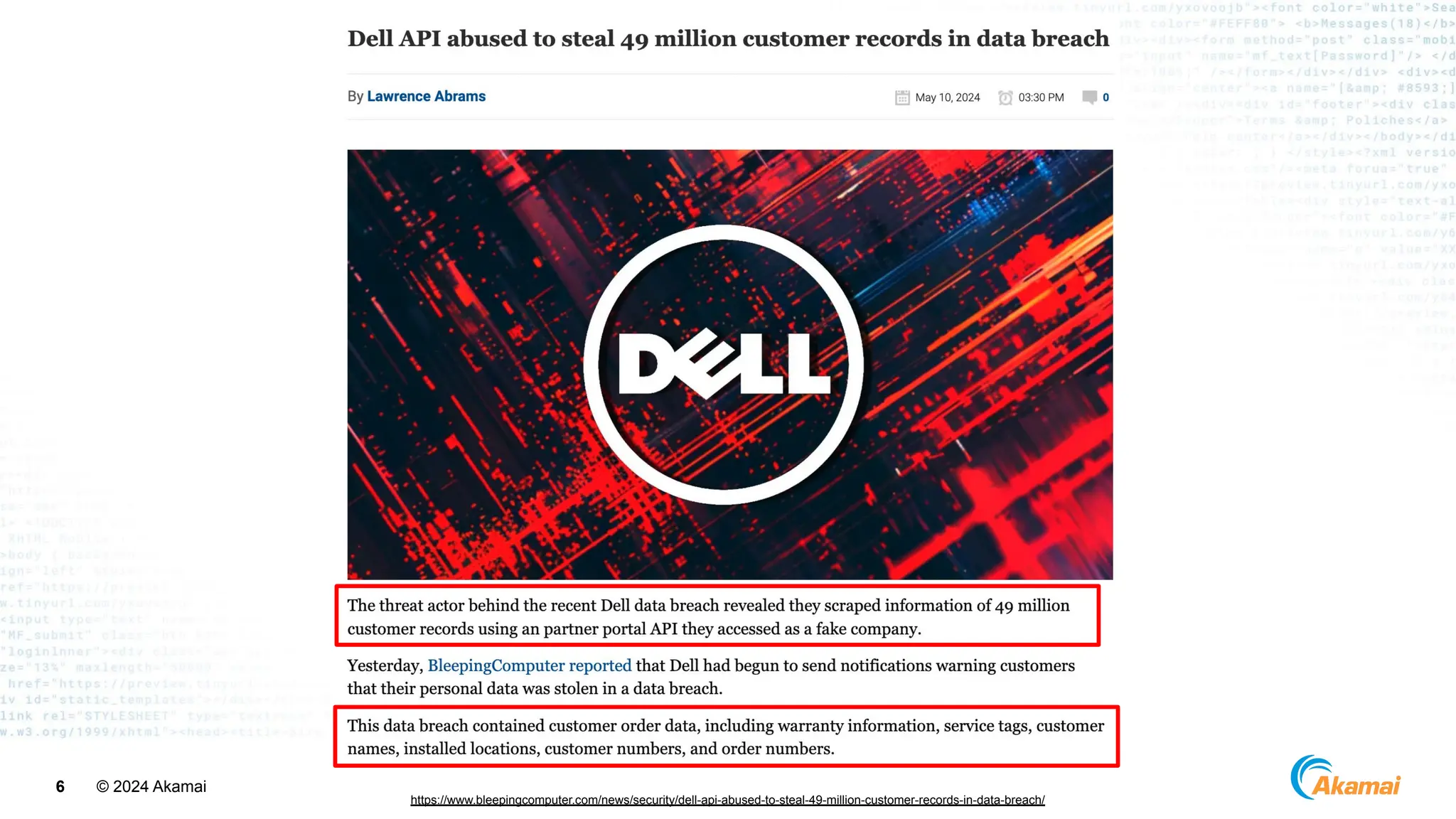
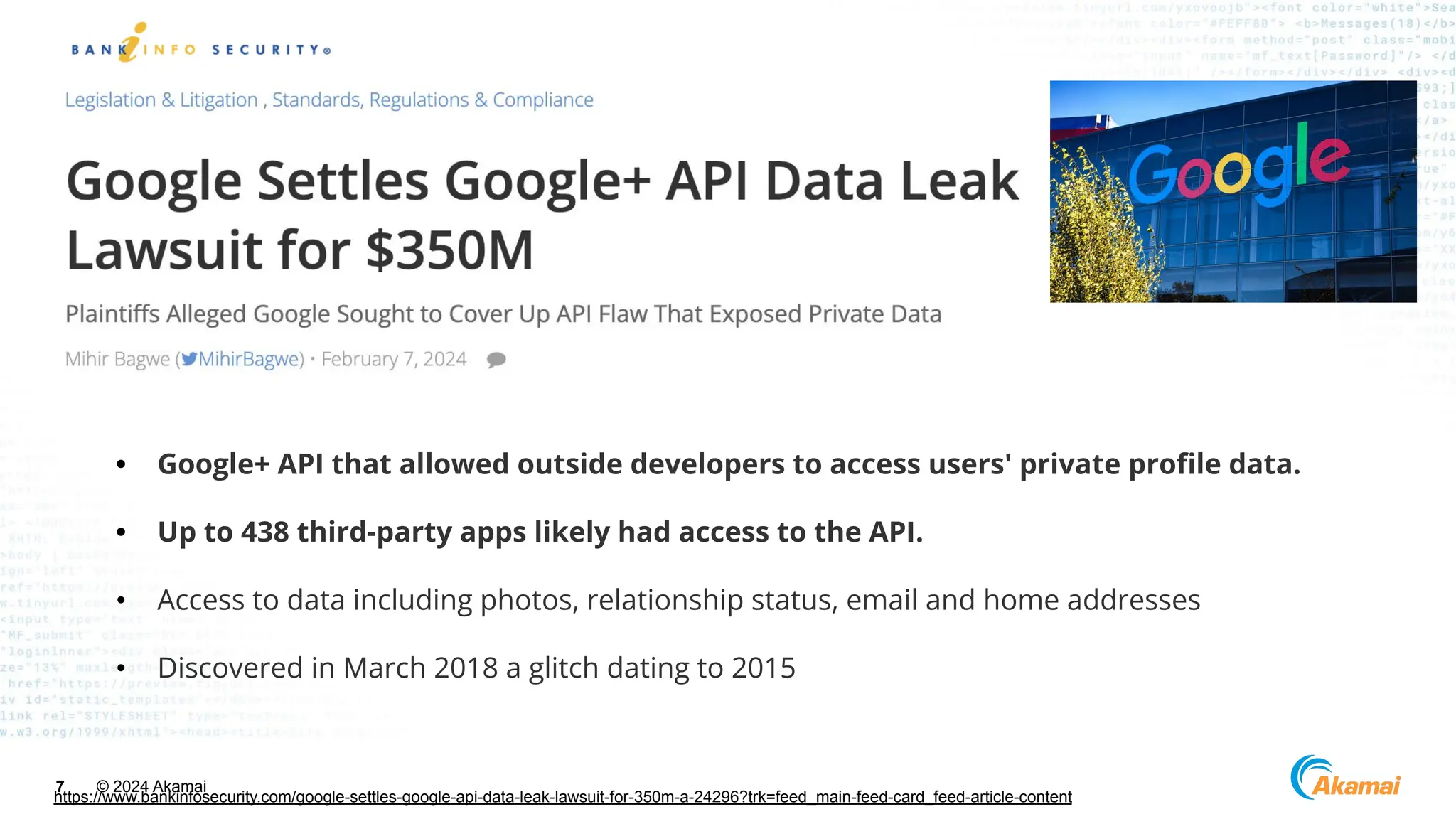
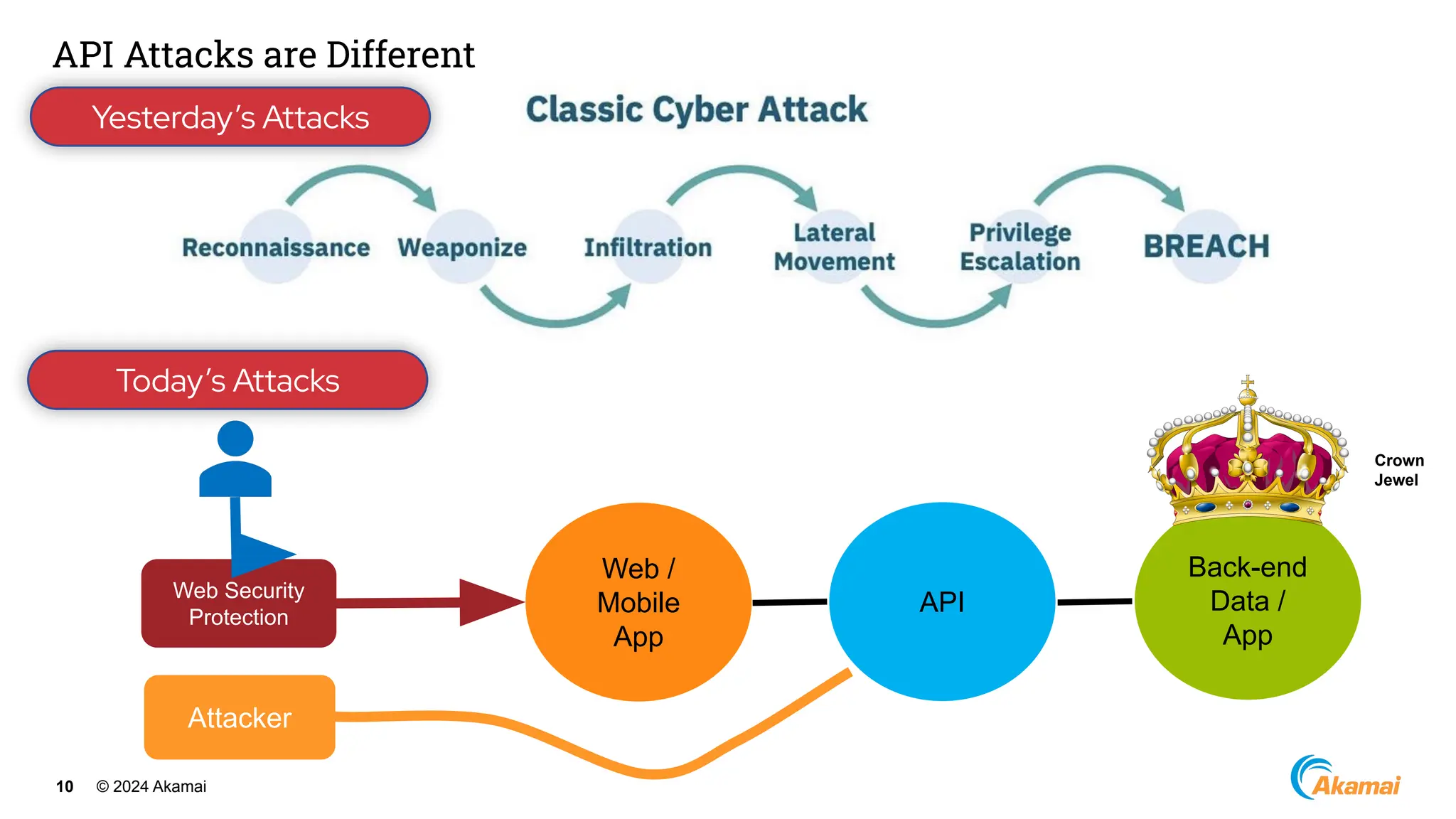
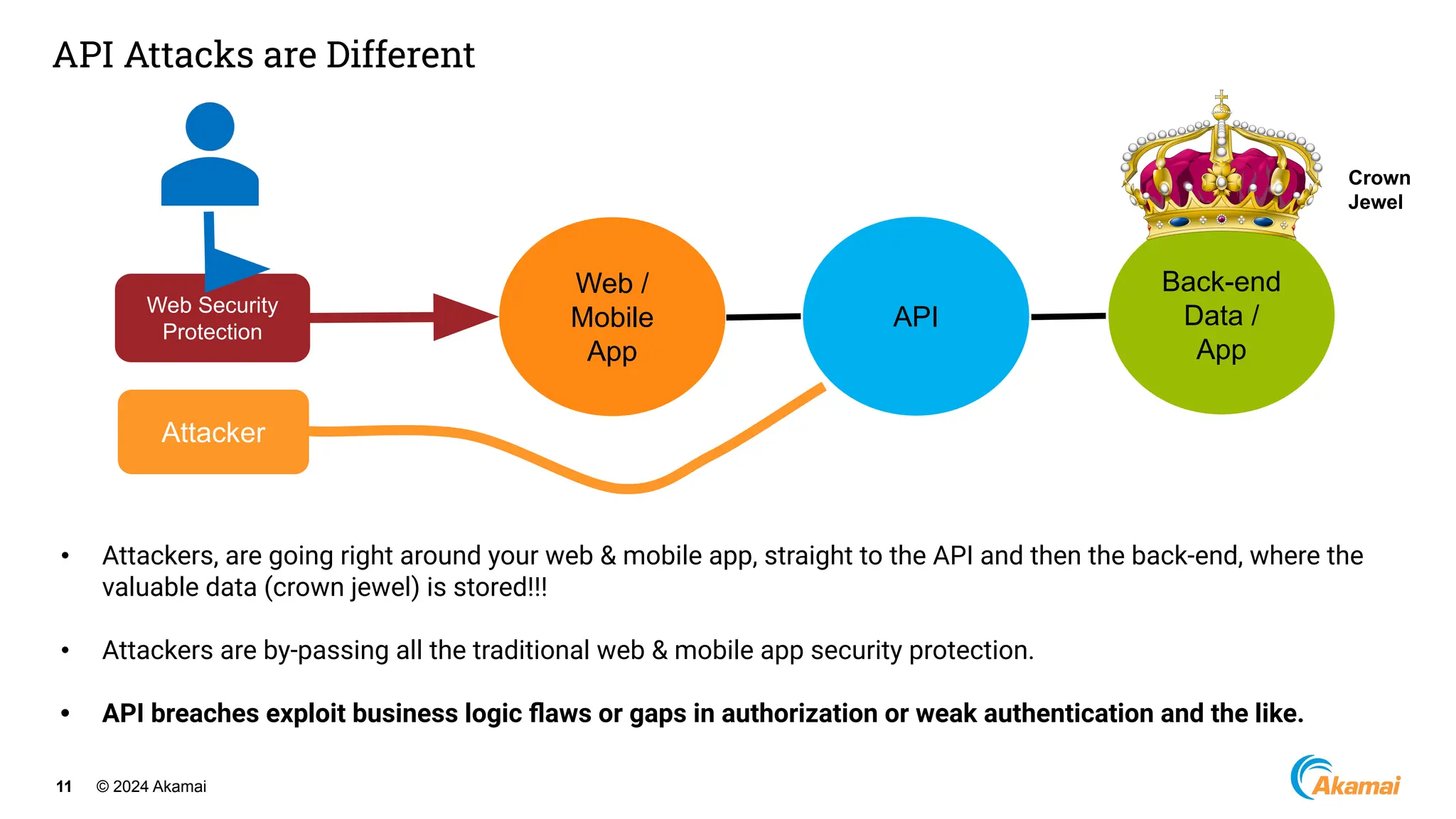
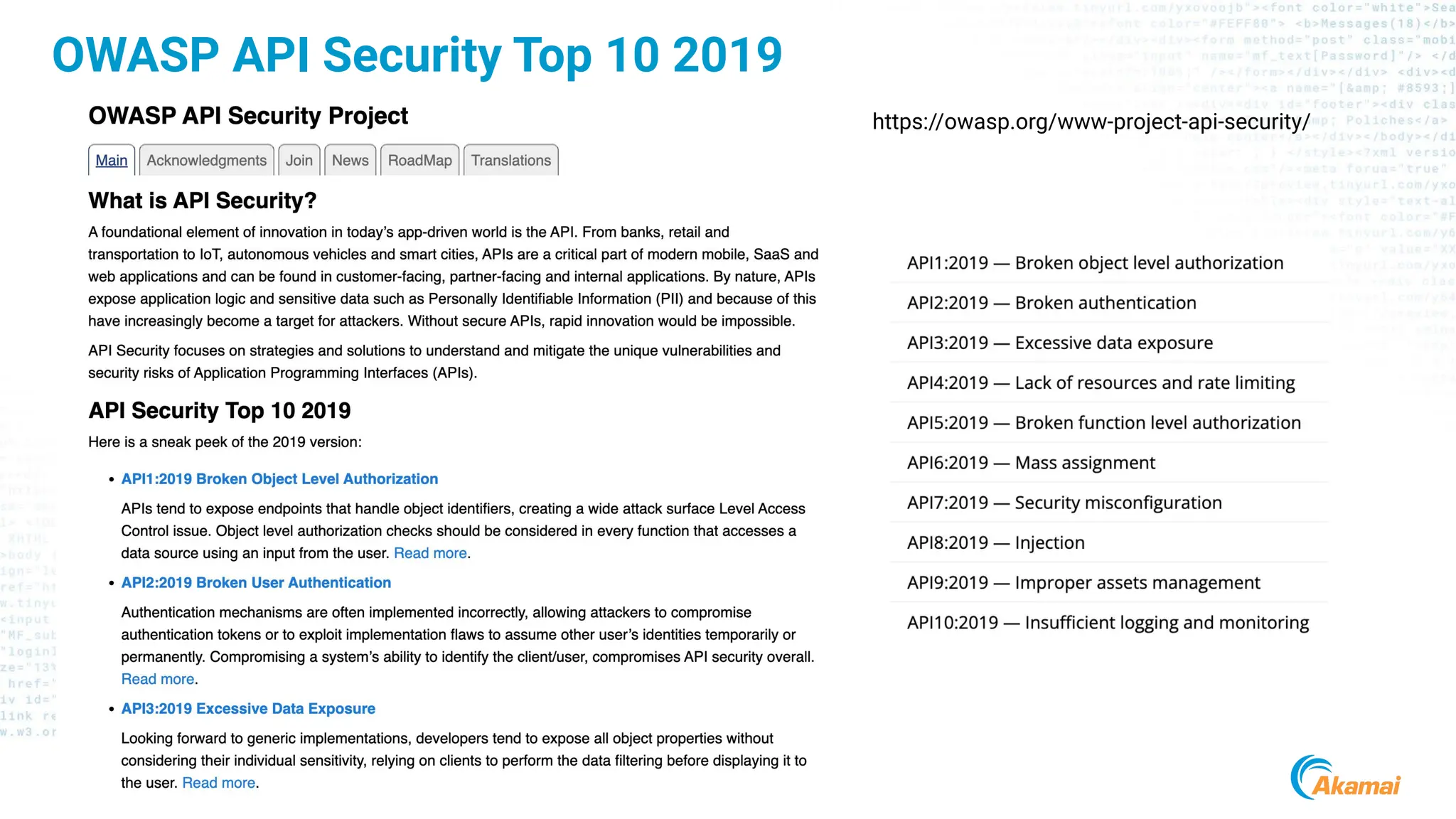
