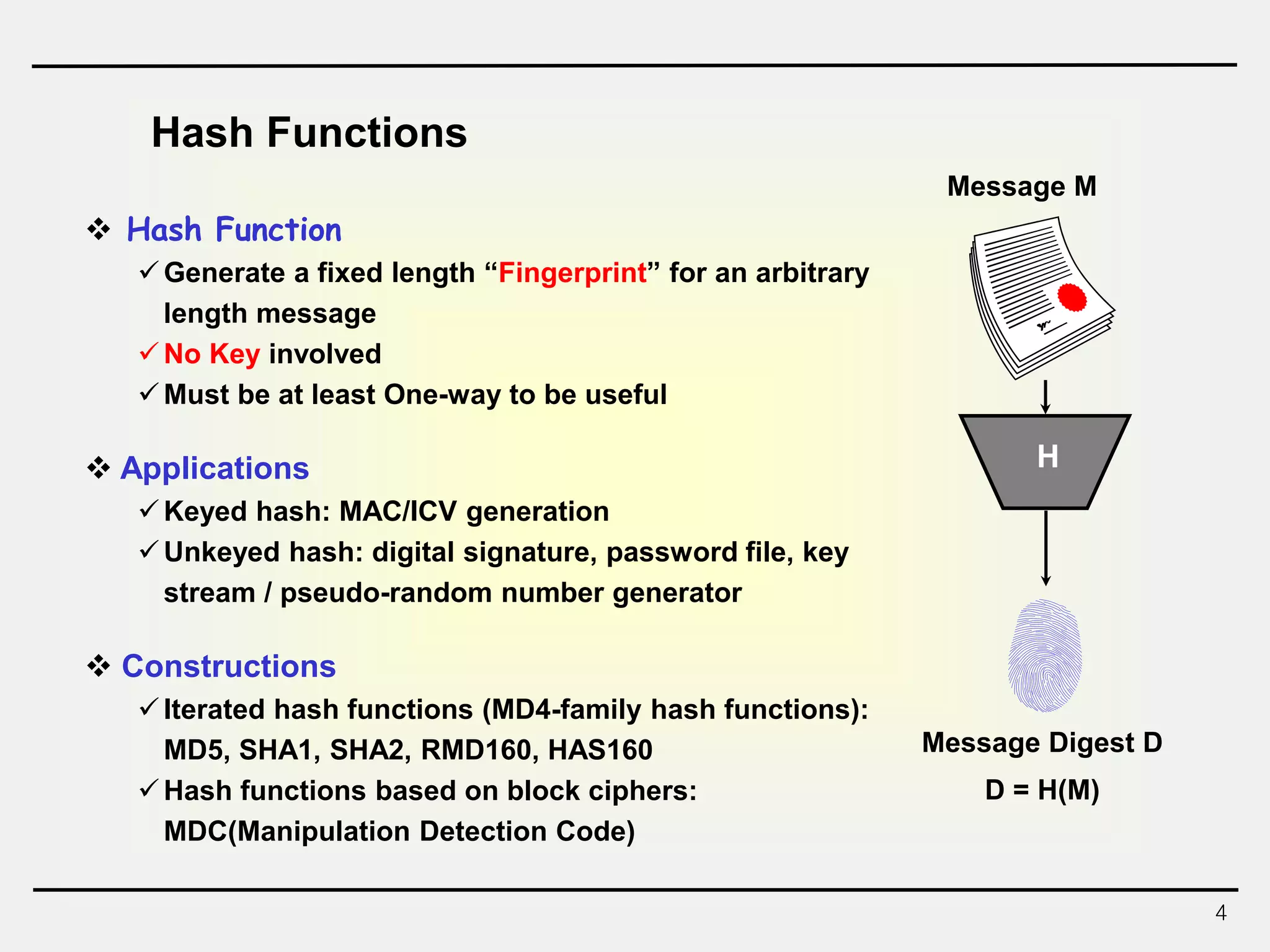
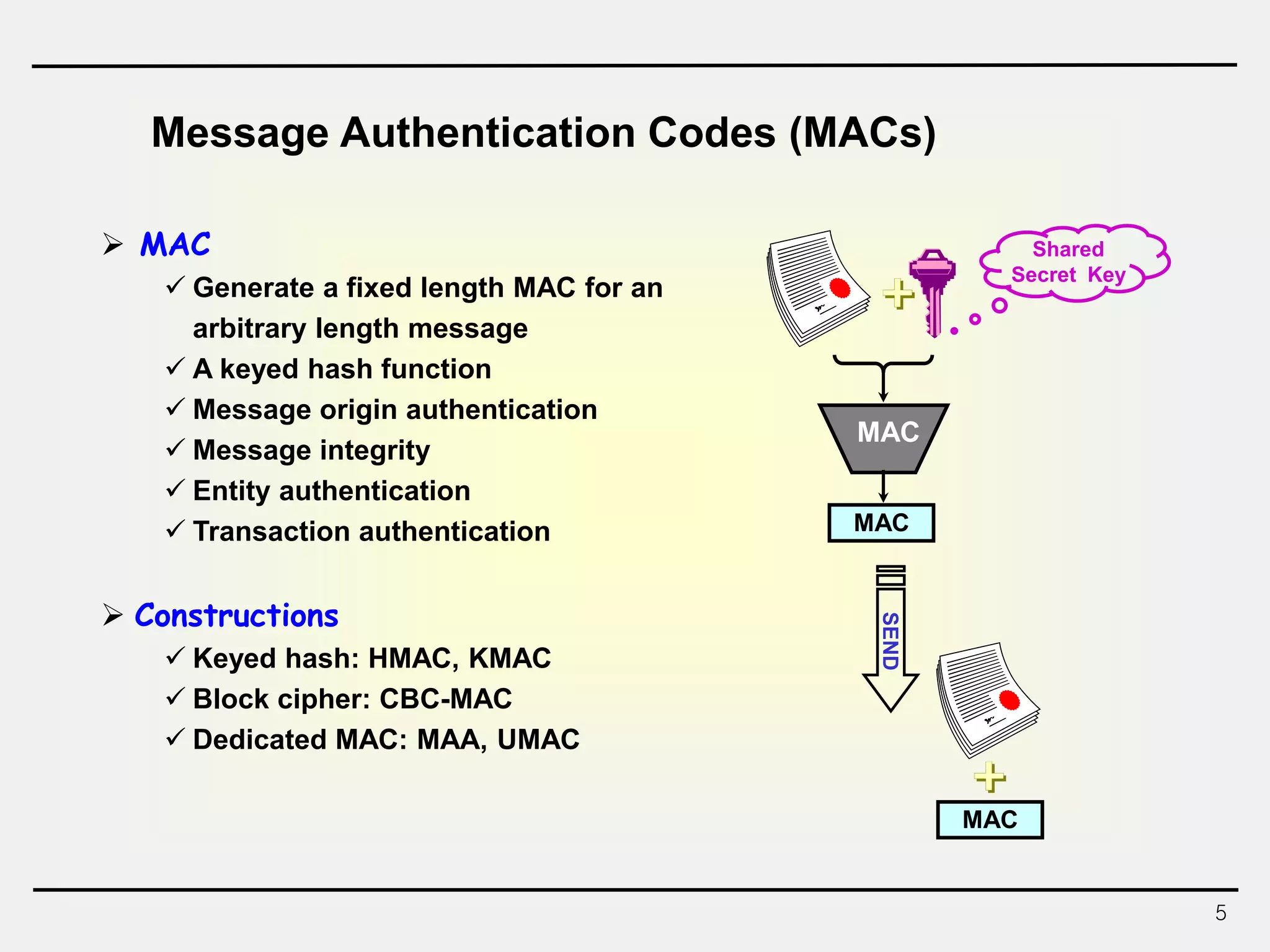
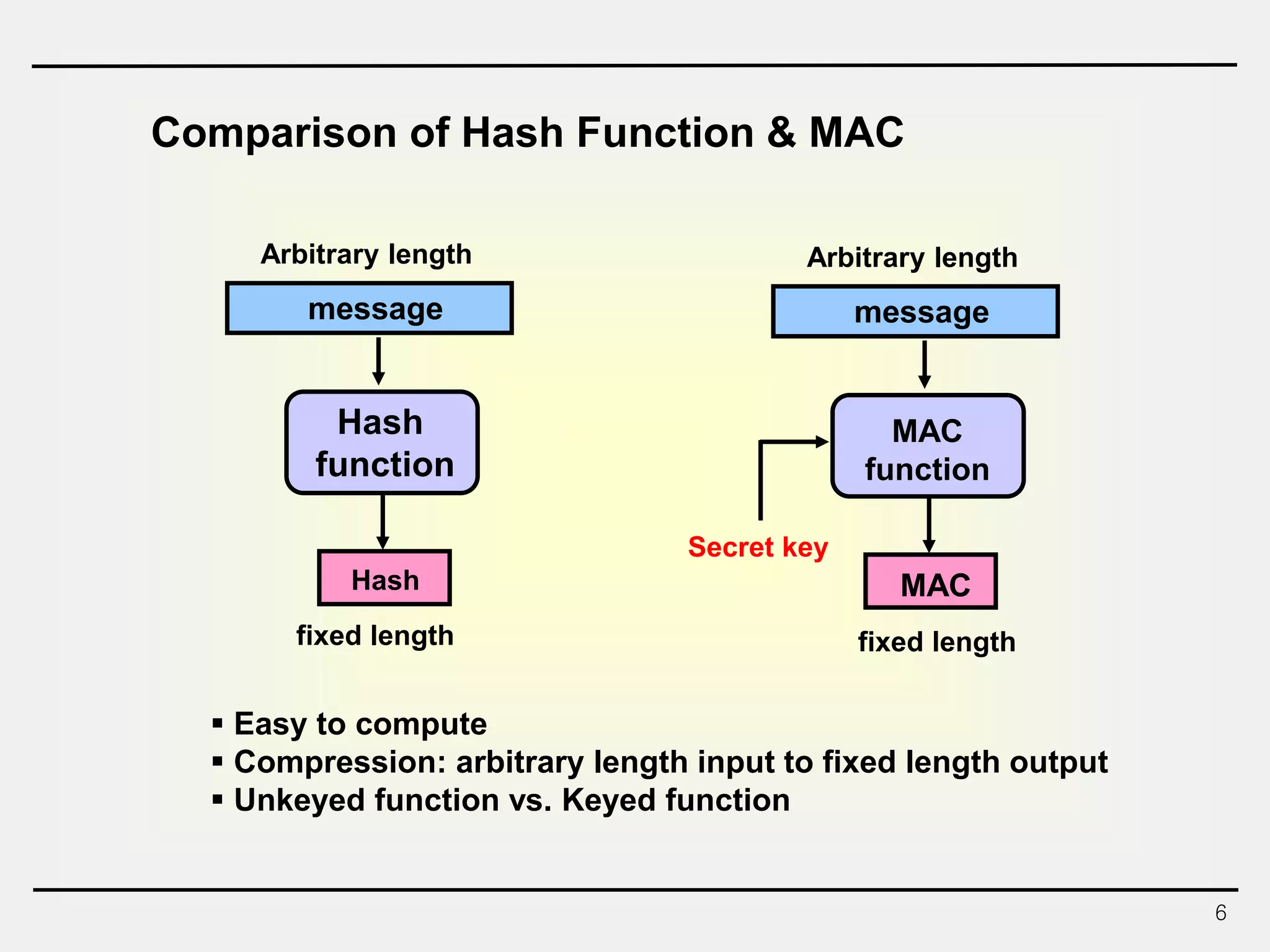
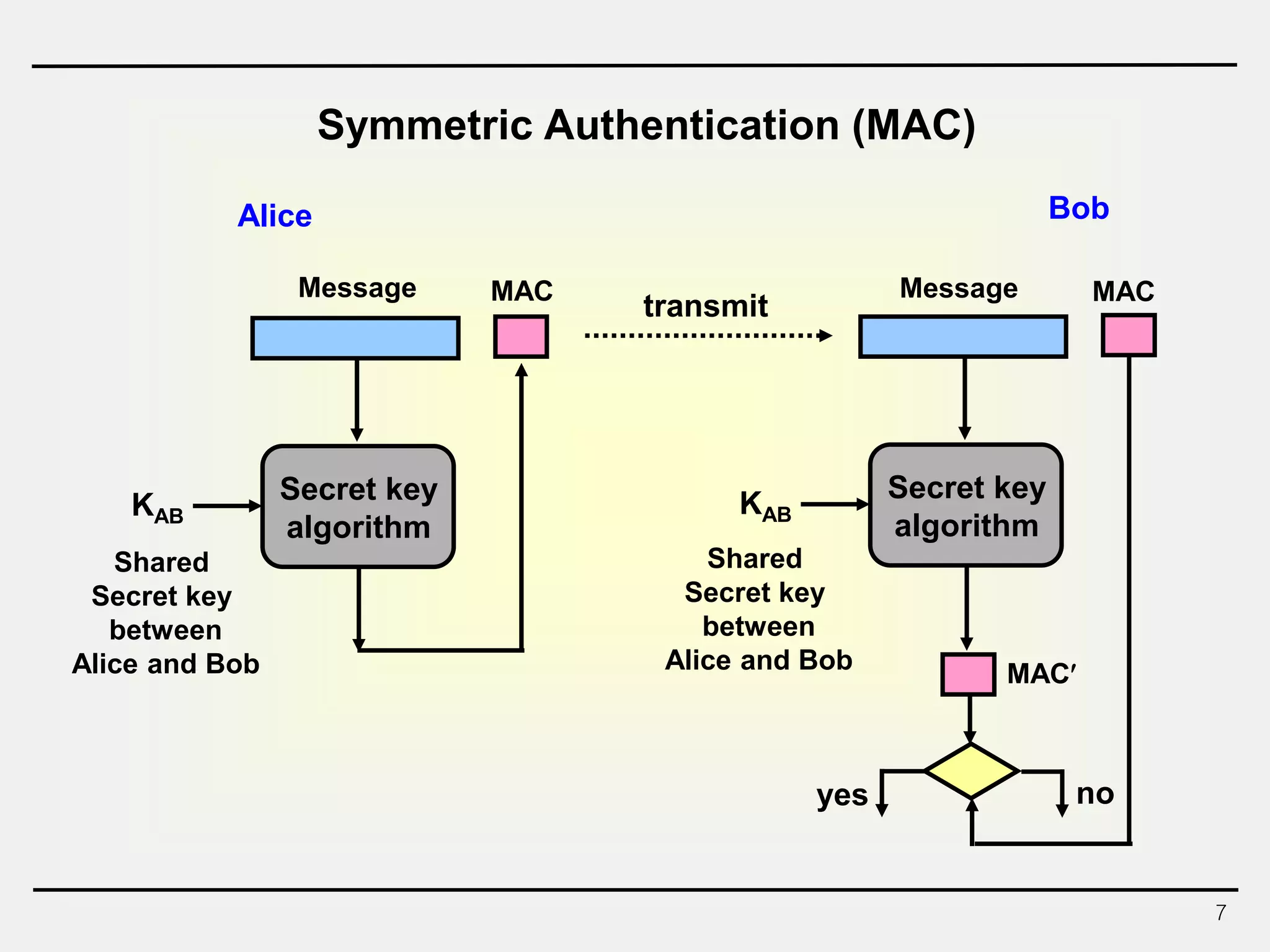
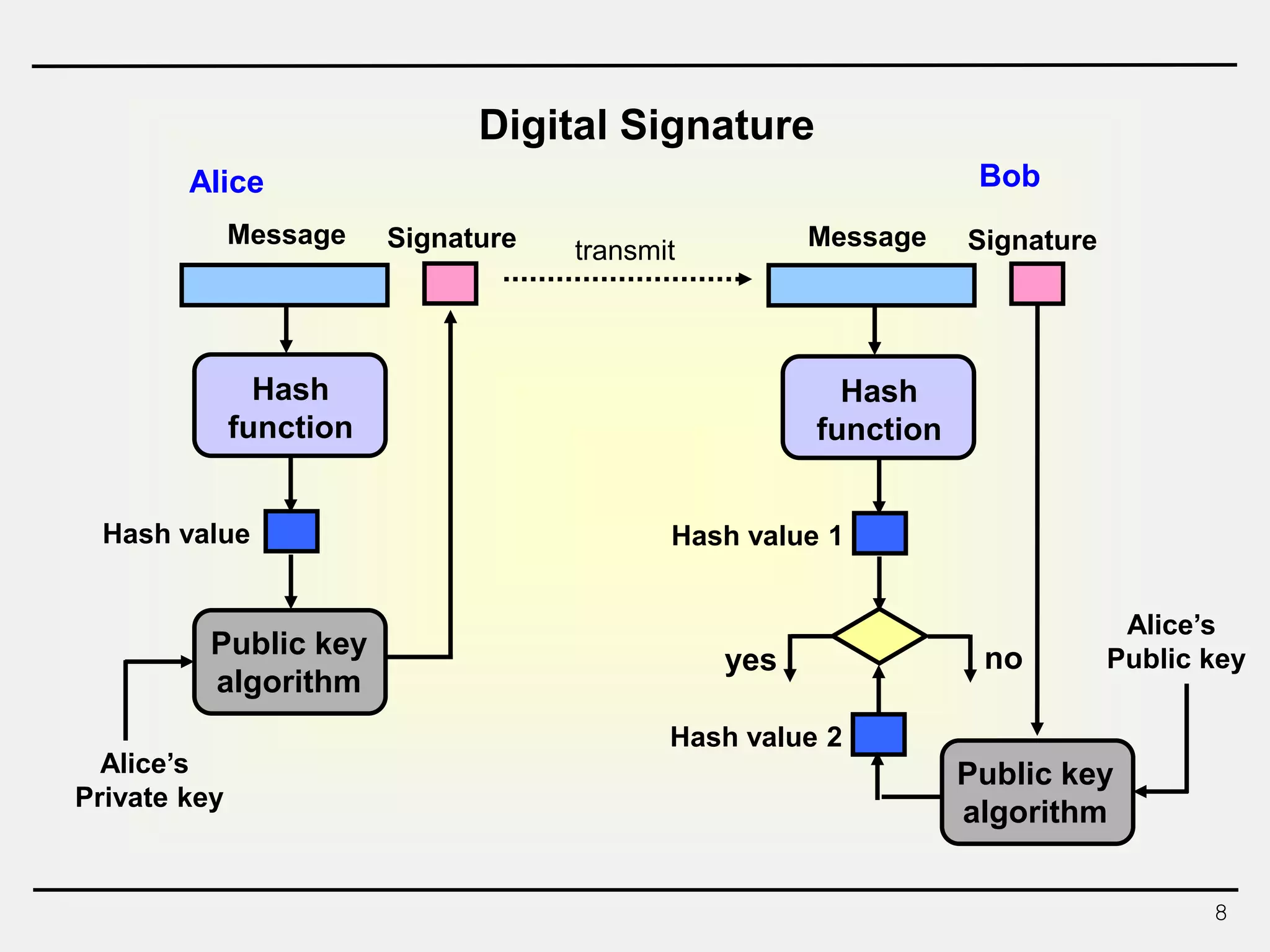
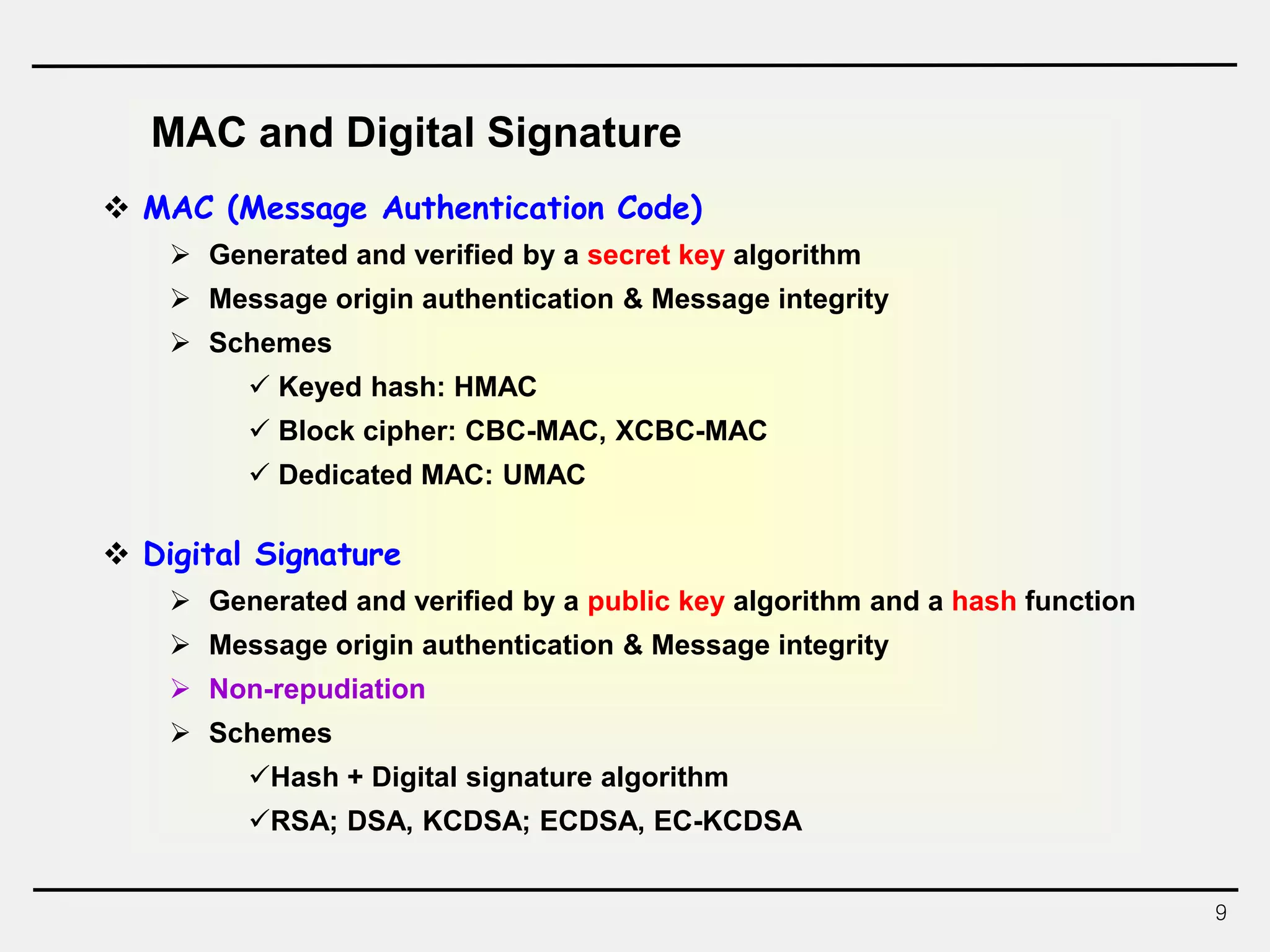
