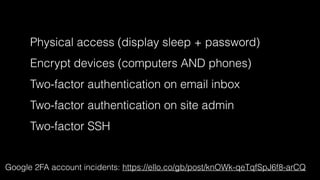
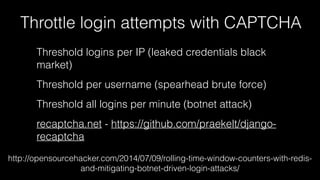
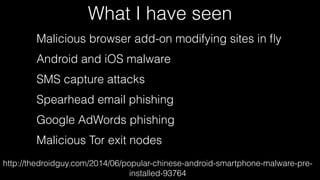
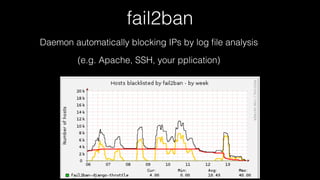
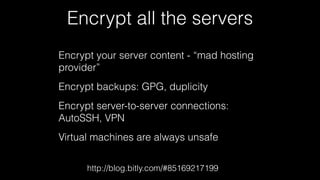
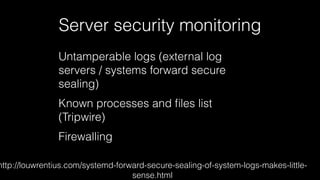
The document discusses operations security (opsec) with a focus on securing user data and infrastructure against various cyber threats, emphasizing the importance of two-factor authentication, encryption, and proper password management. It outlines strategies to mitigate risks such as malware, phishing, and brute-force attacks, and recommends solutions like fail2ban and server encryption. Additionally, it highlights key practices for maintaining security hygiene in both personal and organizational contexts.