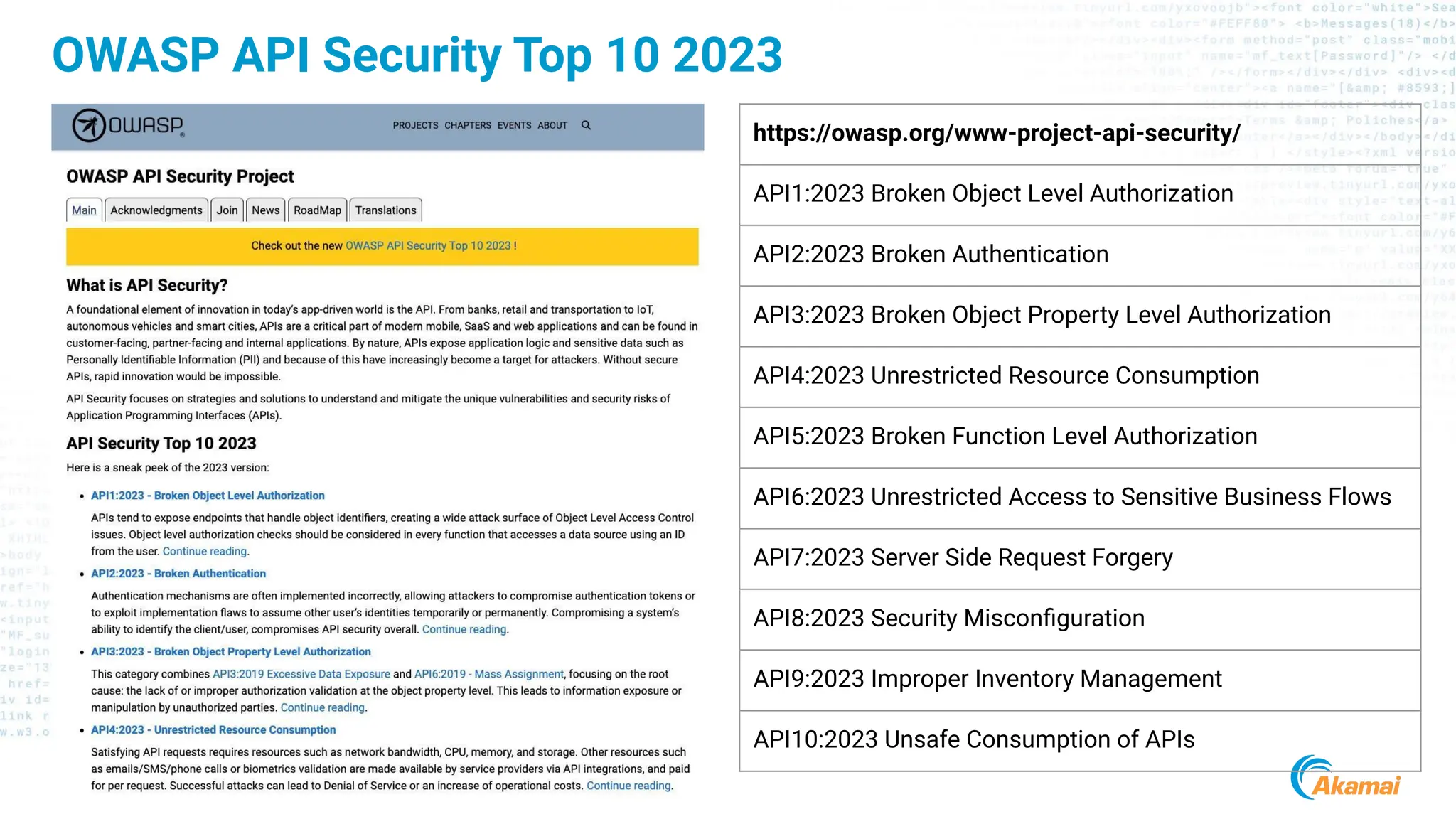
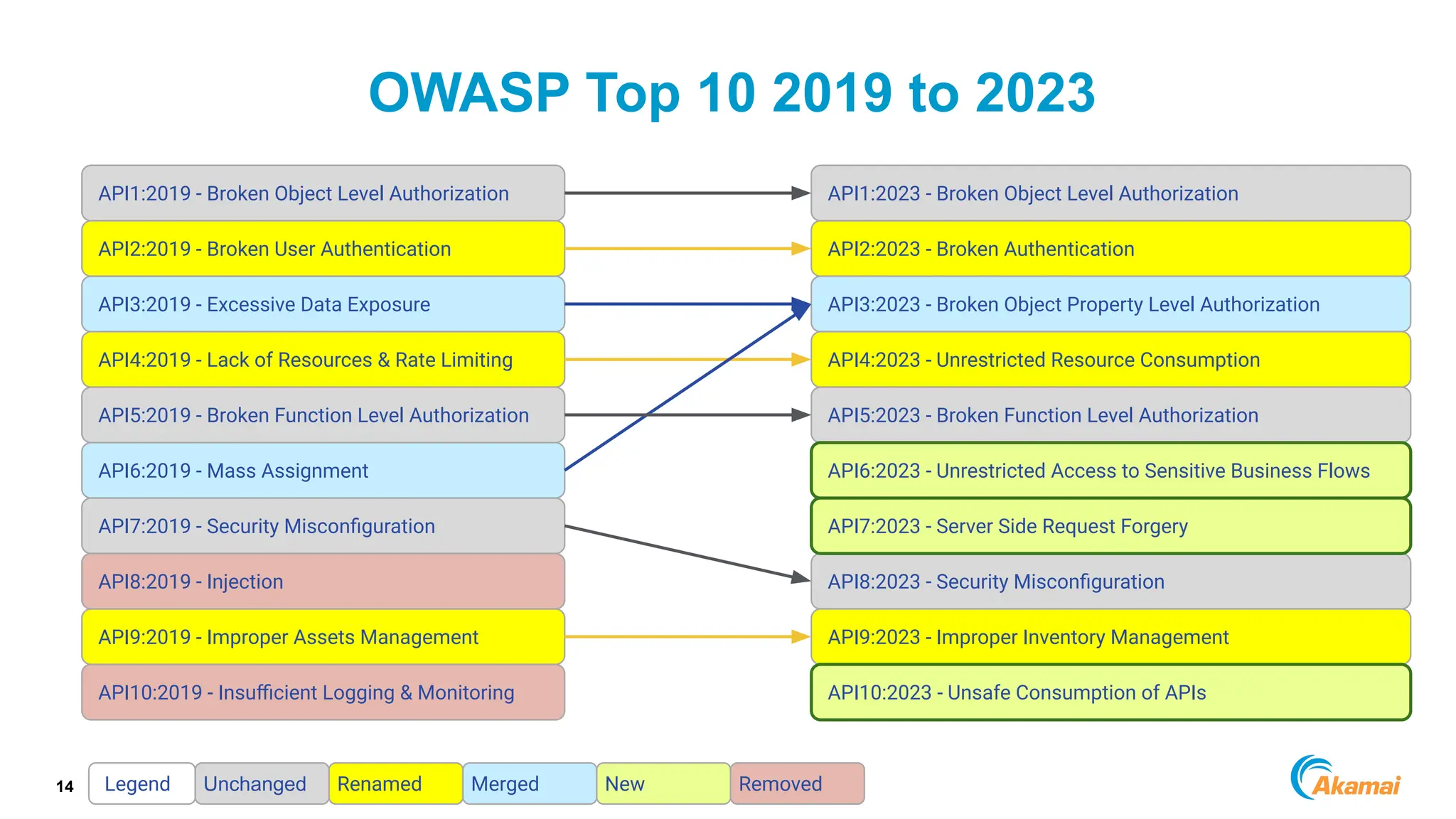
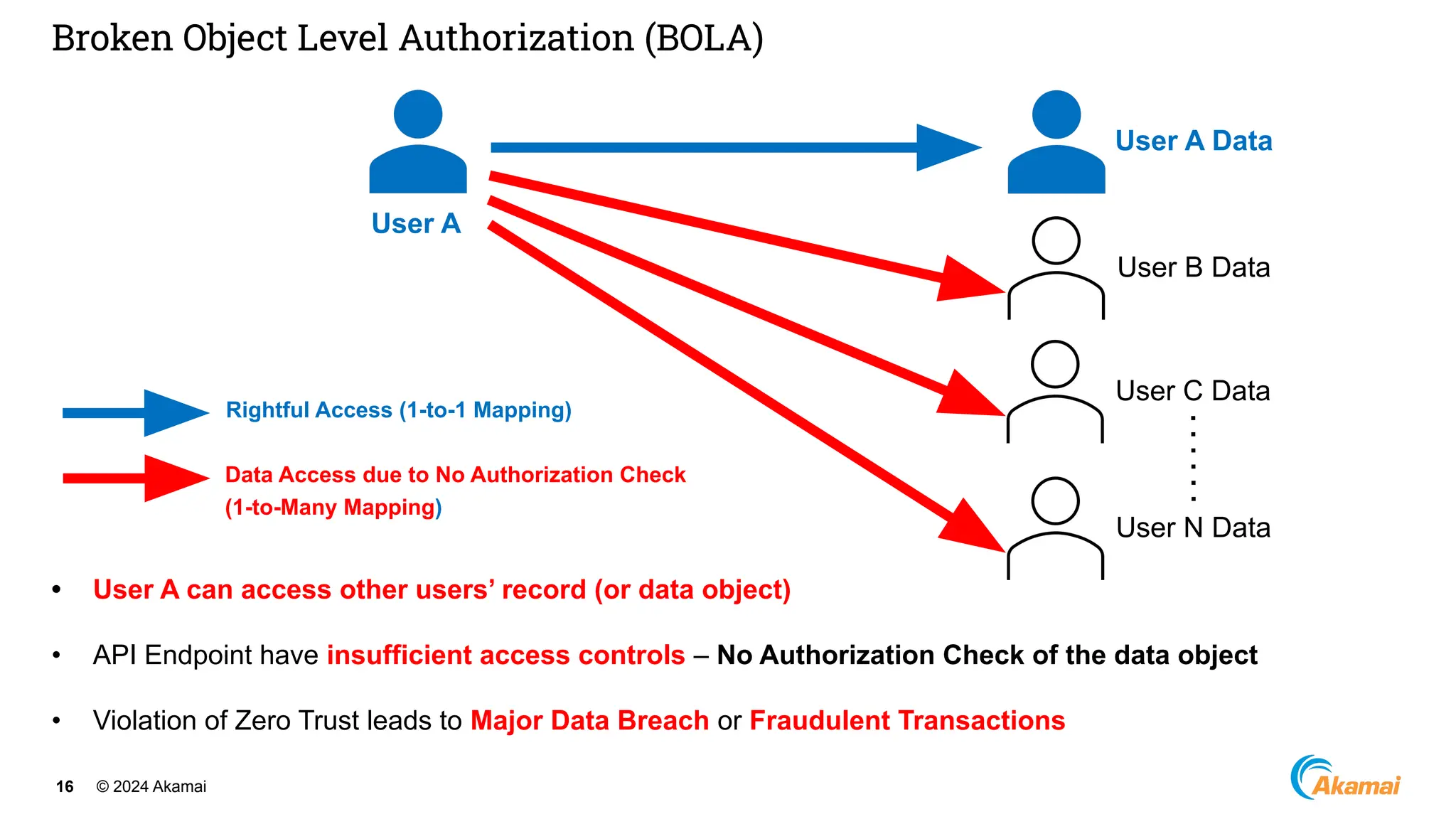
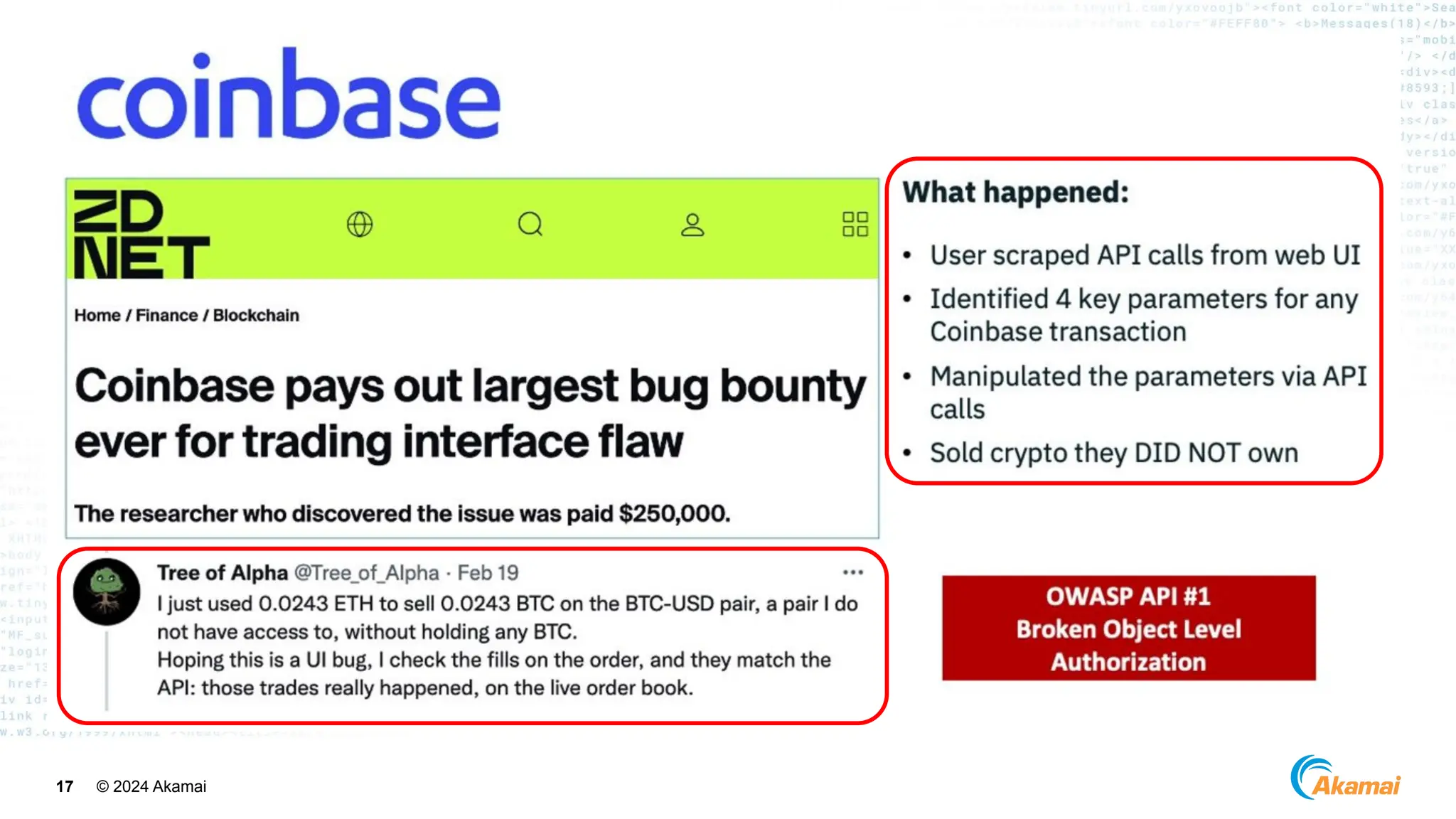
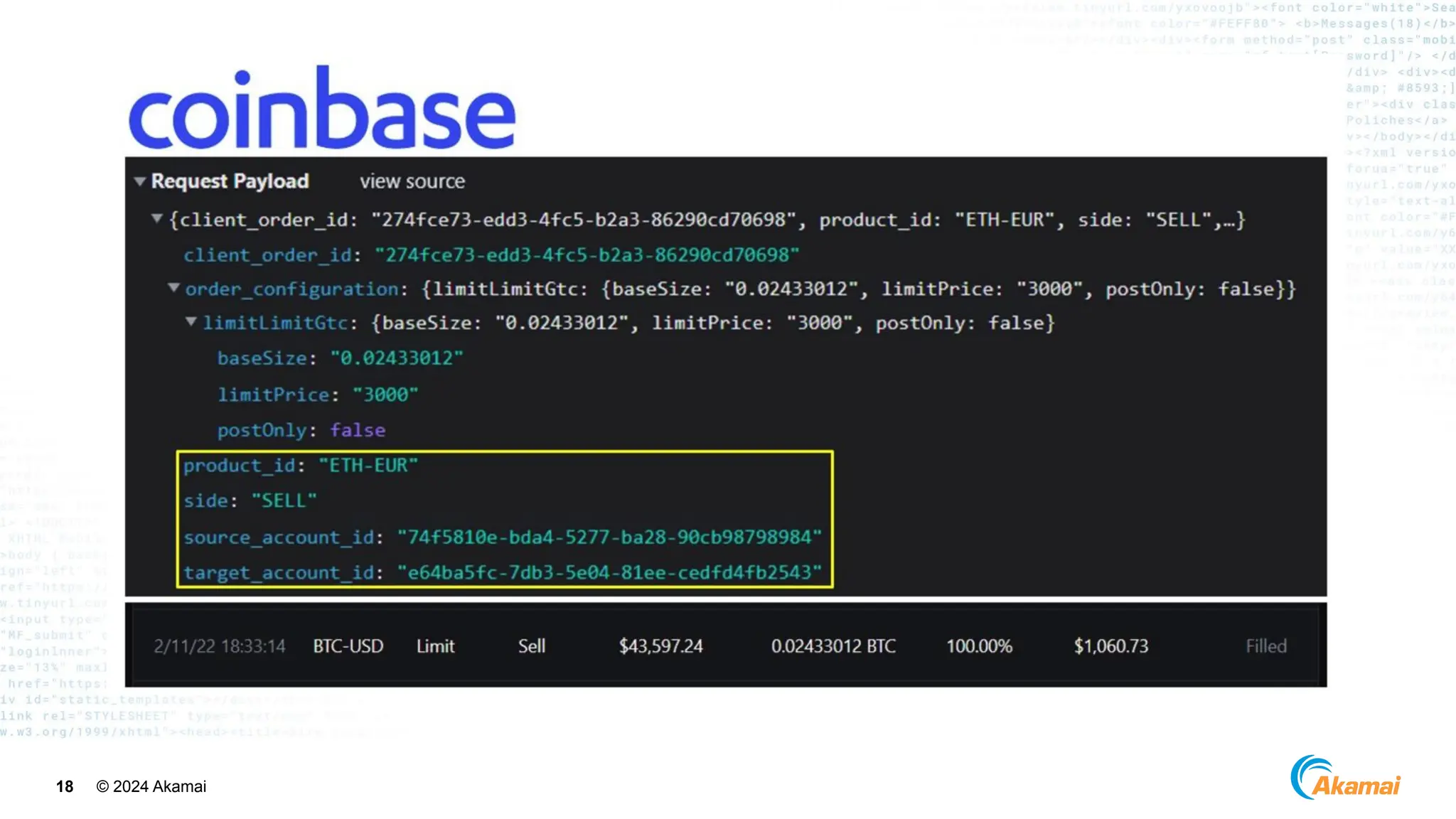
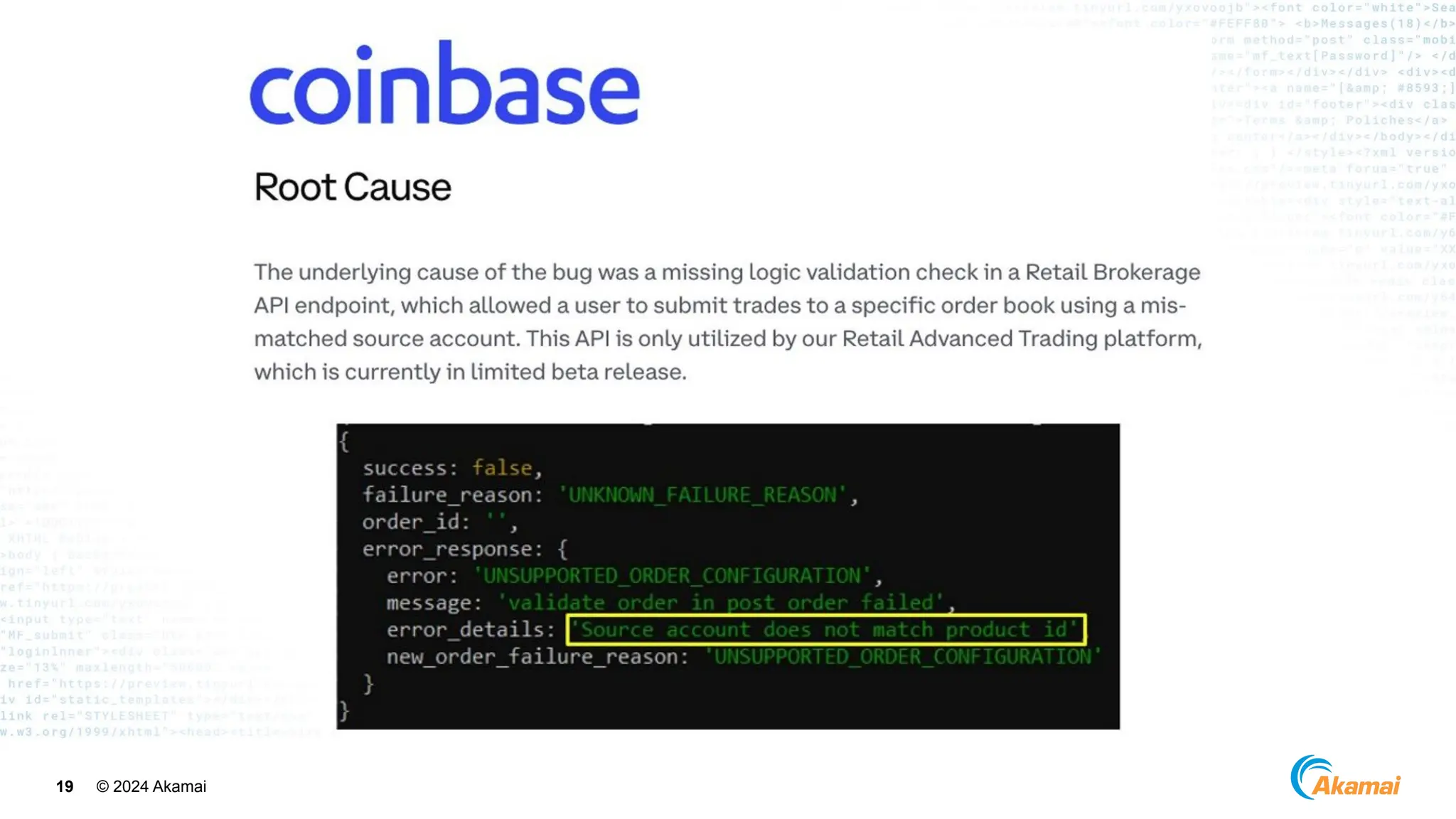