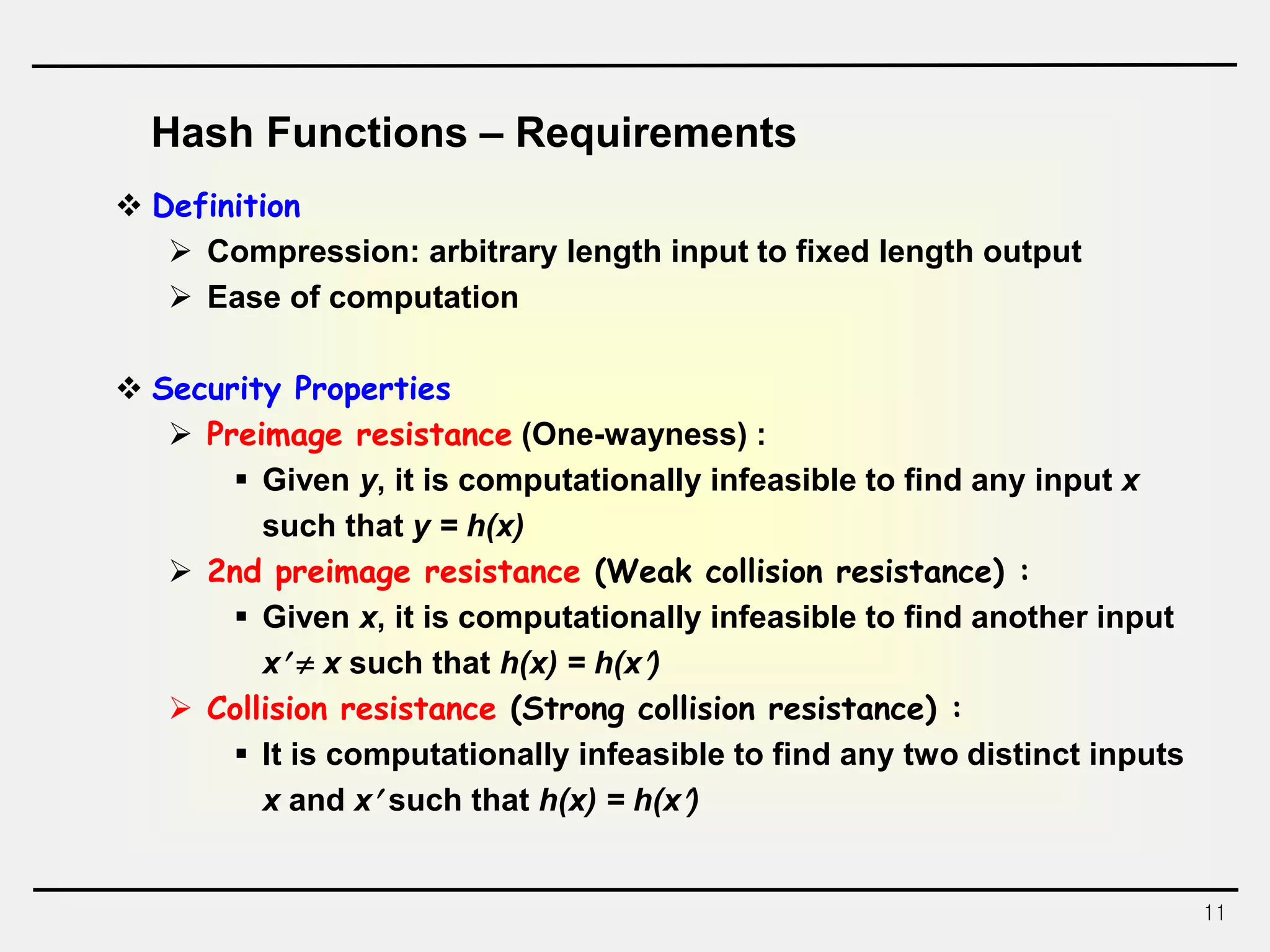
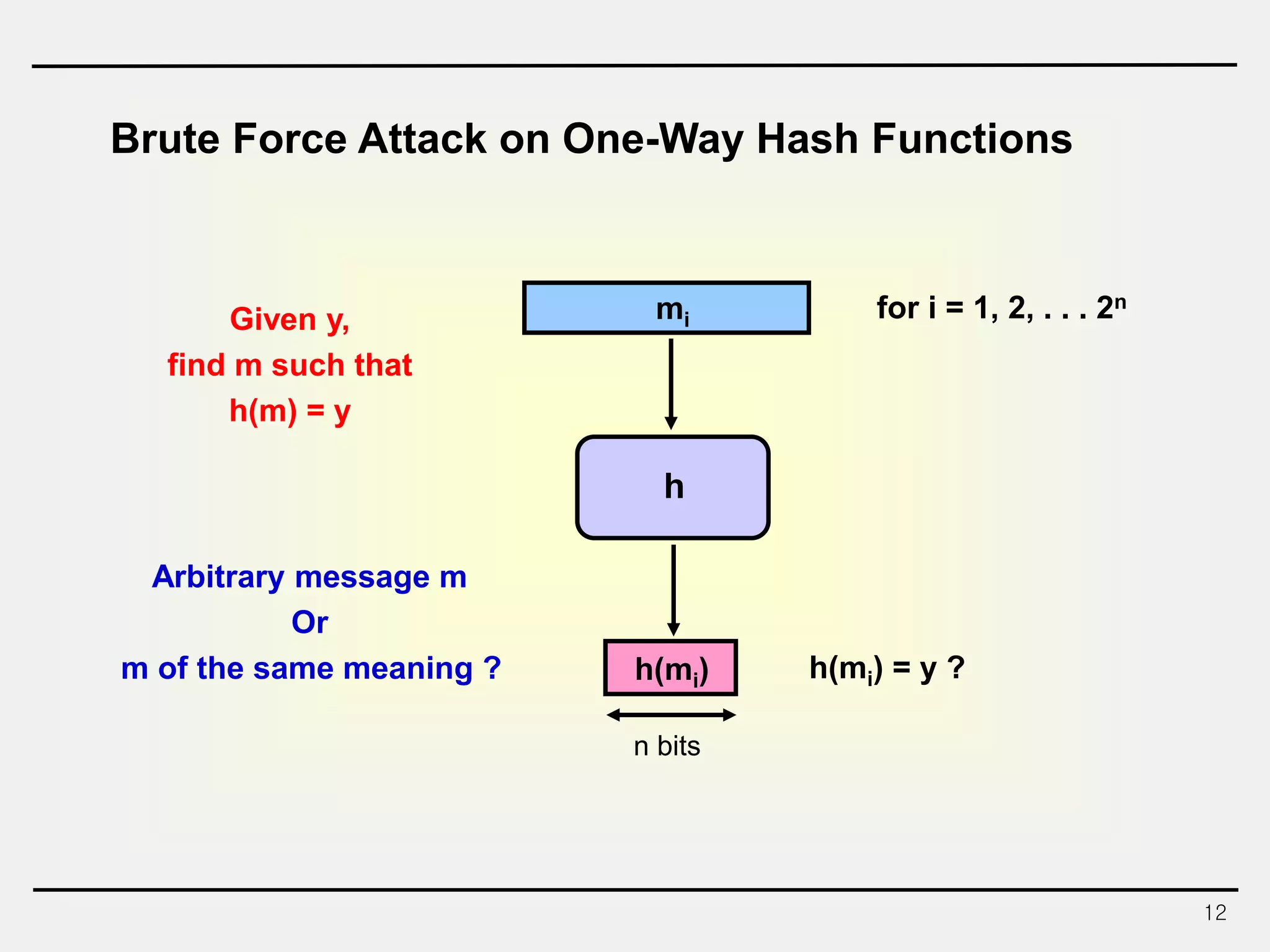
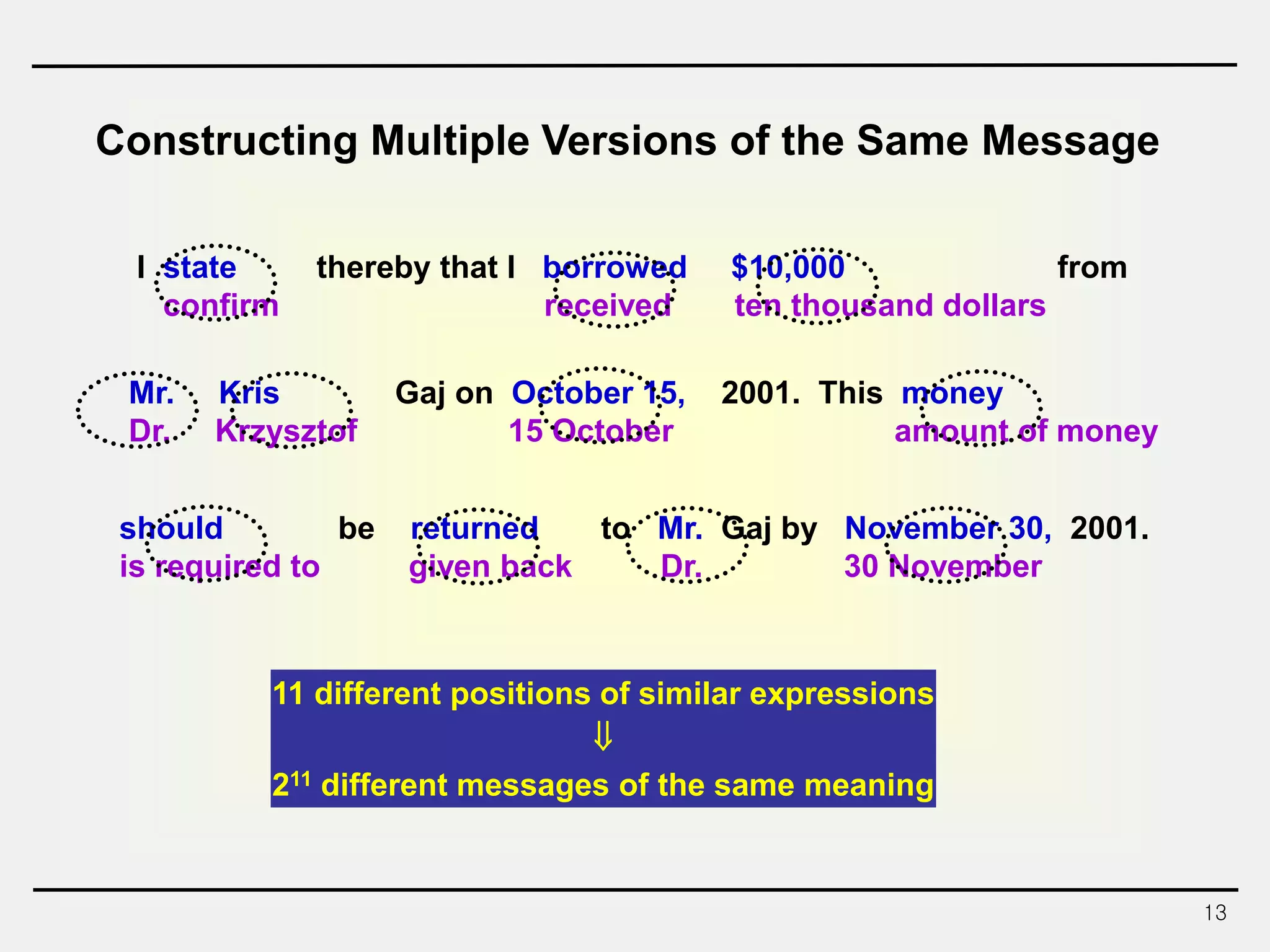
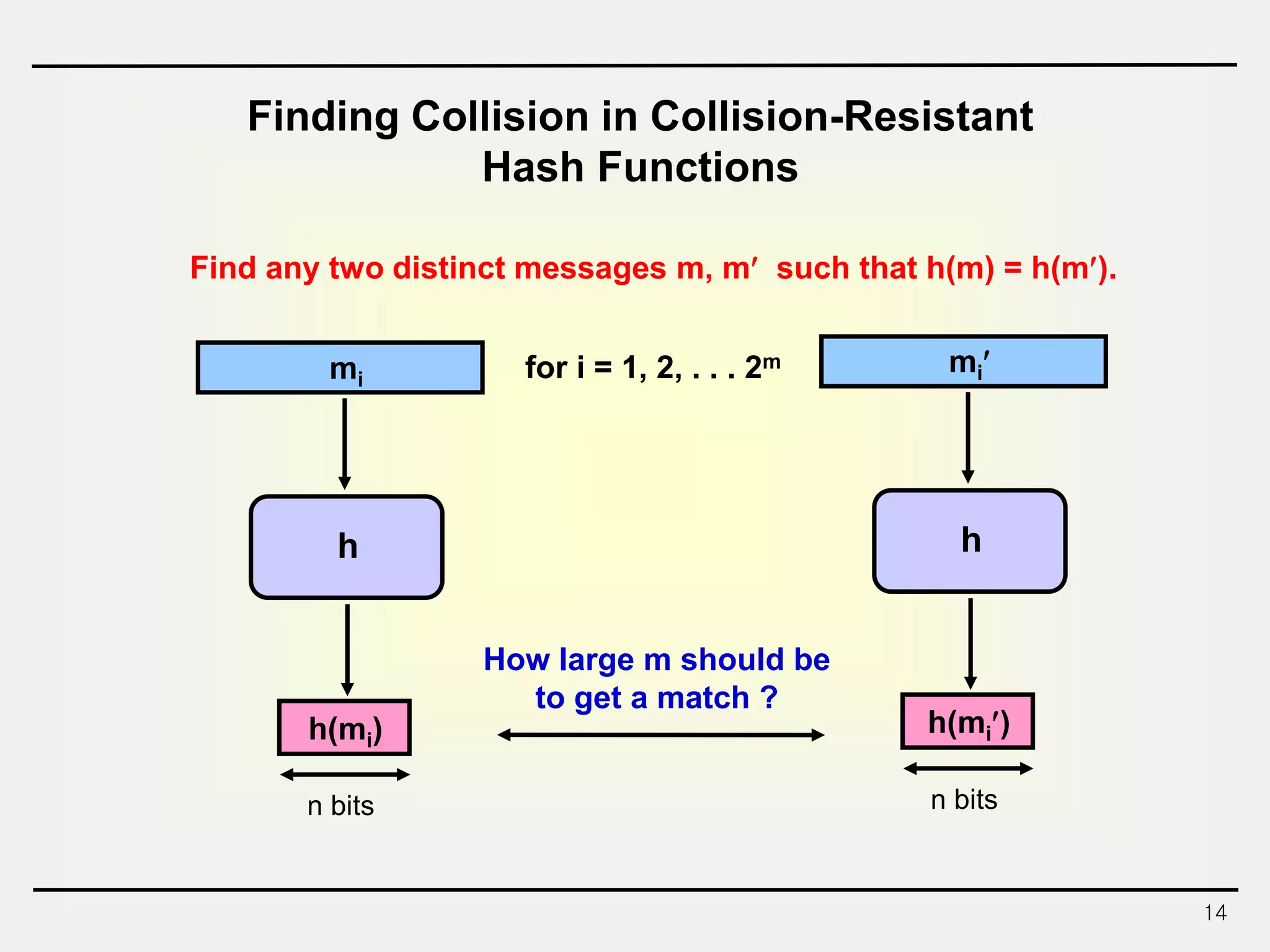
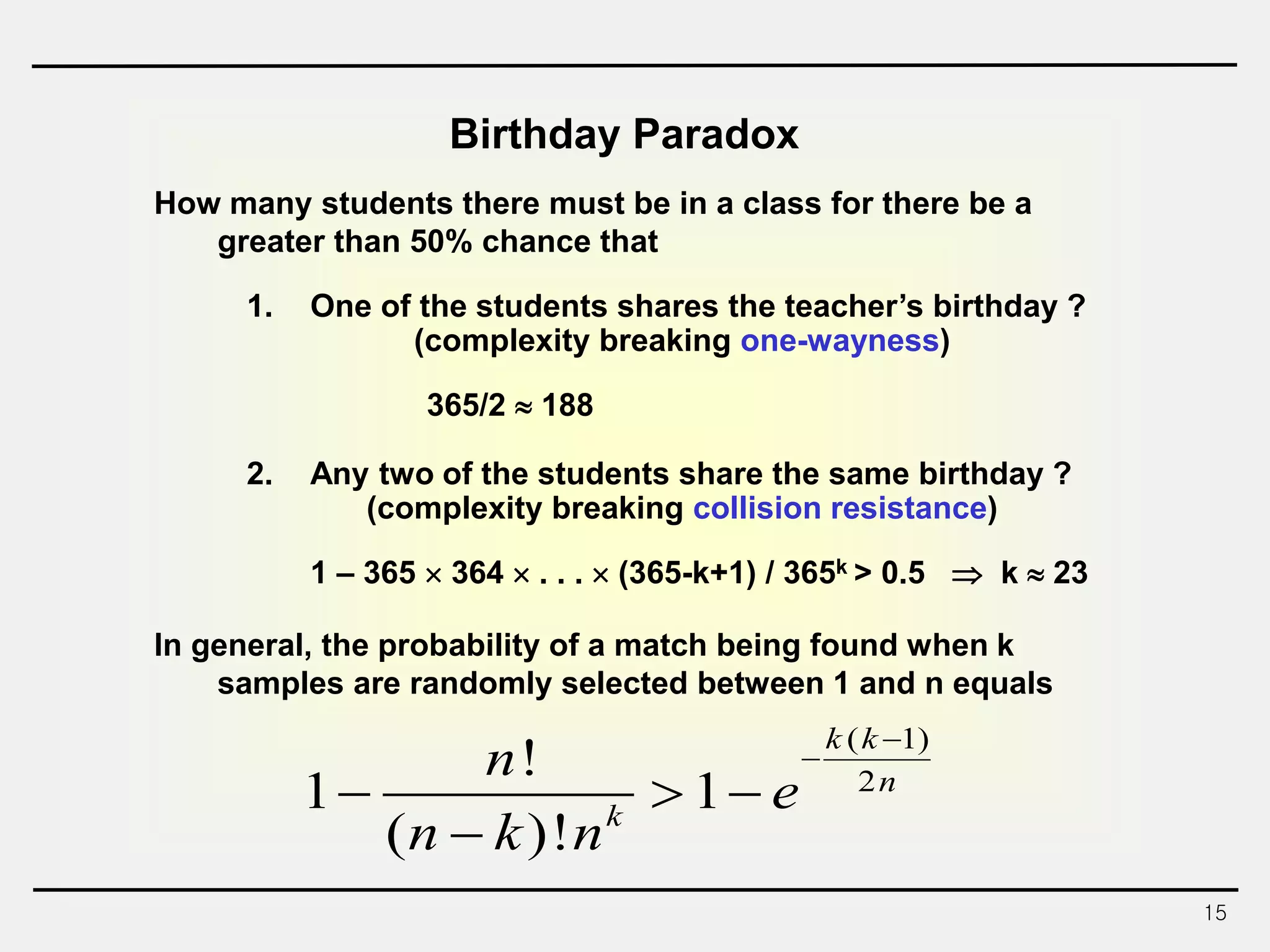
