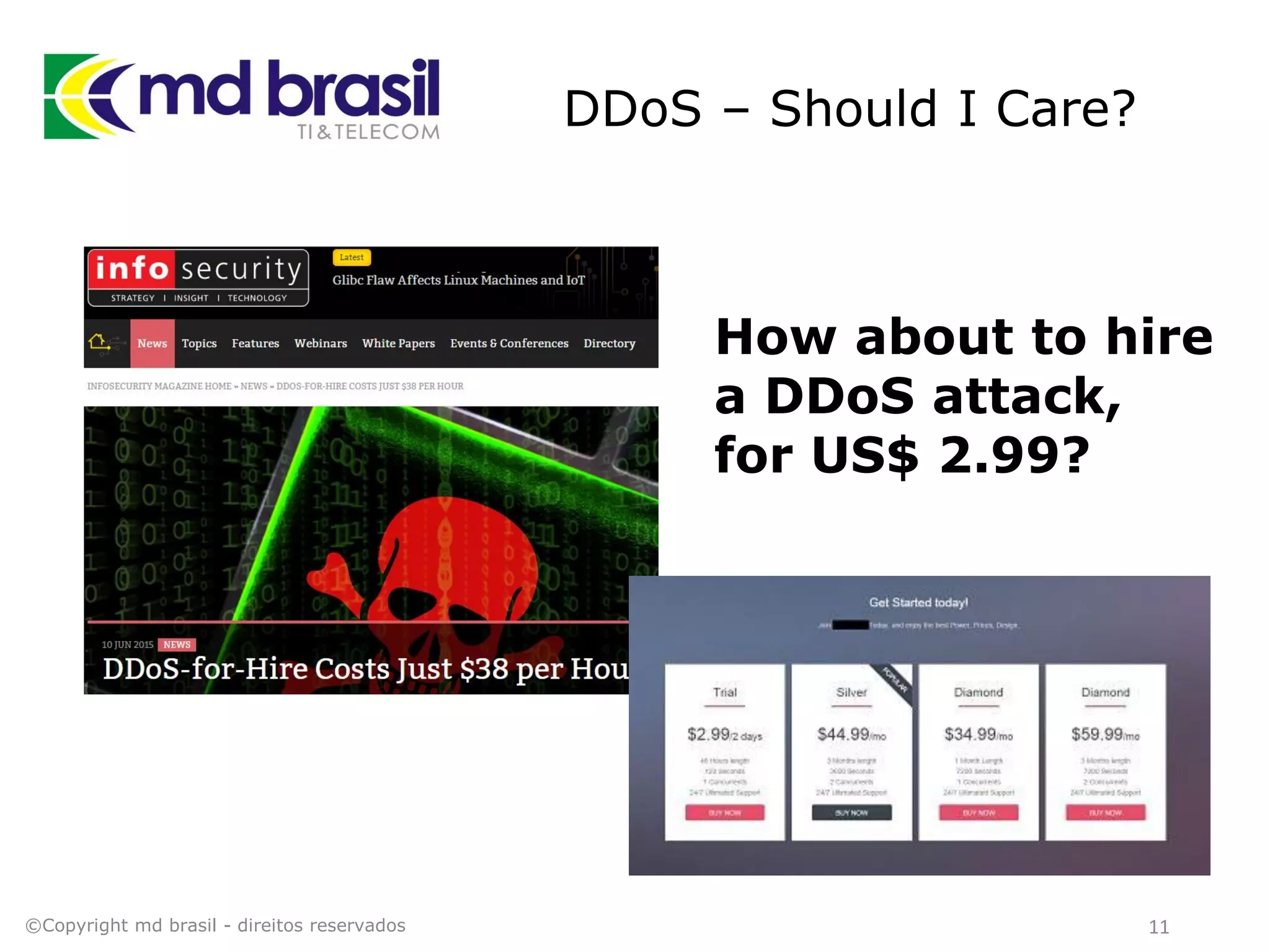
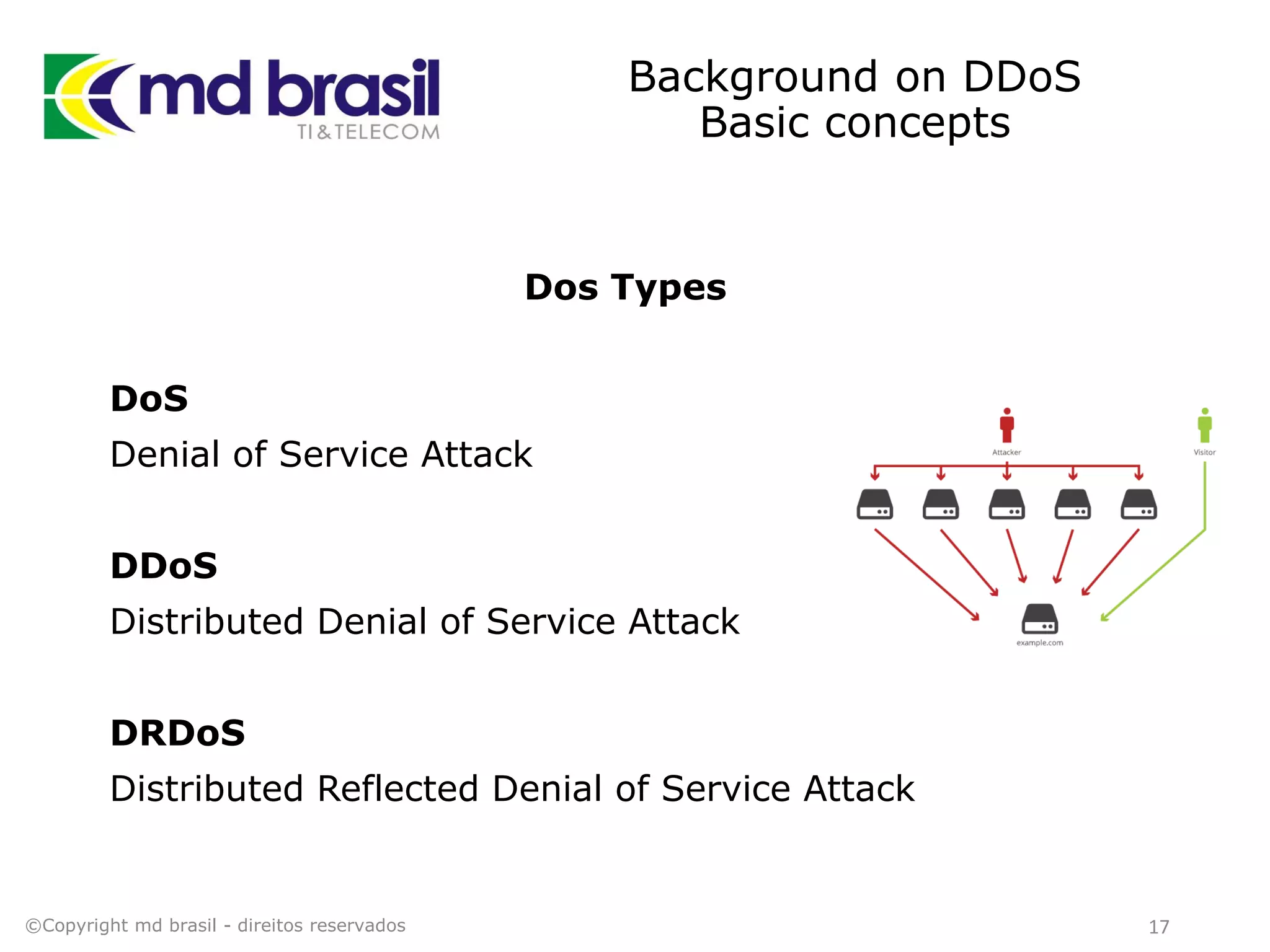
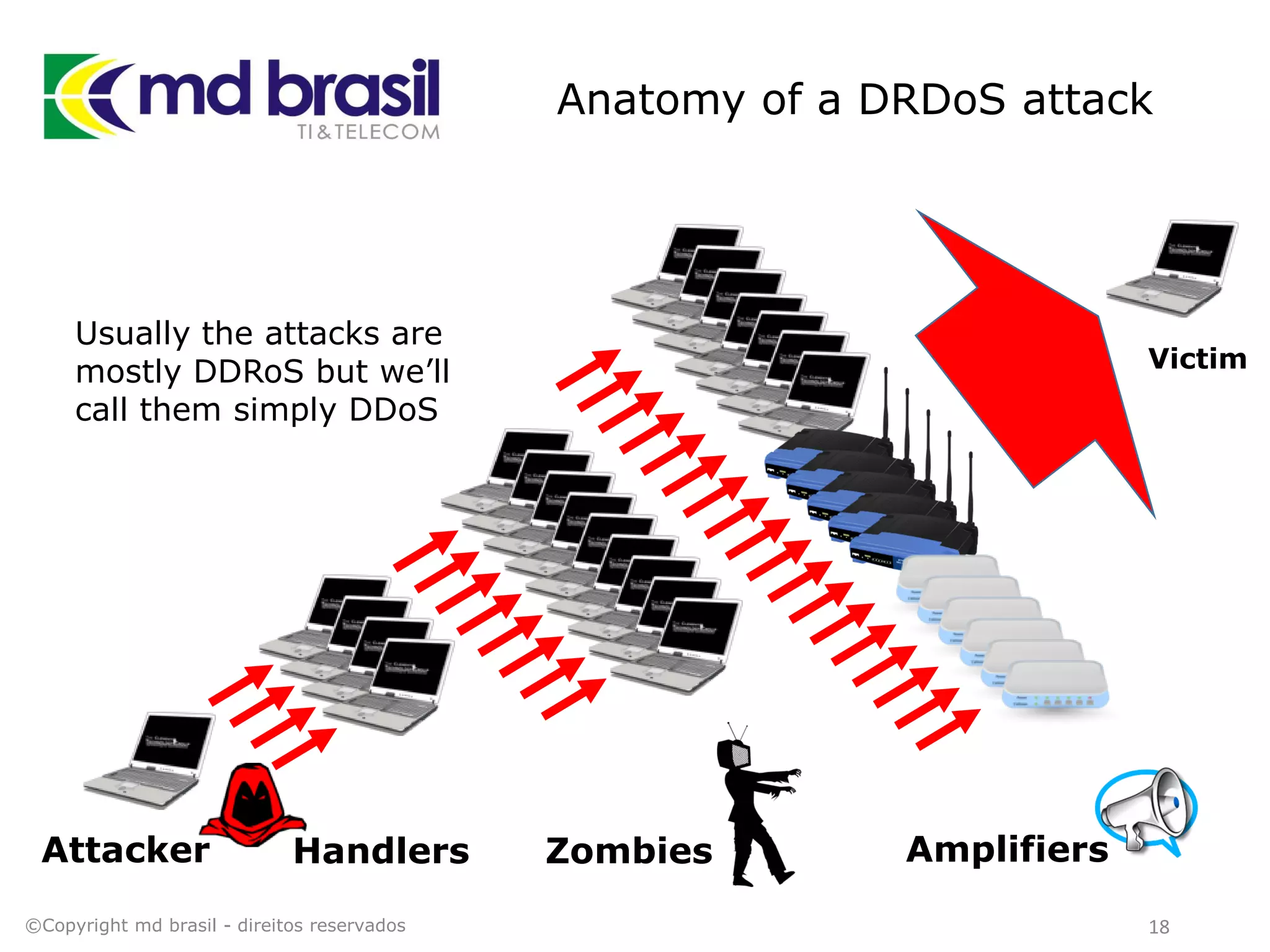