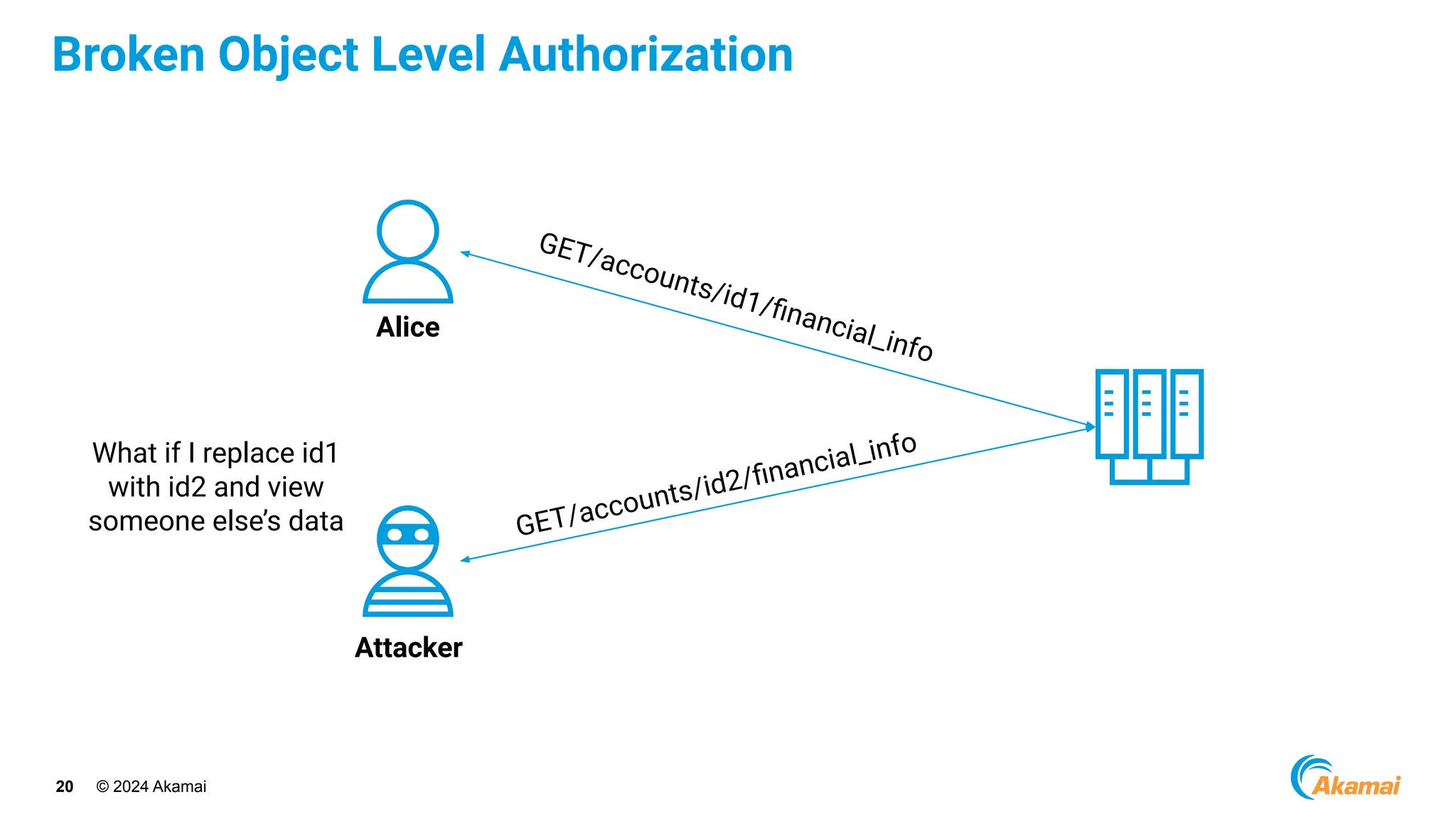
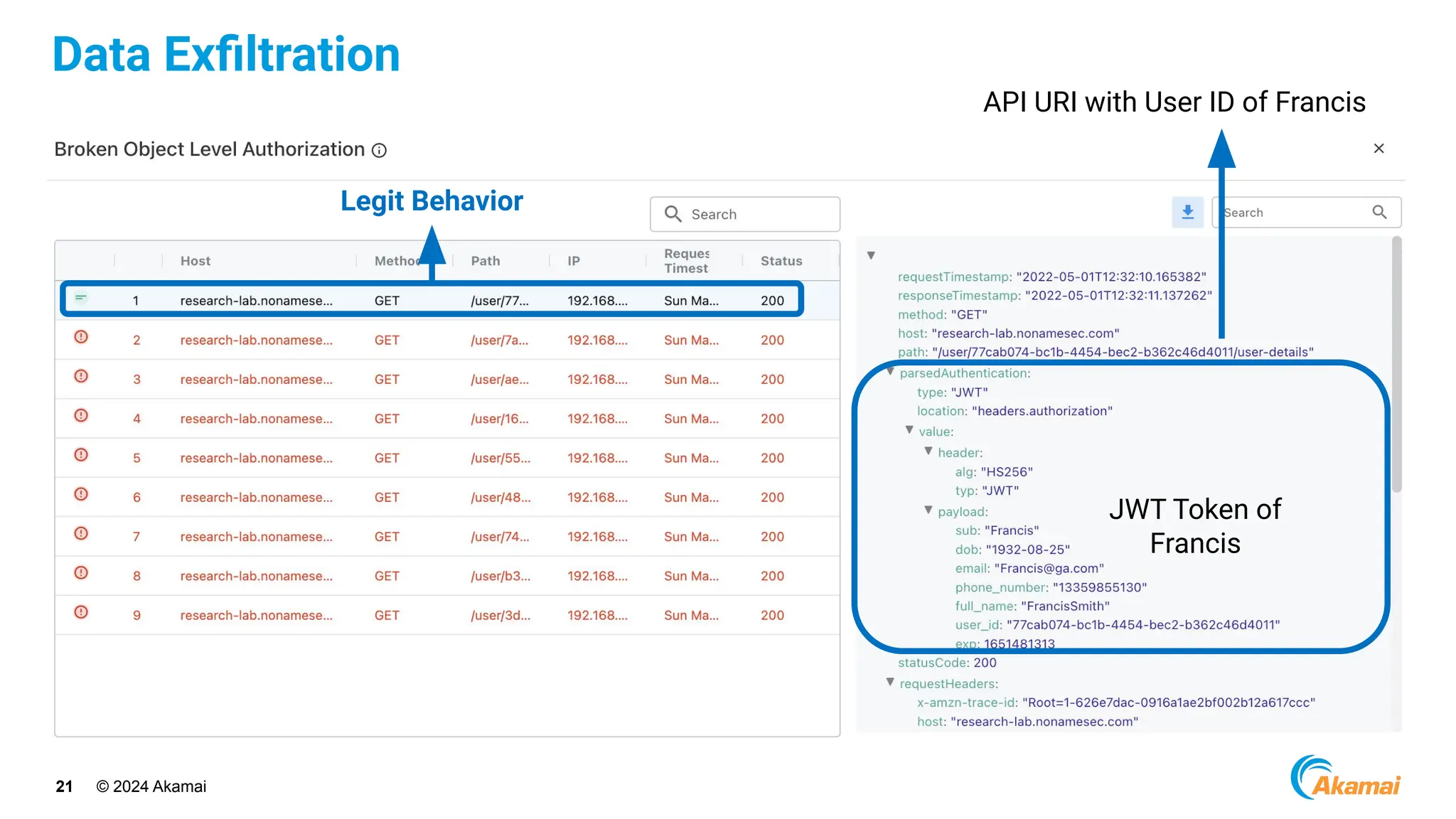
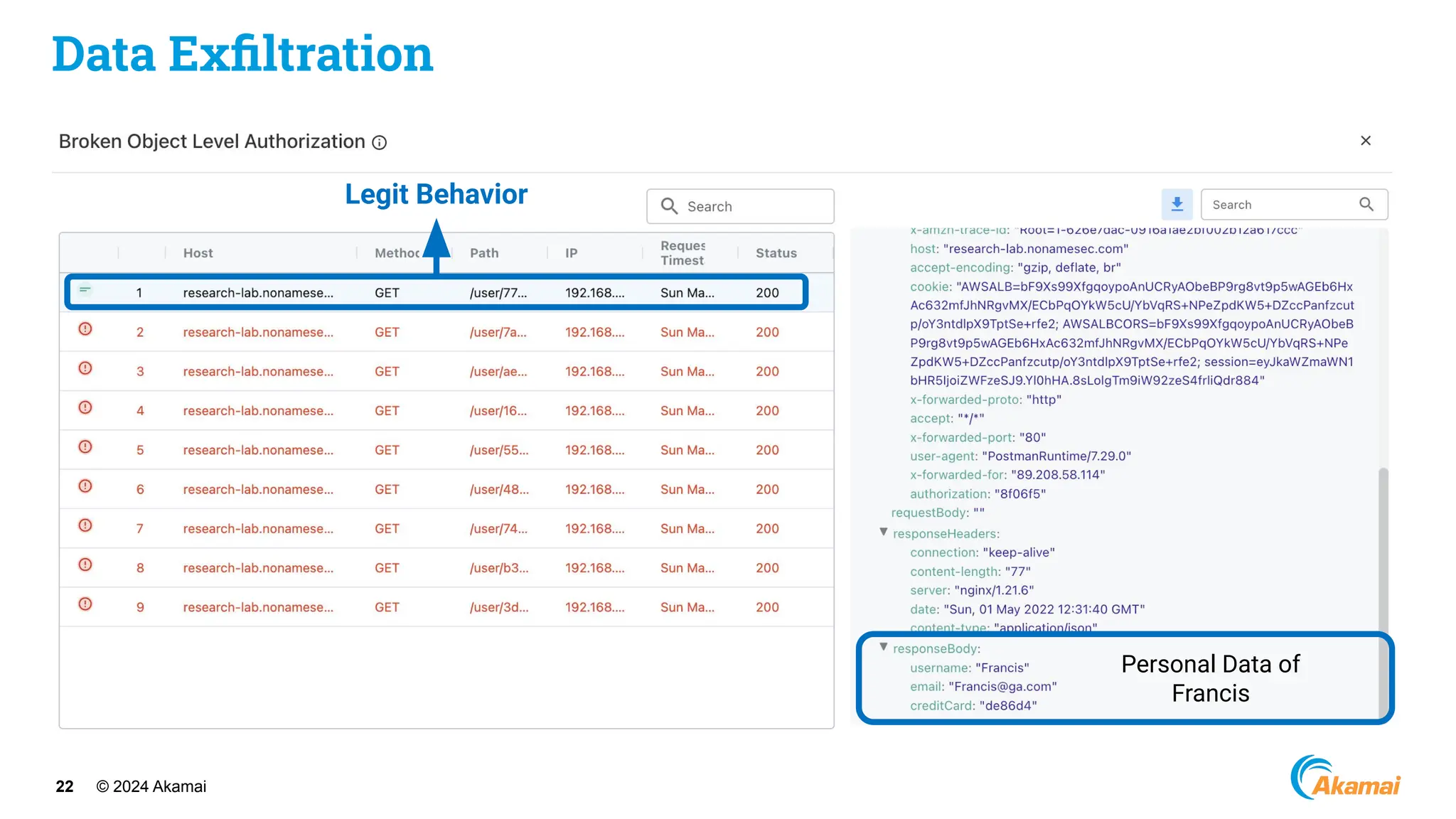
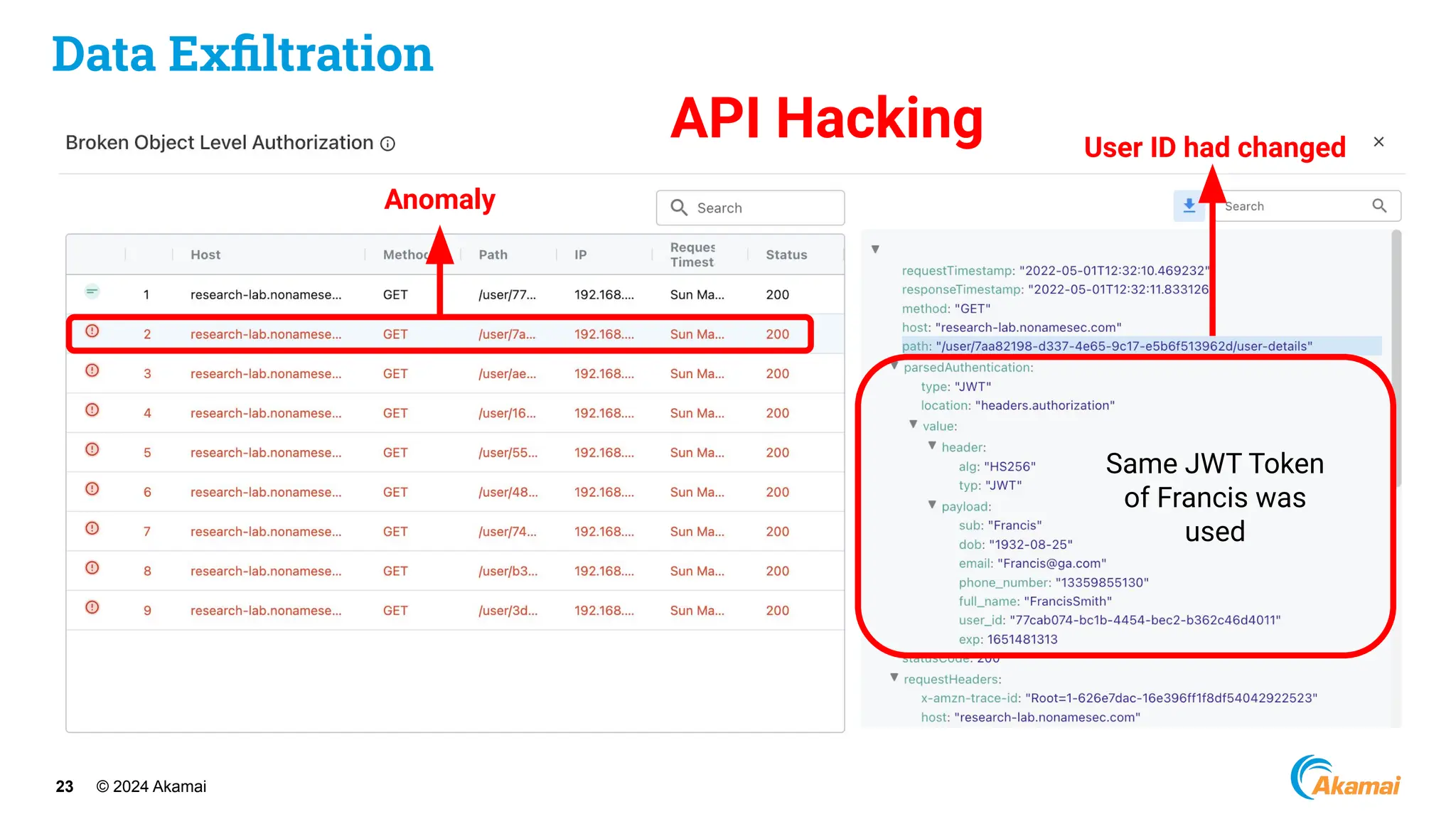
The document discusses API security best