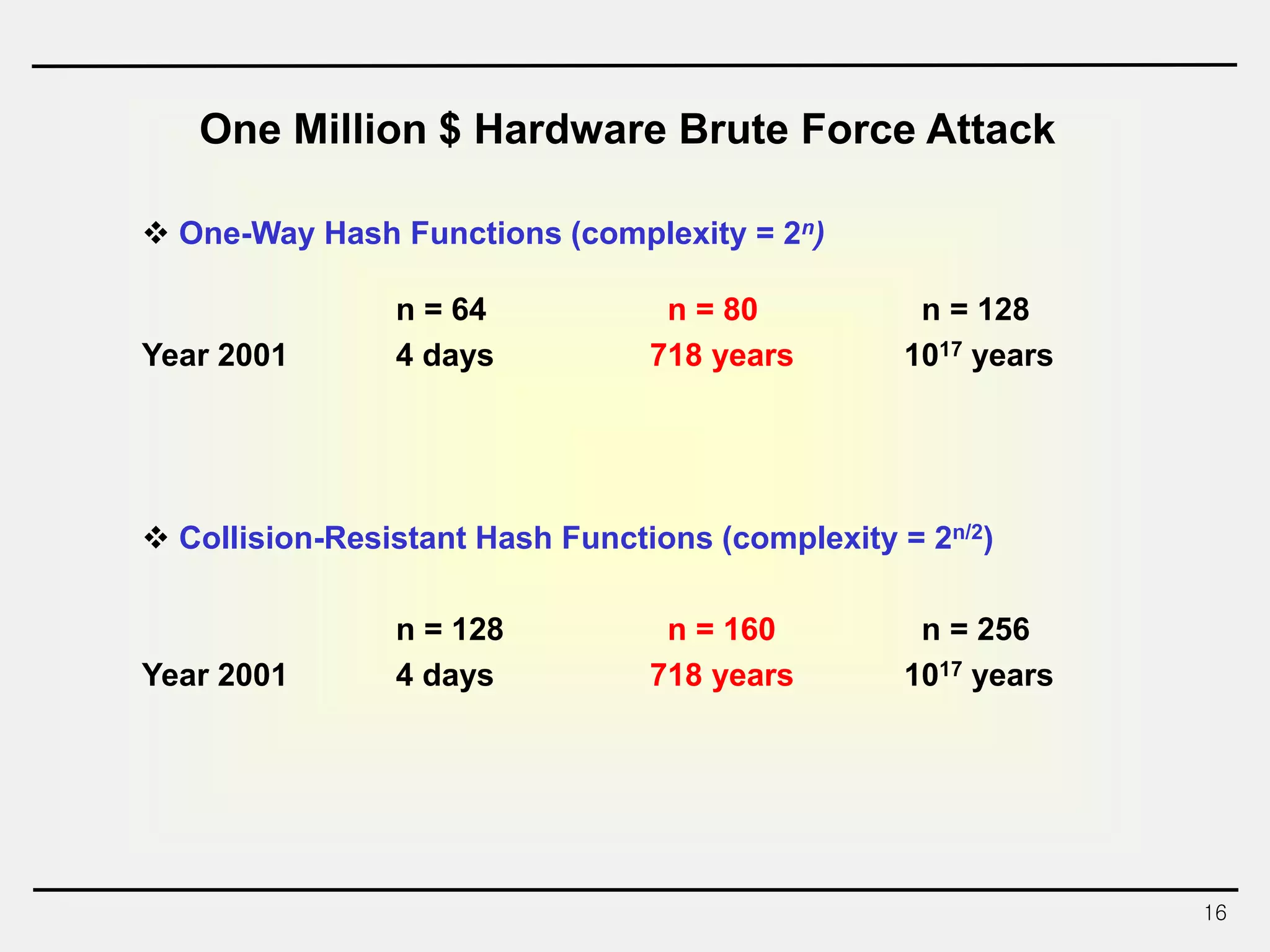
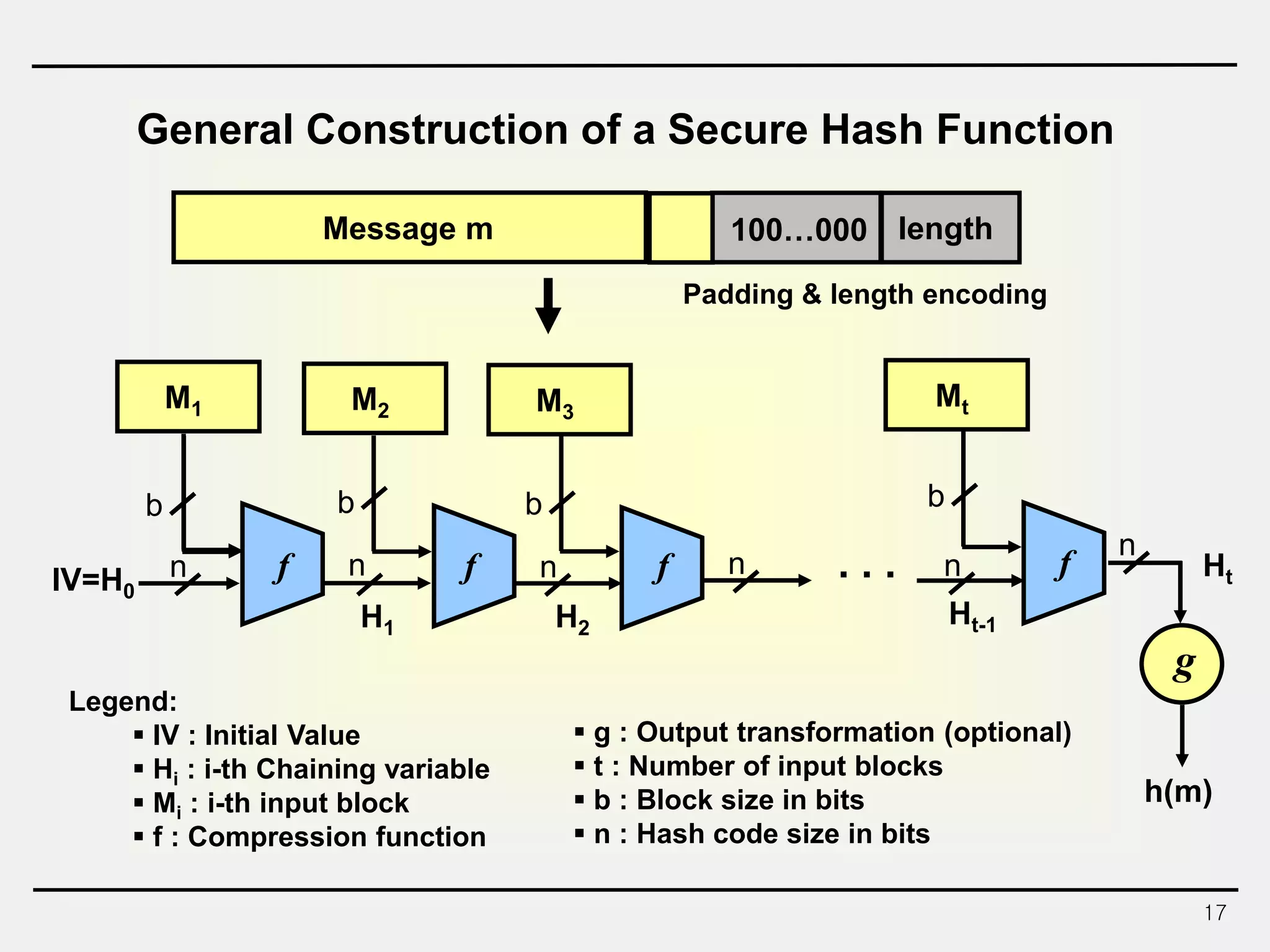
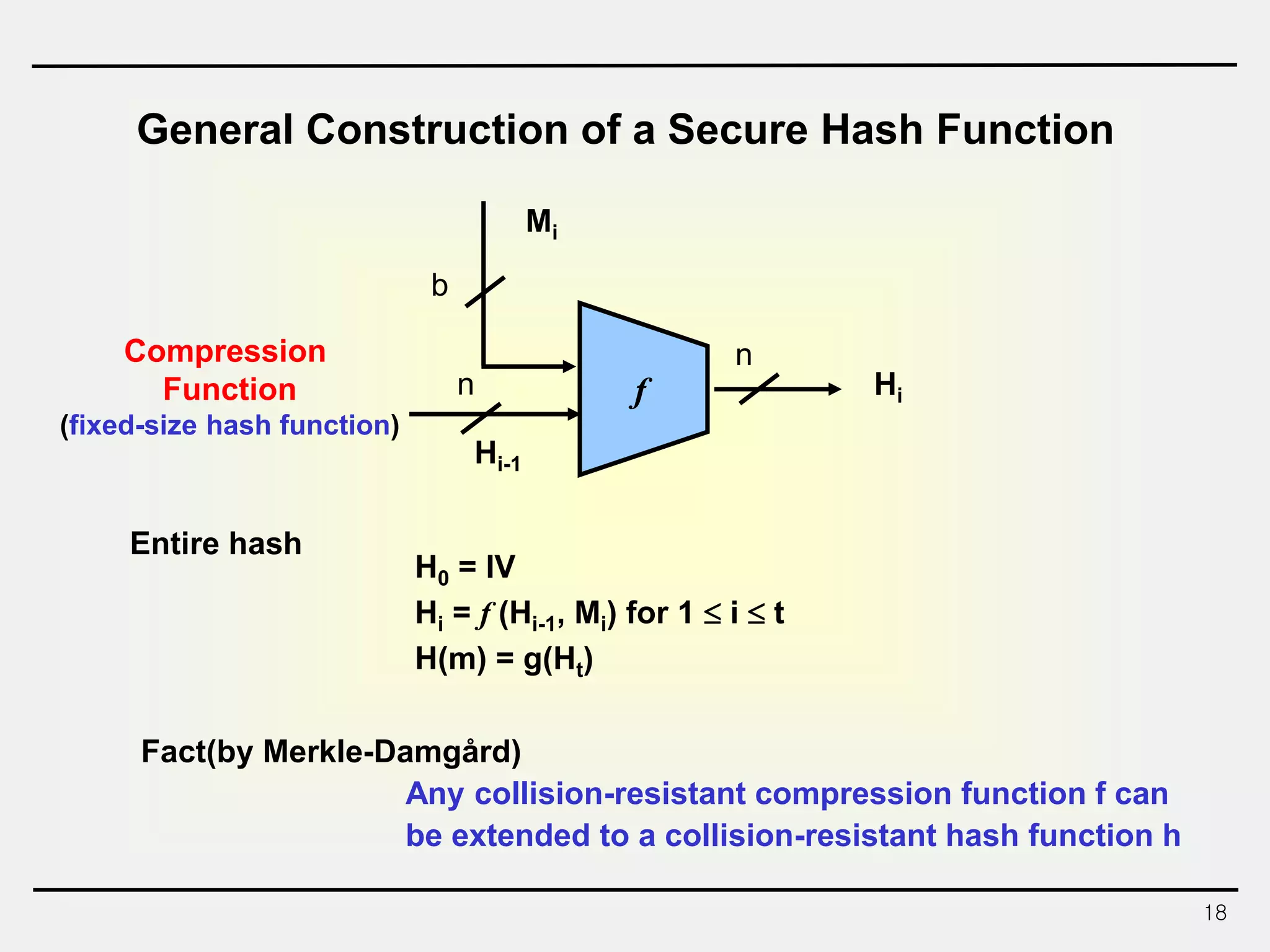
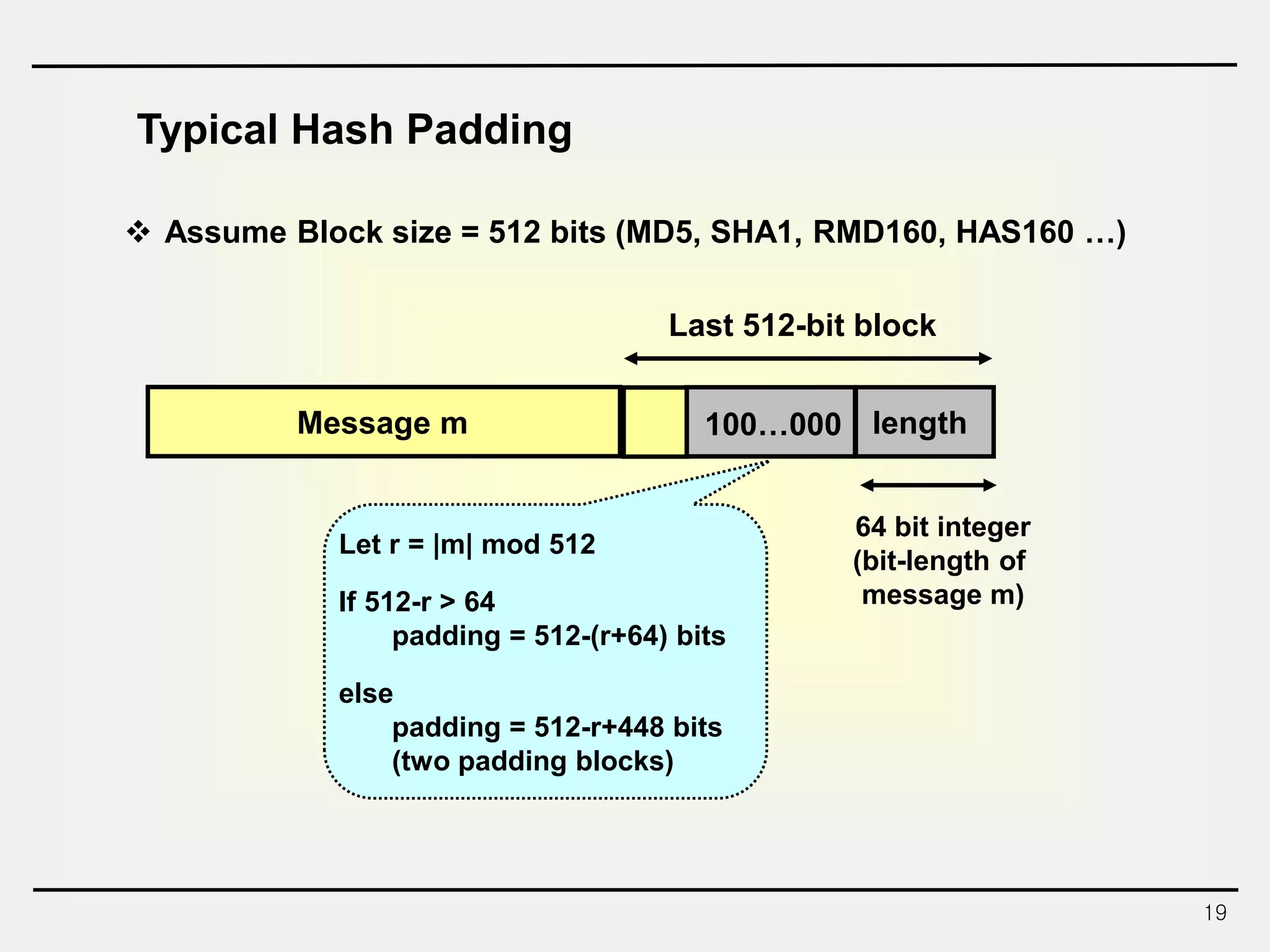
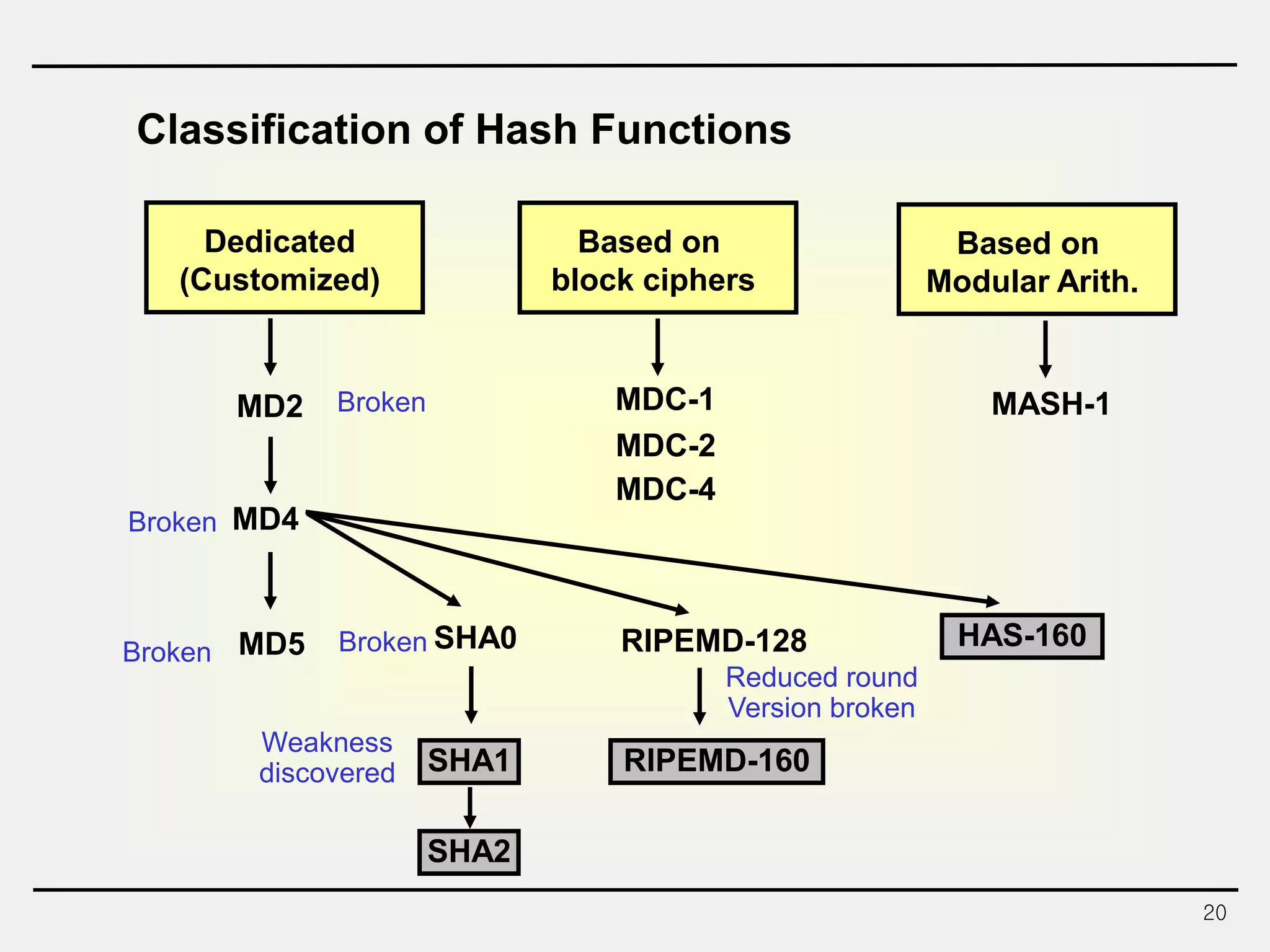
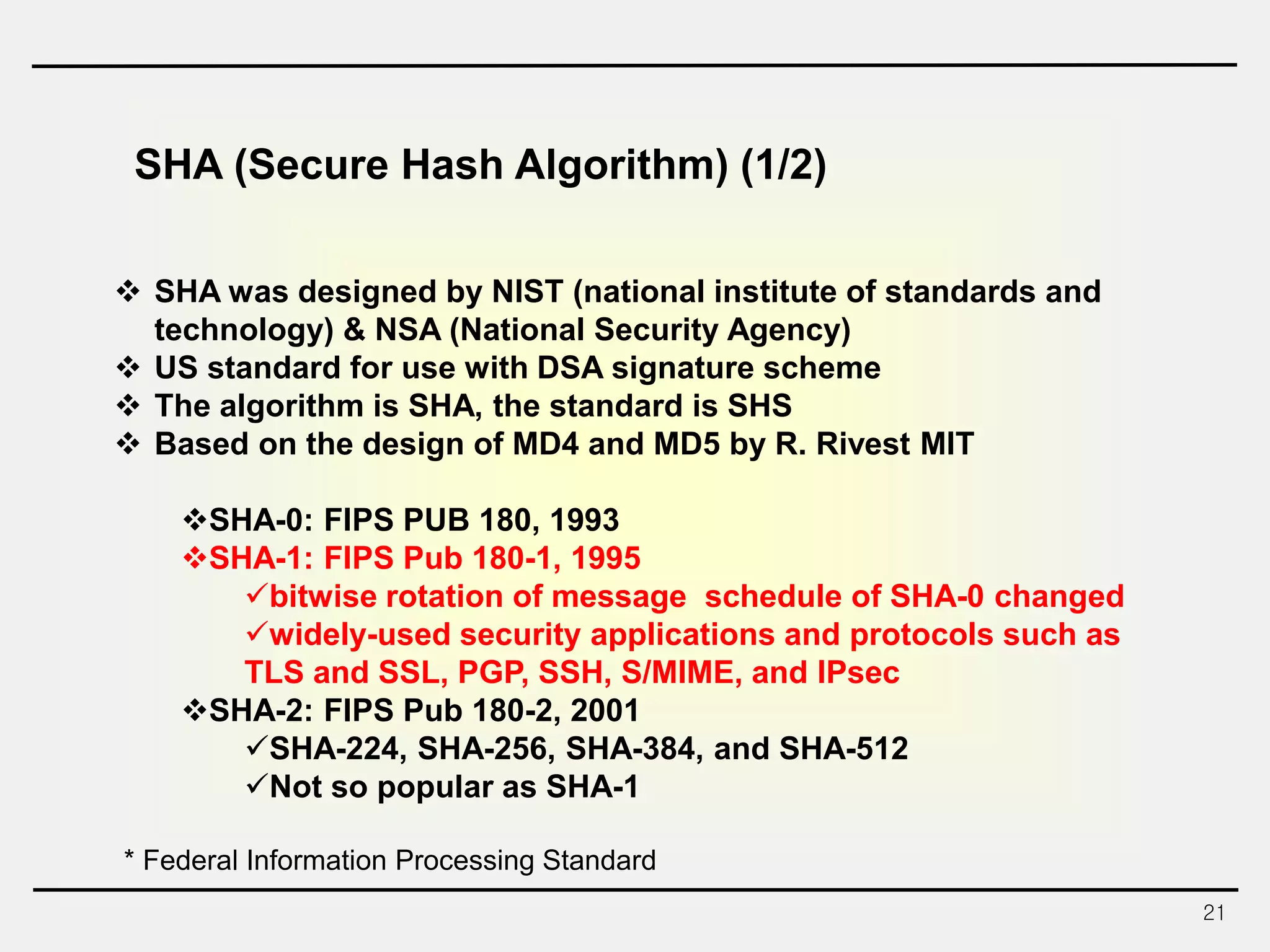