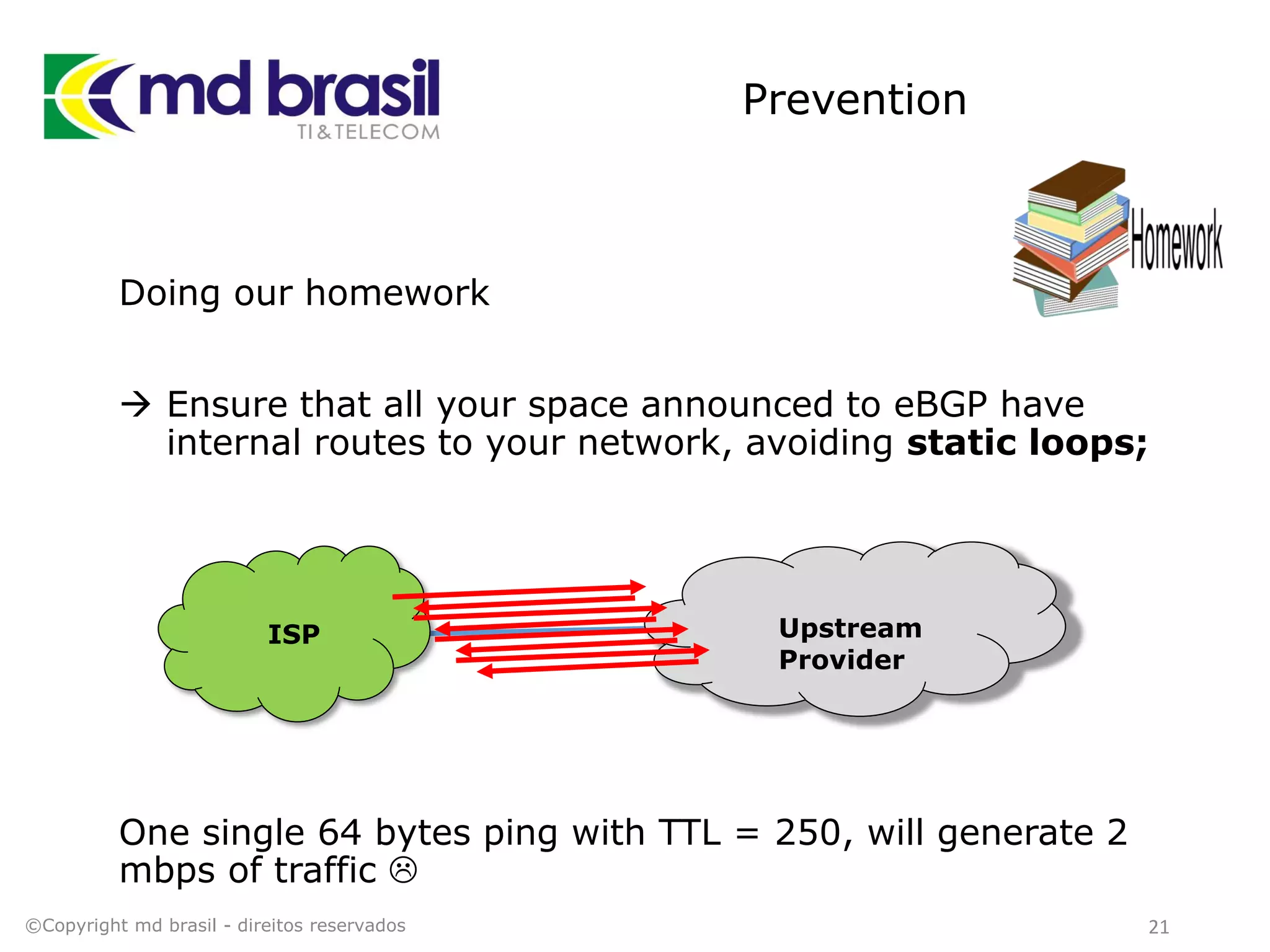
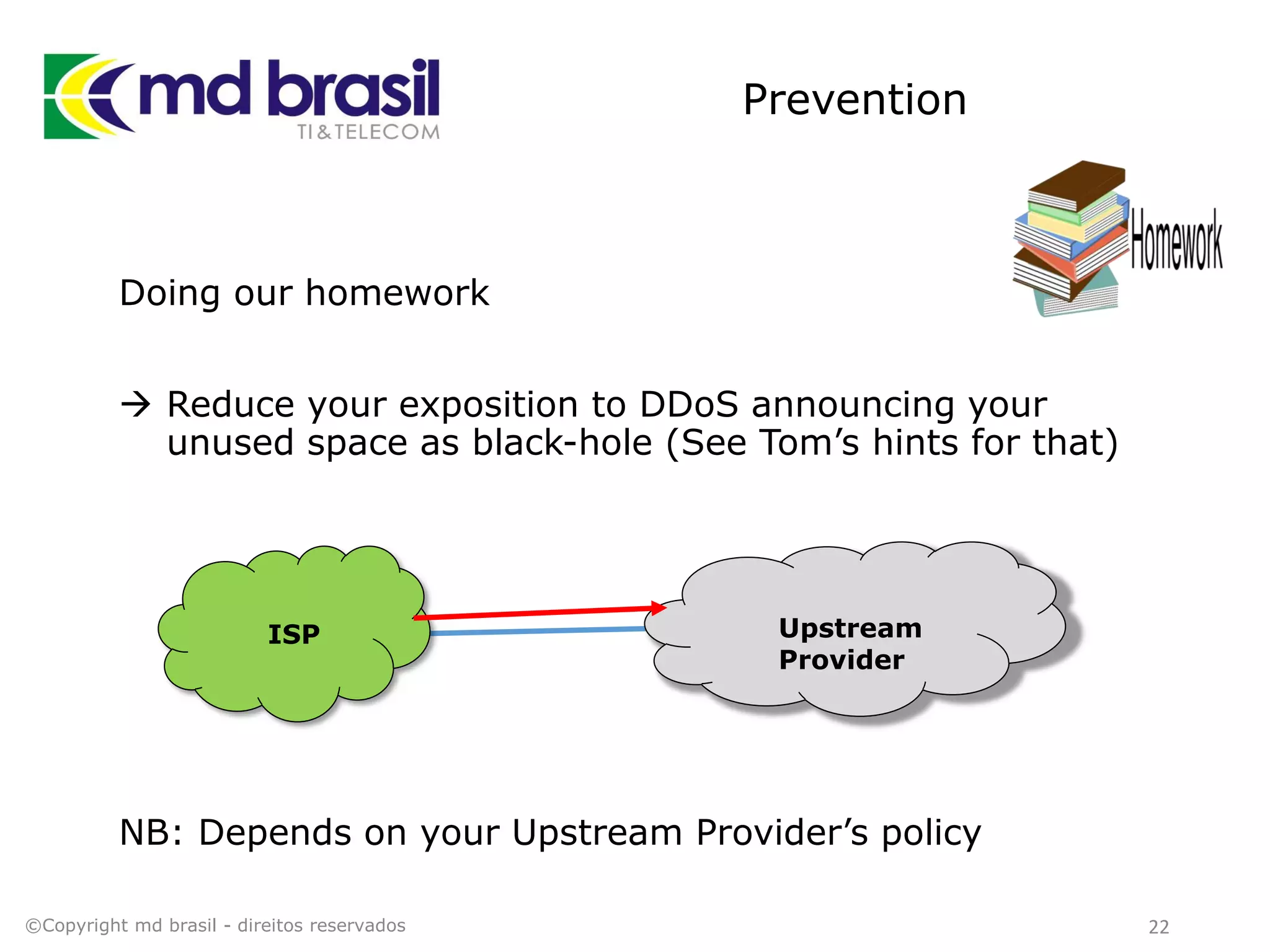
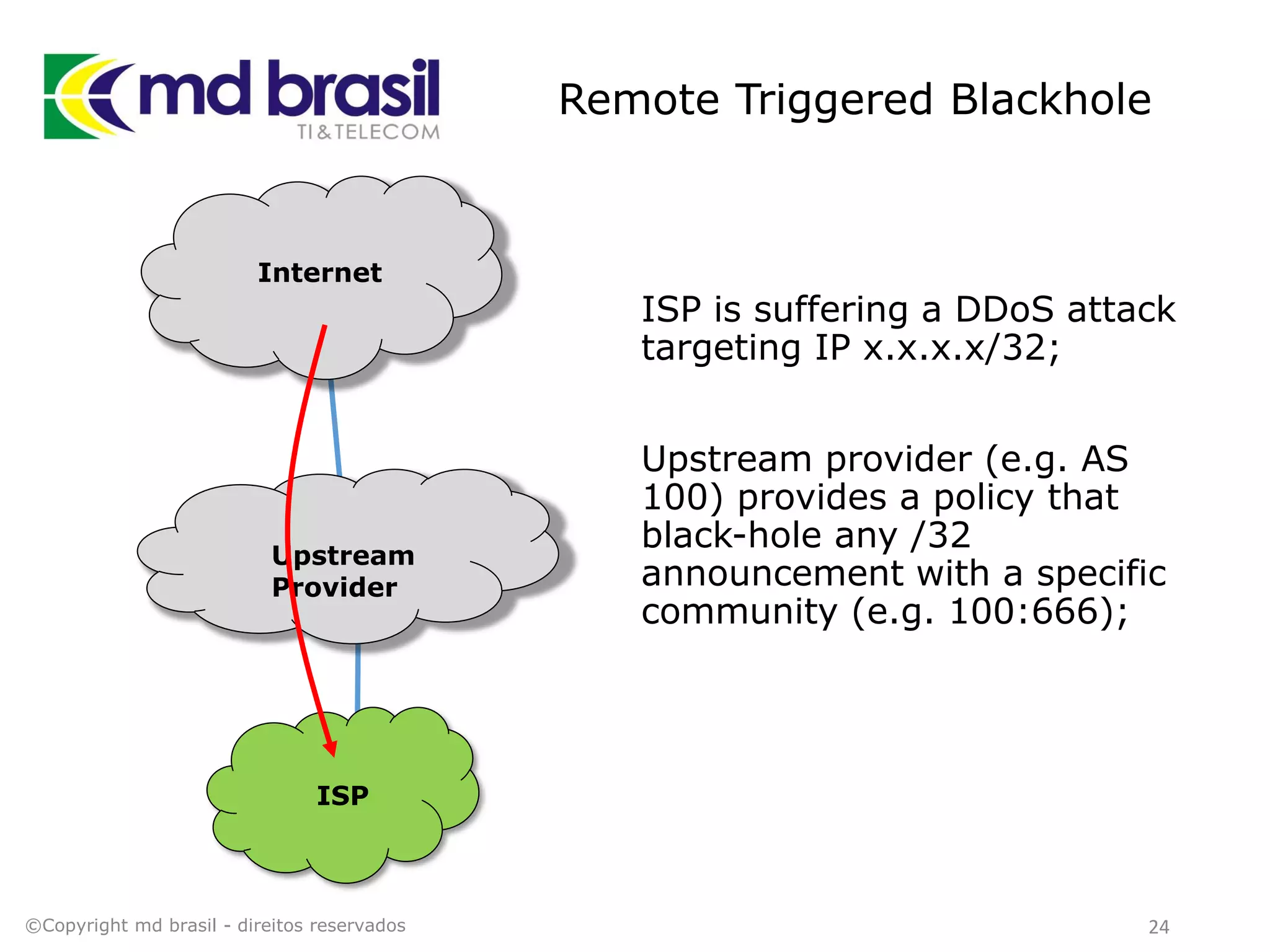
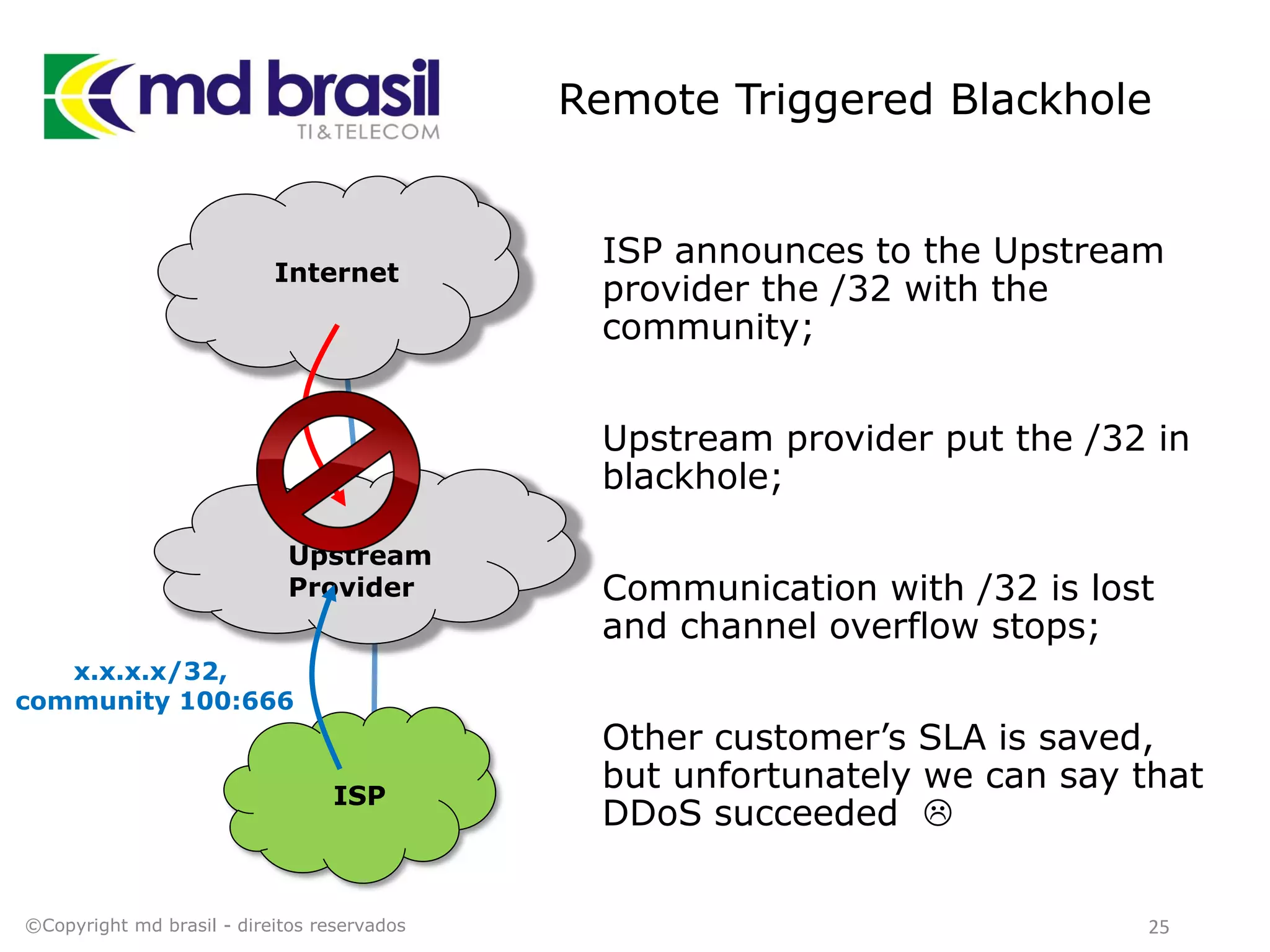
