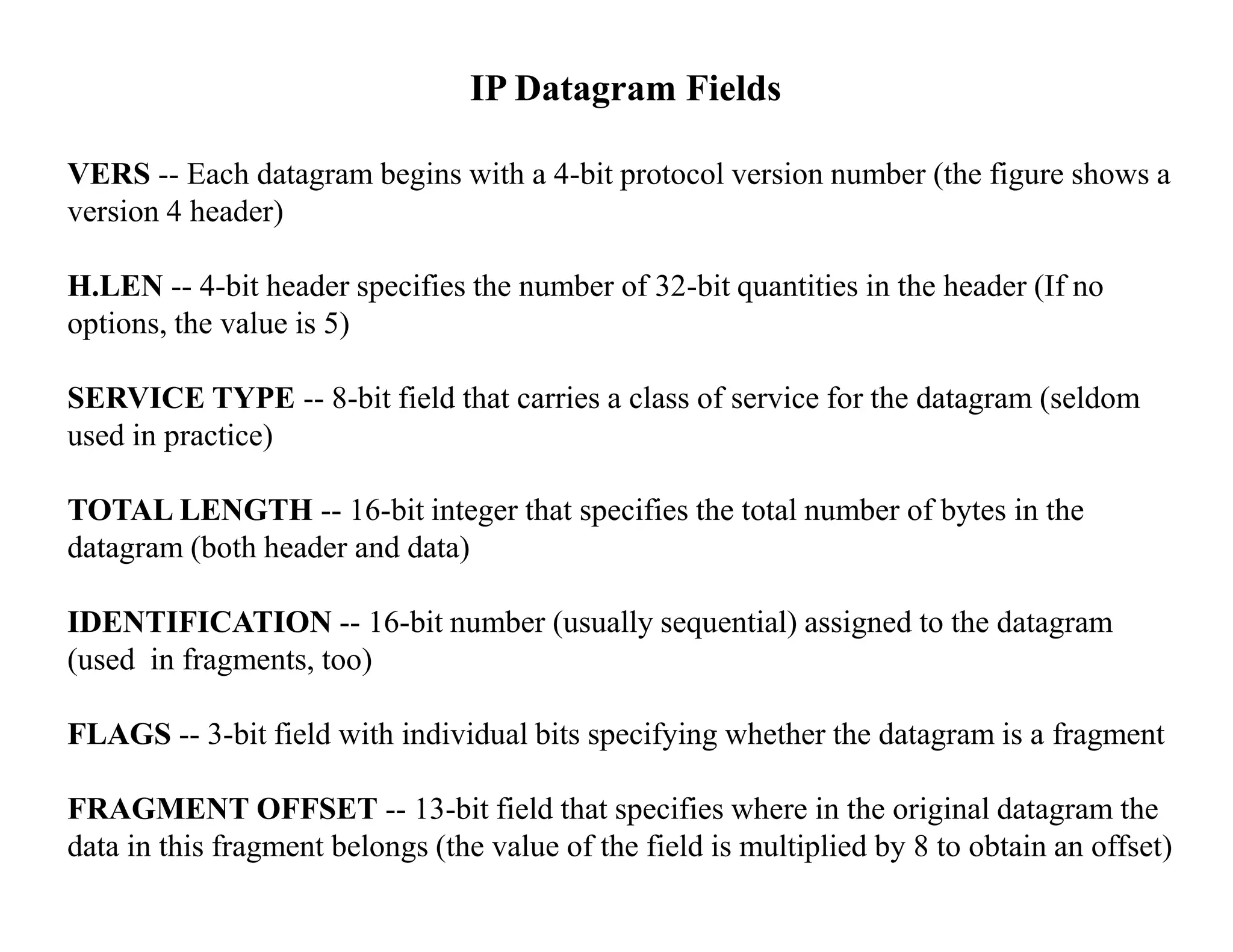
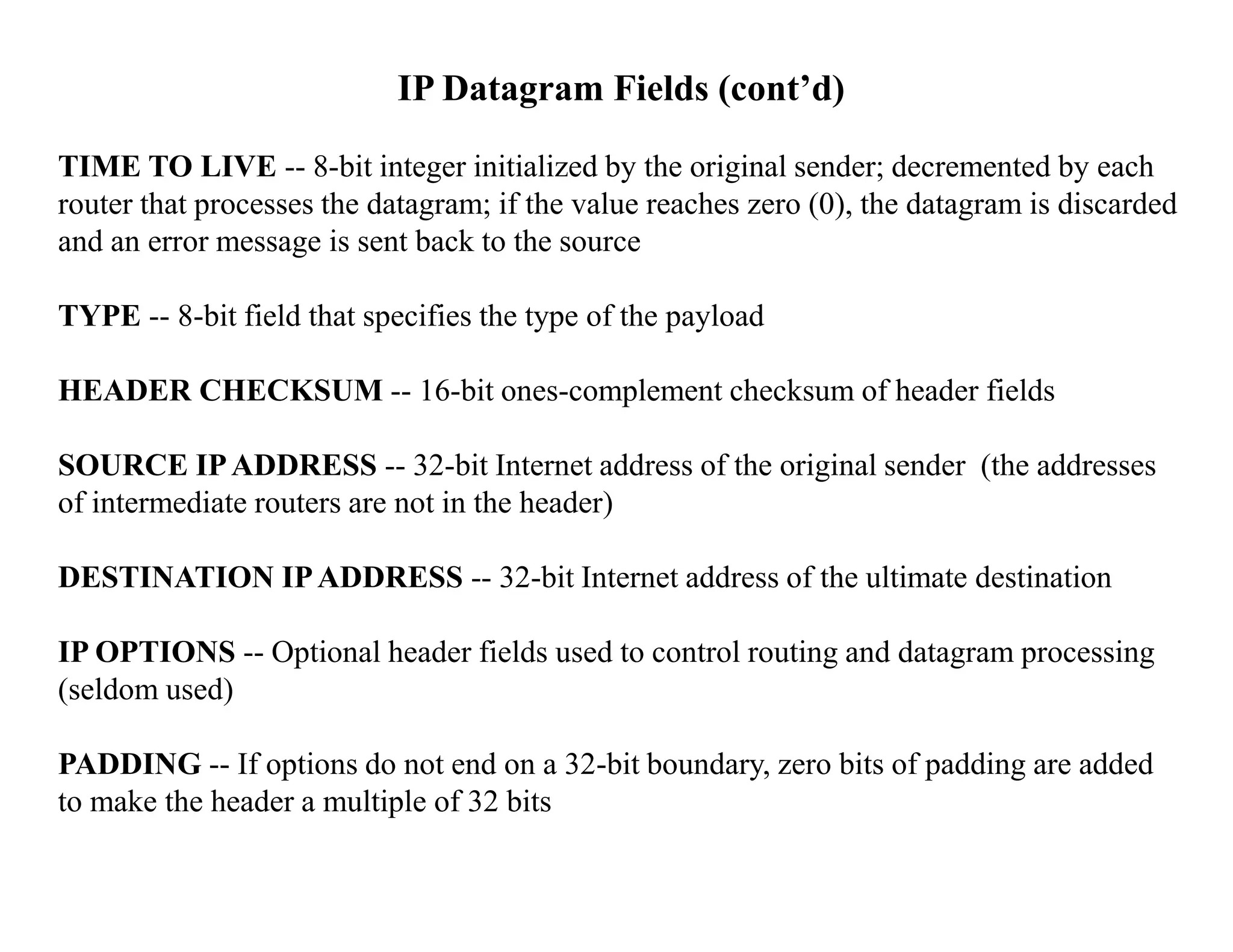
IP datagrams are forwarded across the internet through a process of encapsulation and forwarding. Routers along the path encapsulate each IP datagram within a link layer frame and forward it based on the destination address. If a datagram is larger than the maximum transmission unit of the outgoing link, routers fragment it into smaller pieces that are reassembled by the destination host. Forwarding tables allow routers to determine the next hop for each datagram using longest prefix matching.