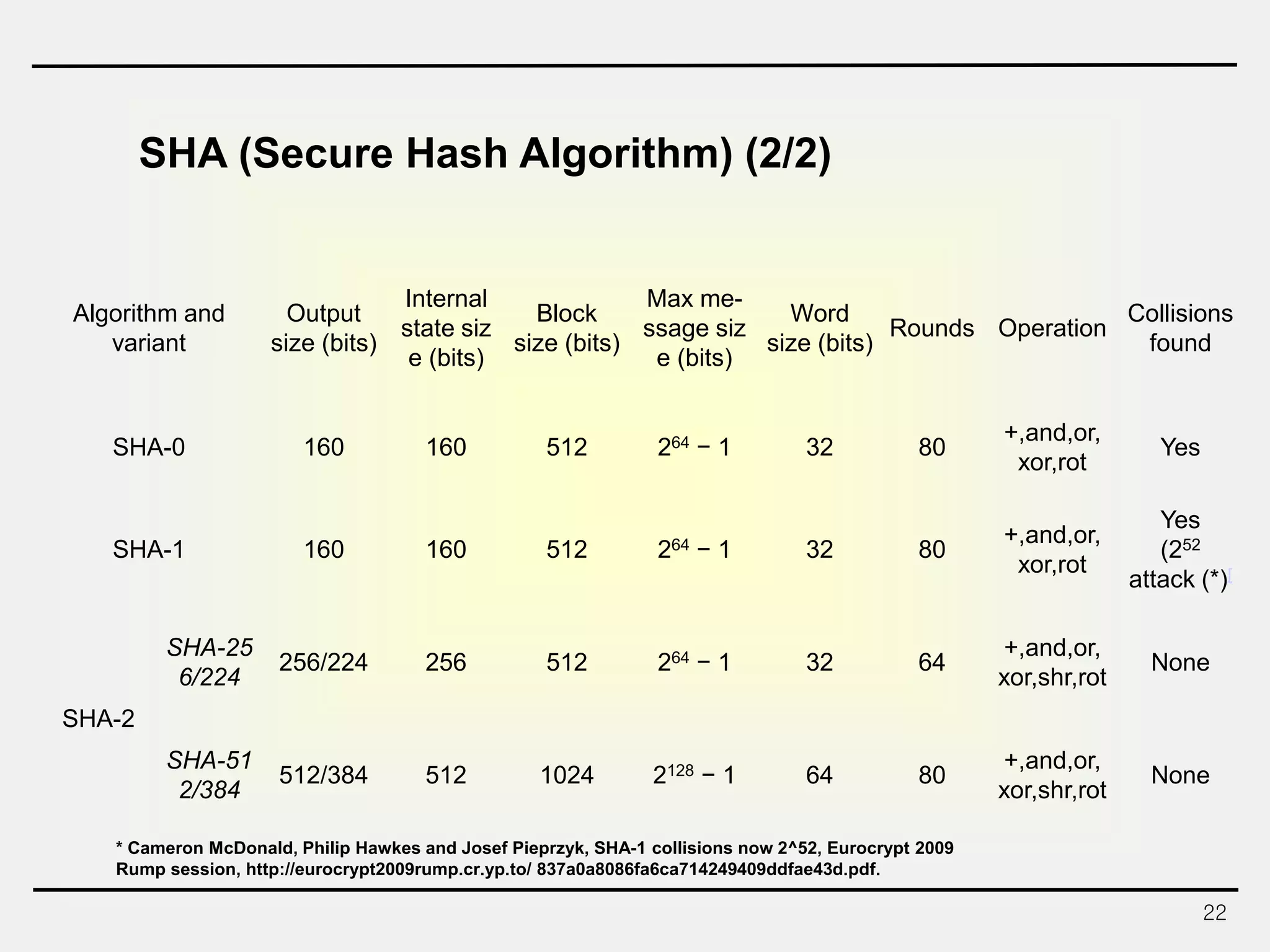
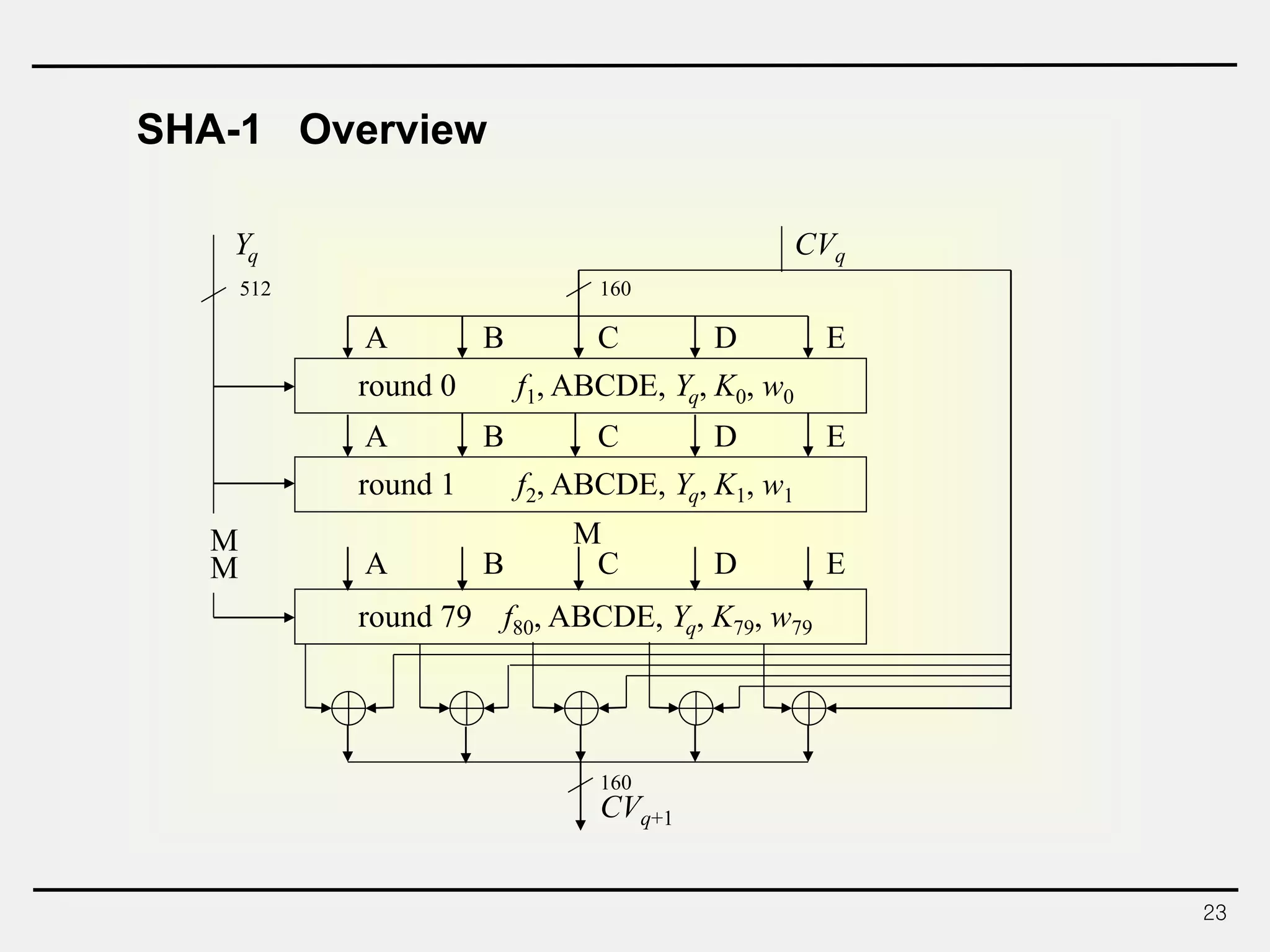
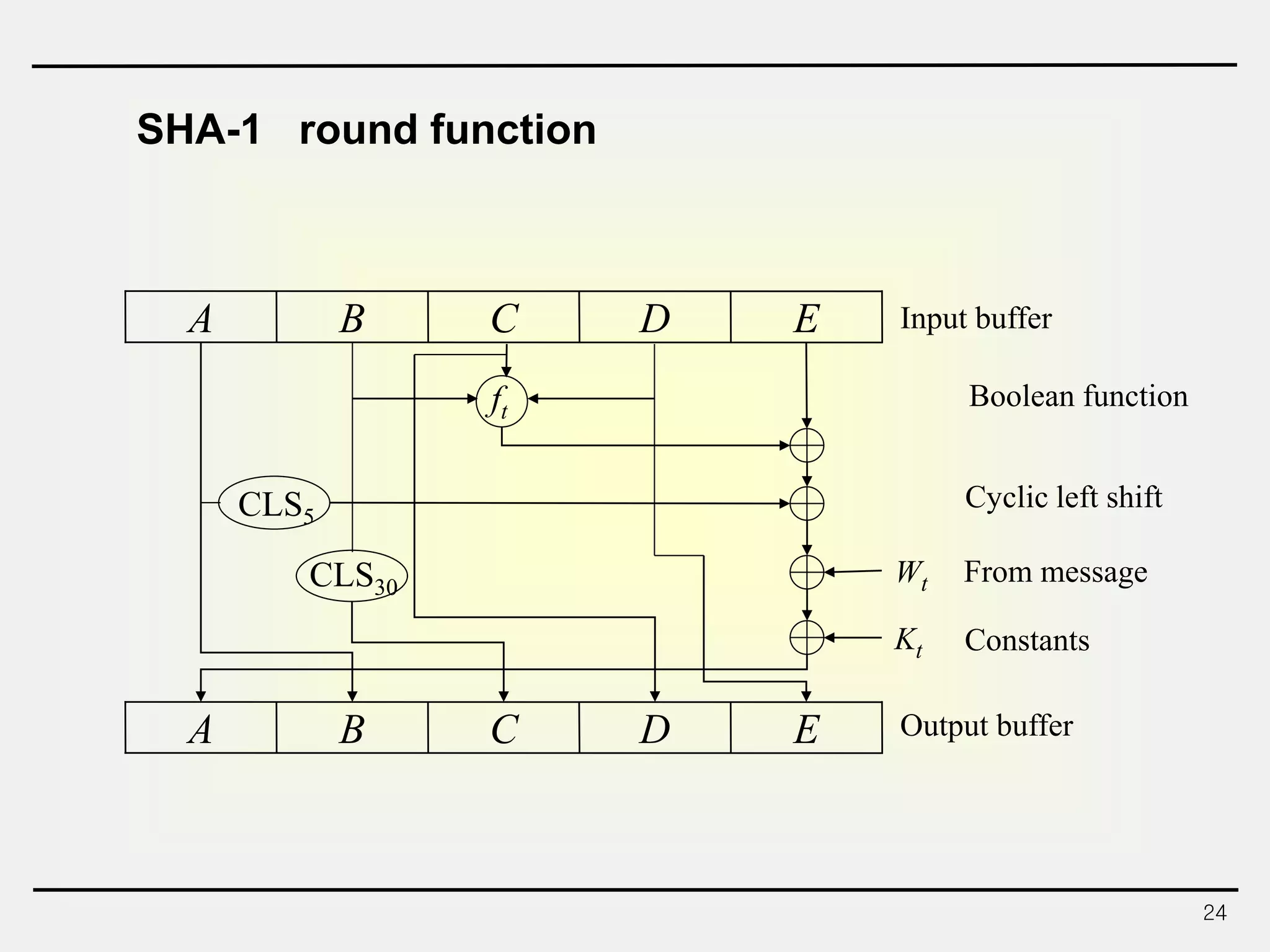
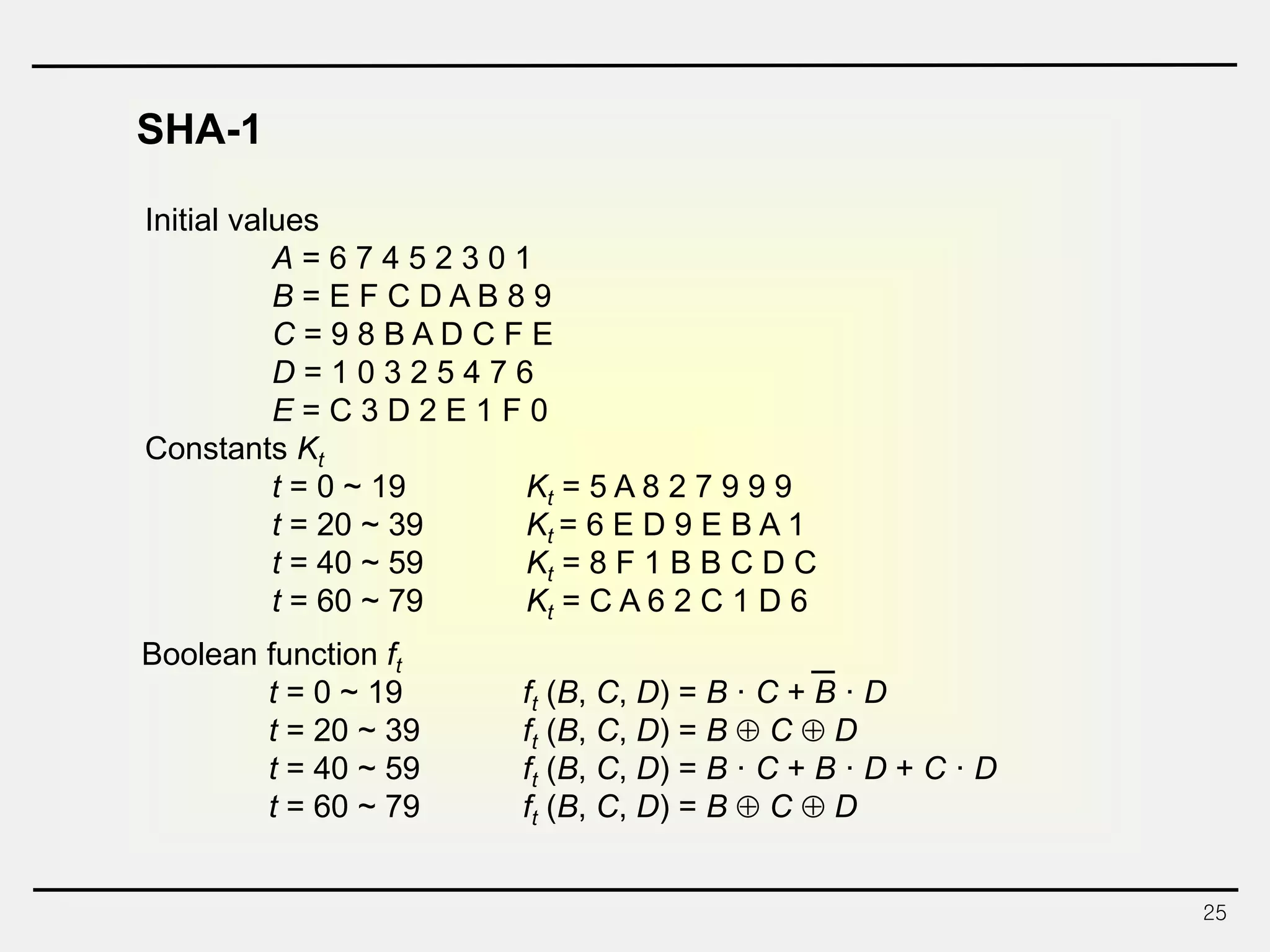
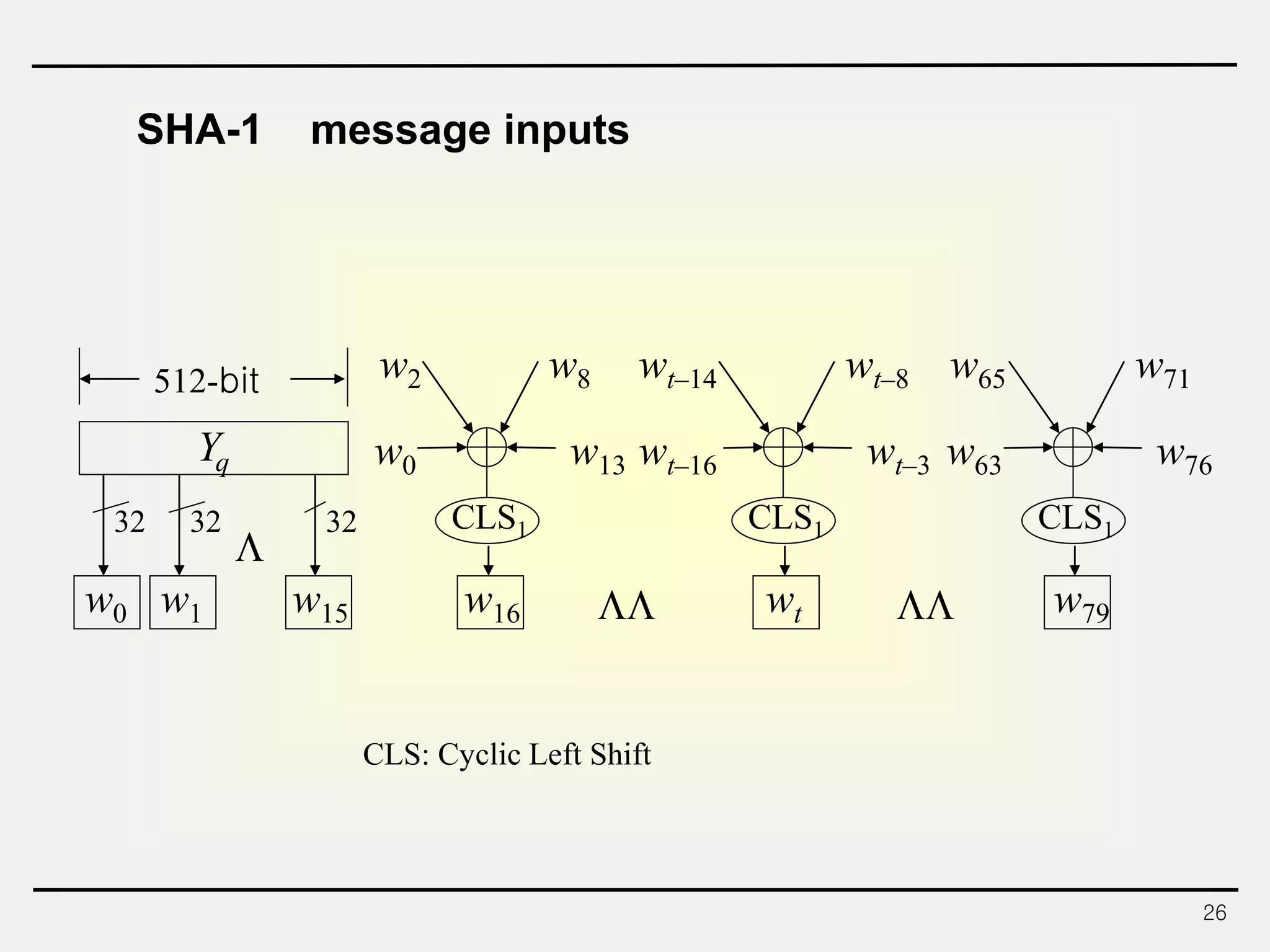