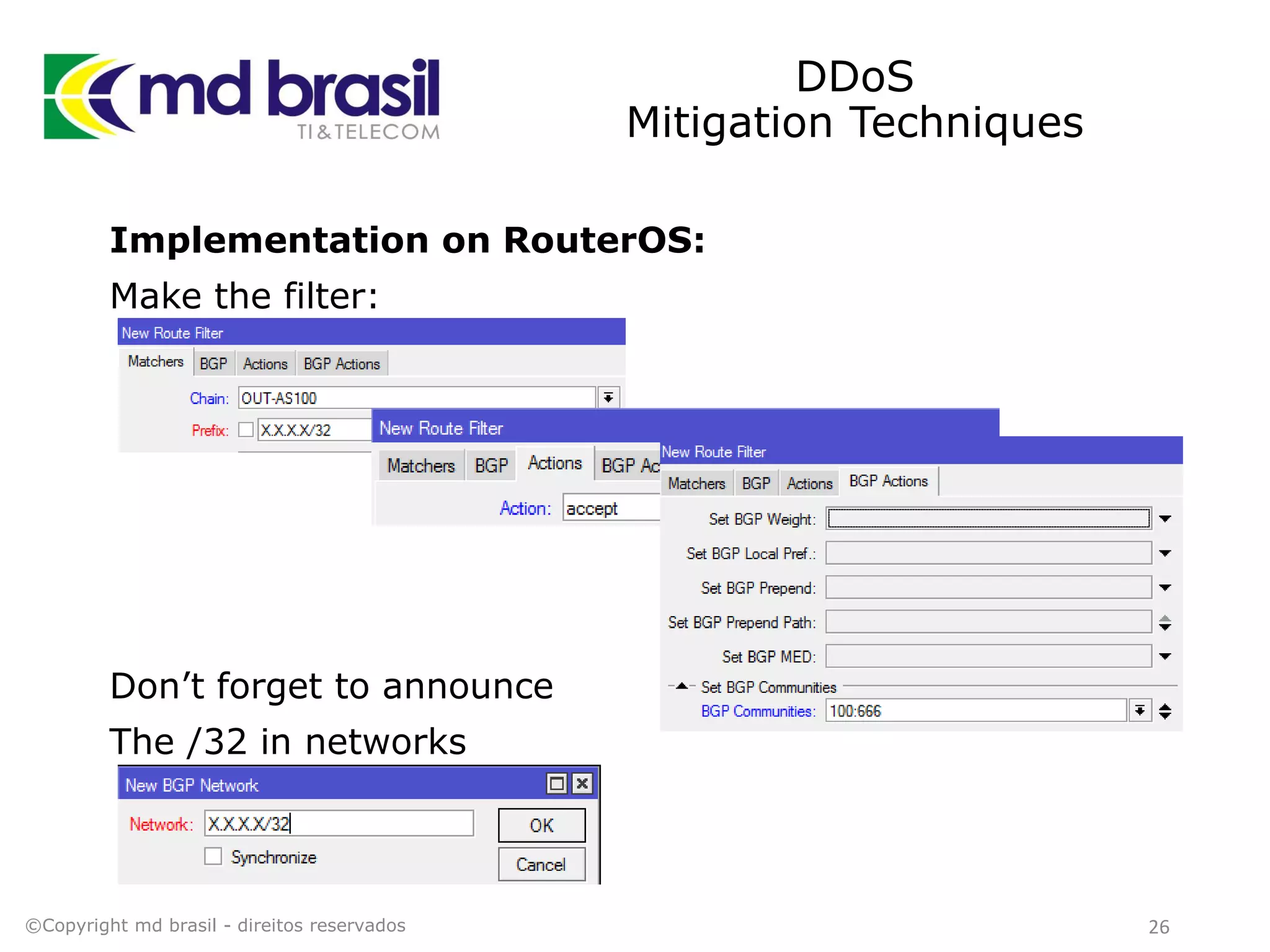
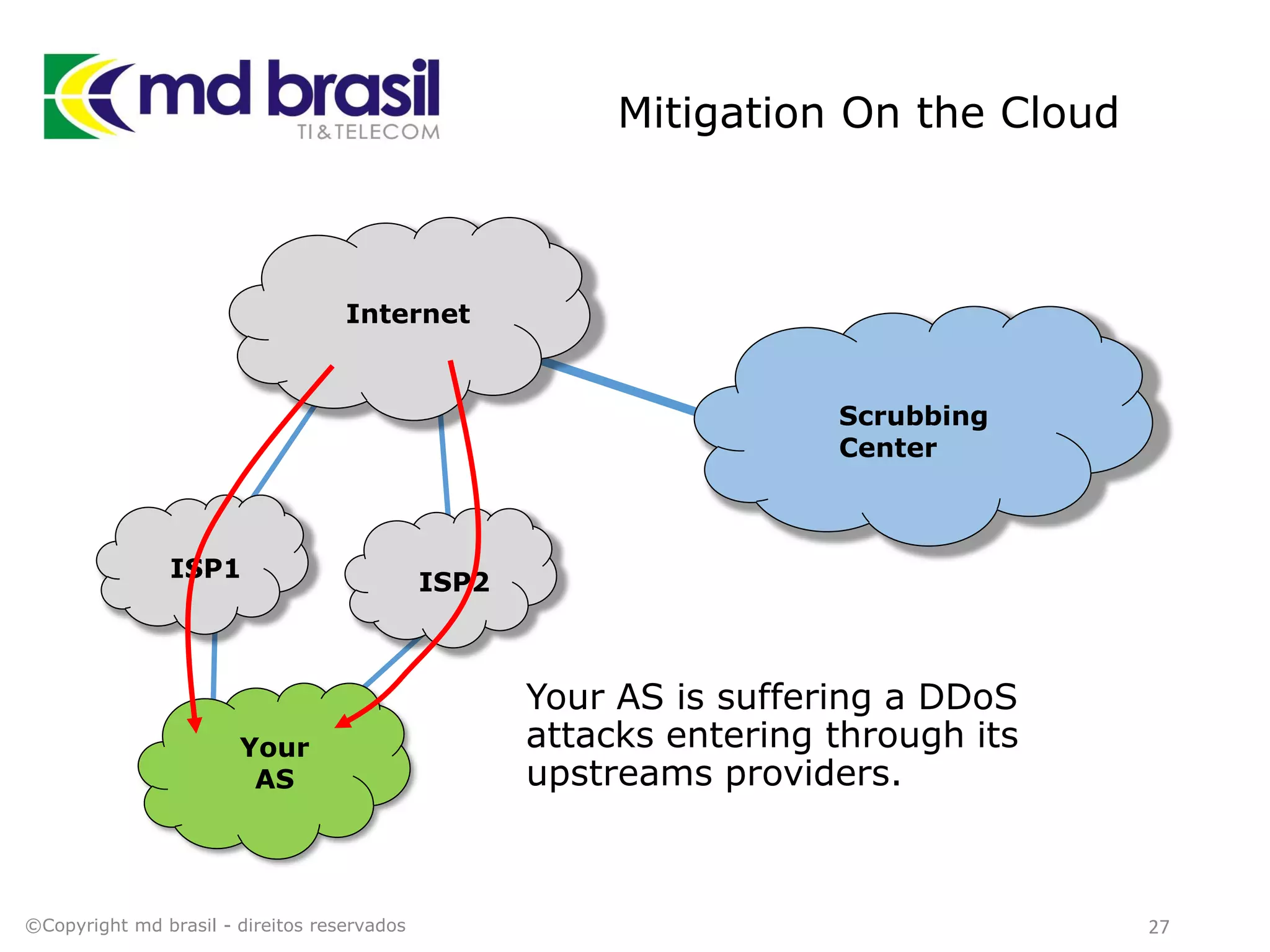
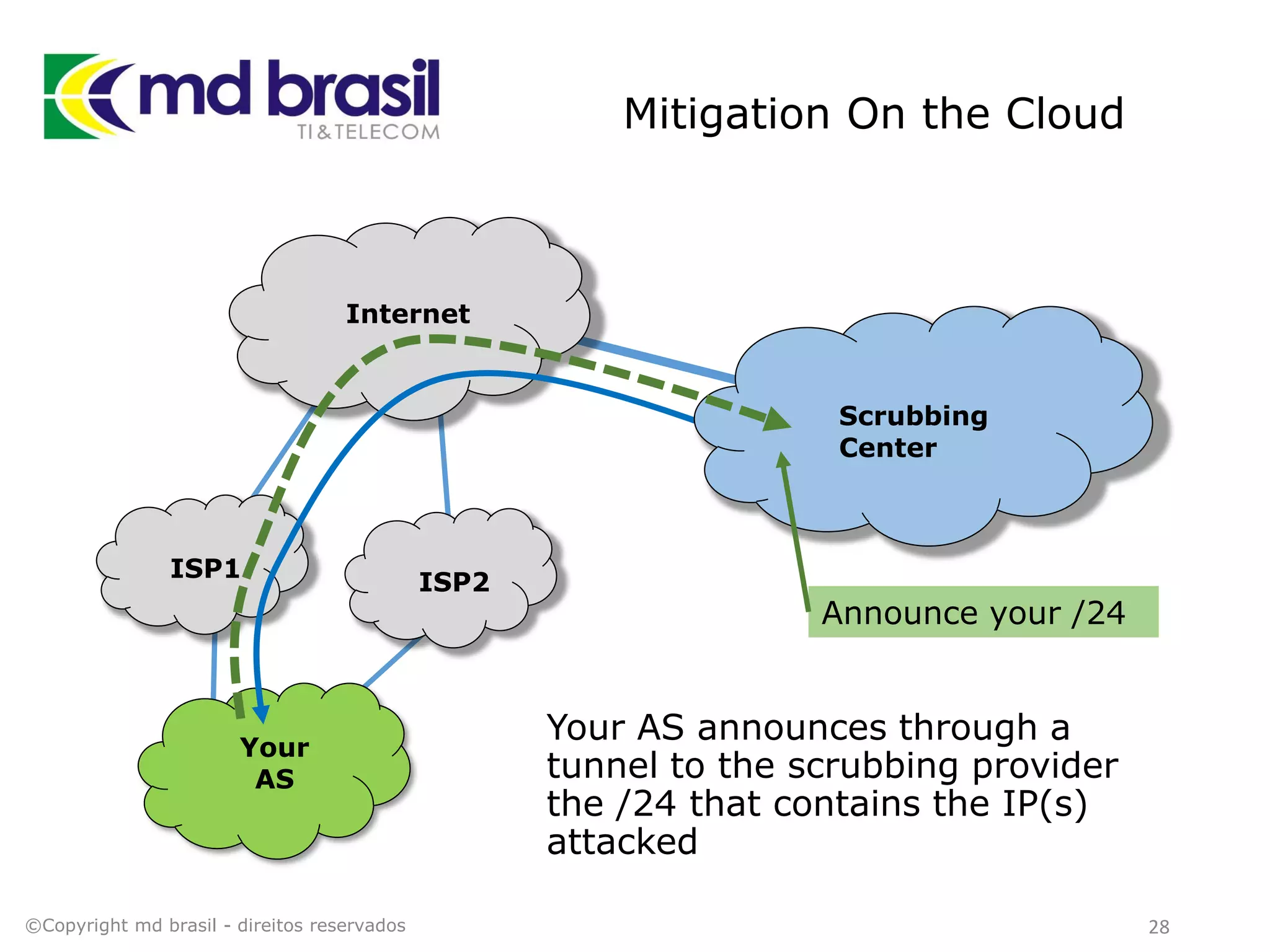
