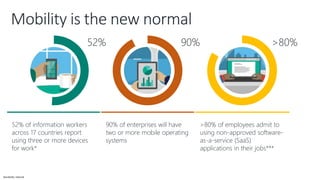
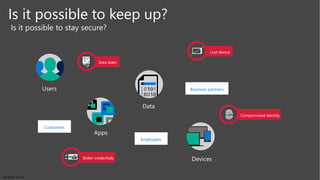
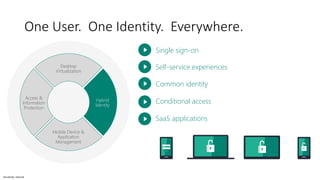
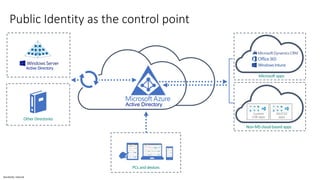
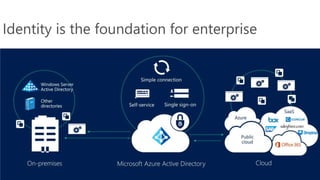
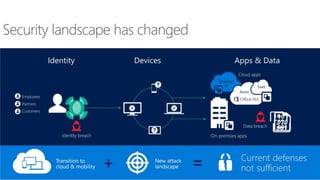
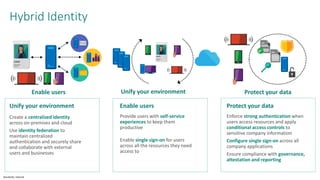
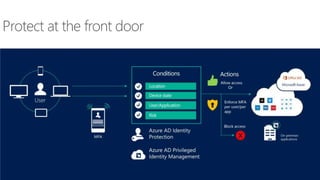
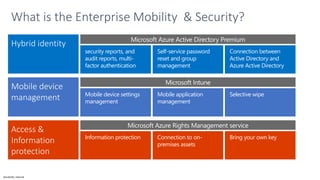
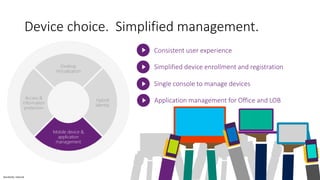
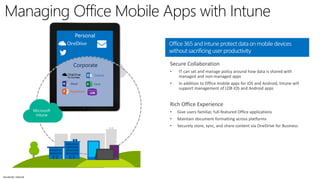
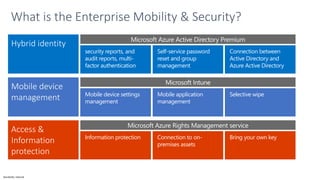
The document discusses the challenges of enabling user mobility and productivity while maintaining security. It notes that most information workers now use multiple devices and over 80% use unsanctioned apps. The document promotes Microsoft's Enterprise Mobility + Security solution for providing identity-driven security, comprehensive management of mobile devices and apps, and protection of data across platforms. It describes capabilities for unified identity, mobile device management, application management, and information rights management.