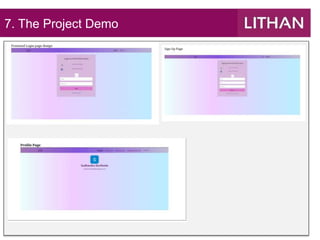
This document summarizes an API module project. It discusses tools used like React JS and Spring Boot. It defines an API as an interface that allows applications to interact without user intervention. The role of APIs is to enable data exchange between applications. Potential security issues with APIs include injection attacks, DoS attacks, sensitive data exposure, broken authentication, broken access control, and man-in-the-middle attacks. The project requirements are to develop a 'Know Your Neighborhood' app that allows login/signup using existing APIs. The strengths and weaknesses of the project API and a security report are also discussed.