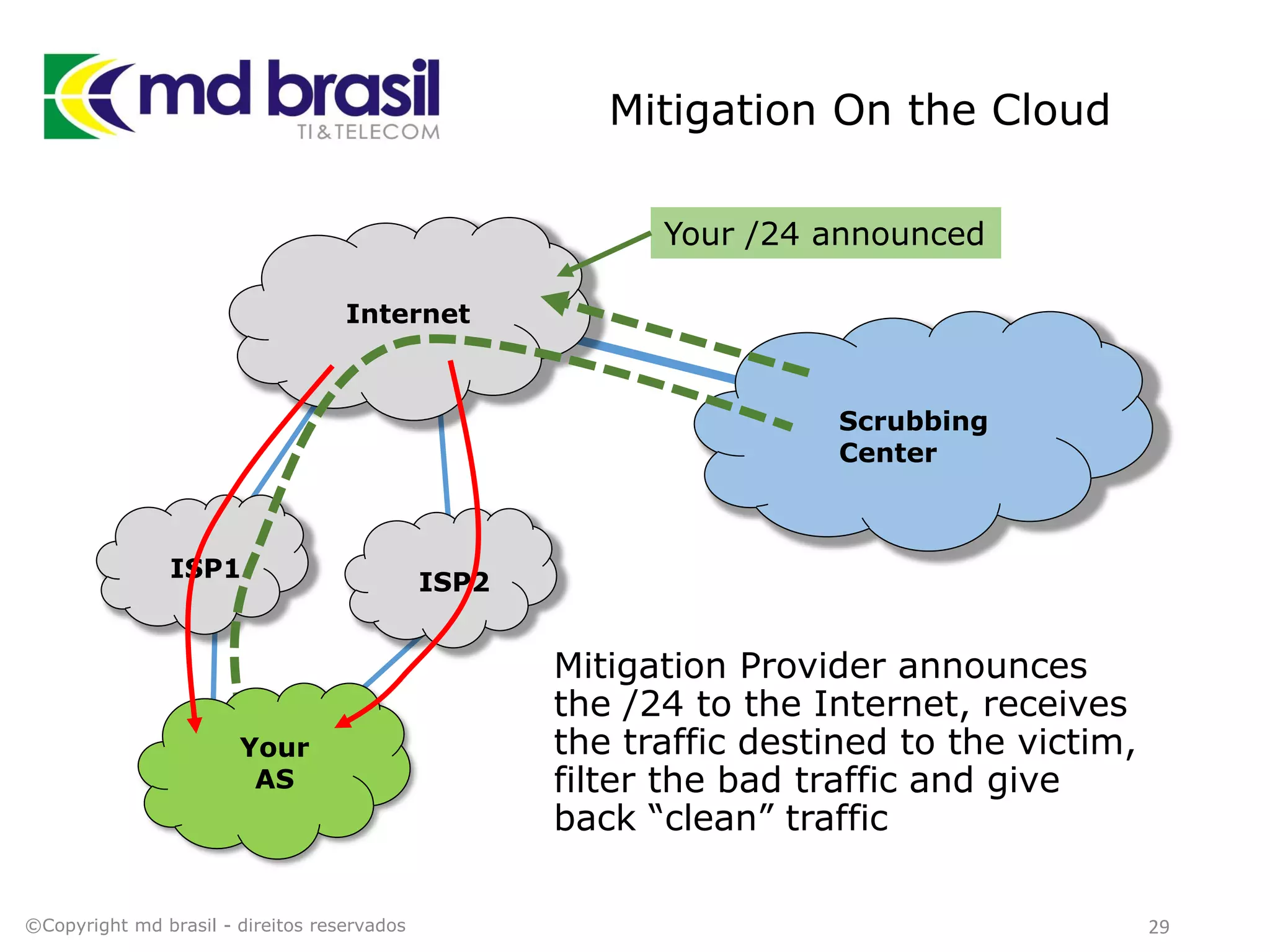
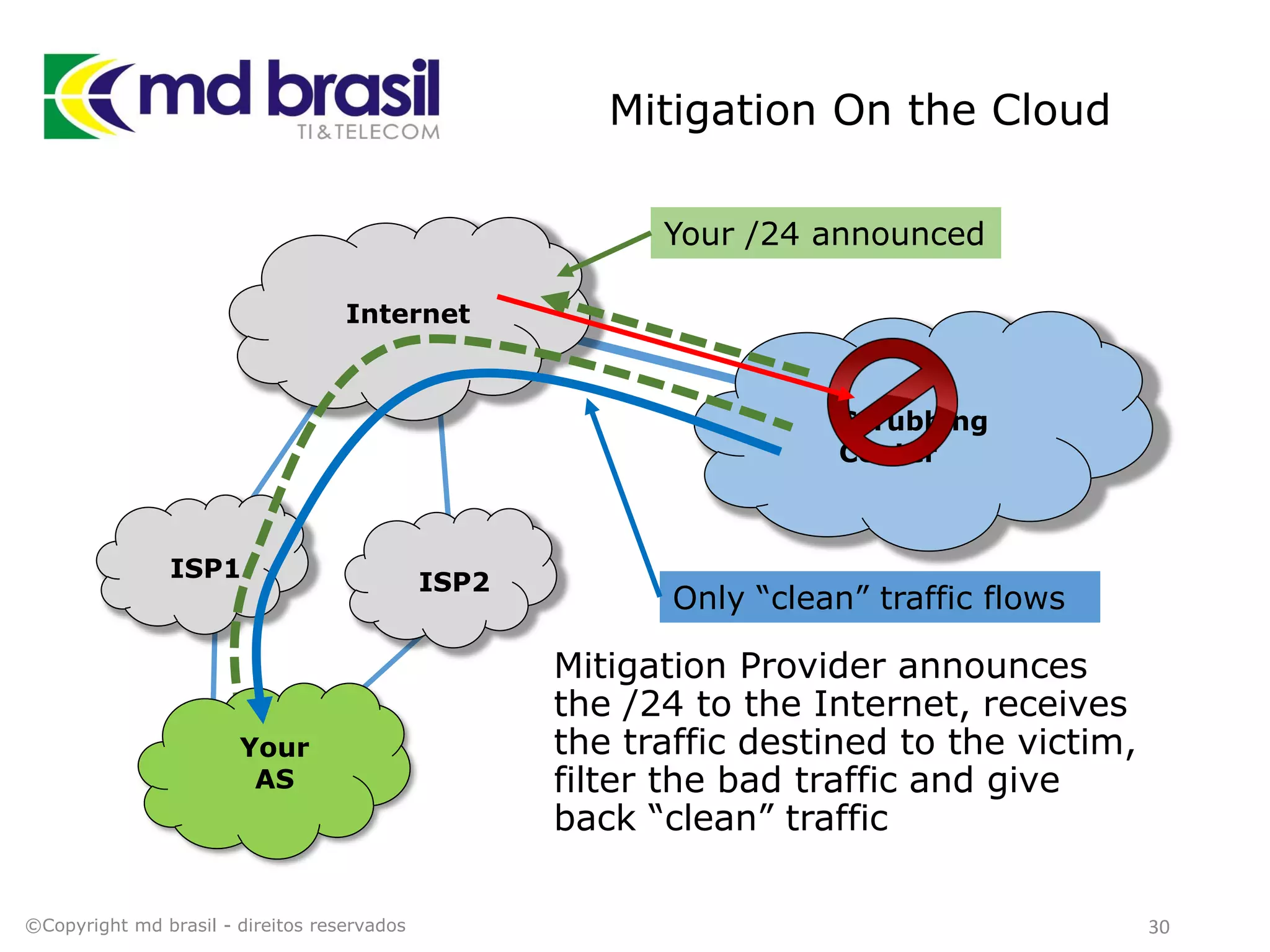
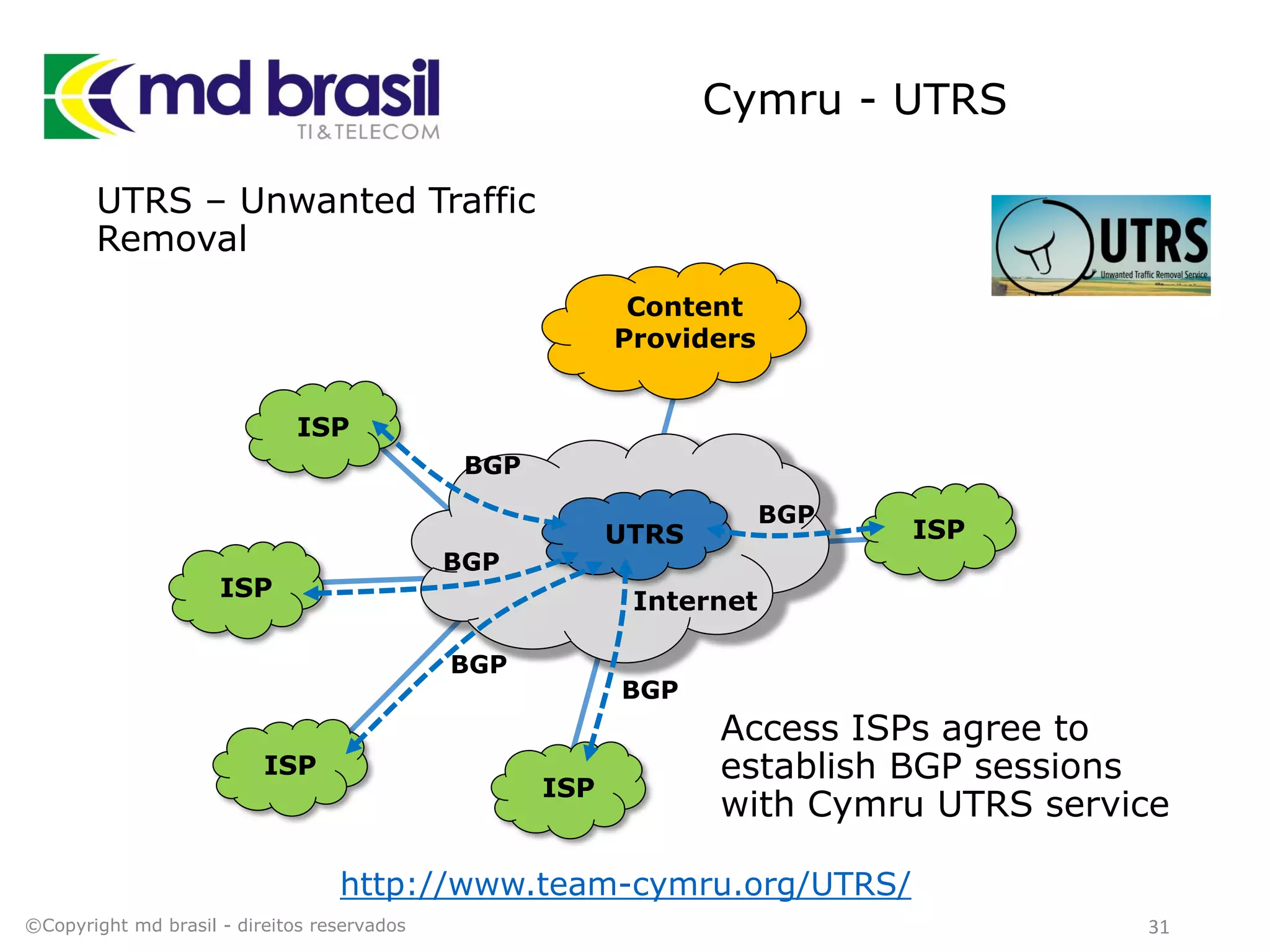
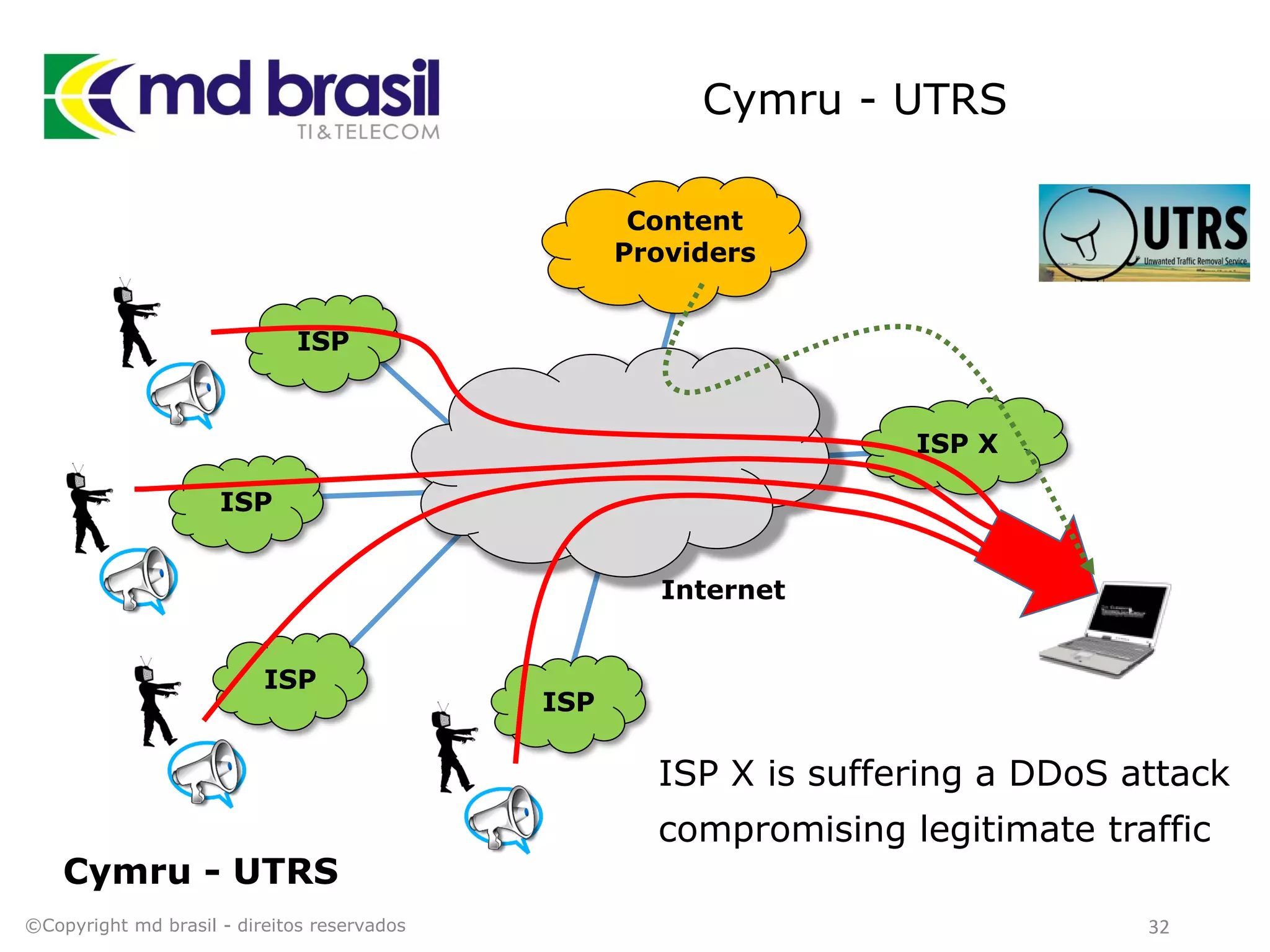
