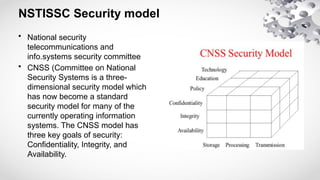
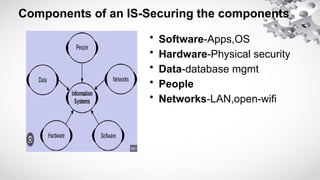
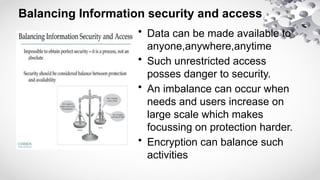
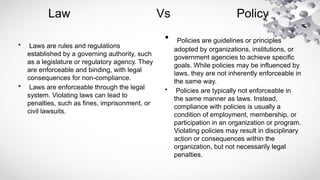
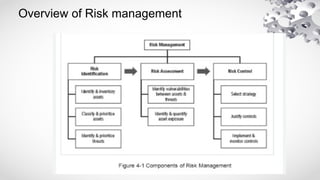
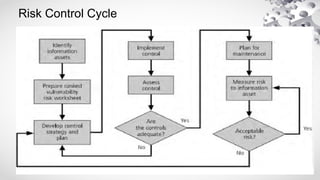
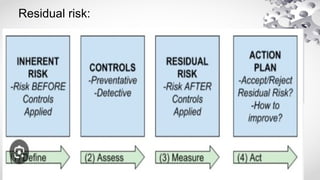
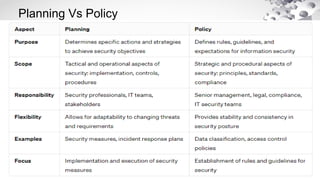
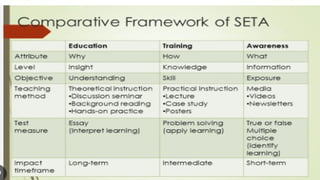
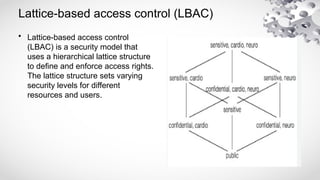
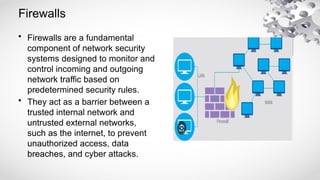
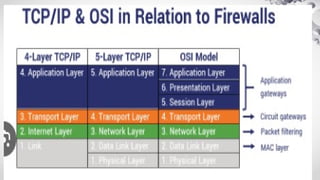
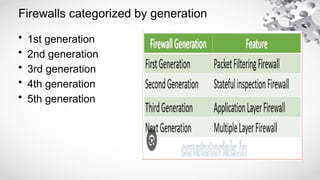
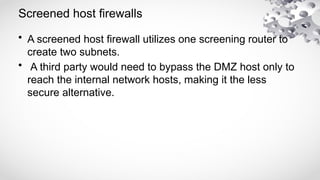
The document covers various aspects of information security, including its history, key components, and security models, emphasizing the importance of protecting sensitive information and managing risks. It discusses government regulations, ethical considerations, and the need for structured planning and policies to safeguard data. Additionally, it outlines risk management strategies, disaster recovery, and continuous security practices to ensure organizational resilience against threats.