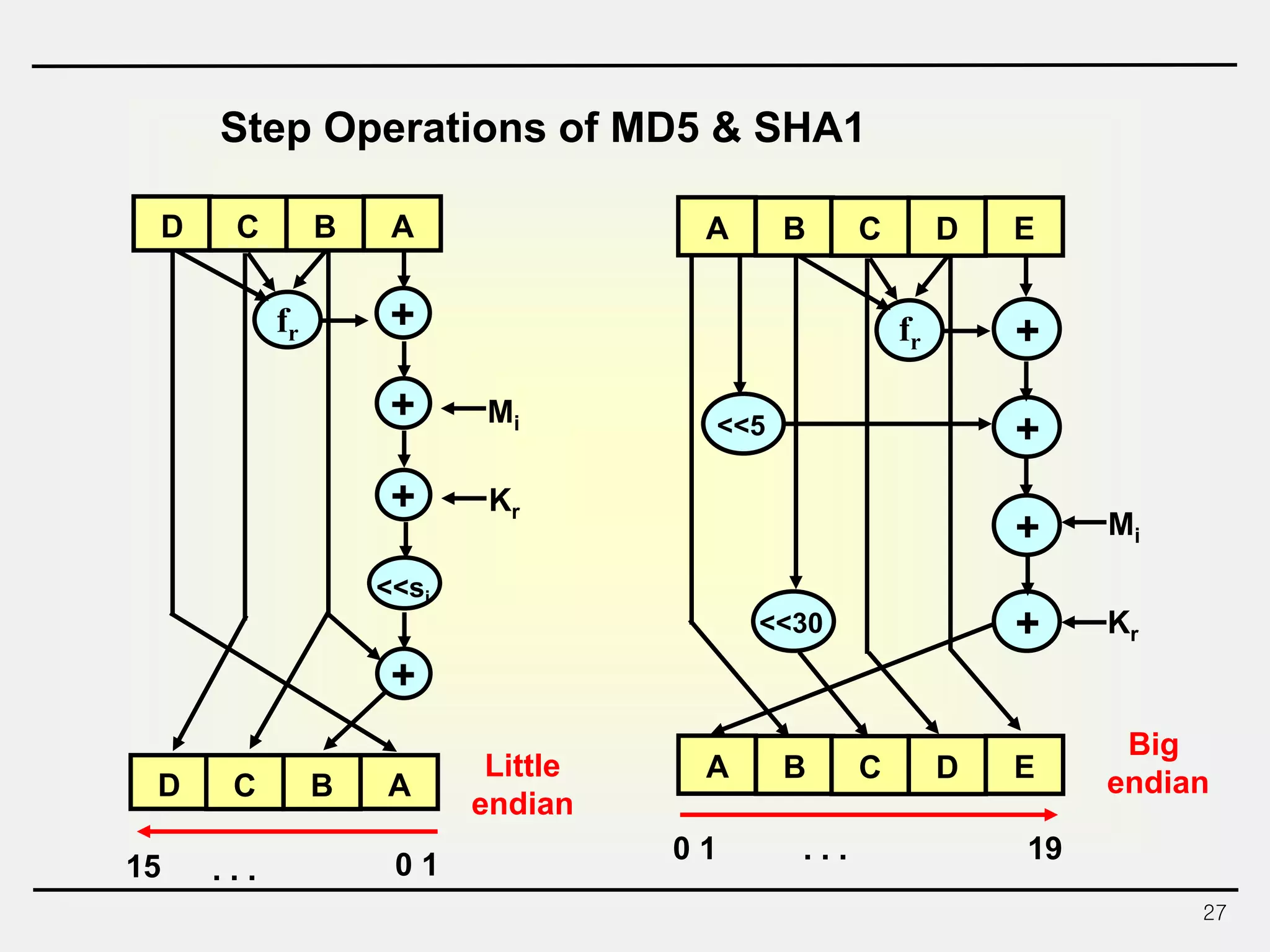
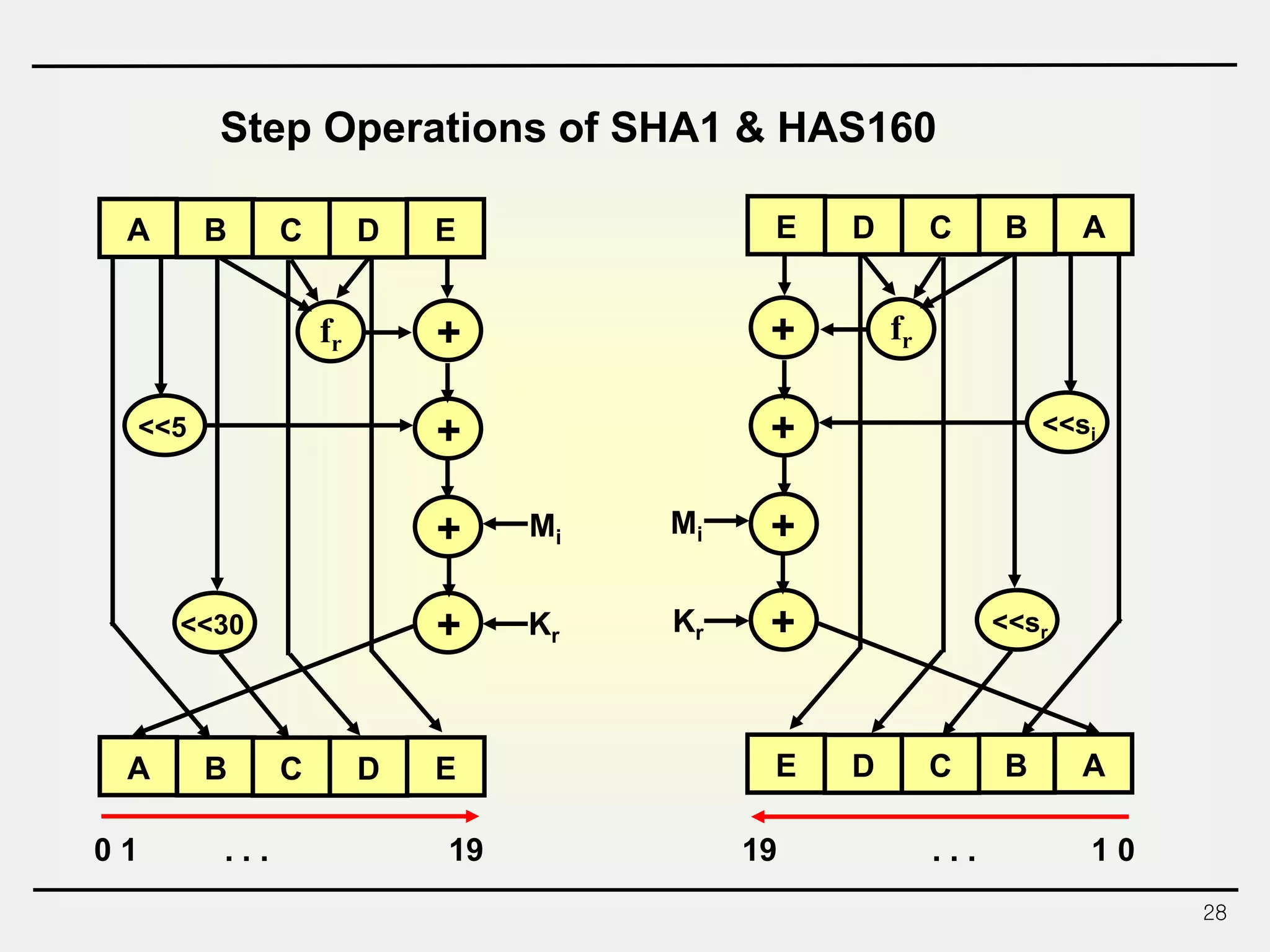
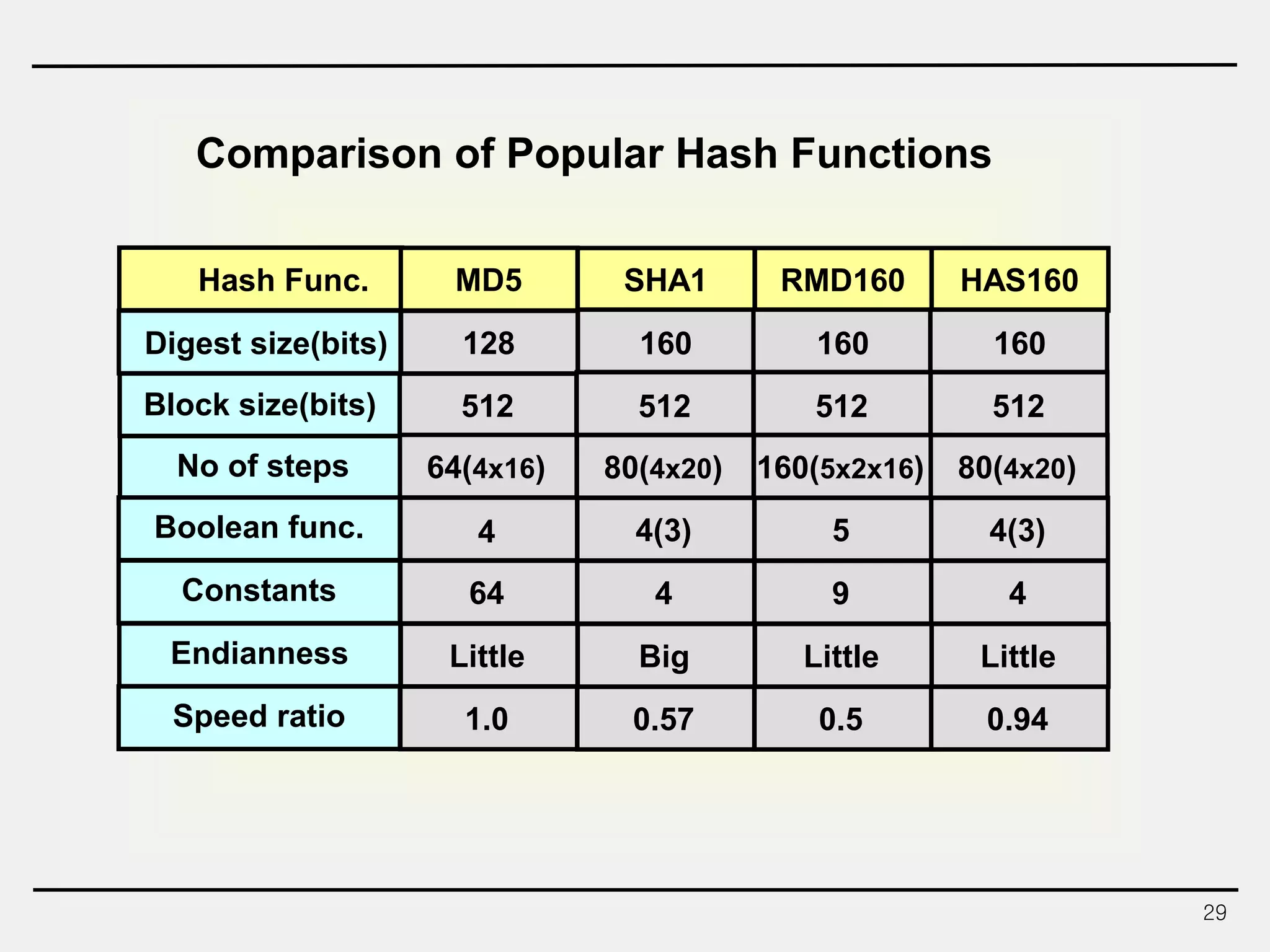
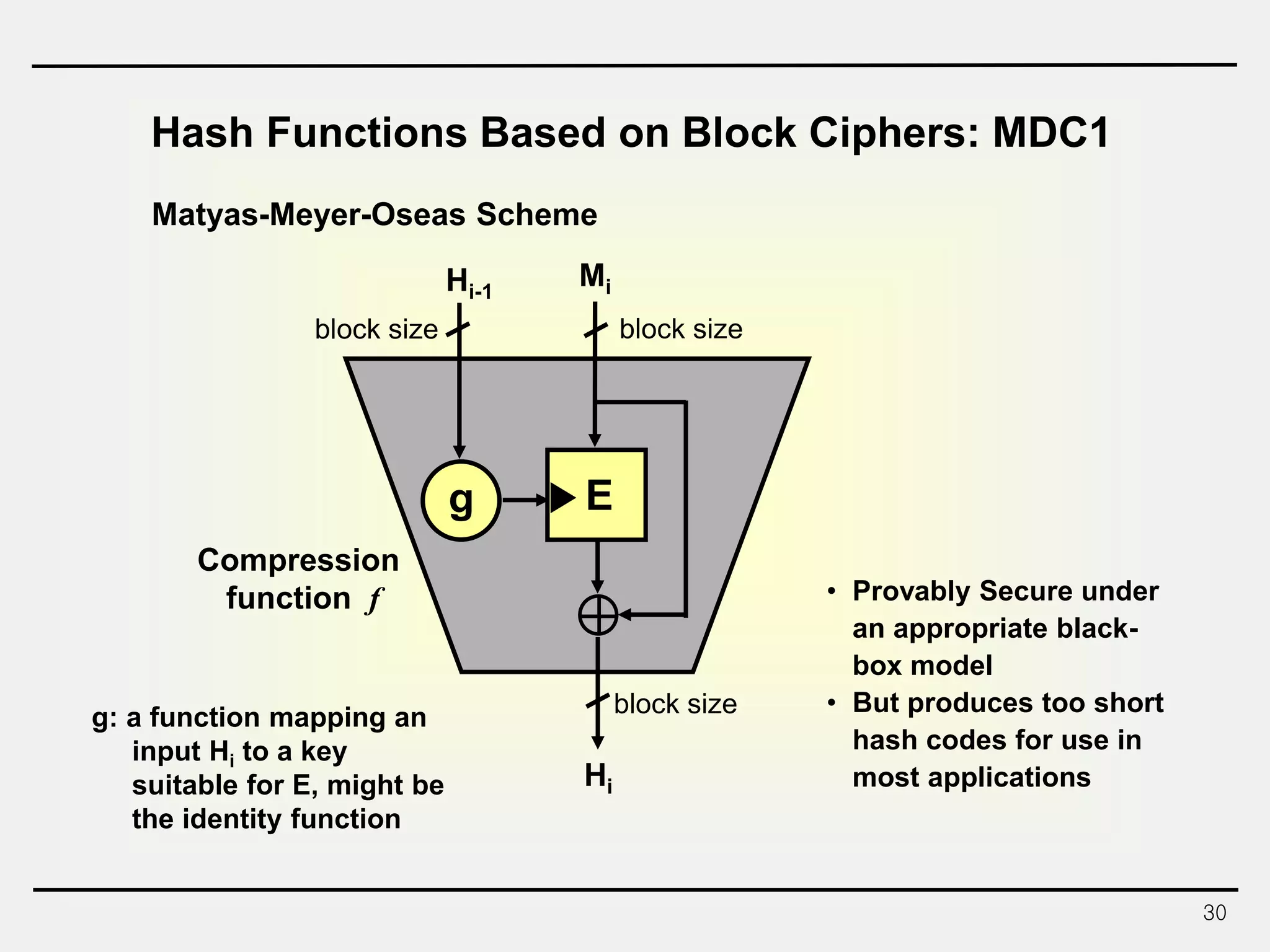
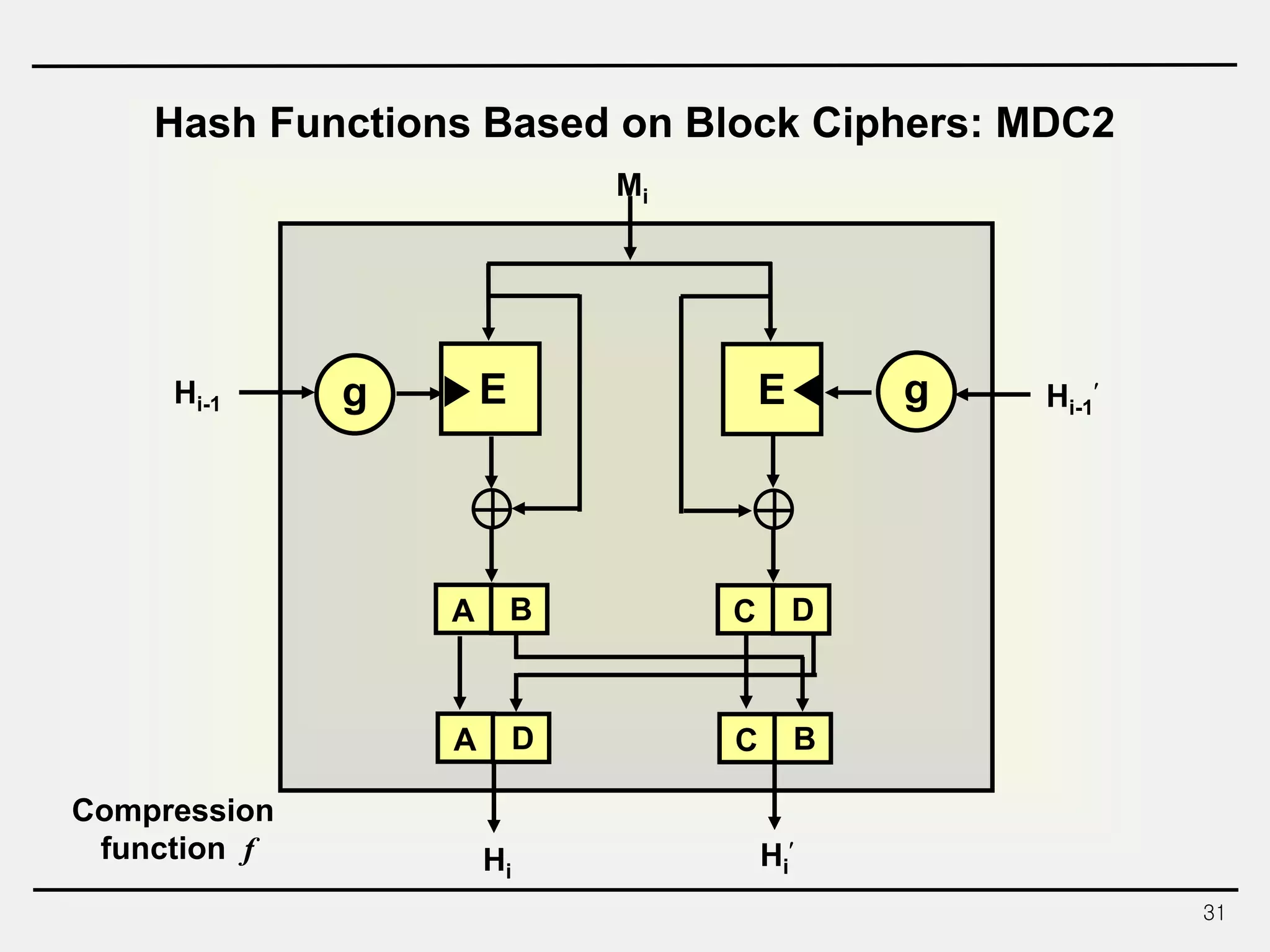
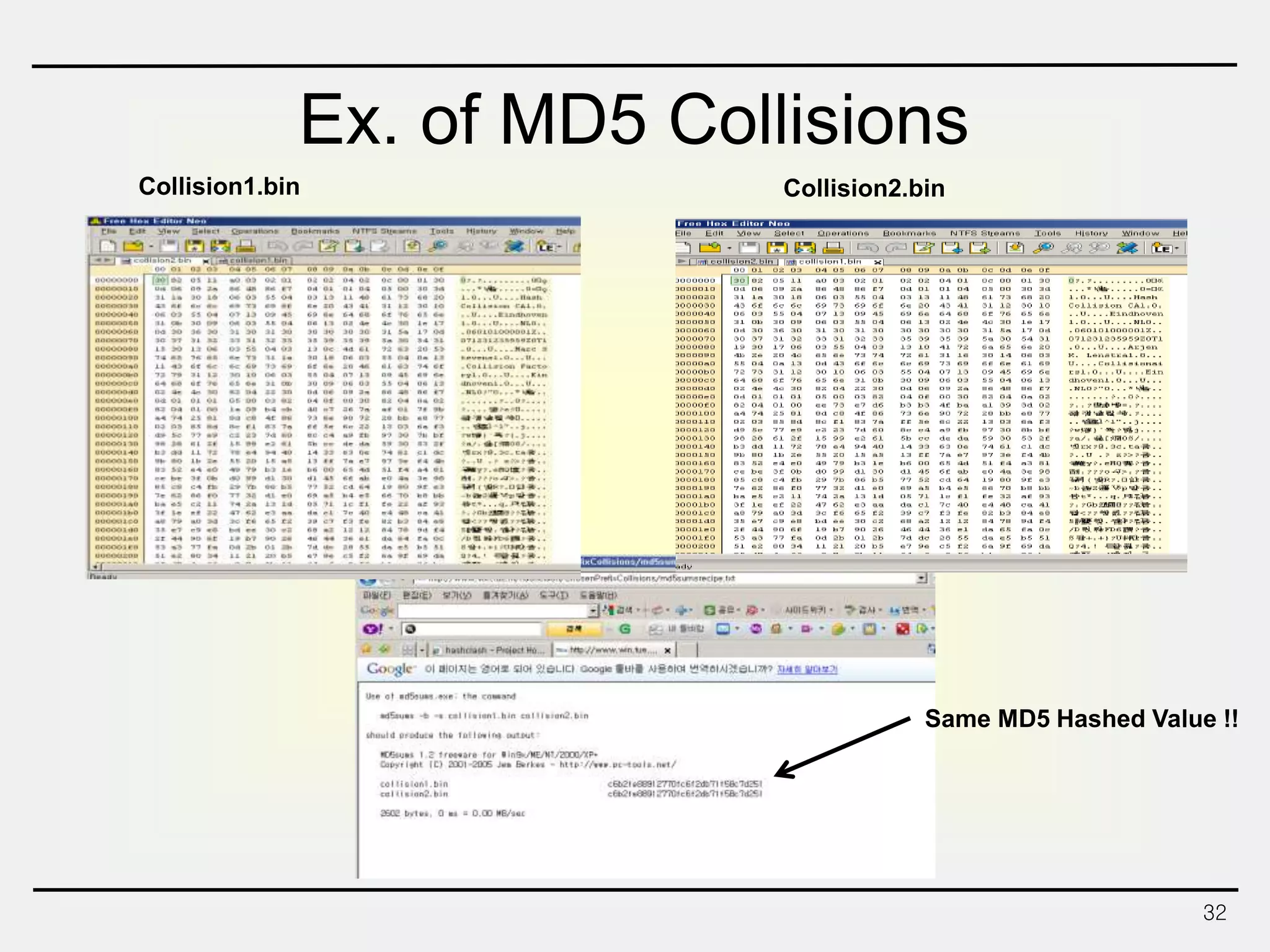