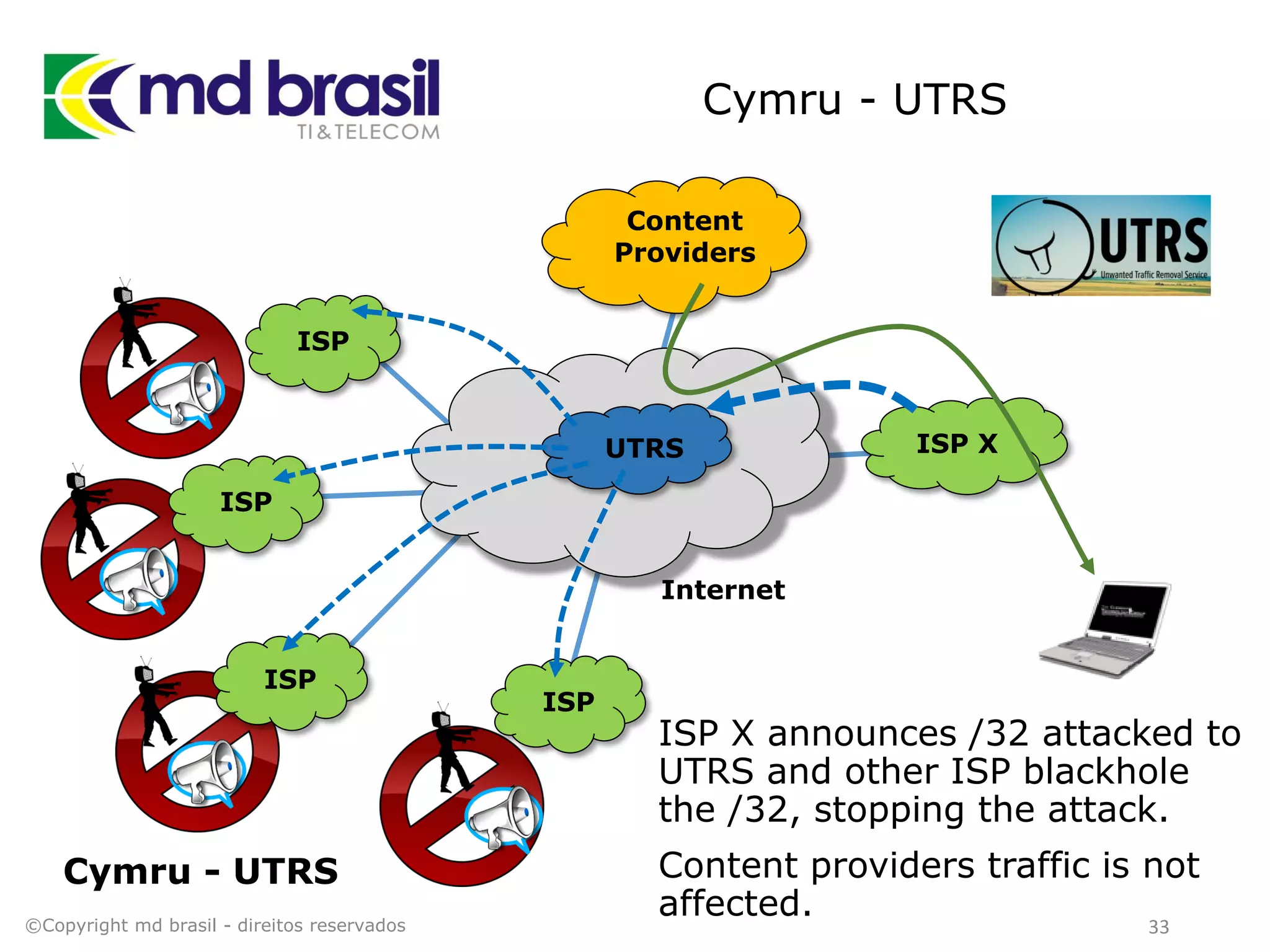
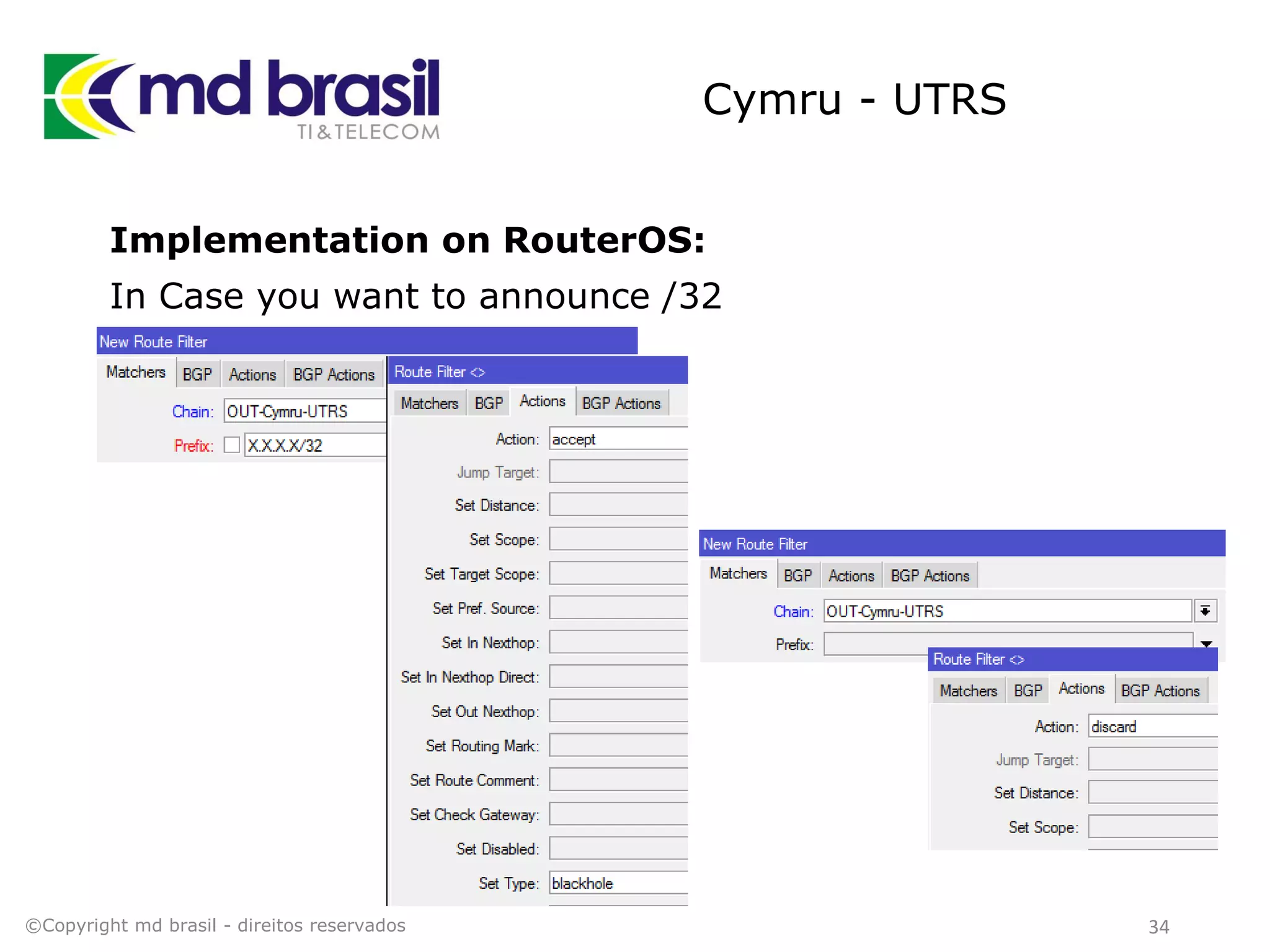
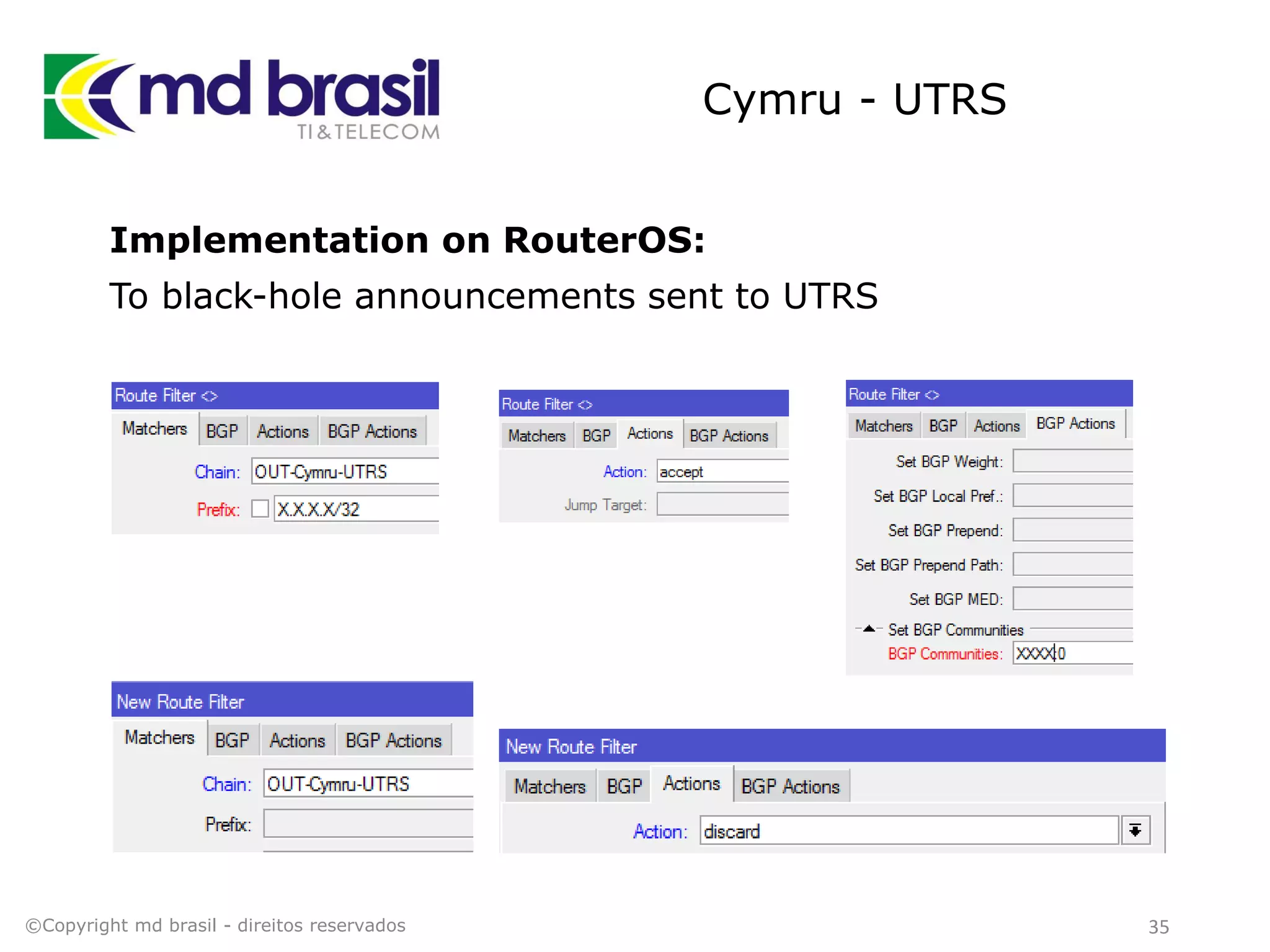
