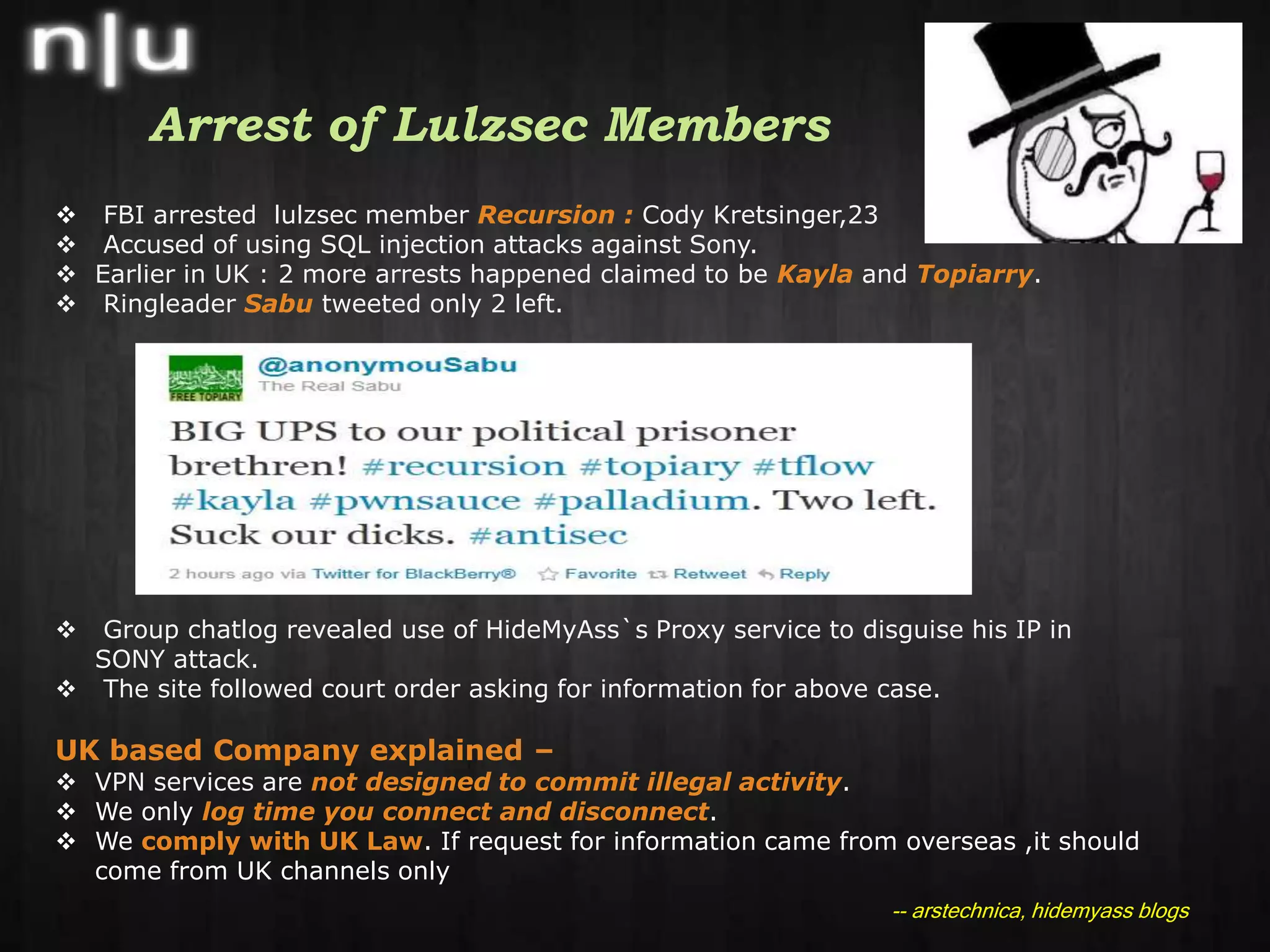
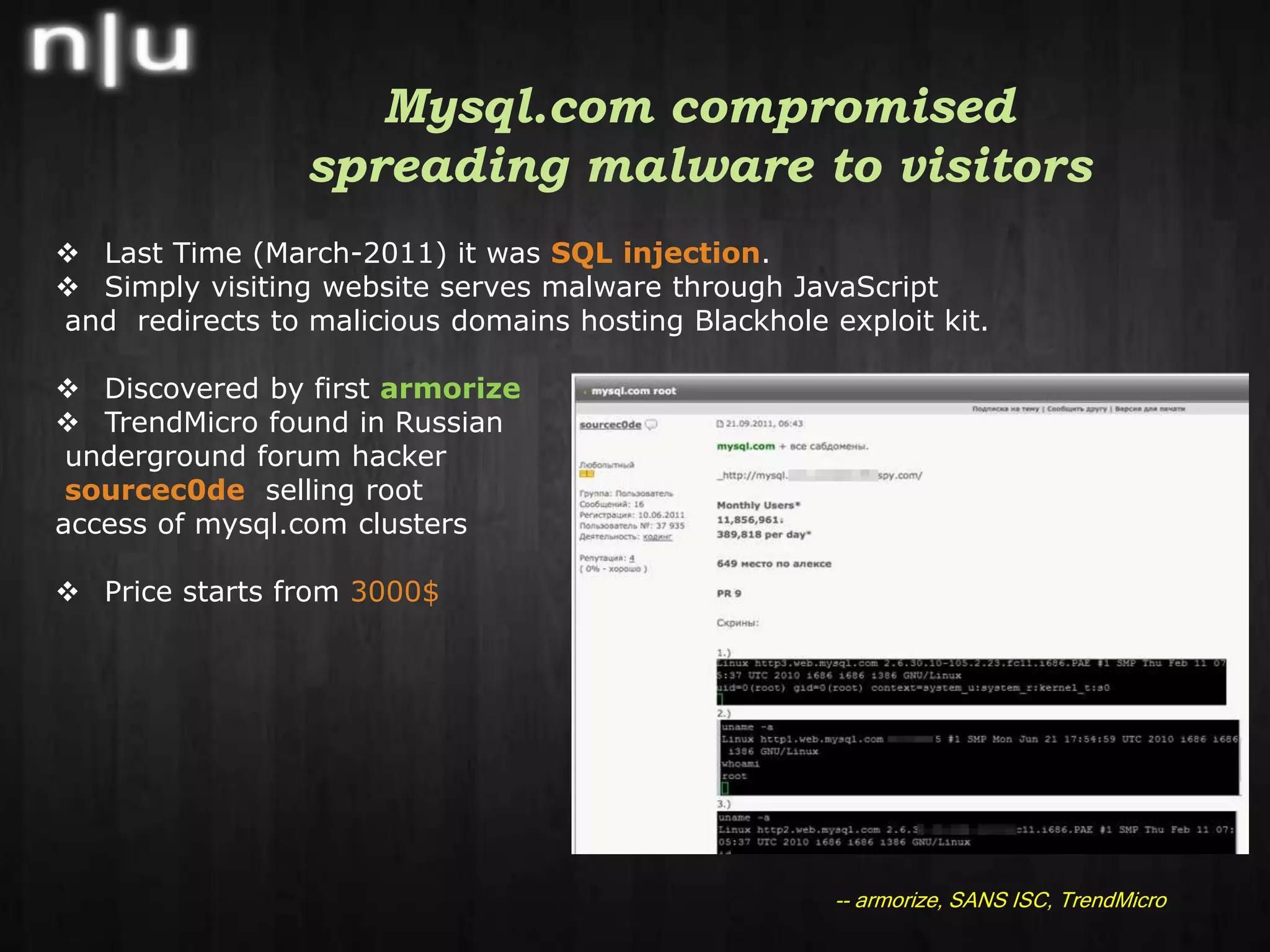
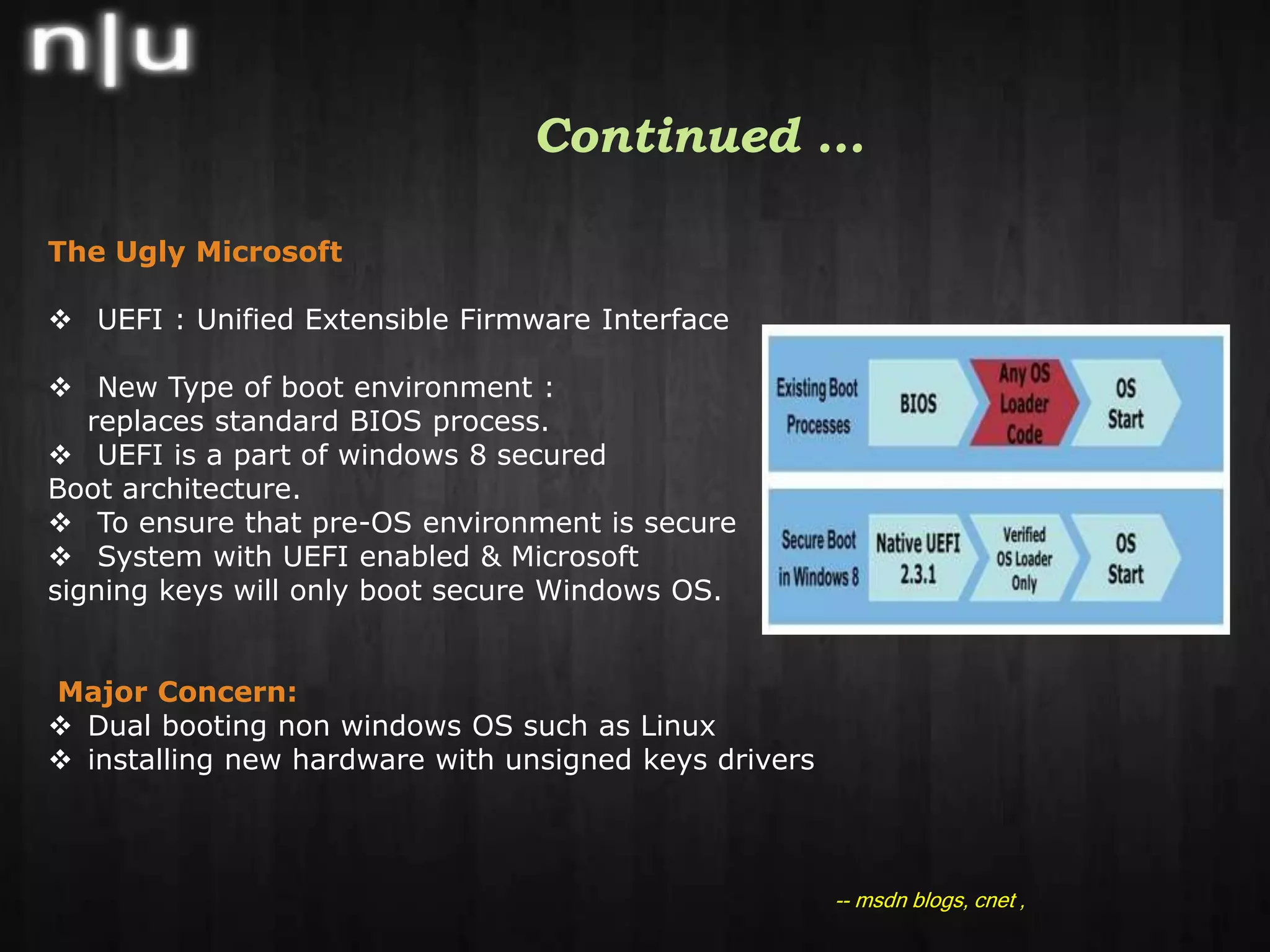
