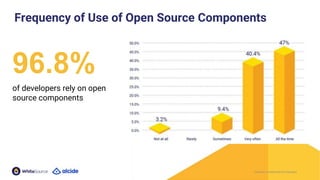
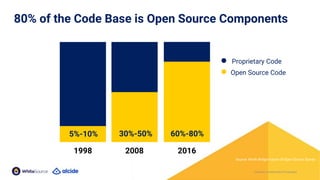
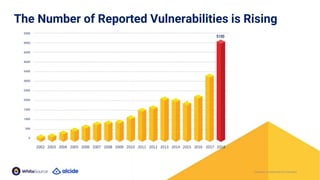
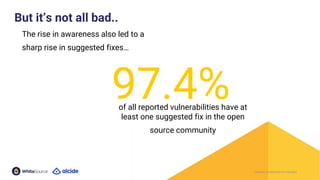
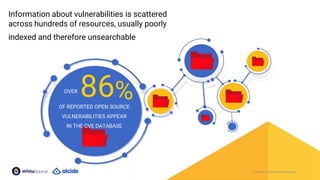
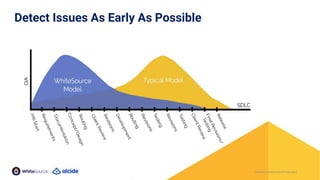
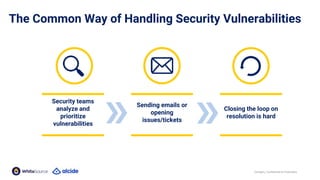
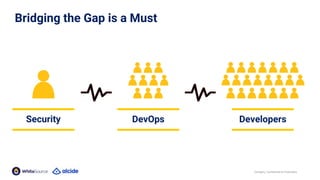
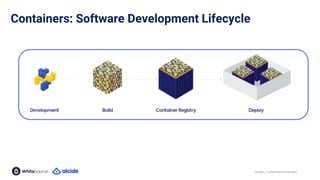
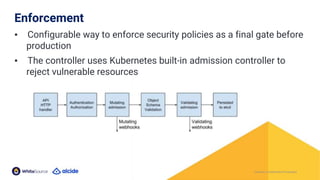
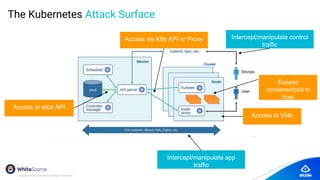
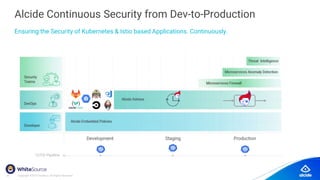
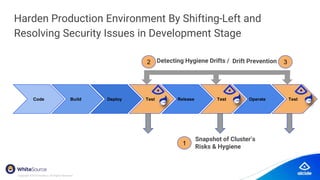
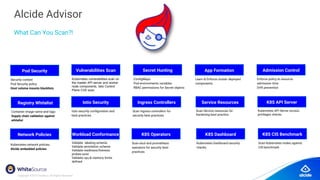
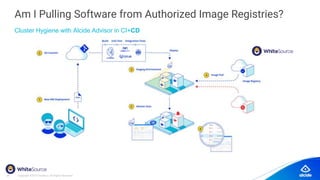
The document discusses the importance of Kubernetes security, emphasizing the reliance on open-source components in software development and the rising number of vulnerabilities. It highlights best practices for handling vulnerabilities, integrates security into existing workflows, and offers specific tools like Alcide Advisor for ensuring continuous security from development to production. The agenda includes an overview of handling vulnerabilities, a demo of Alcide Advisor, and discusses strategies for maintaining secure Kubernetes environments.