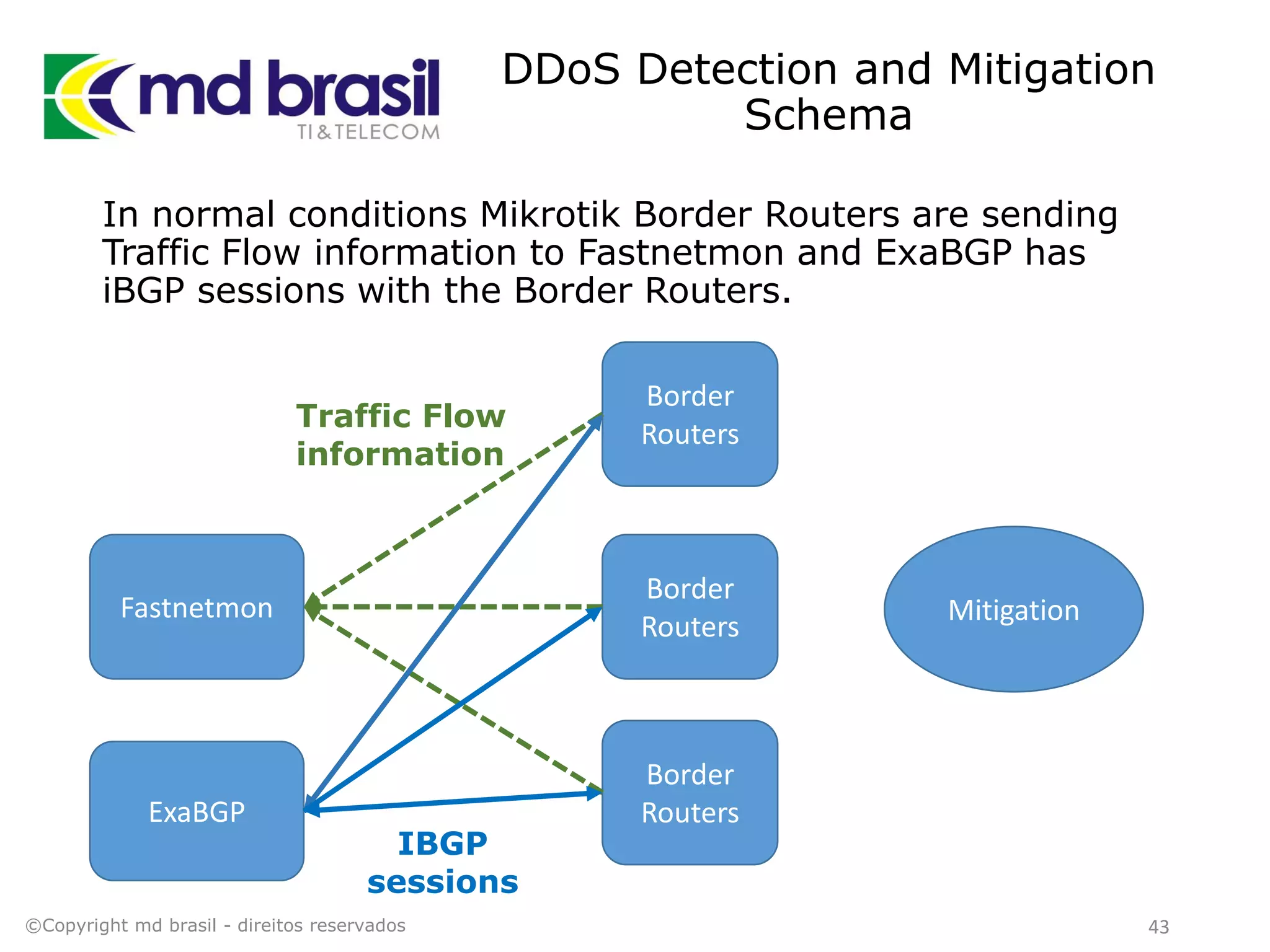
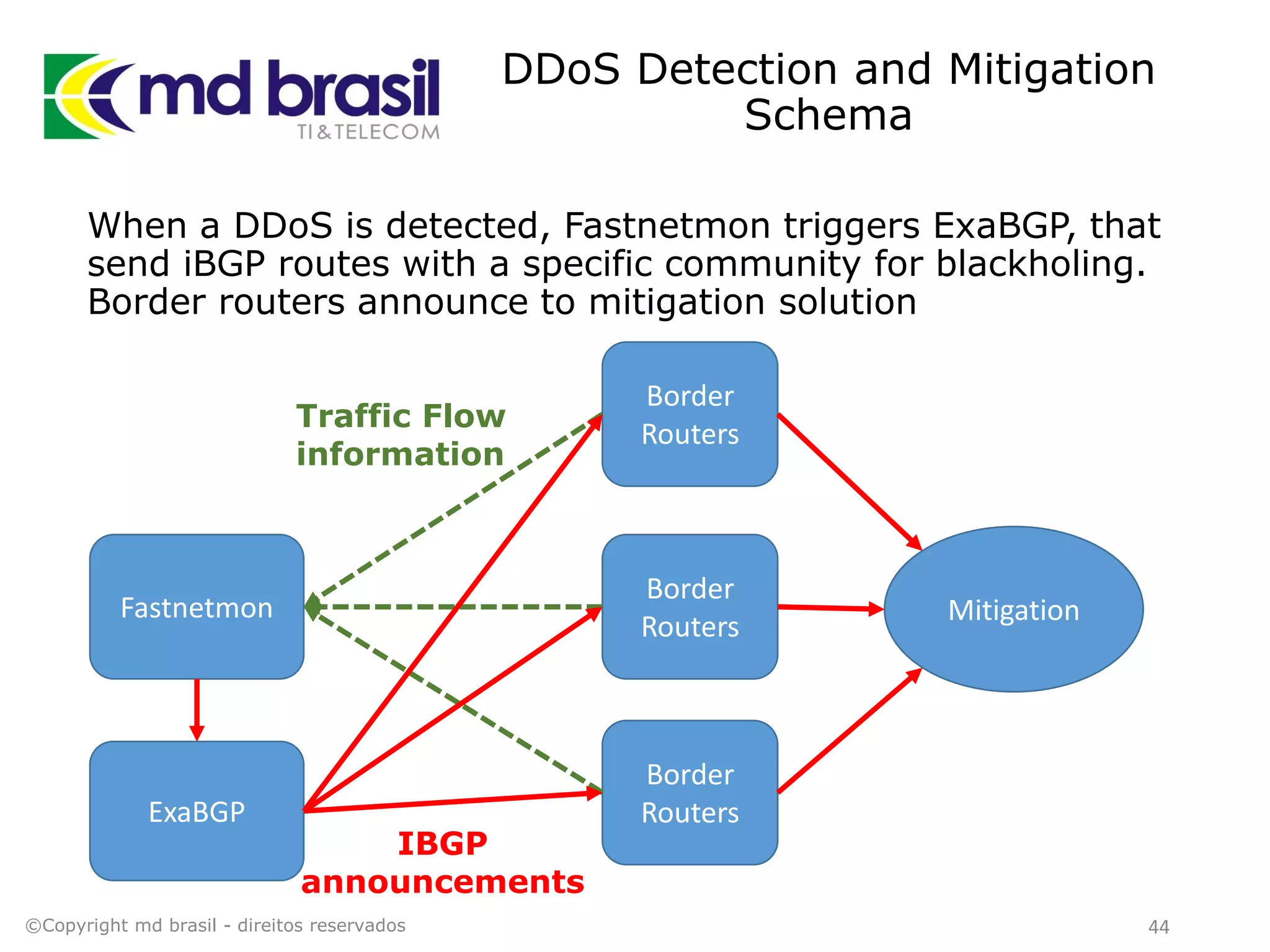
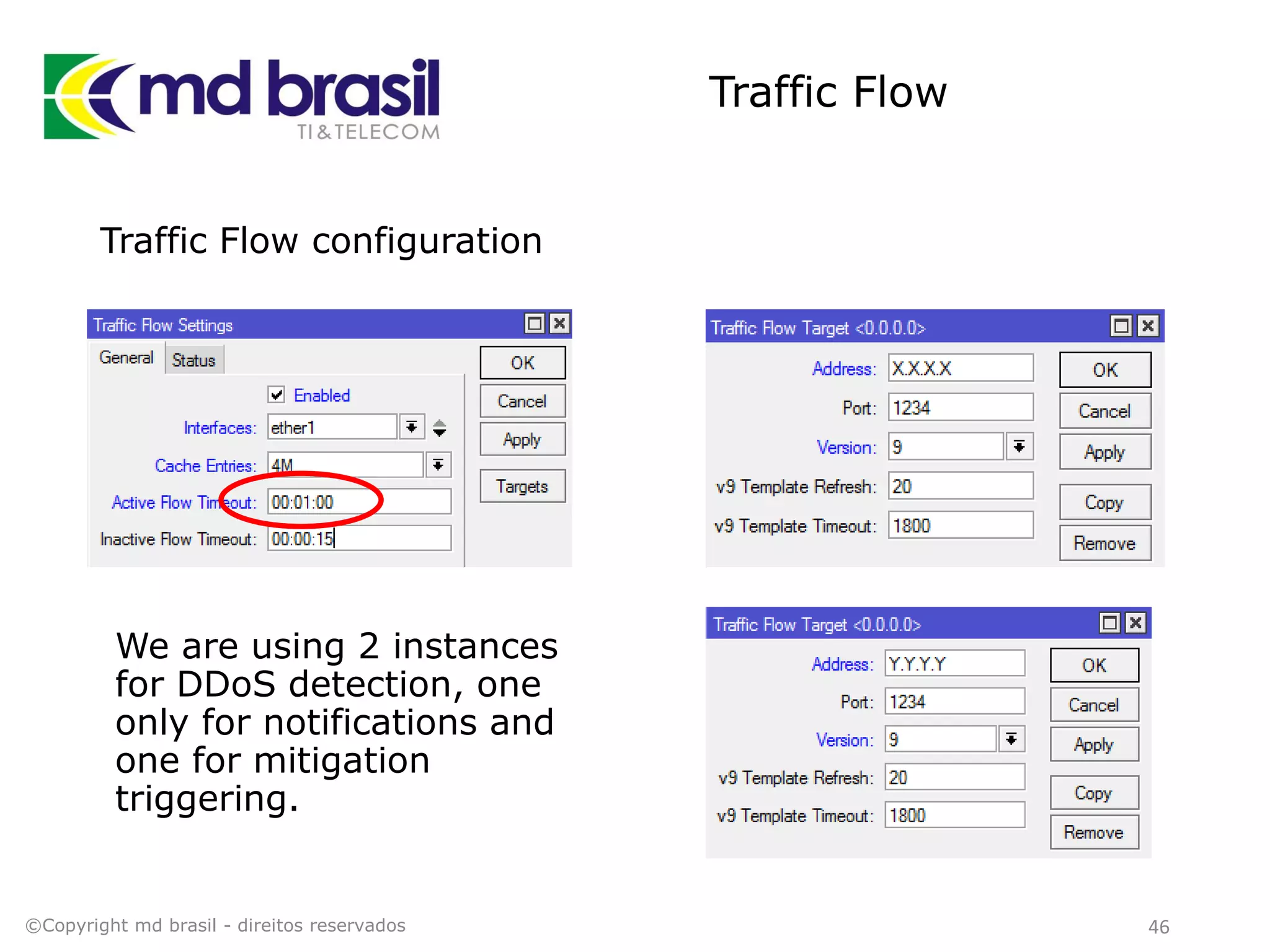
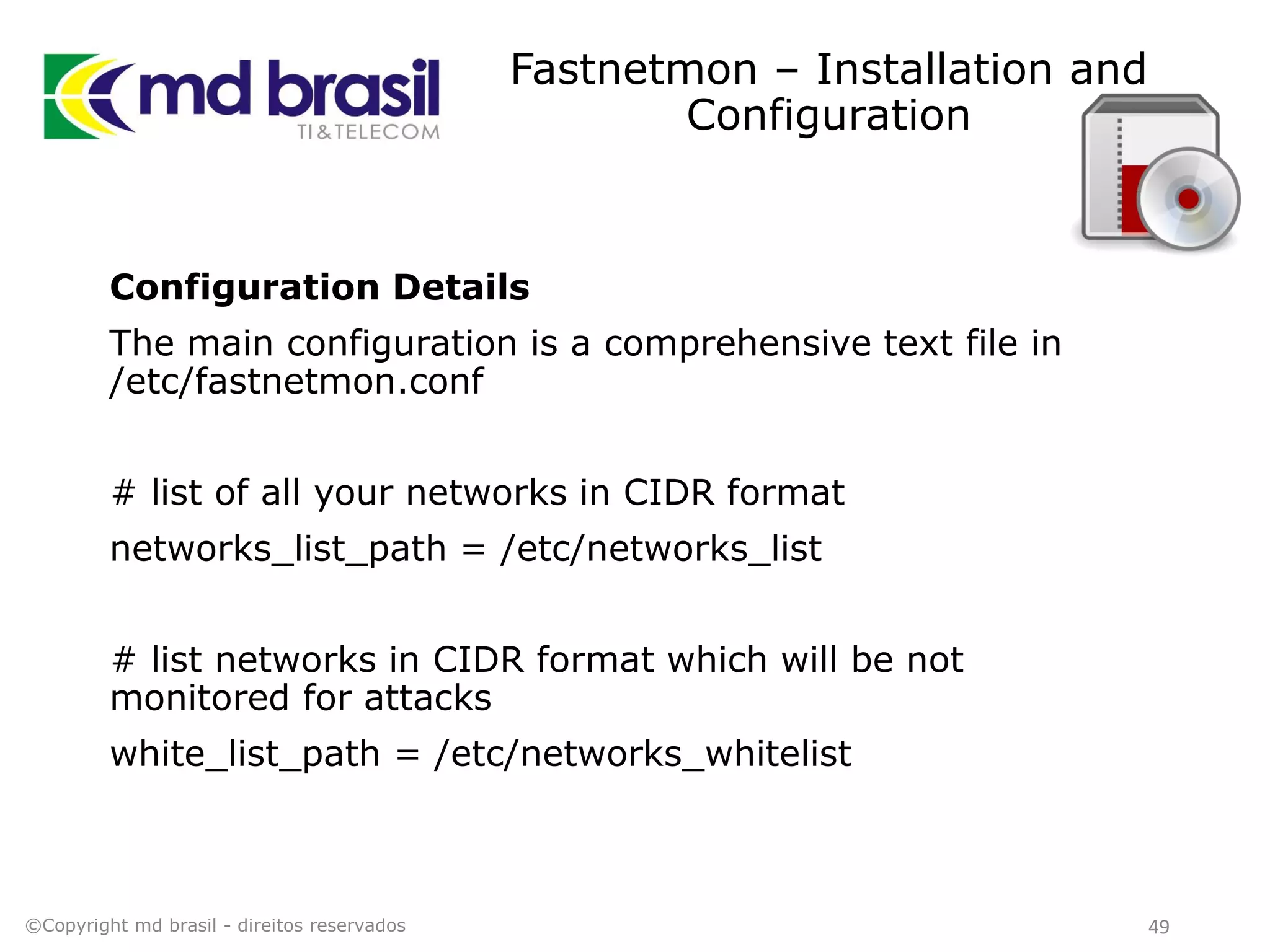