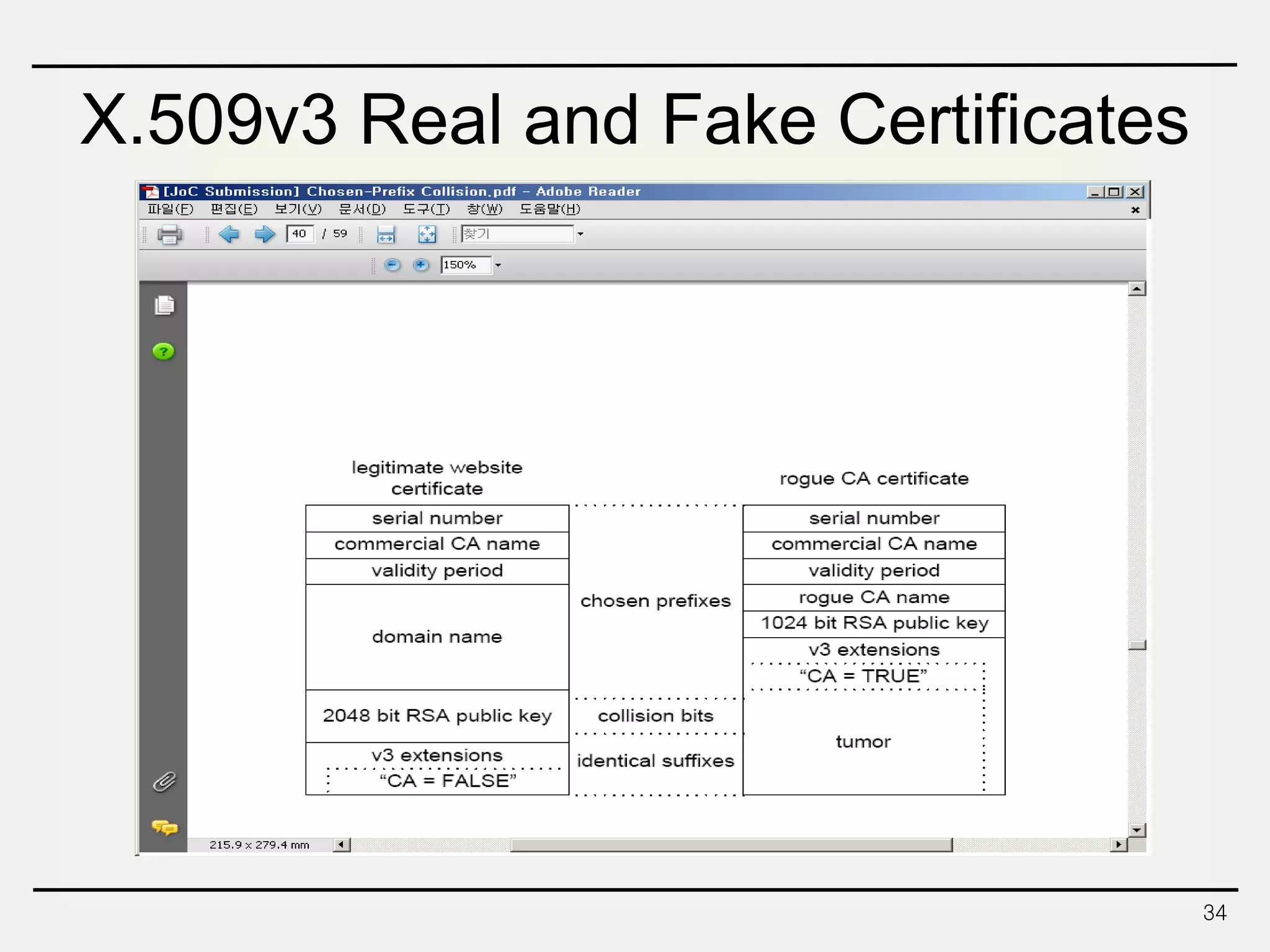
The document discusses hash functions and message authentication codes (MACs). It begins by defining hash functions and MACs, noting that hash functions generate a fingerprint for a message without a key while MACs use a keyed hash function. It then covers security requirements for hash functions like one-wayness and collision resistance. Popular hash functions are described like MD5, SHA-1, and the SHA-2 family. Constructions for hash functions based on block ciphers and iterated hash functions are also outlined. The document concludes by comparing hash functions and MACs and describing common MAC constructions.