practices, highlighting real-world incidents of API-related breaches affecting organizations. It emphasizes the importance of robust authorization checks and outlines the OWASP API Security Top 10 vulnerabilities from 2019 to 2023. The Akamai API Security Platform is presented as a solution for detecting and mitigating API threats and vulnerabilities throughout the API lifecycle.






![© 2024 Akamai
27
© Akamai API Security. All rights
reserved.
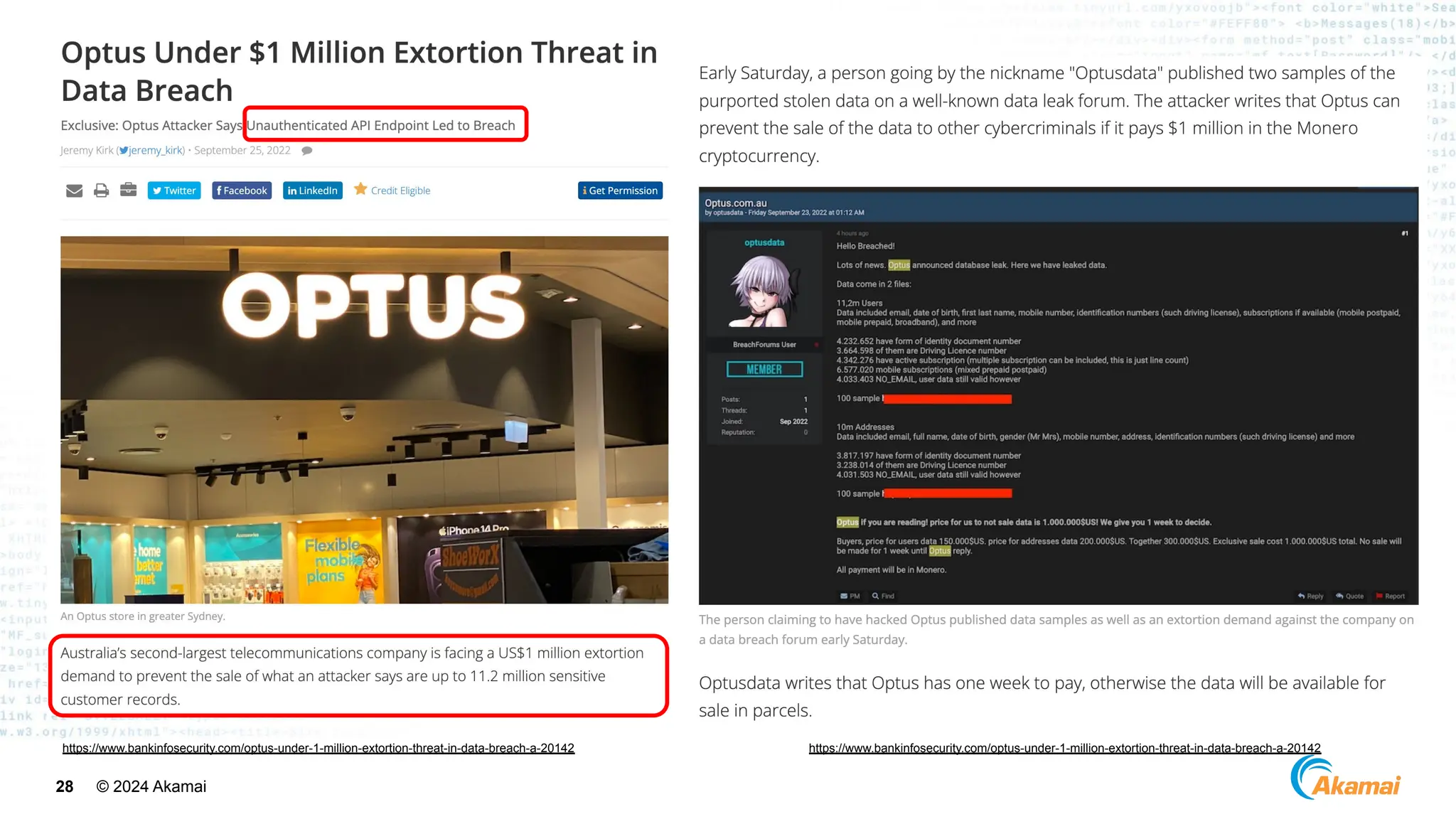
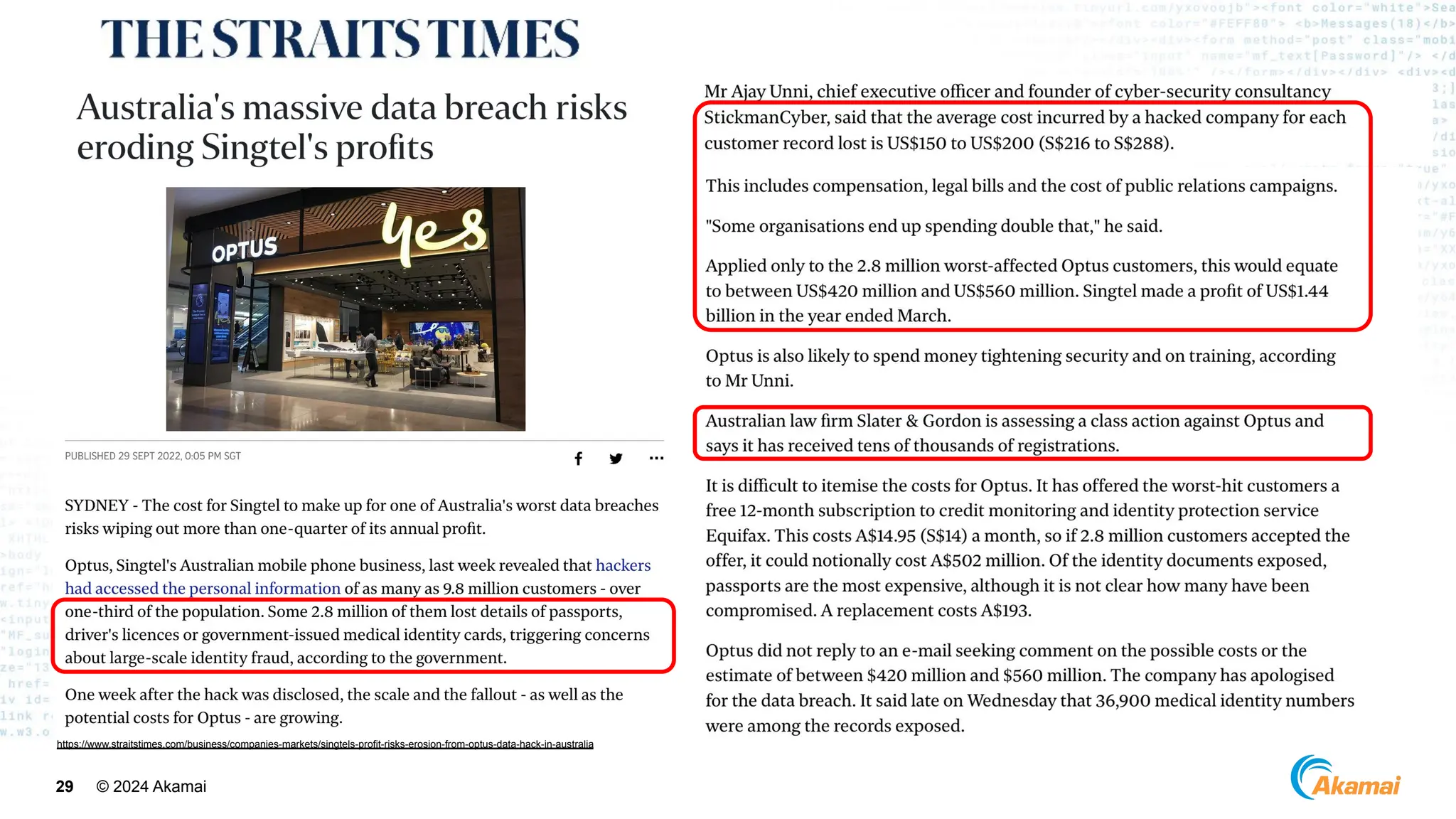
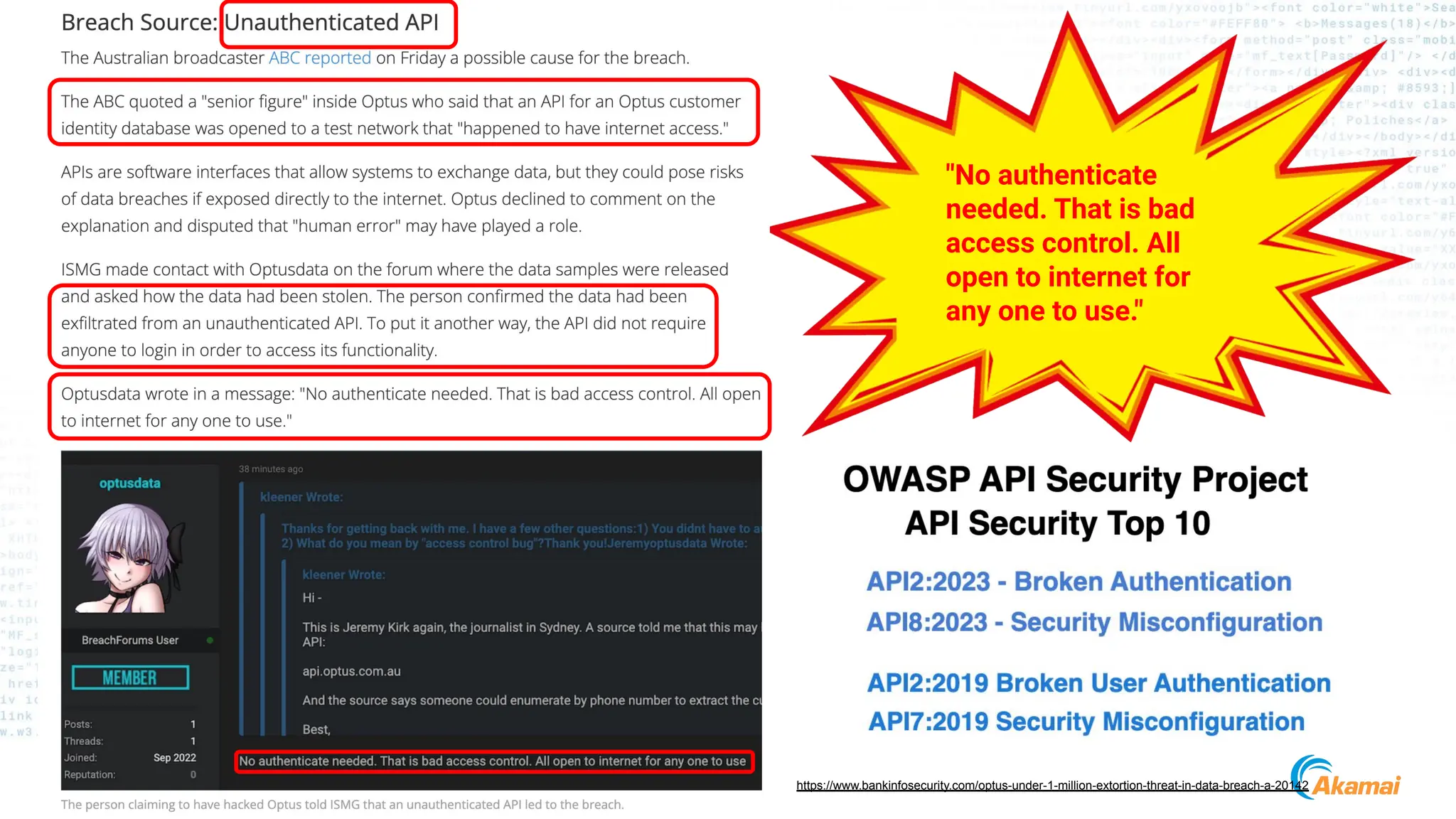
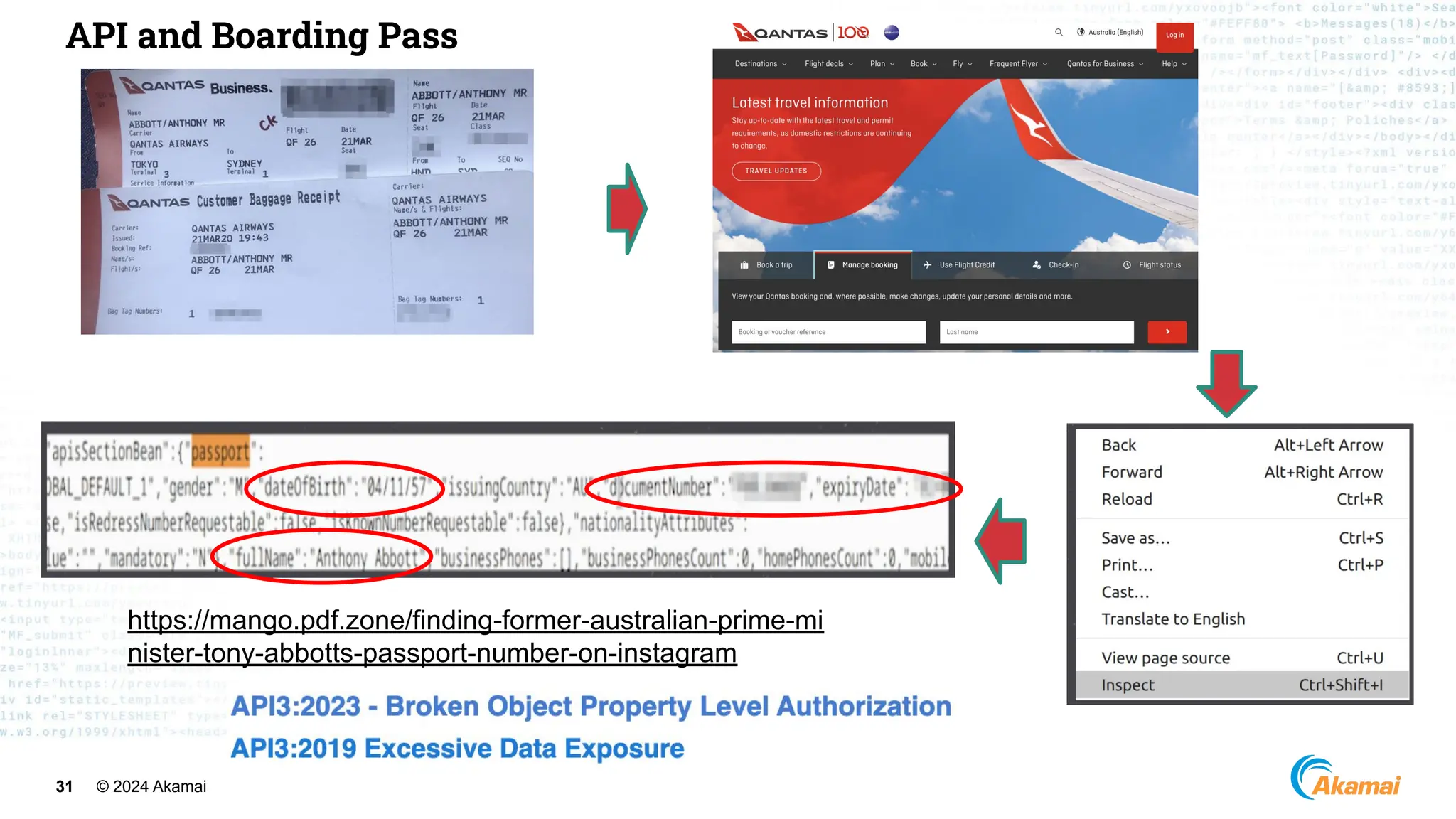
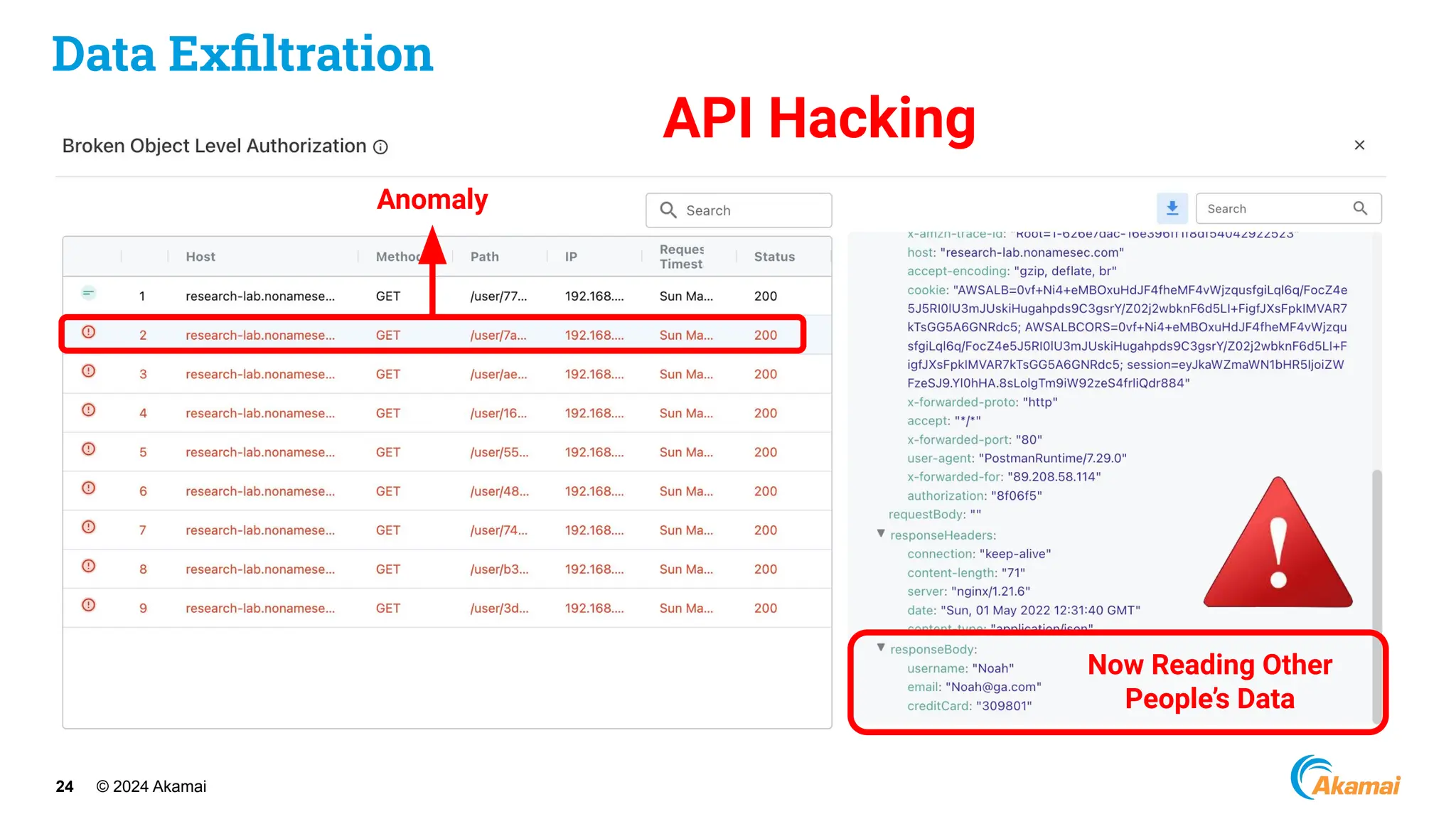
