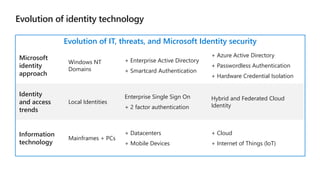
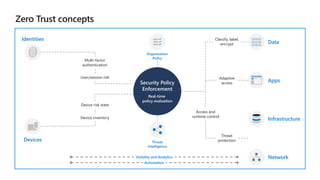
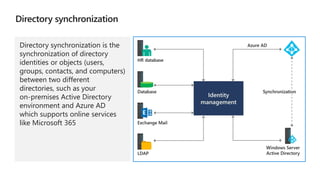
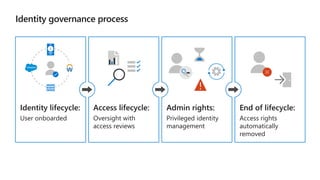
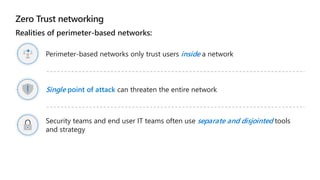
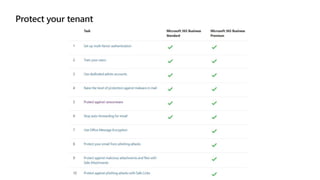
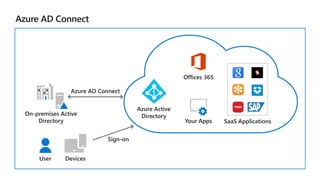
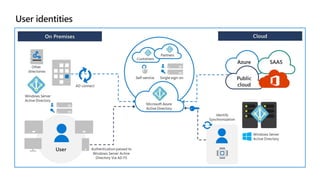
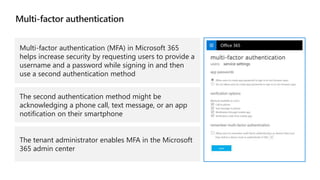
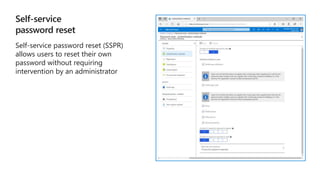
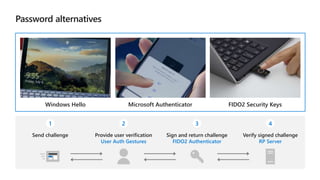
Kushantha Gunawardana presented on Microsoft 365 security. The presentation covered security concepts like the CIA triad and identity challenges. It discussed evolution of identity technology and zero trust concepts. It also outlined how to protect the Microsoft tenant, including managing user identities, multi-factor authentication, self-service password reset, and Windows Hello for Business. The presentation provided an overview of key security features in Microsoft 365.