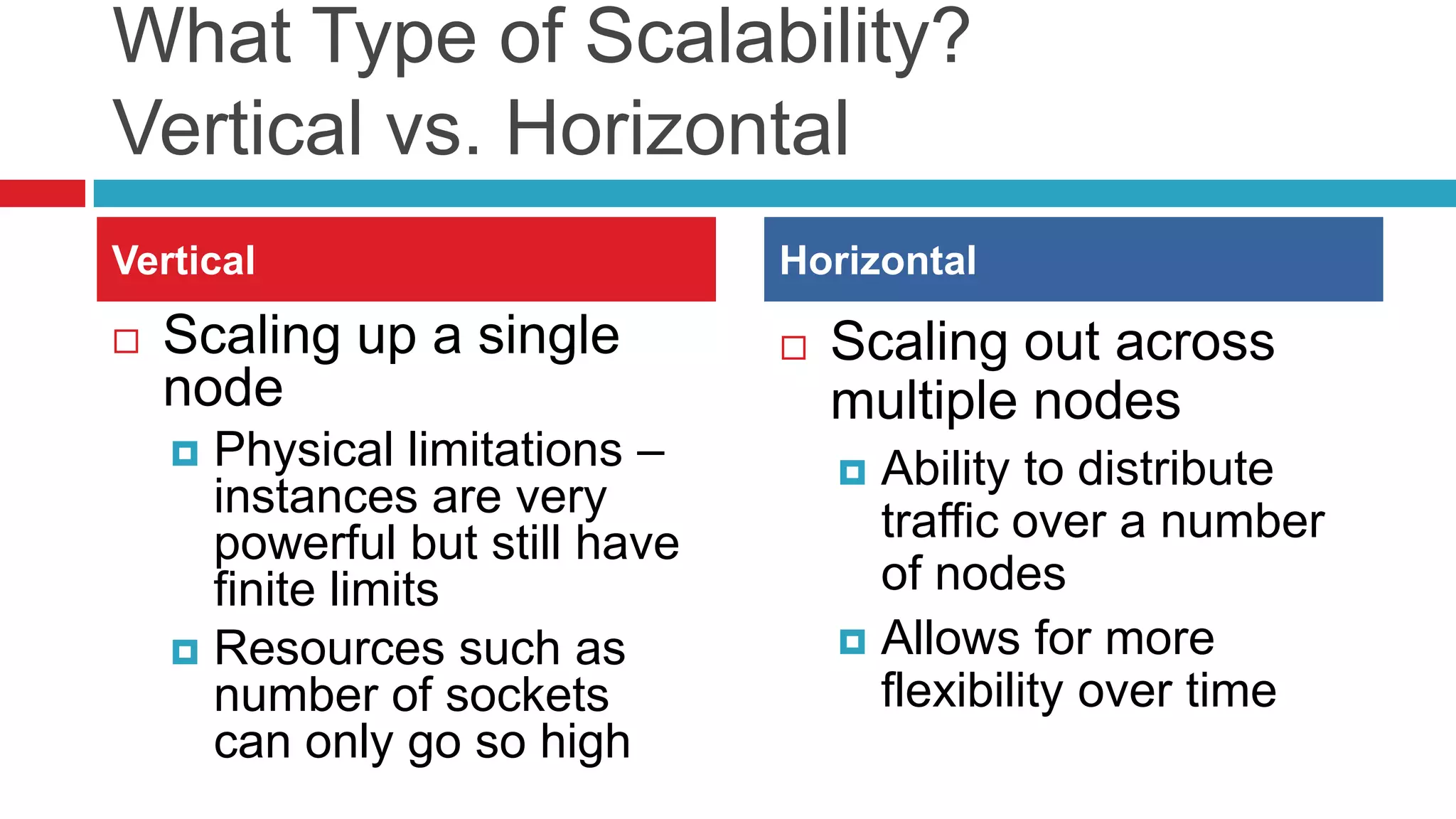
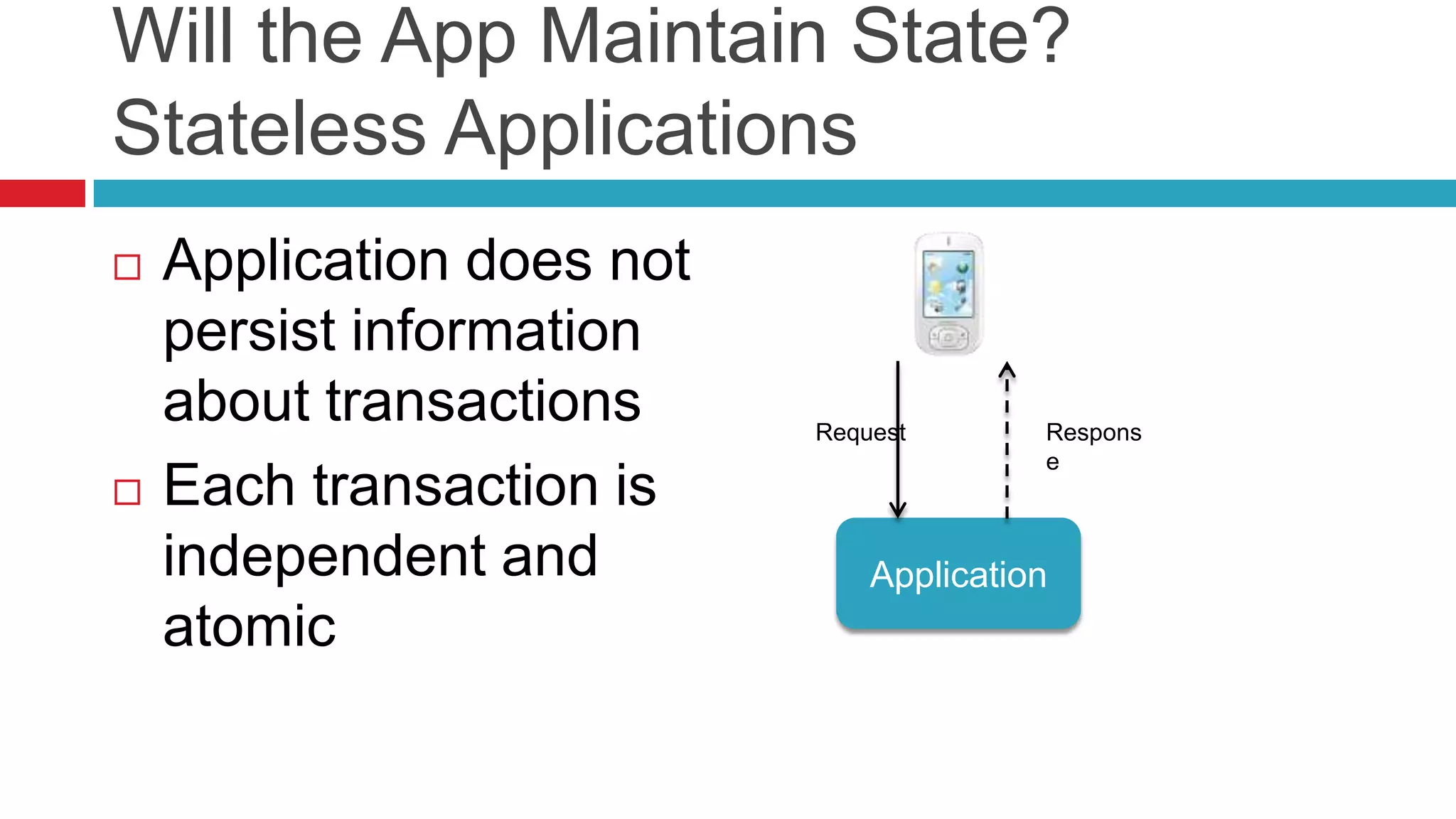
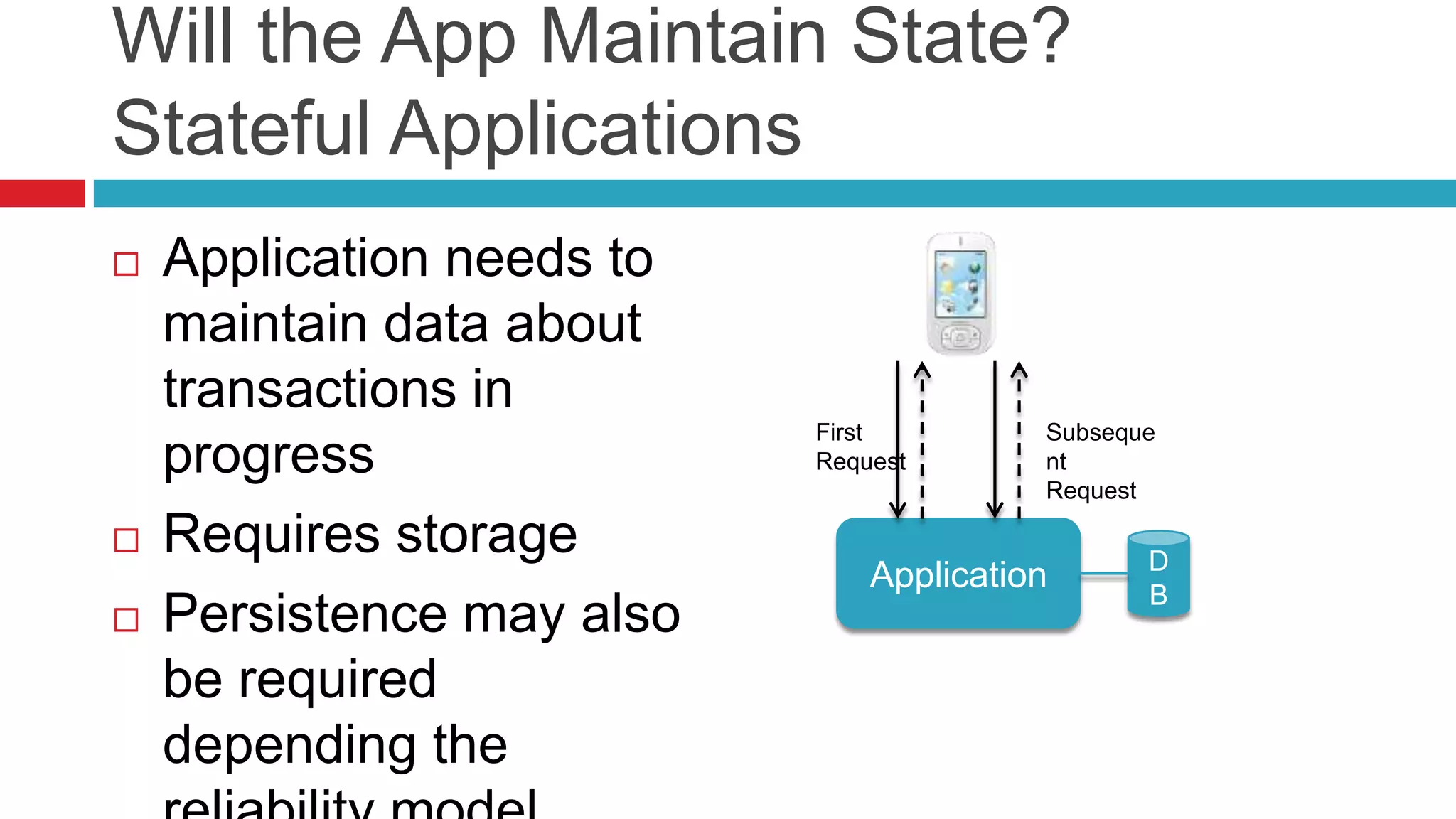
