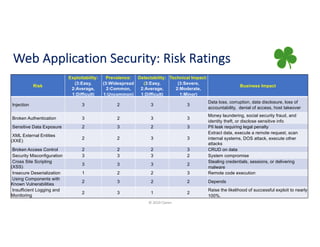
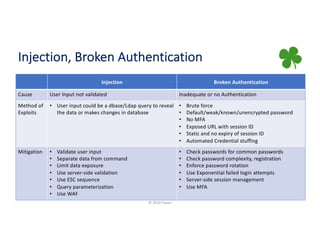
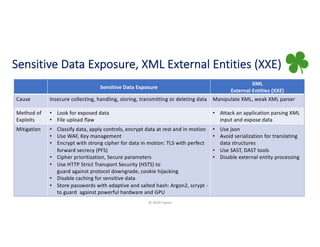
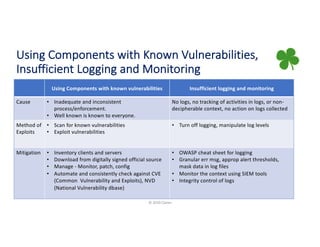
The document provides a comprehensive overview of application security, covering various topics such as web, mobile, API, container, and open-source security. It highlights key vulnerabilities, attack methods, and best practices for securing applications against risks like injections, broken authentication, and insecure data handling. Additionally, it emphasizes the importance of continuous security assessments and adherence to best practices to mitigate potential threats.