The document discusses various functions and design issues related to the data link layer, including:
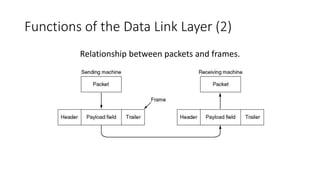
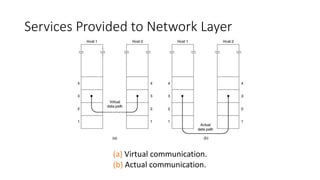
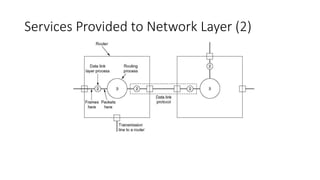
1. The data link layer provides services like framing, error control, and flow control to regulate data transmission between network layers.
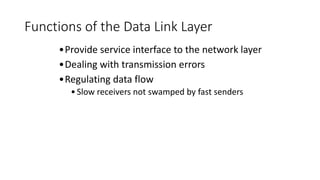
2. Functions of the data link layer include providing an interface to the network layer, dealing with transmission errors, and regulating data flow to prevent fast senders from swamping slow receivers.
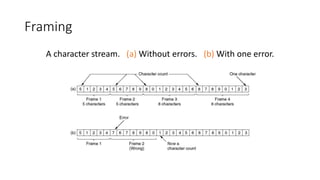
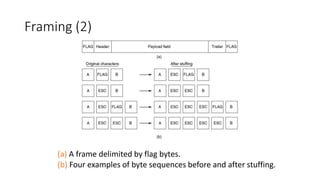
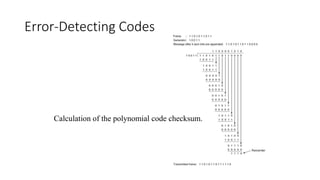
3. The document discusses various data link layer techniques for framing, error detection, error correction, and flow control including bit stuffing, parity schemes, CRC schemes, and error-correcting codes.