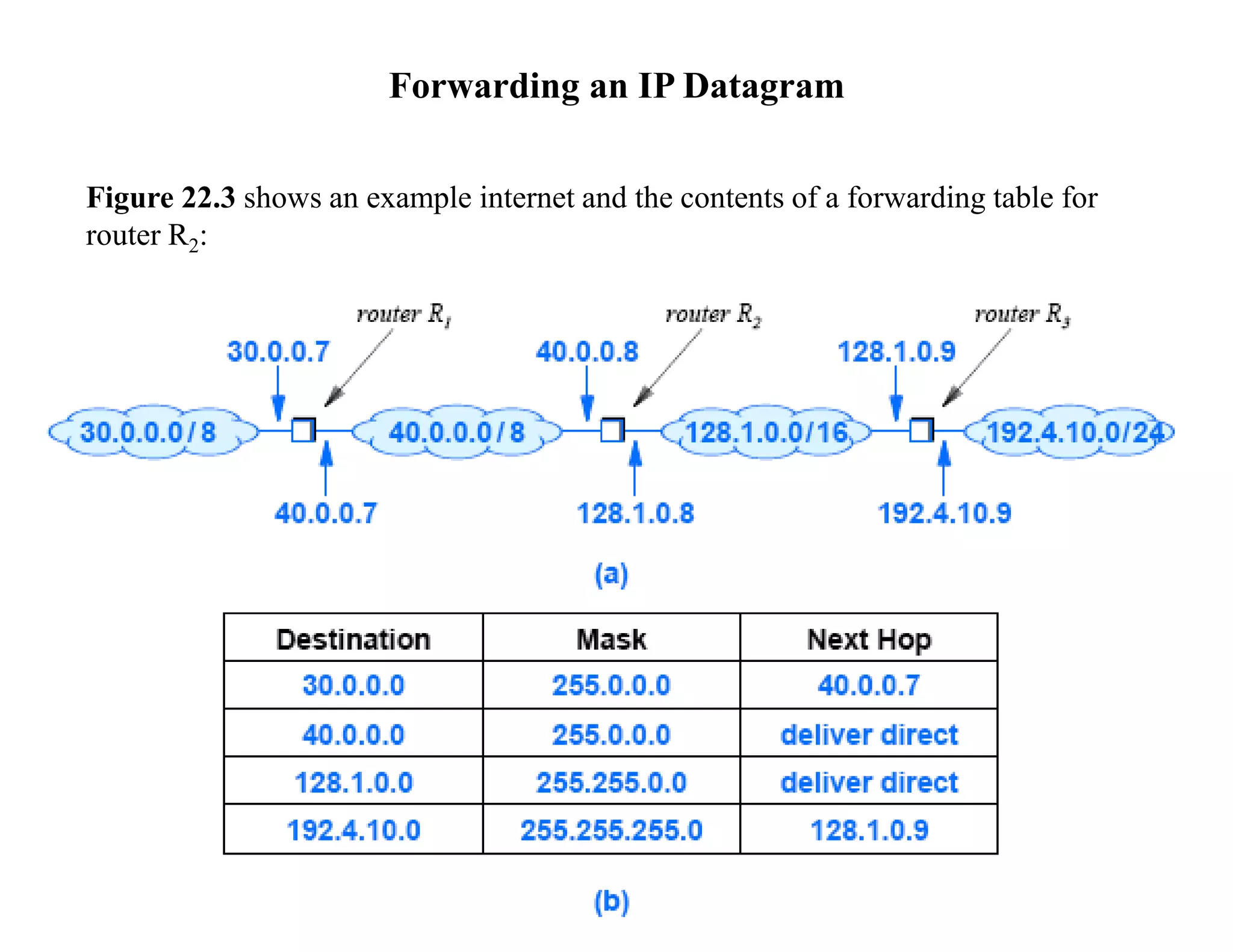

![Network Prefix Extraction (cont’d)
The bit mask representation makes extraction efficient:
• the computation consists of a Boolean & between the mask and destination
address, D
The computation to examine the ith entry in the table can be as:
if ( (Mask[i] & D) == Destination[i] ) forward to NextHop[i]](https://image.slidesharecdn.com/474-22-datagramforwarding-230806174142-8b72dbc3/75/474-22-DatagramForwarding-pptx-11-2048.jpg)