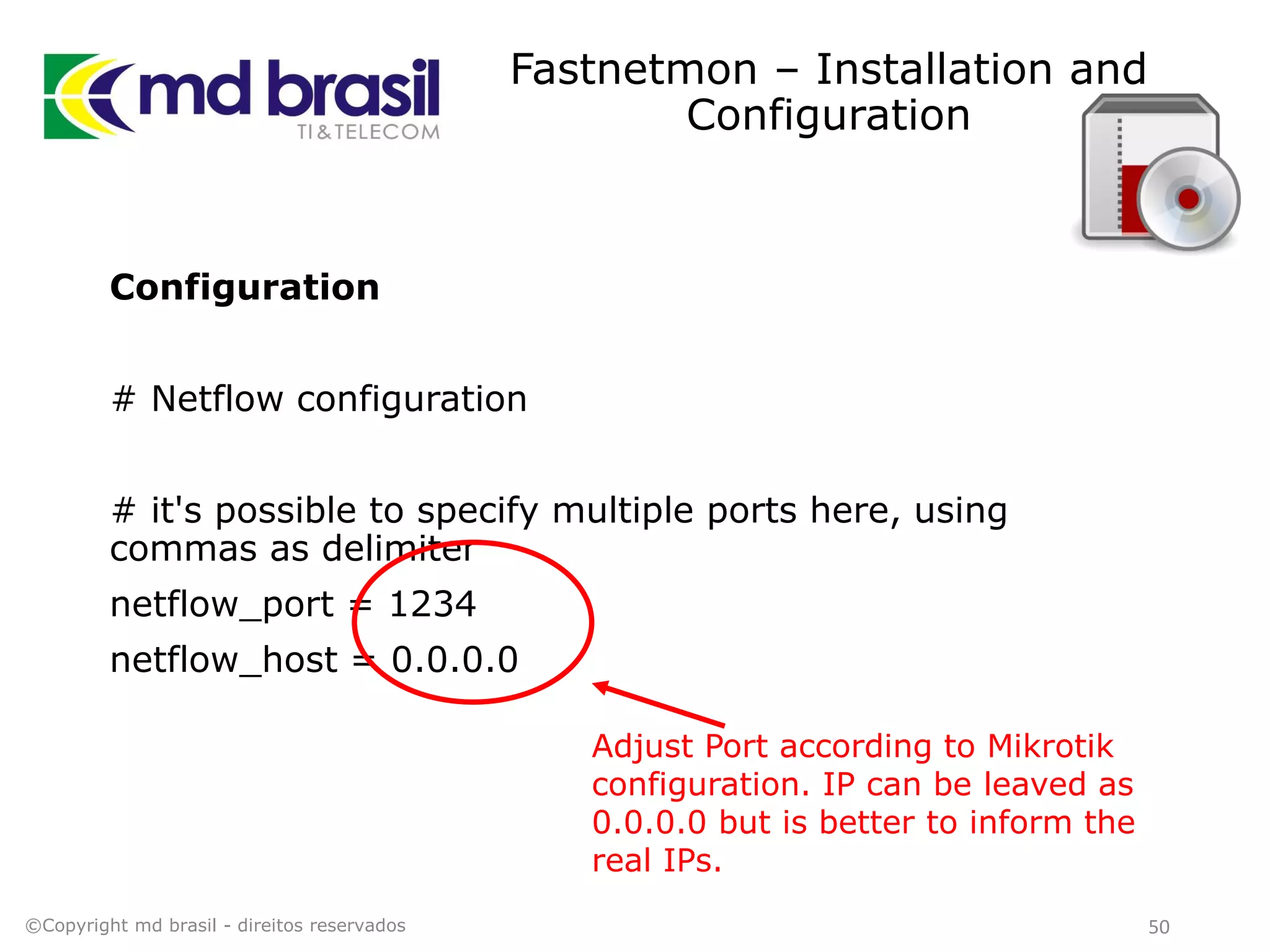
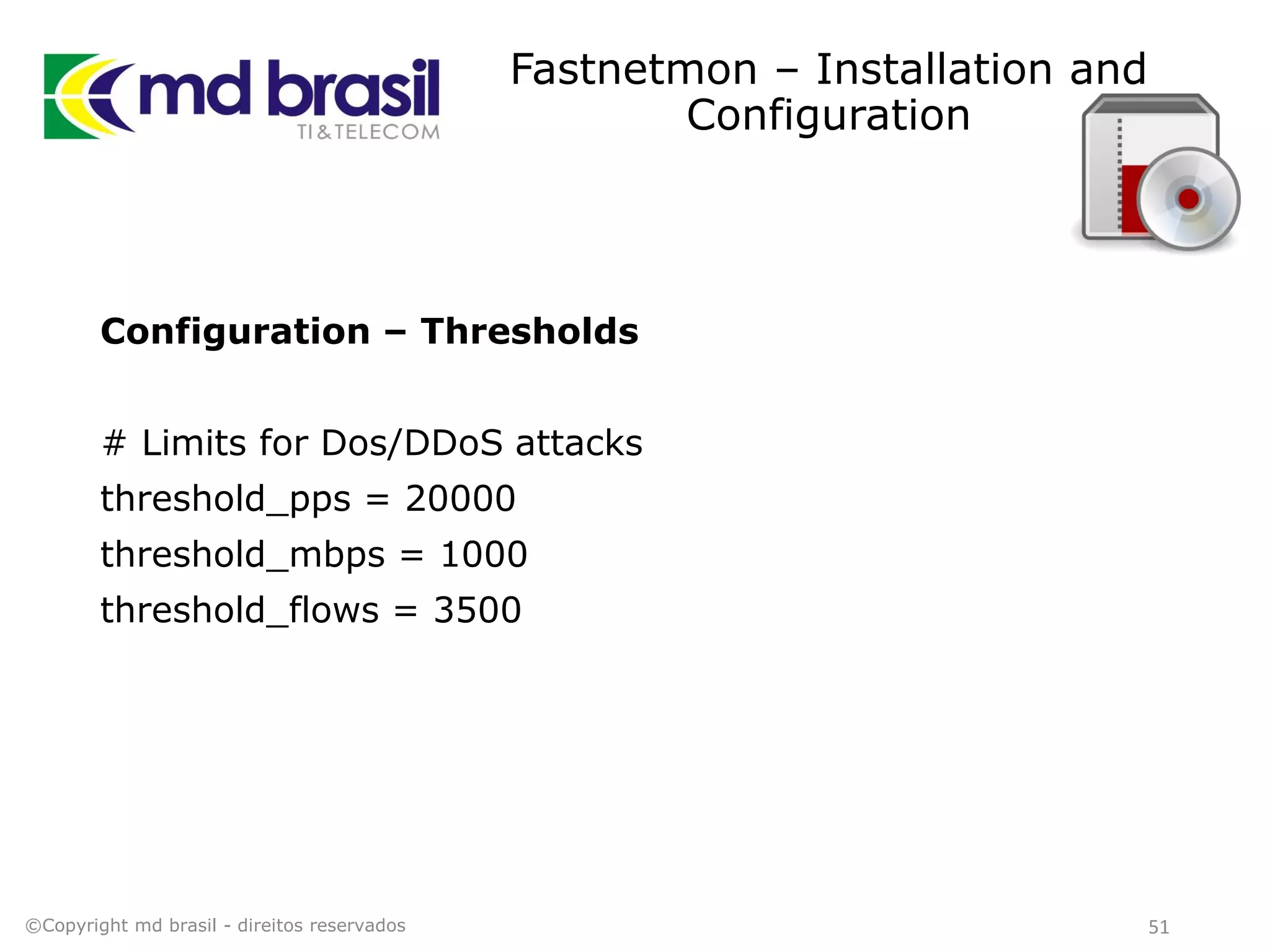
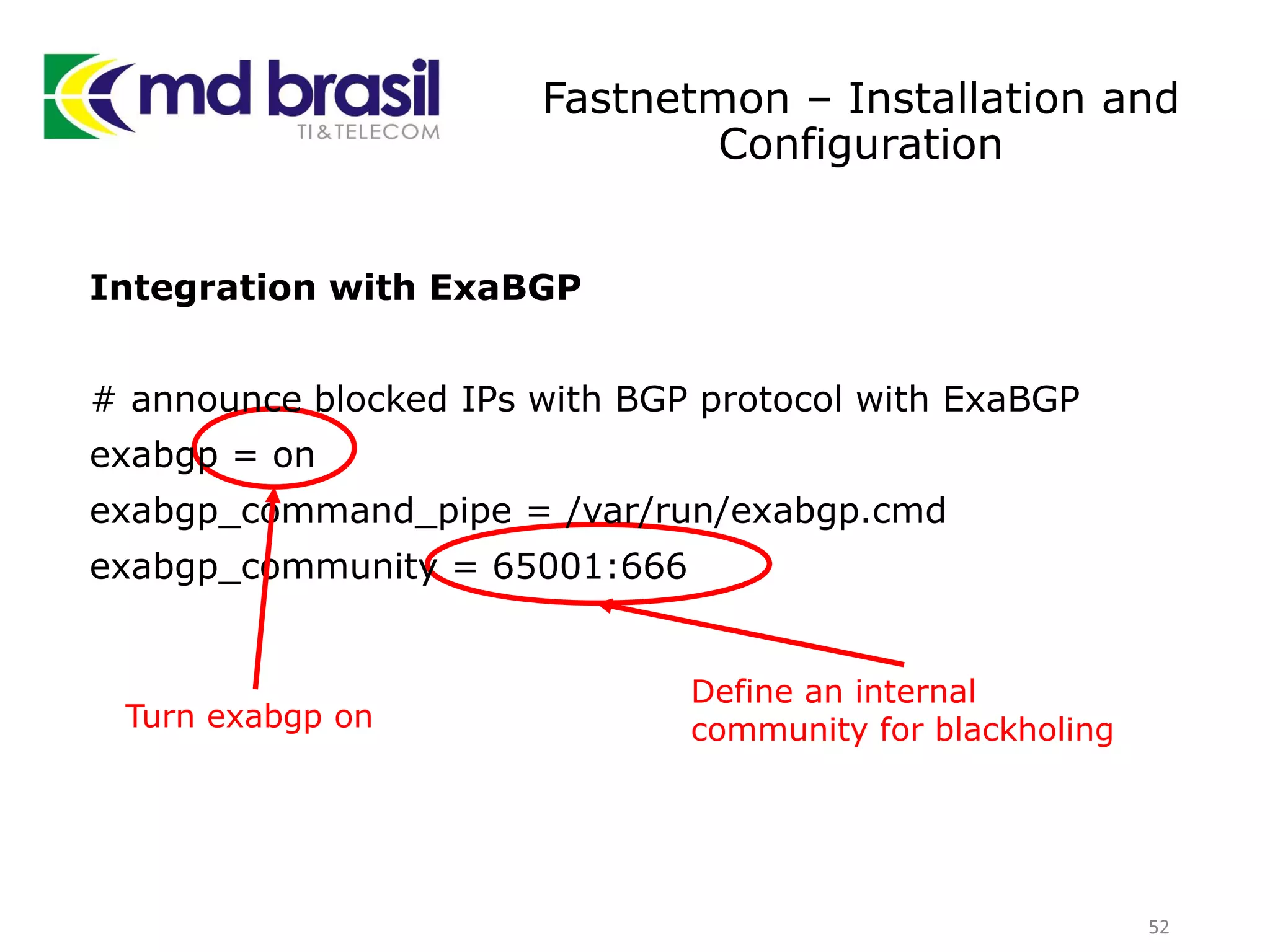
