Embed presentation
Downloaded 164 times



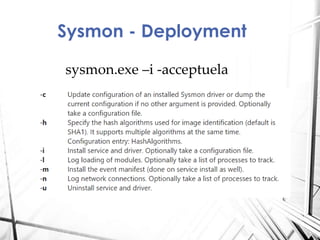

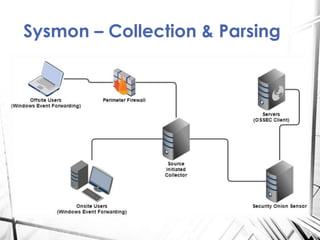

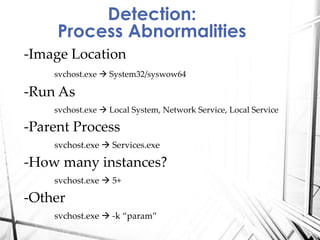


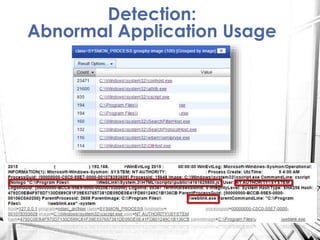


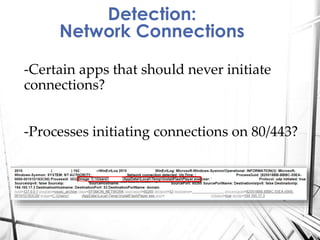
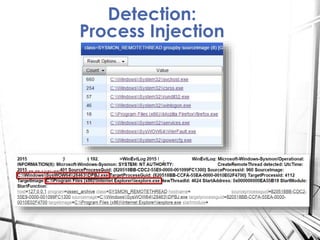





Sysmon is a Windows system service and tool that monitors process creation and other system events. It provides visibility into process activity through logging process command lines, parent processes, file and network activity. The summary discusses how to deploy Sysmon, collect its logs, and analyze the logs for detections related to abnormal processes, applications, network connections, process injections and loaded drivers. It concludes with discussing rulesets for detections and future work.



