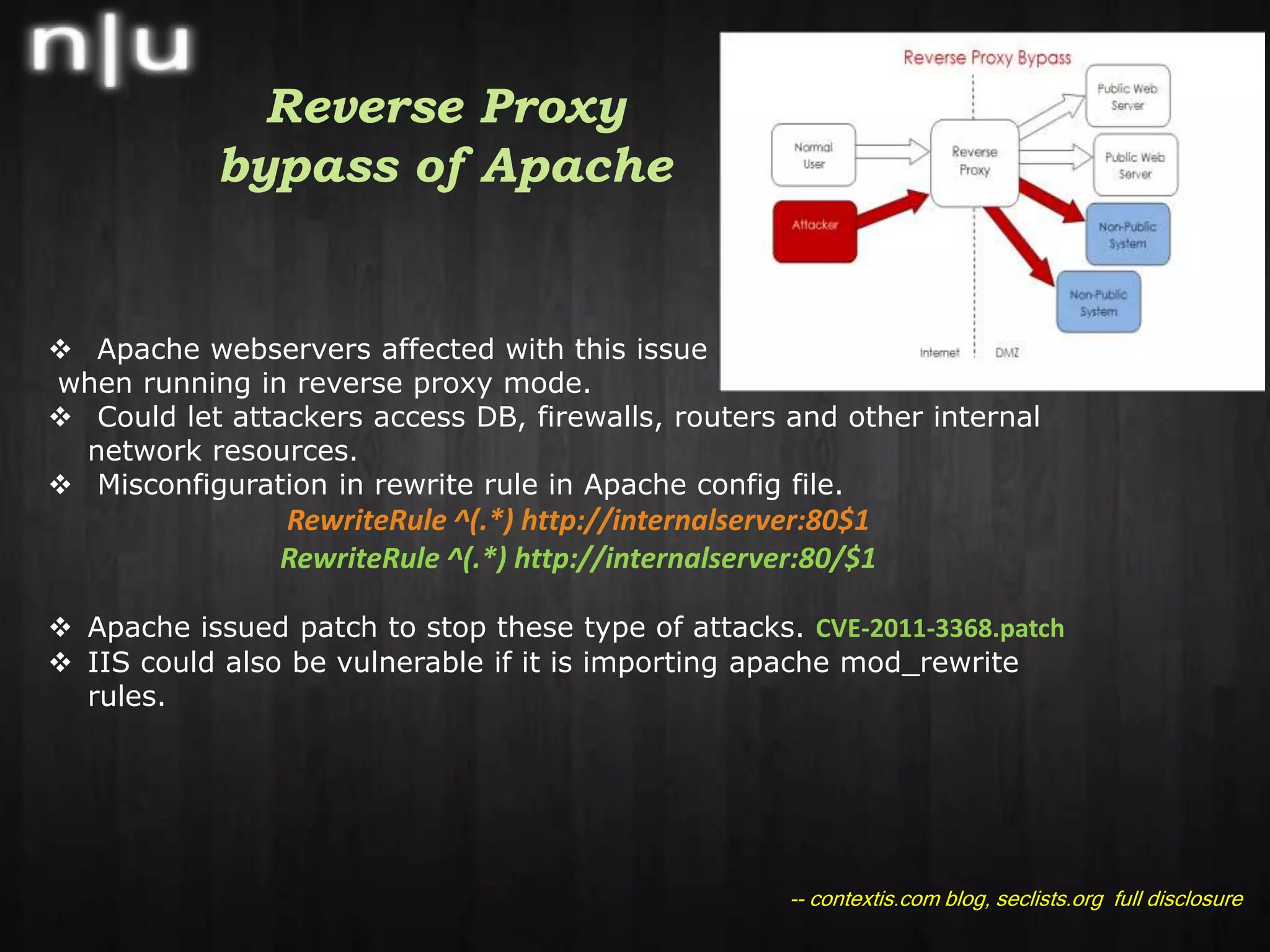
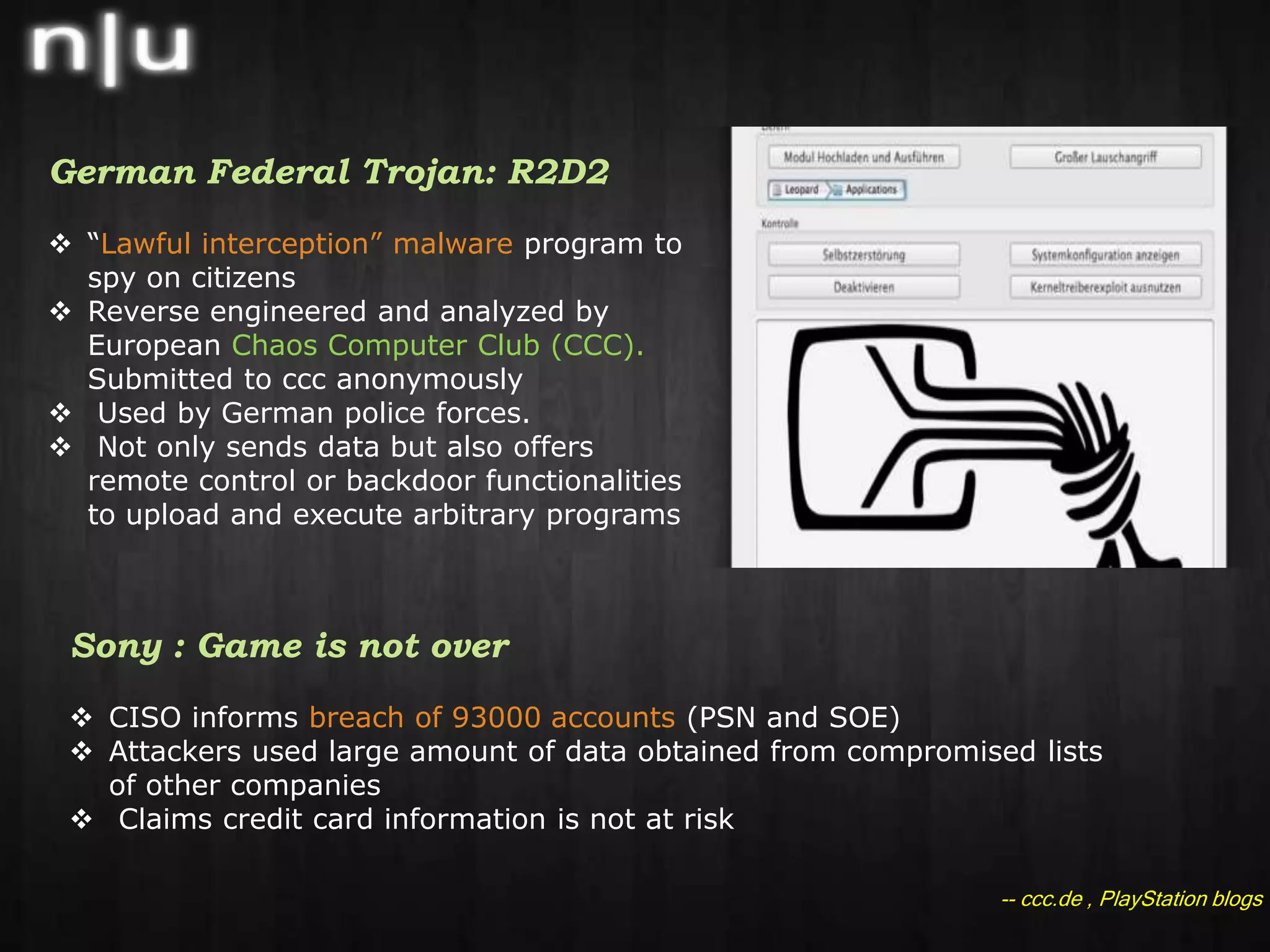
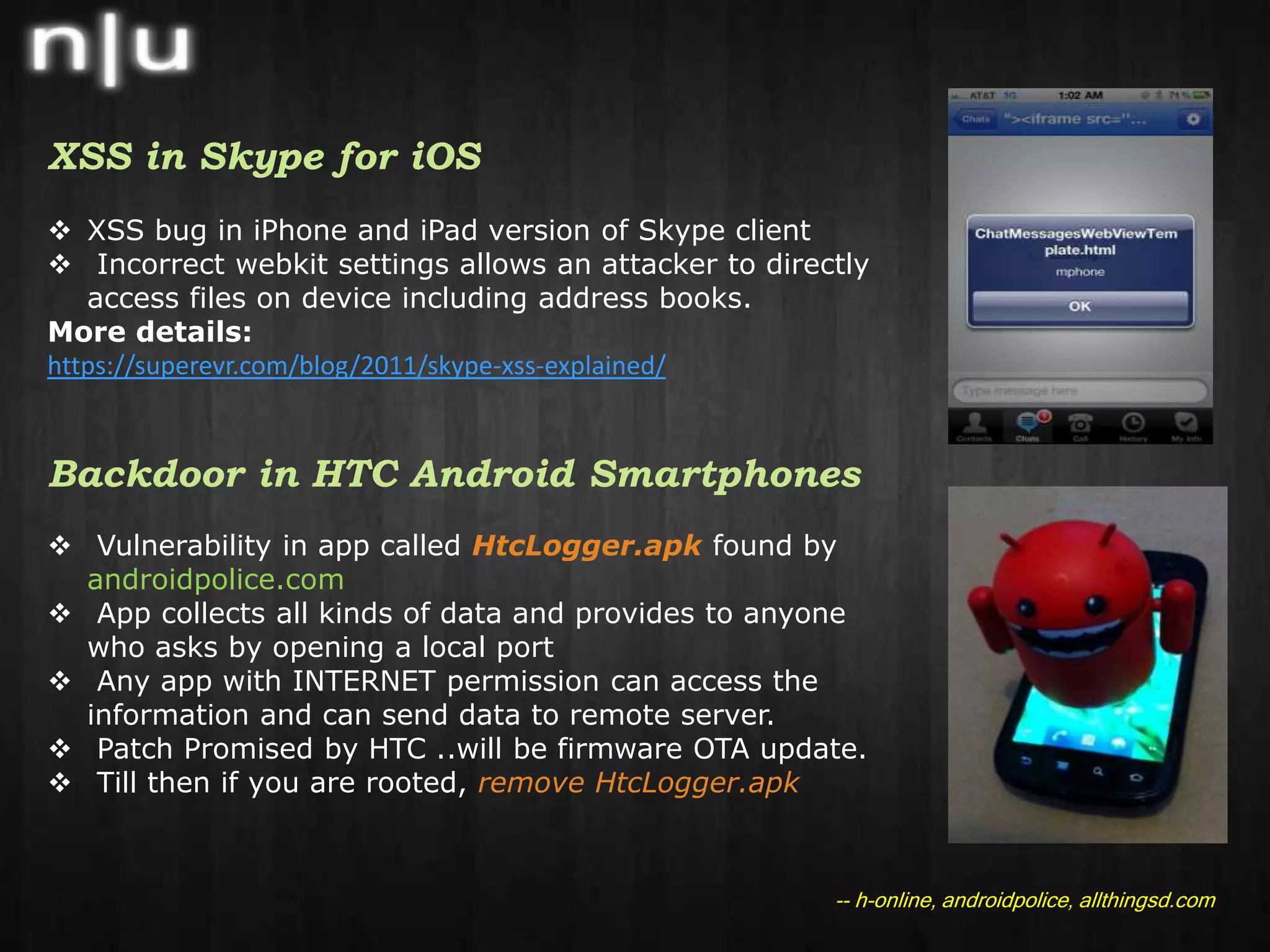
This document summarizes recent cybersecurity news and events in the information security field. It discusses several security conferences that recently occurred including Brucon, Derbycon, and HITB as well as the arrest of members of the hacker group Lulzsec. It also covers recent vulnerabilities including a chosen plaintext attack against AES in SSL/TLS, the compromise of the mysql.com website, and an Apache reverse proxy bypass issue. Lastly, it mentions new security tools releases, recent malware activity including new Android threats, and recommended security reading materials.