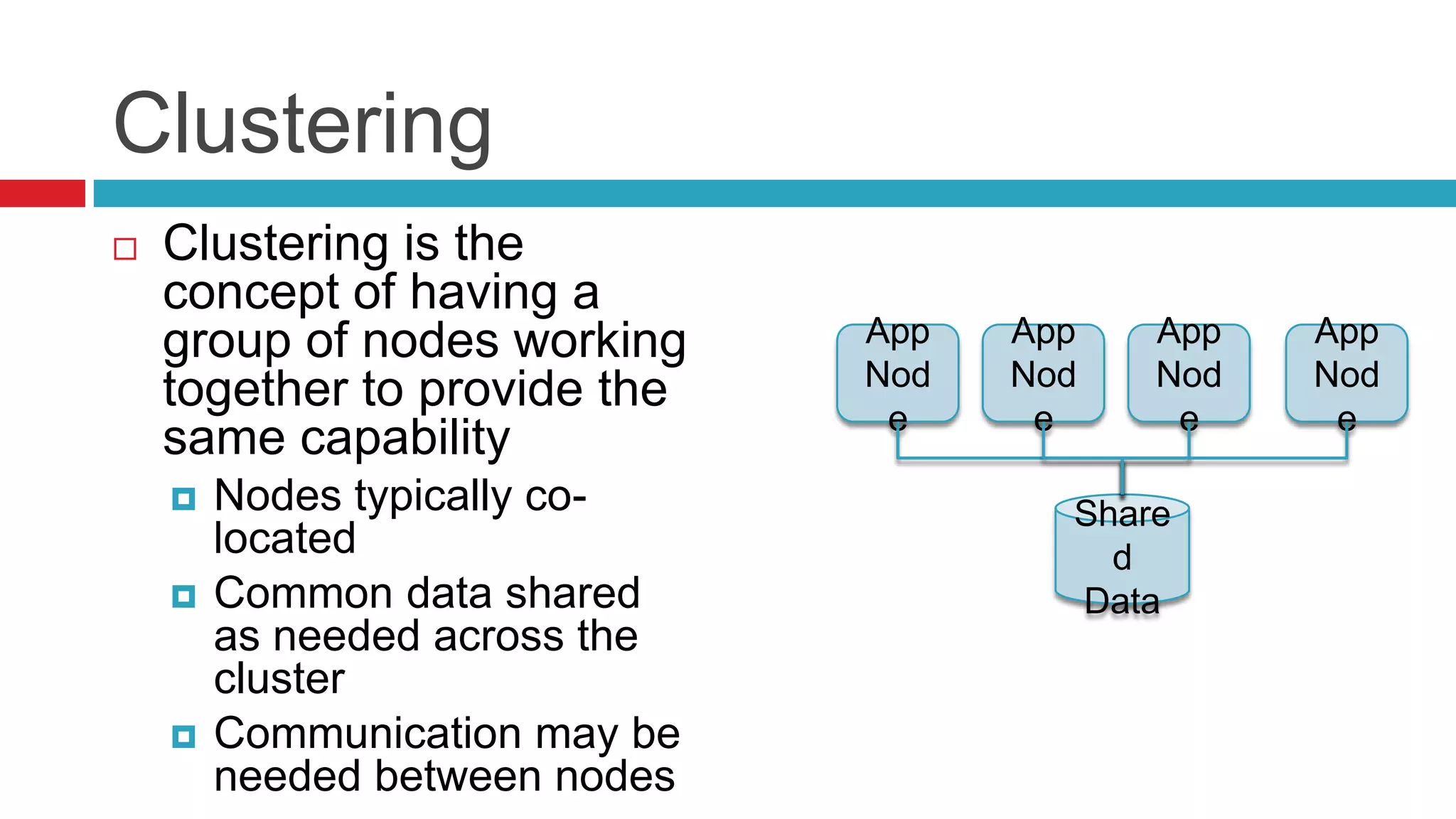
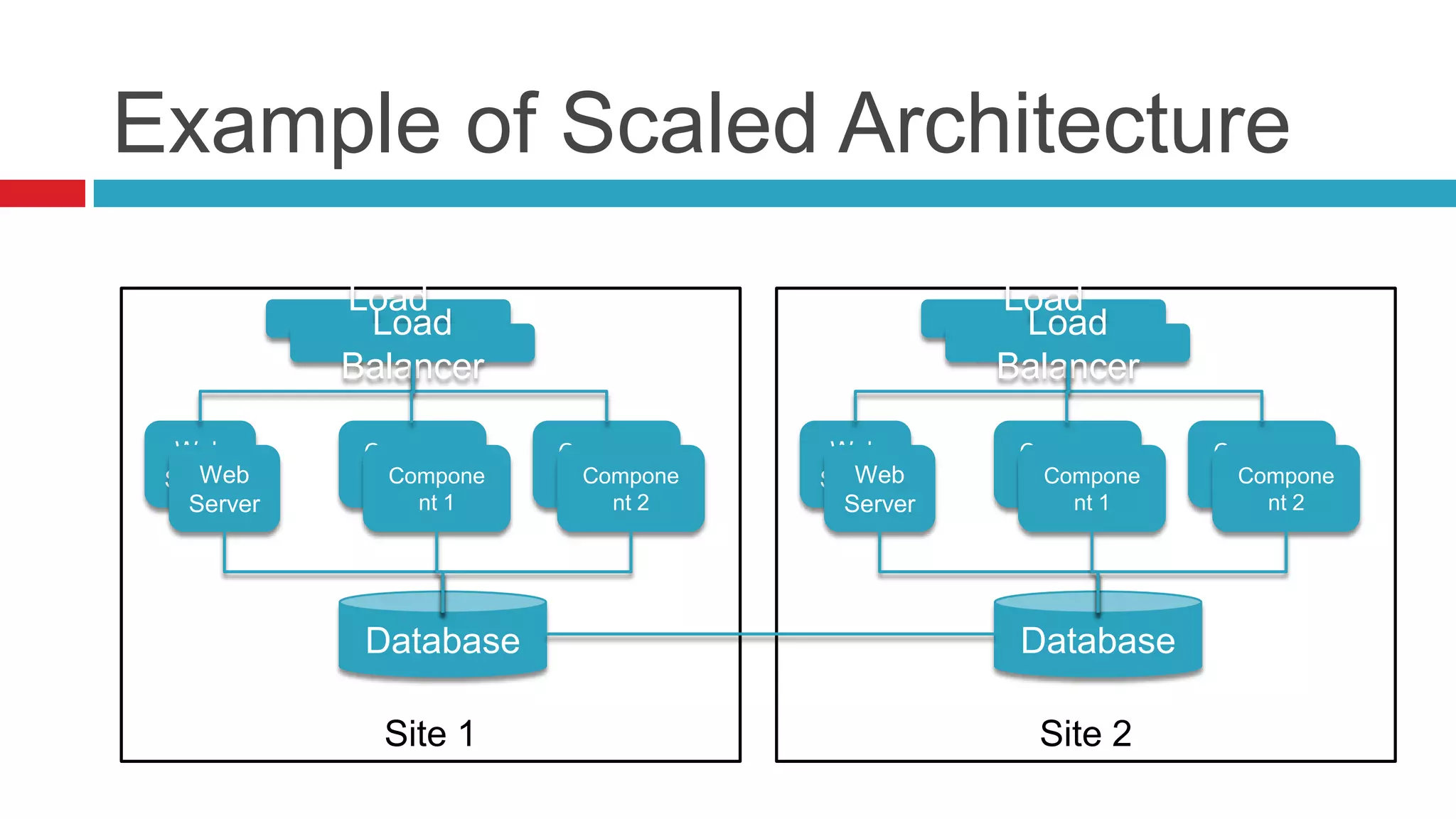