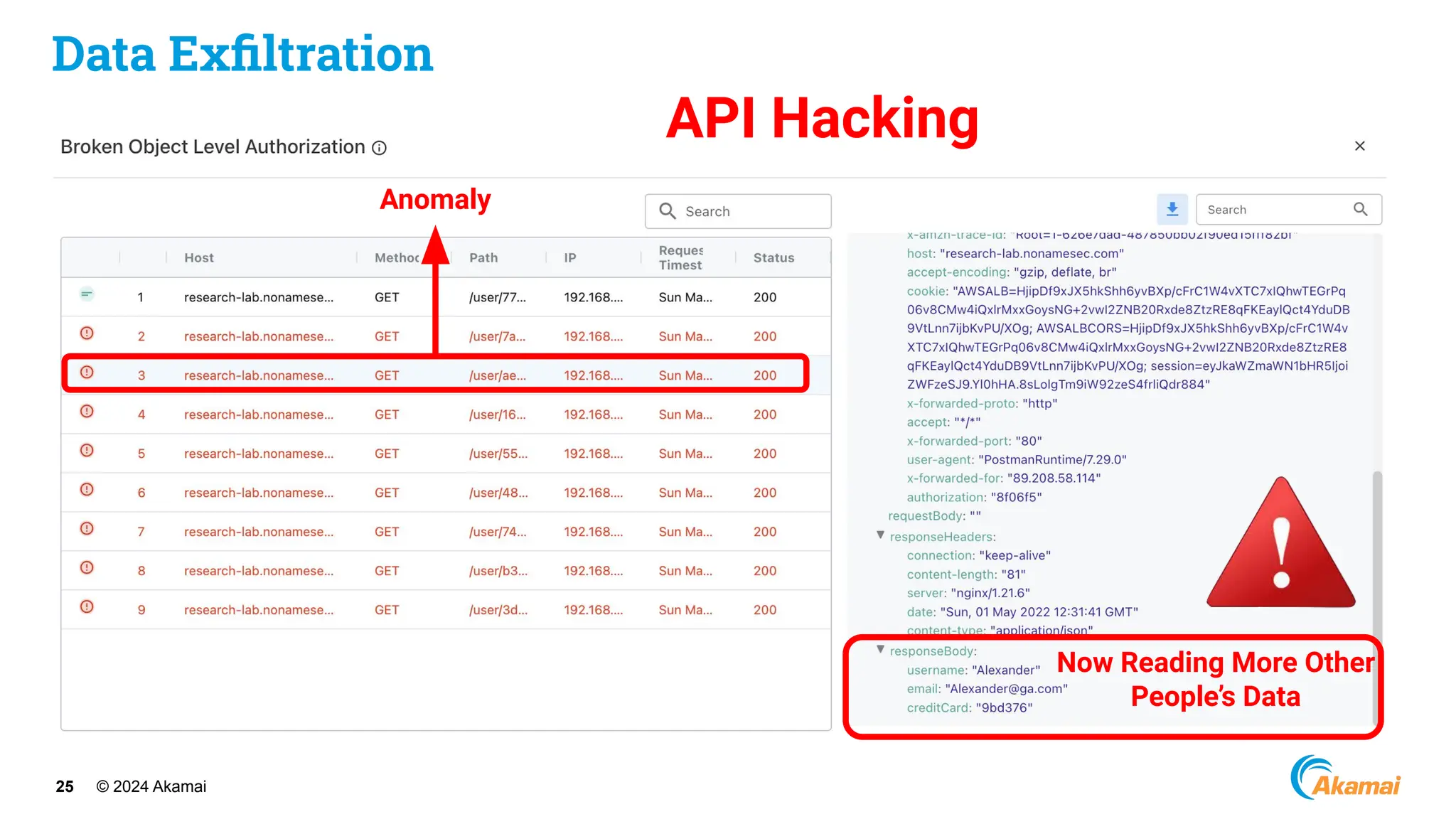
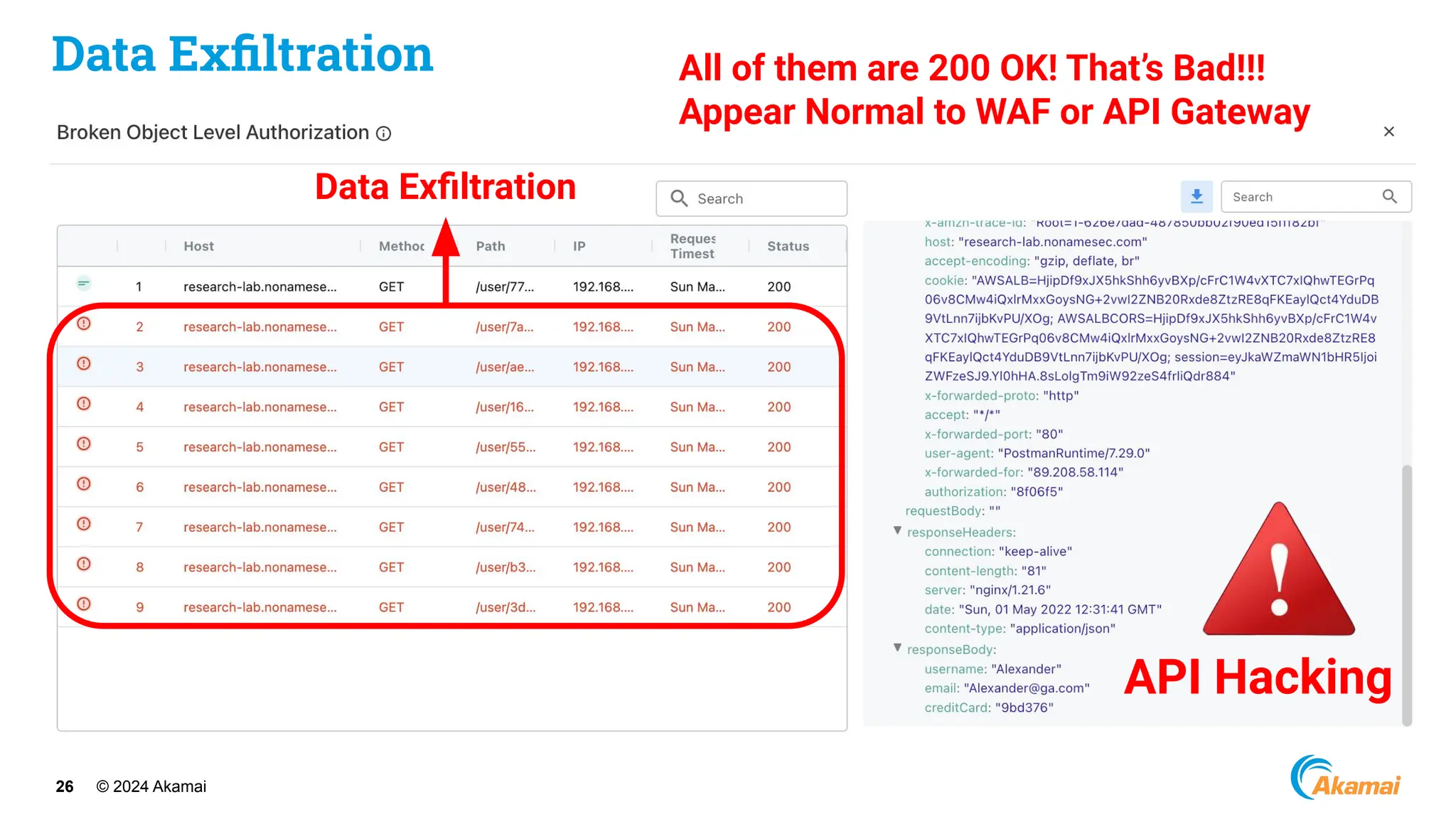
[ Optus Data Breach]
● Company: Optus
● Industry: Telco
● Impact: ~600M USD
● Vulnerability:
○ Unauthenticated, publicly exposed
API Endpoint
○ Excessive Data Exposure
○ Incrementing Customer Identifiers](https://image.slidesharecdn.com/akamaiapisecuritybestpractices-241003005801-ee2d4c54/75/Akamai_-API-Security-Best-Practices-Real-world-attacks-and-breaches-27-2048.jpg)