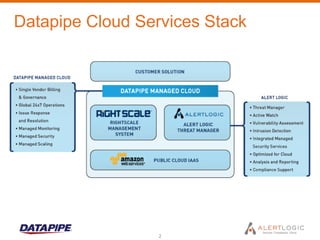
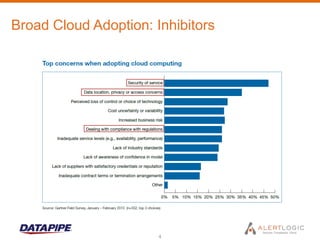
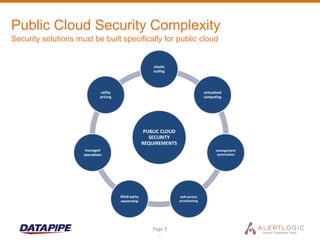
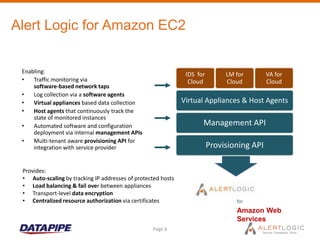
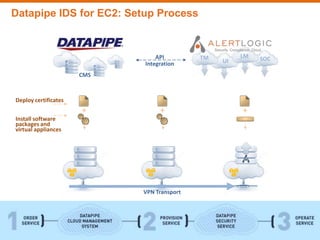
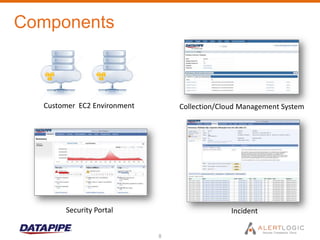
This document discusses managing cloud security and intrusion detection services in public clouds. It describes Datapipe's cloud security stack including intrusion detection, 2-factor authentication, vulnerability scanning, integrity monitoring, and firewall/antivirus software. It also discusses how security solutions must be adapted specifically for public clouds due to attributes like elastic scaling, utility pricing, and virtualization. The document outlines how Alert Logic provides intrusion detection for Amazon EC2 through software-based network taps, log collection agents, and virtual appliances to detect threats across elastic cloud environments.