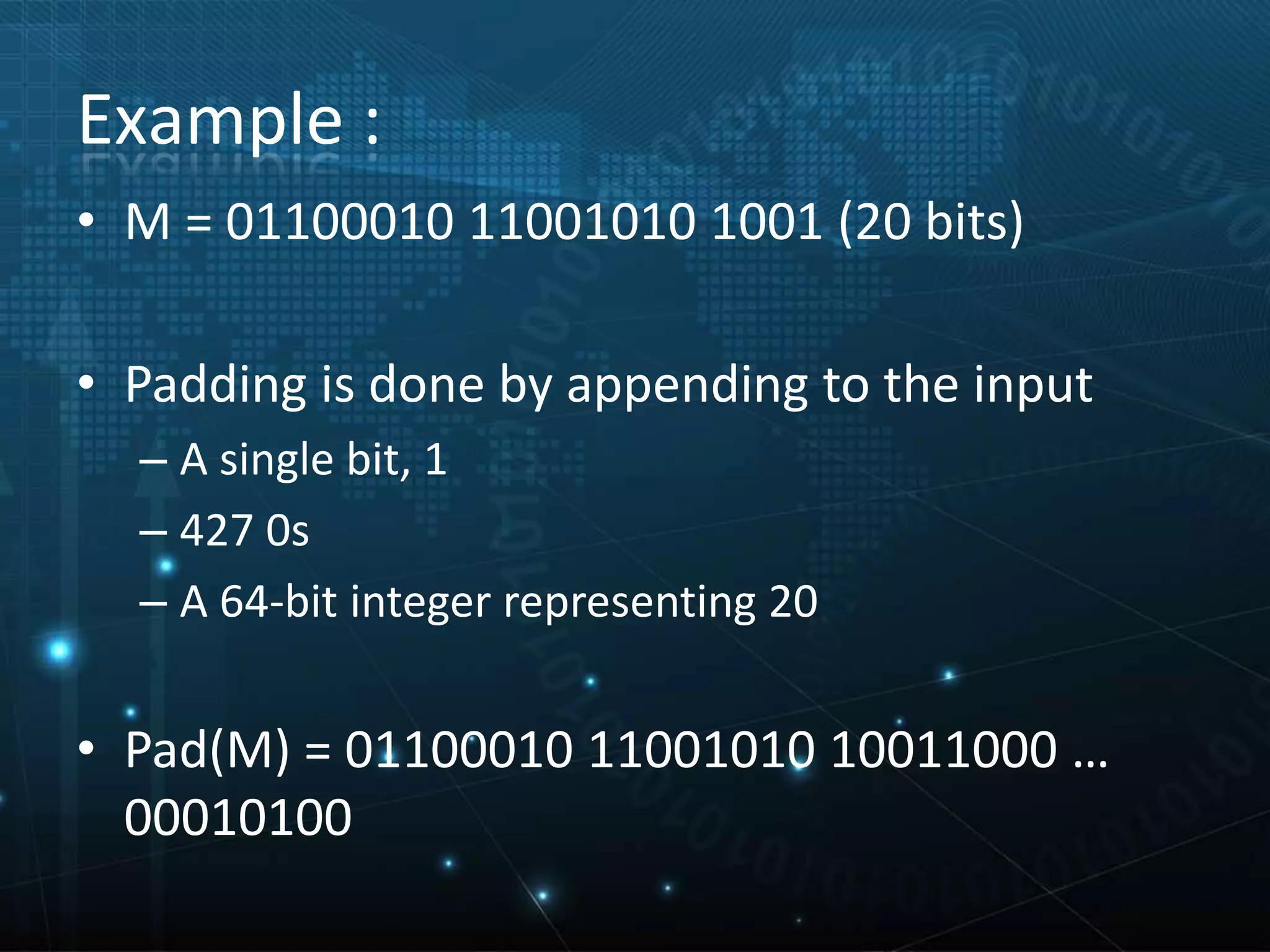
The document explains secure hashing techniques, describing how hash functions transform variable-length data into fixed-length hash values that are difficult to reverse-engineer. It discusses one-way hashing, message digest functions, and specific secure hashing algorithms like SHA-0, SHA-1, and SHA-2, highlighting their characteristics and vulnerabilities. Applications of secure hashing are mentioned in contexts where sensitive data is handled, such as online banking and e-learning.