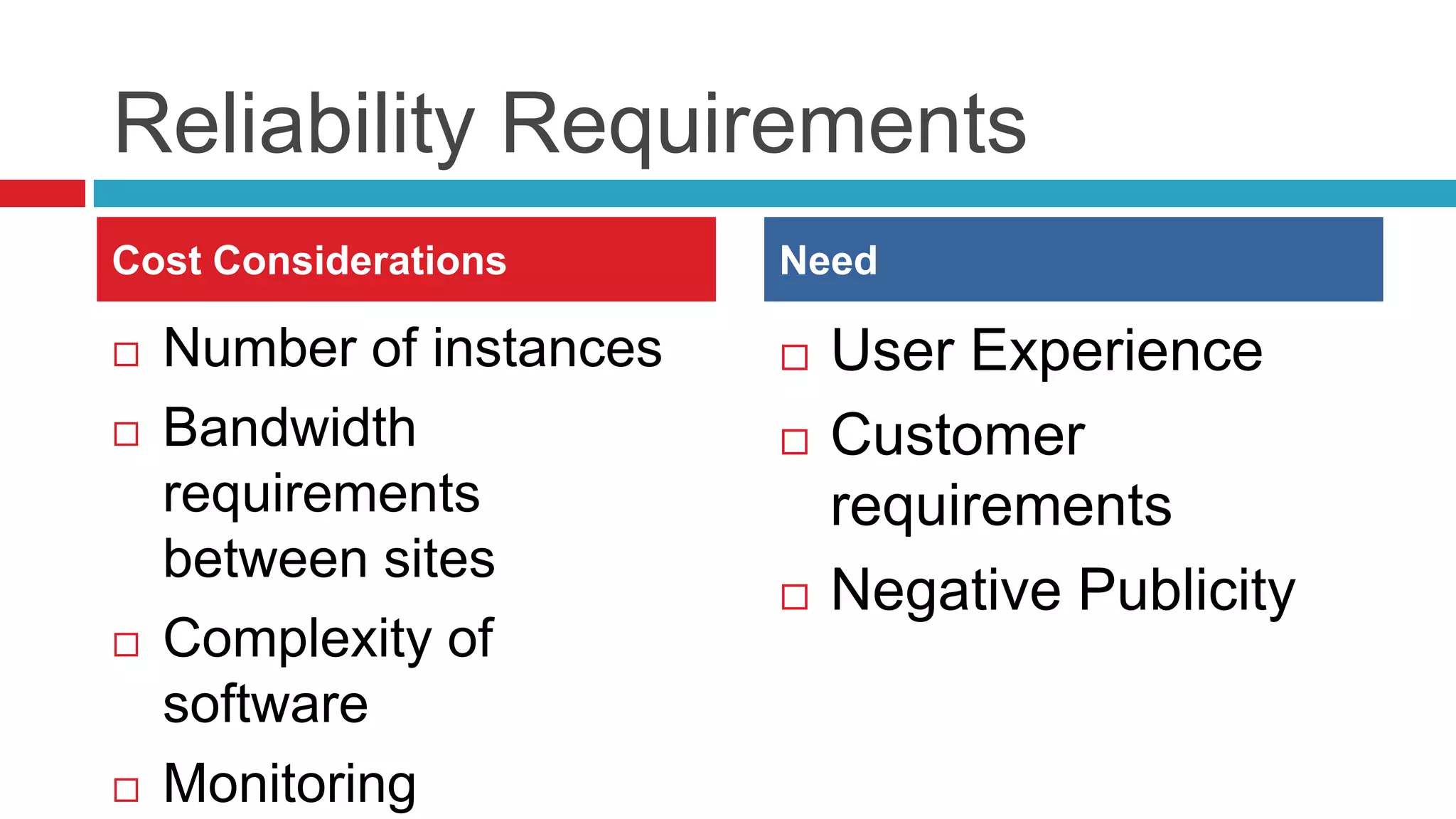
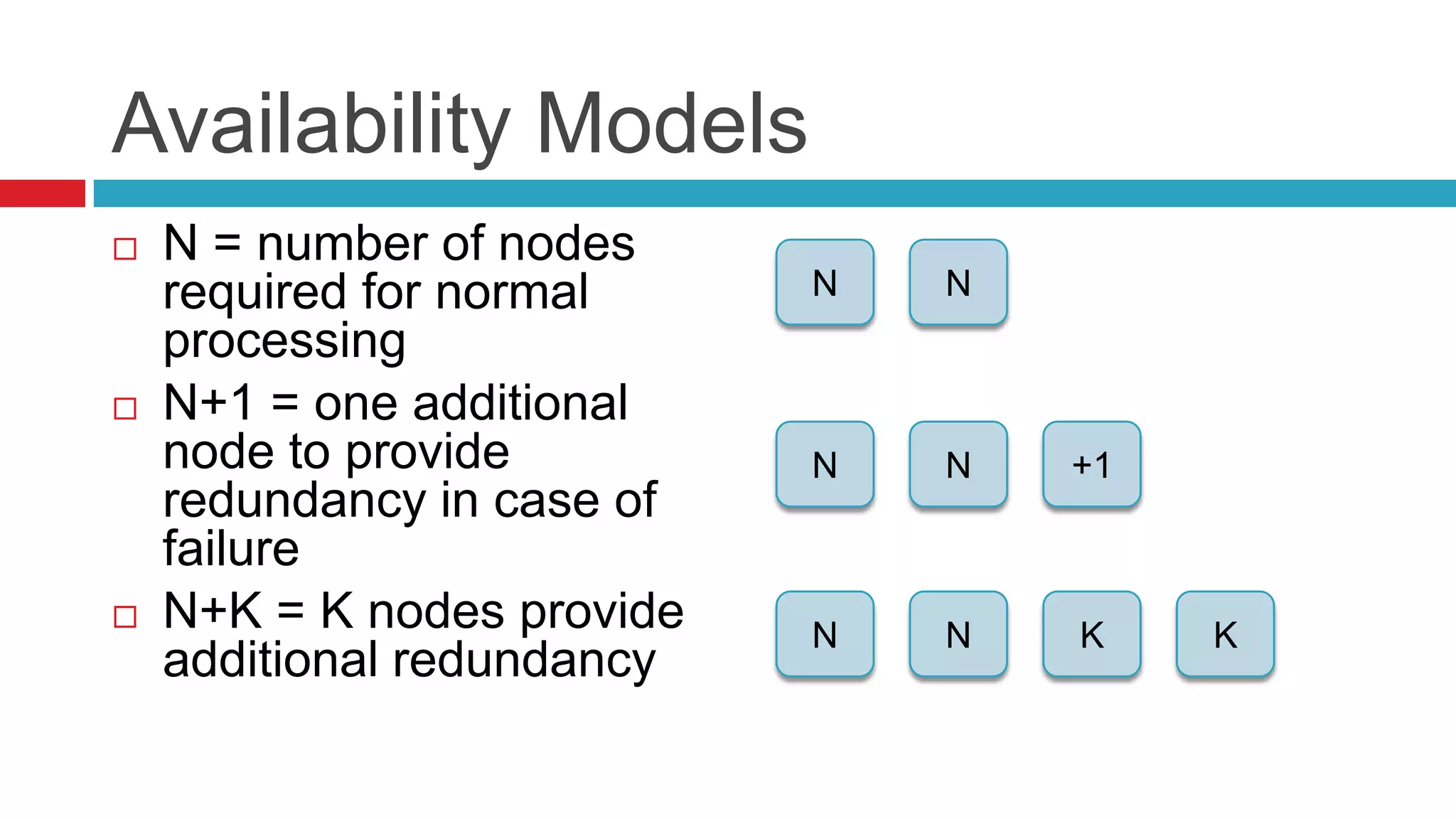
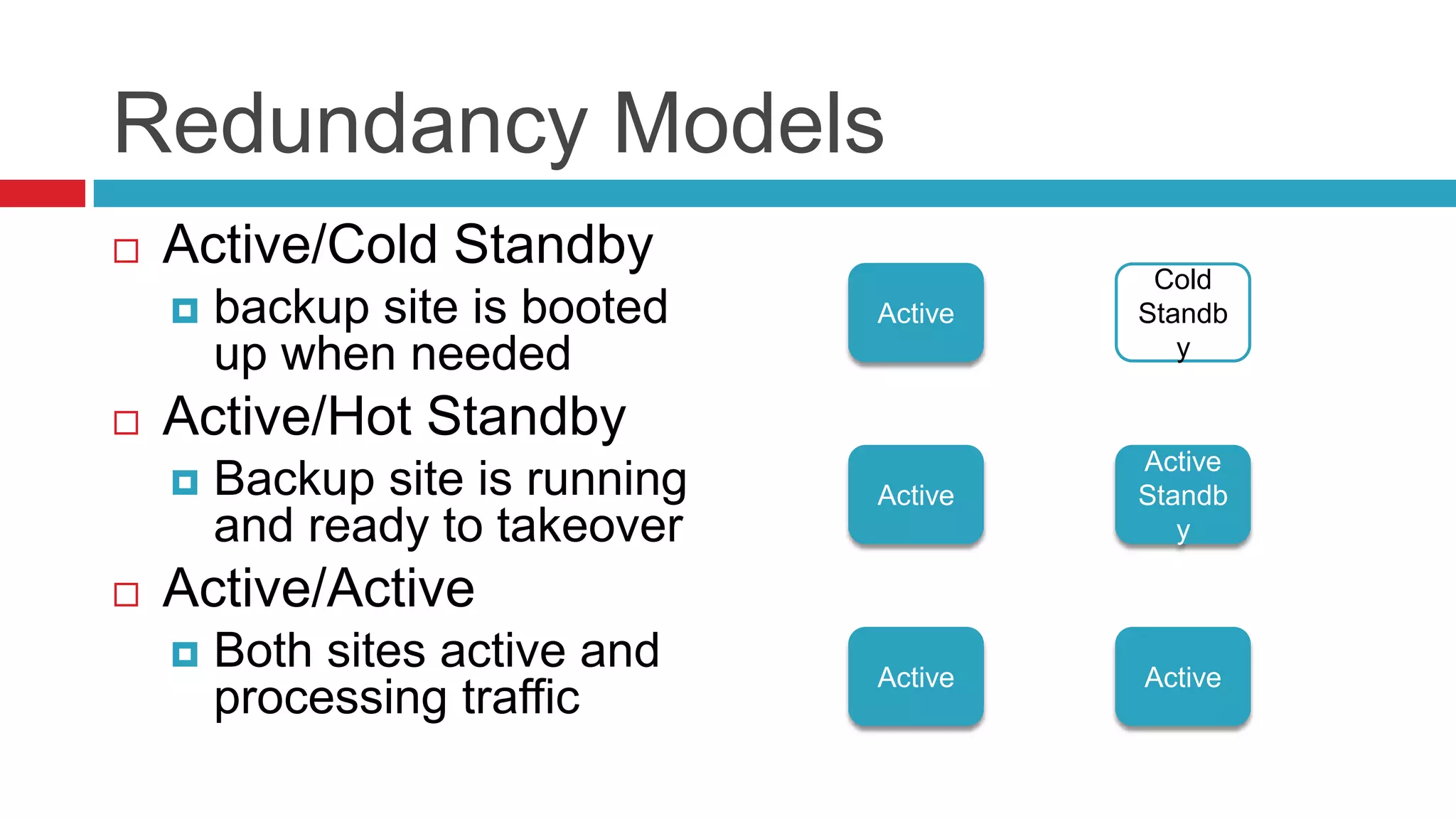
