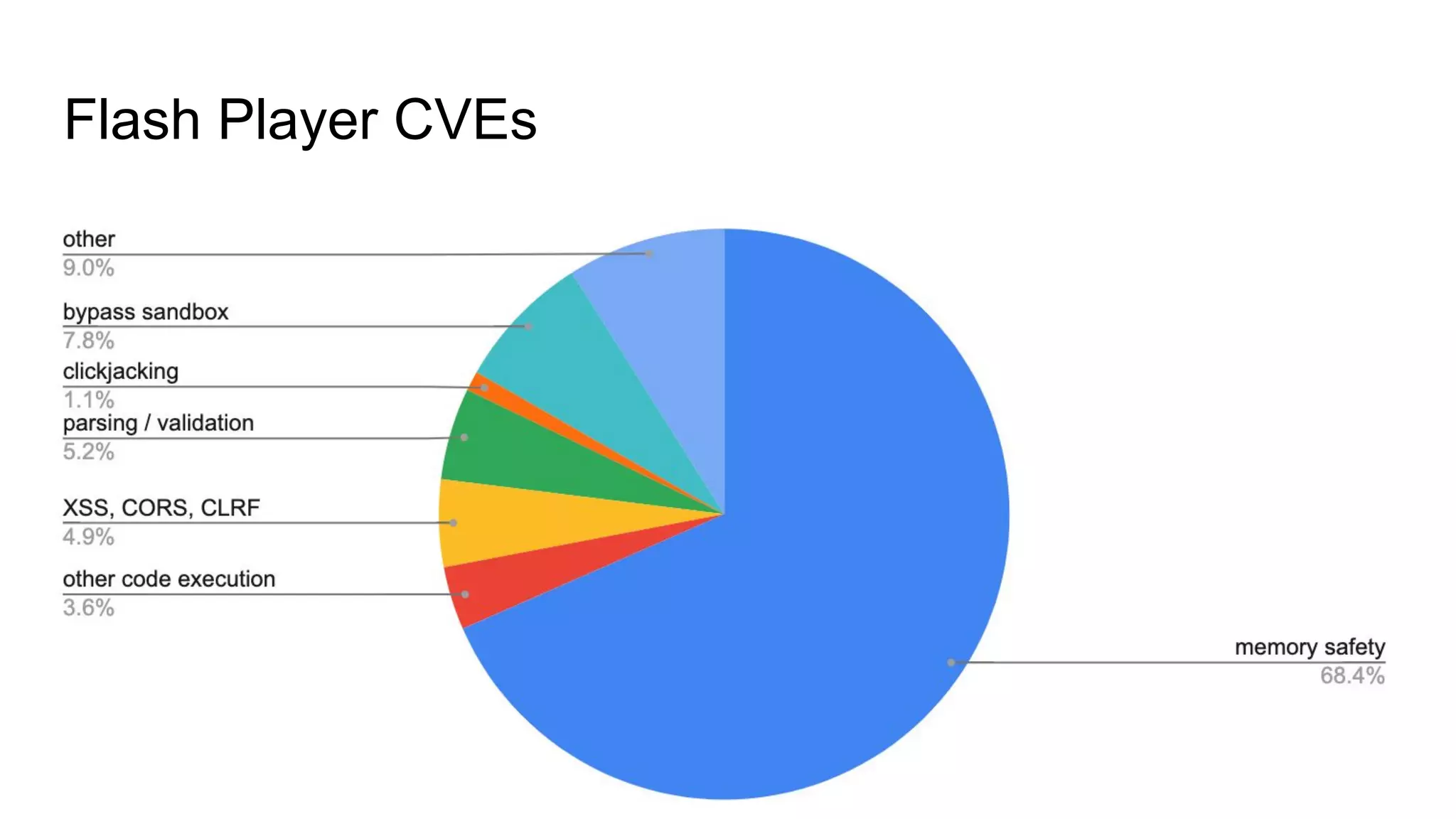
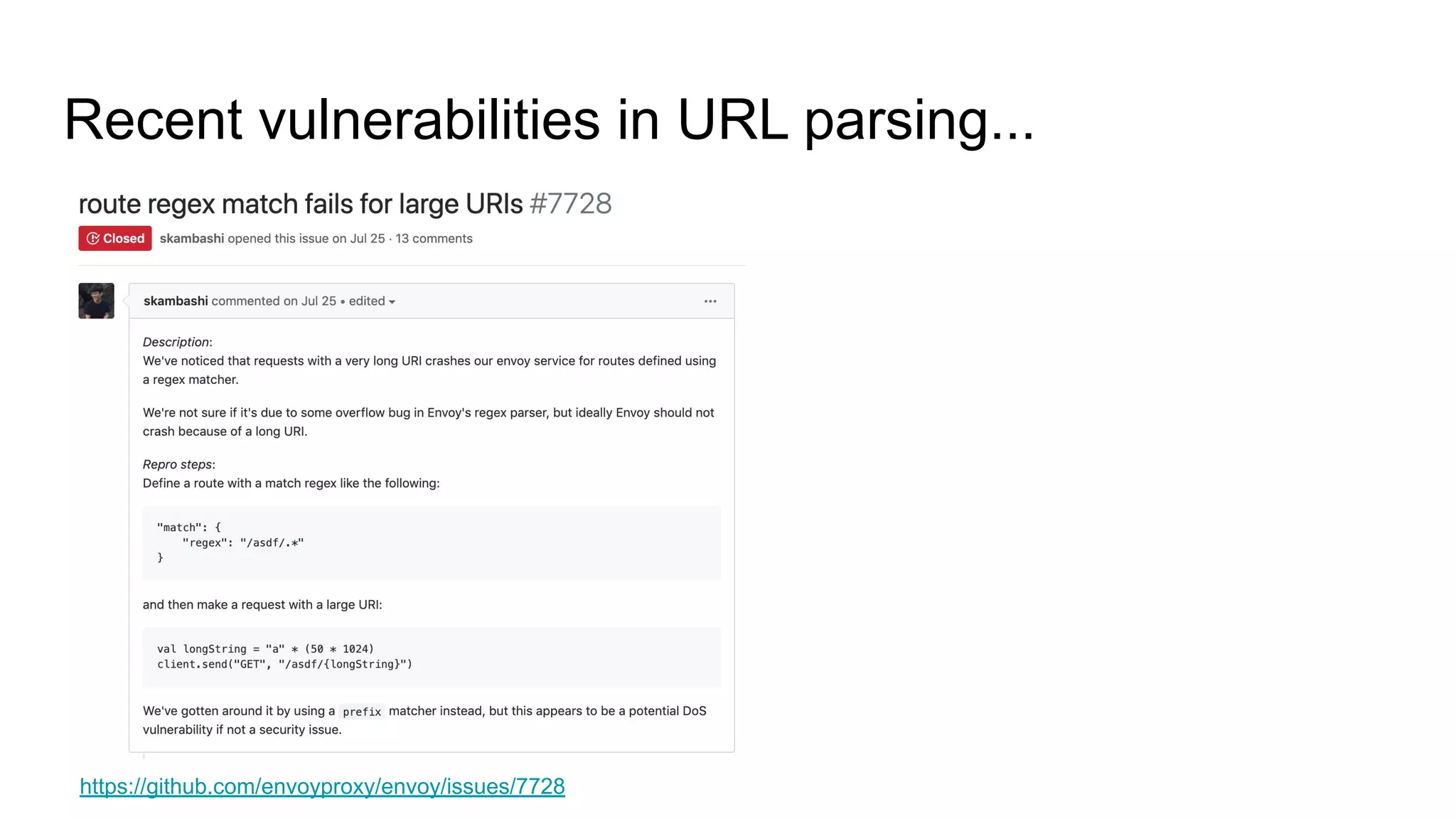
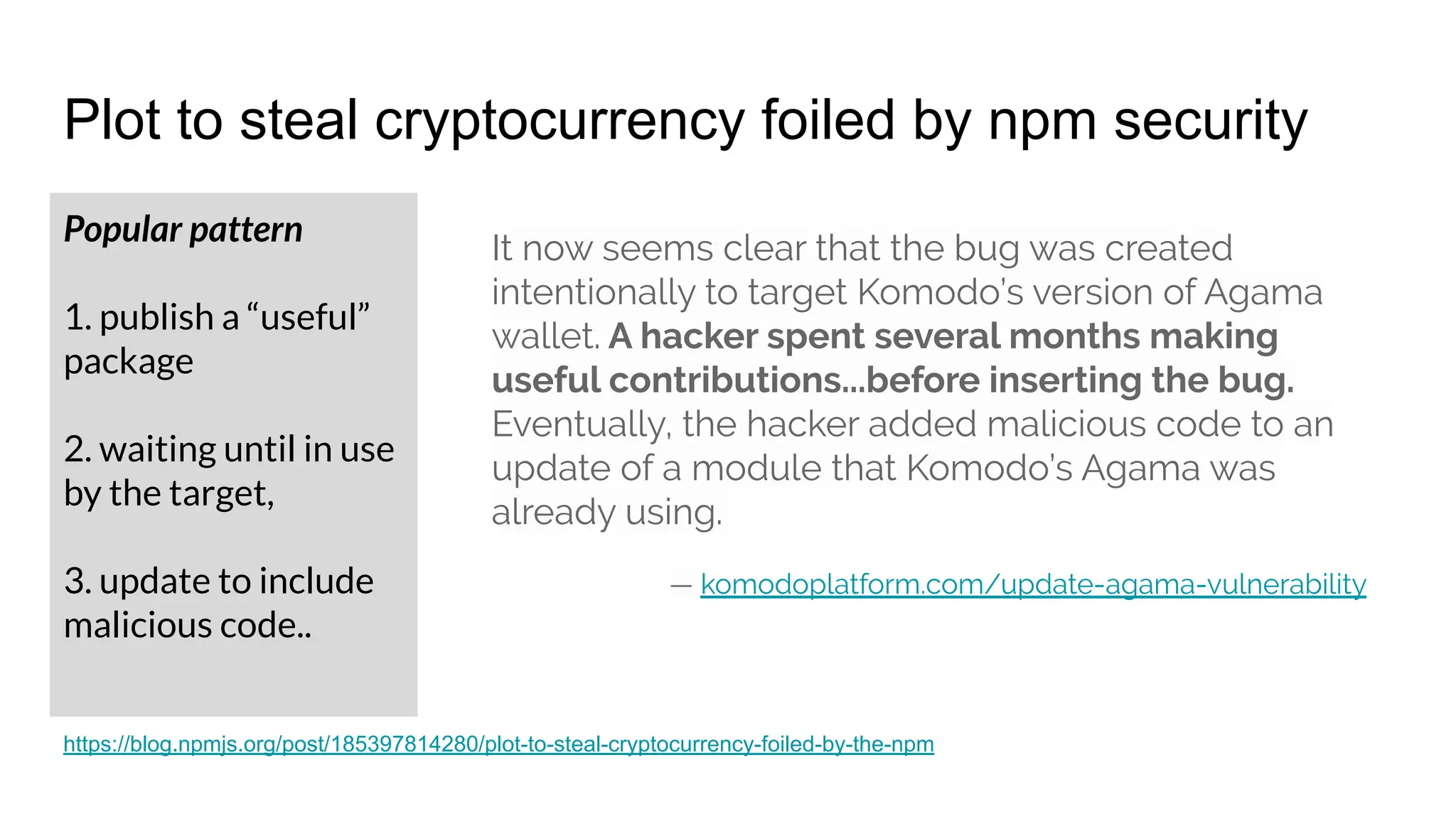
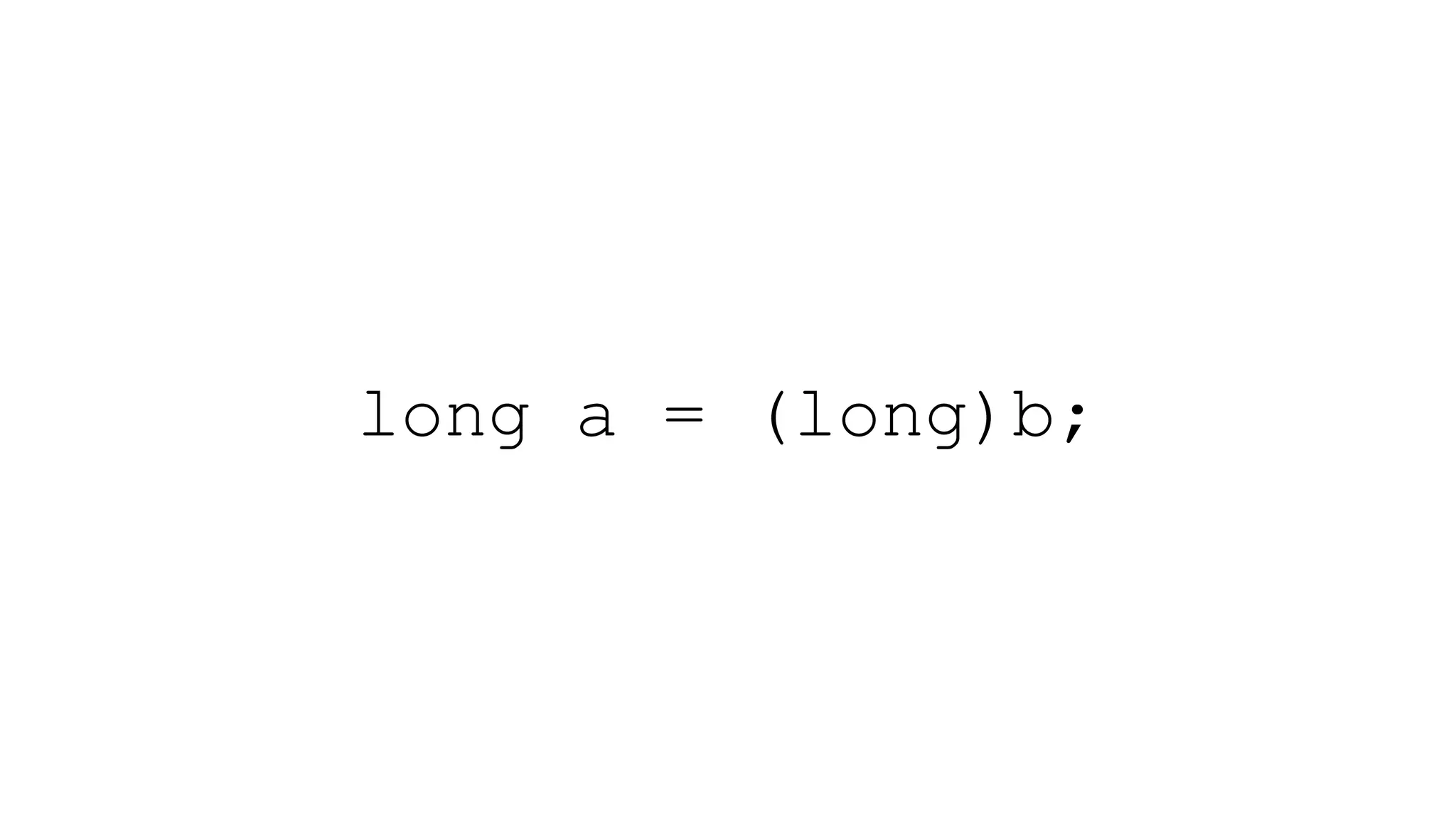The document discusses various cybersecurity vulnerabilities and attack methods, specifically focusing on issues related to memory safety and exploitation techniques in software. It highlights the importance of being prepared for breaches with incident response plans and critiques common security practices. Additionally, it addresses evolving security landscapes, emphasizing the need for secure programming practices and proactive monitoring.