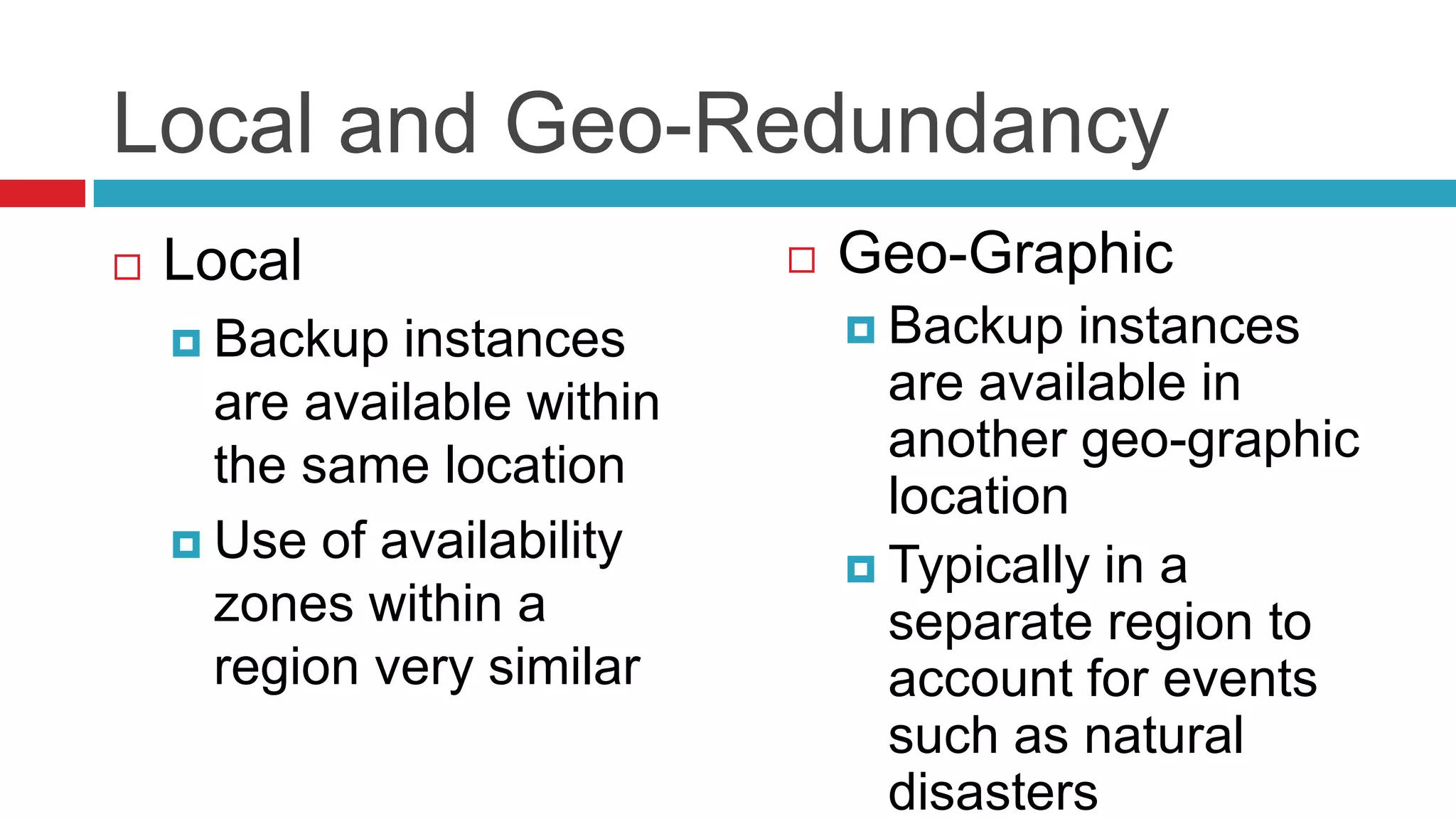
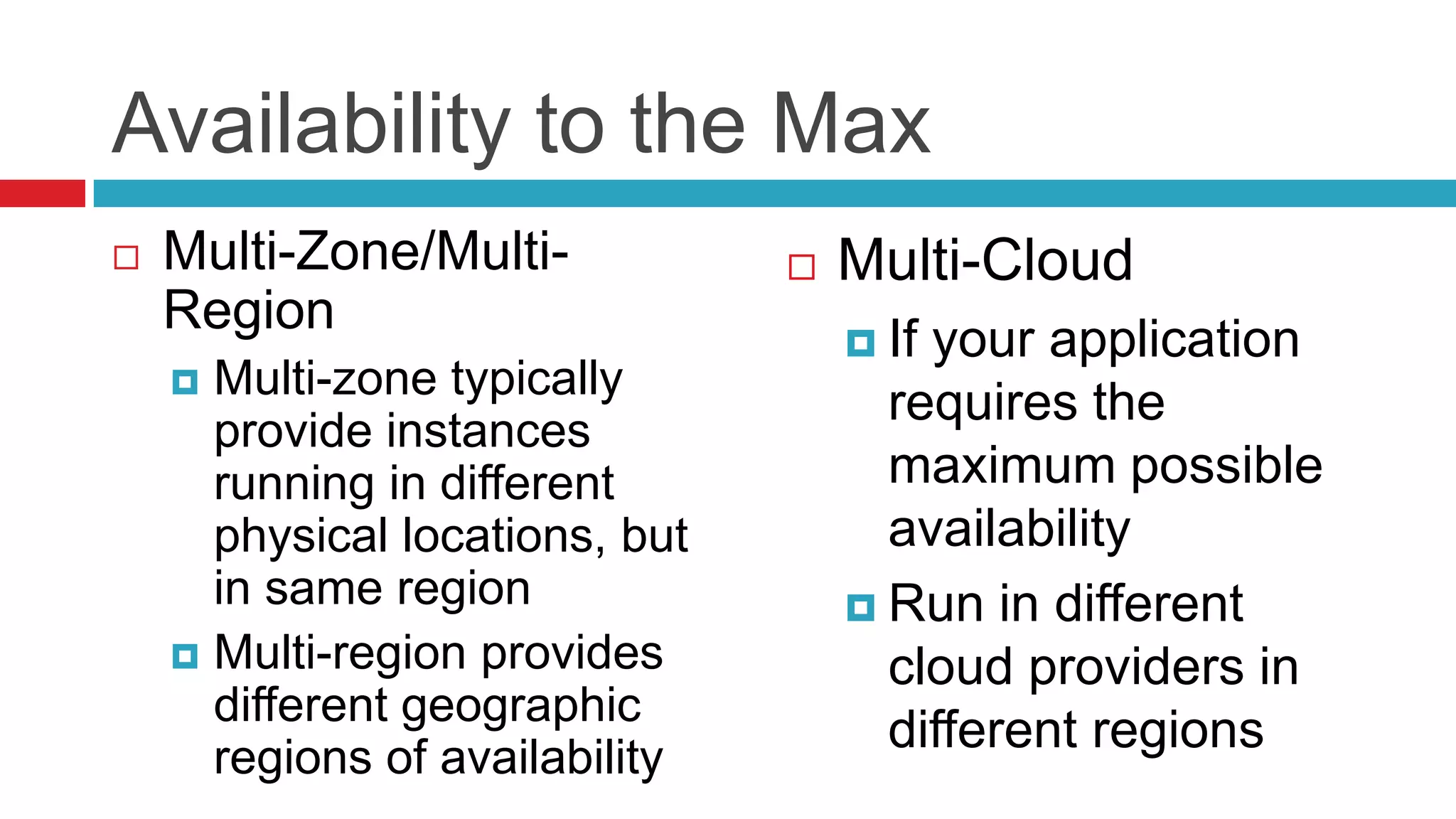
This document discusses key considerations for backend application developers regarding scalability and reliability in cloud environments, focusing on factors such as state management, traffic segmentation, and clustering. It outlines the importance of testing, monitoring, and automation to enhance application availability and reduce downtime. Additionally, it explores various availability models and strategies for handling failures and improving overall reliability.