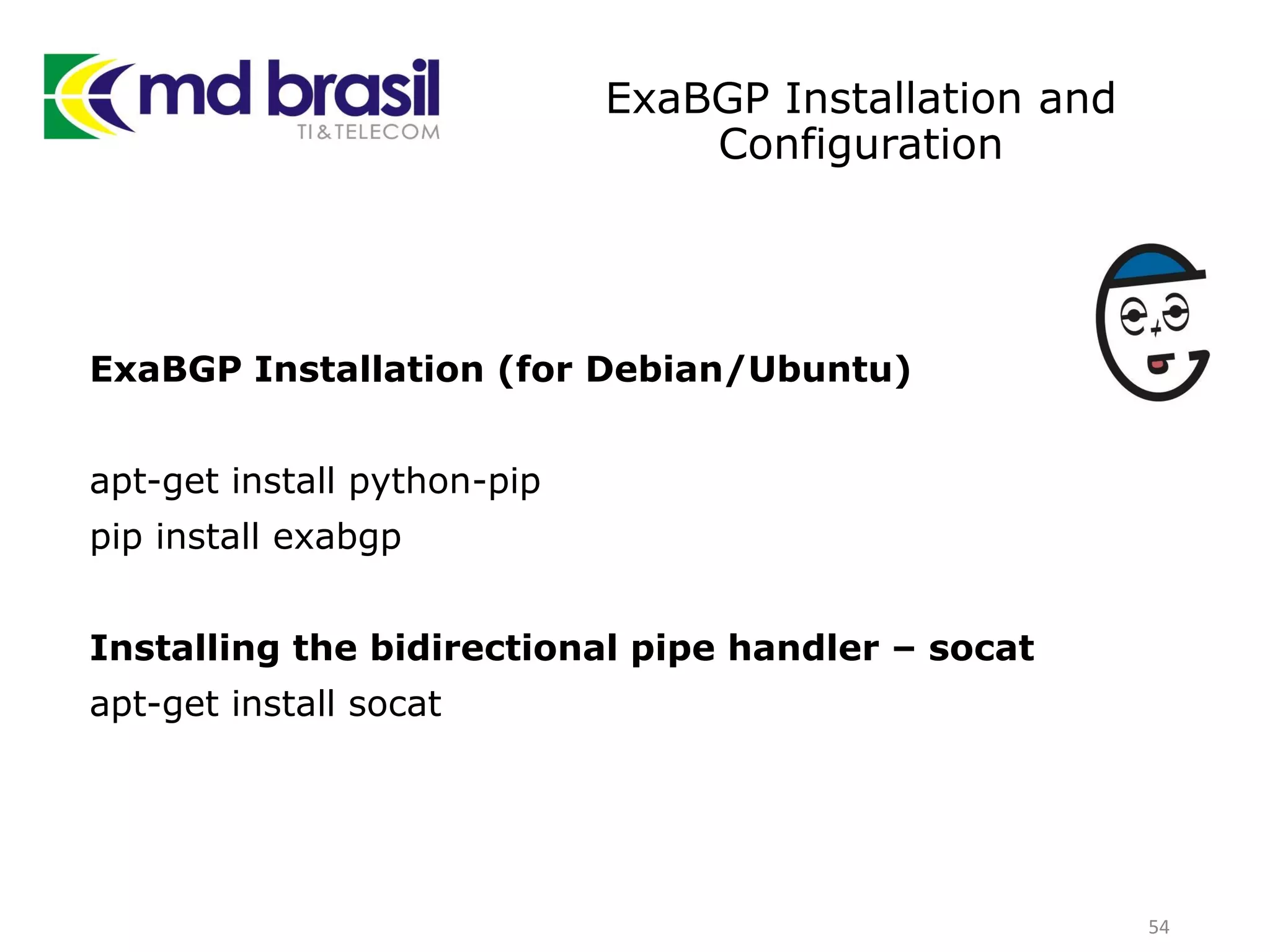
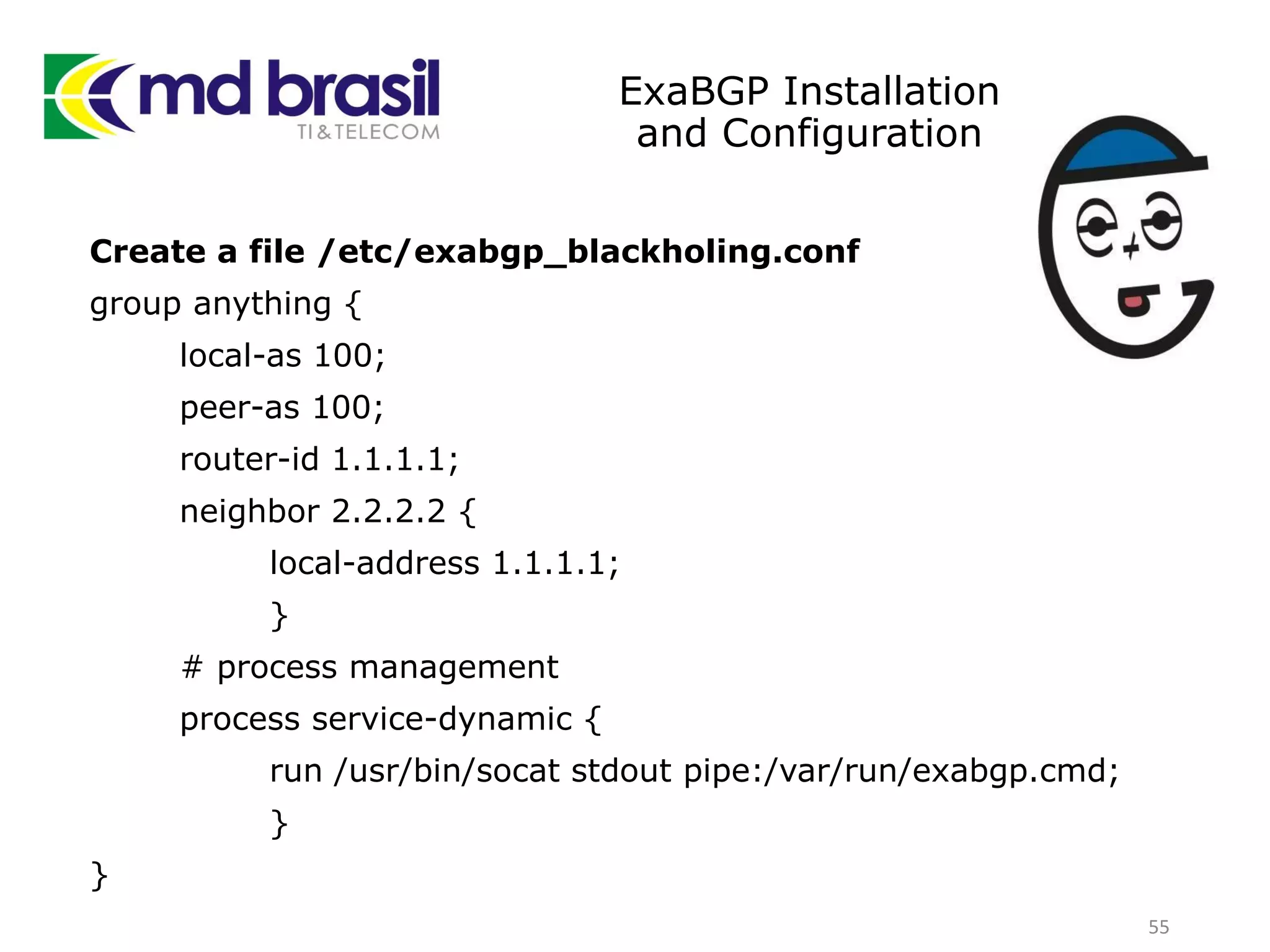
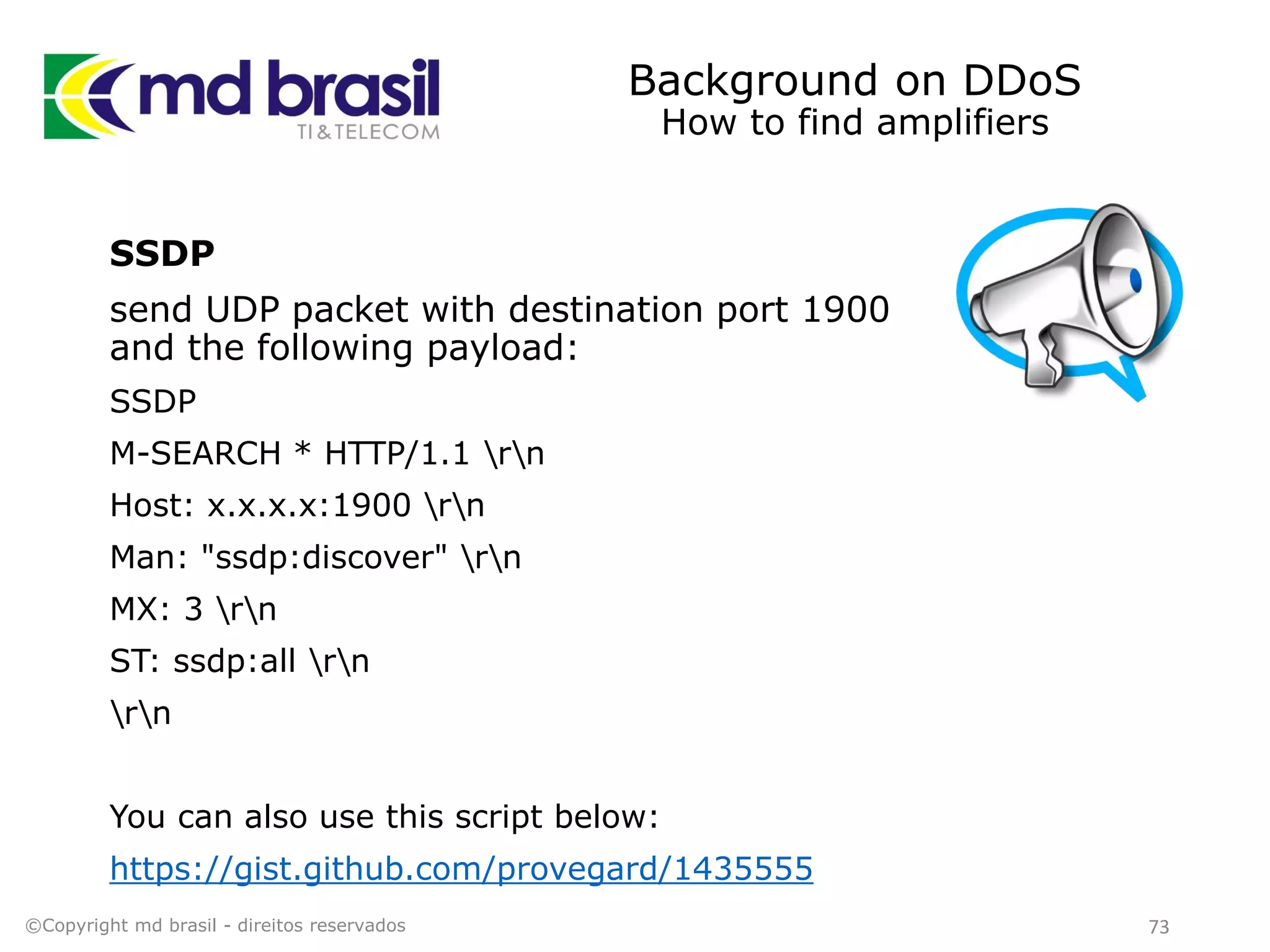
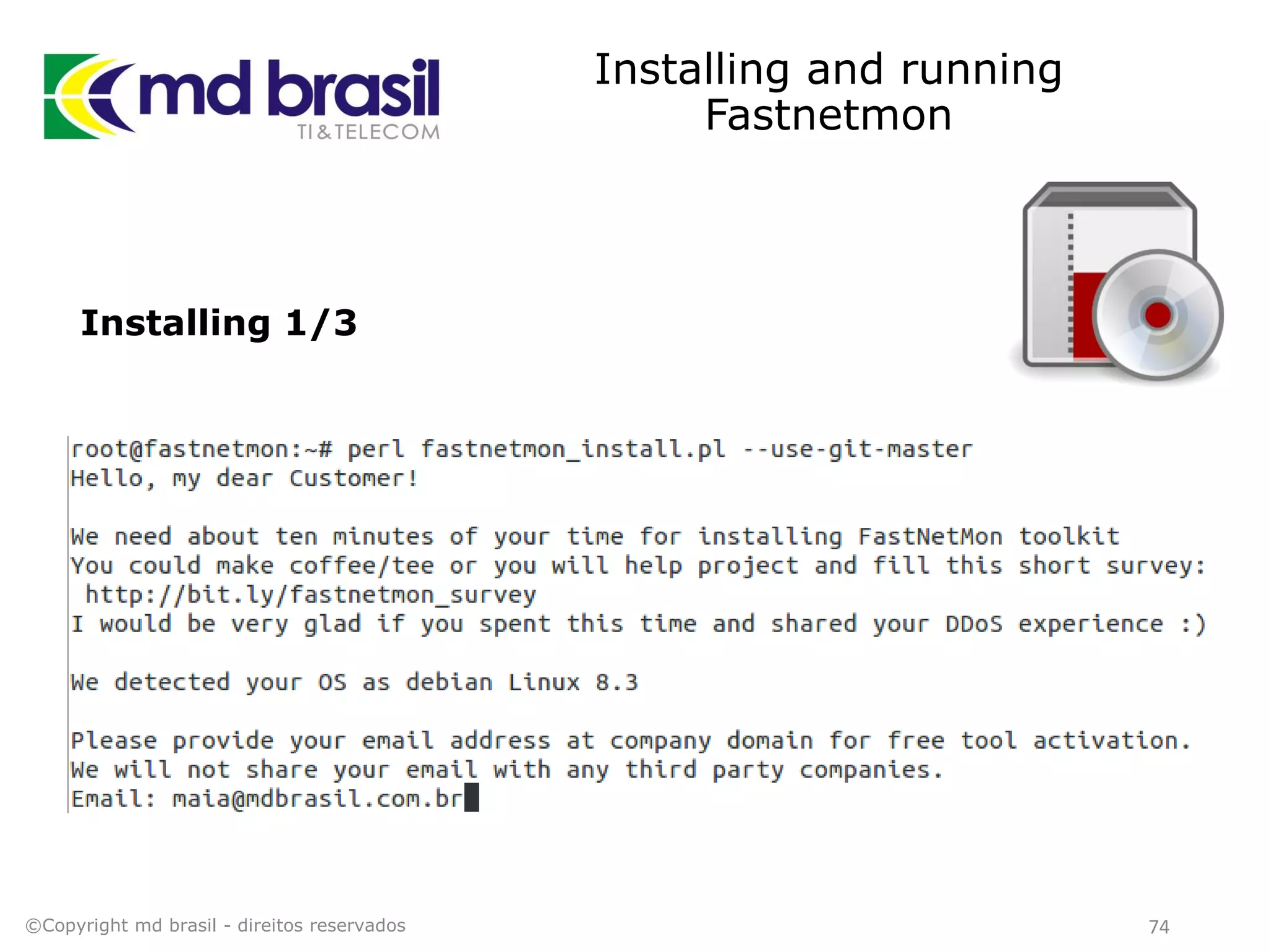
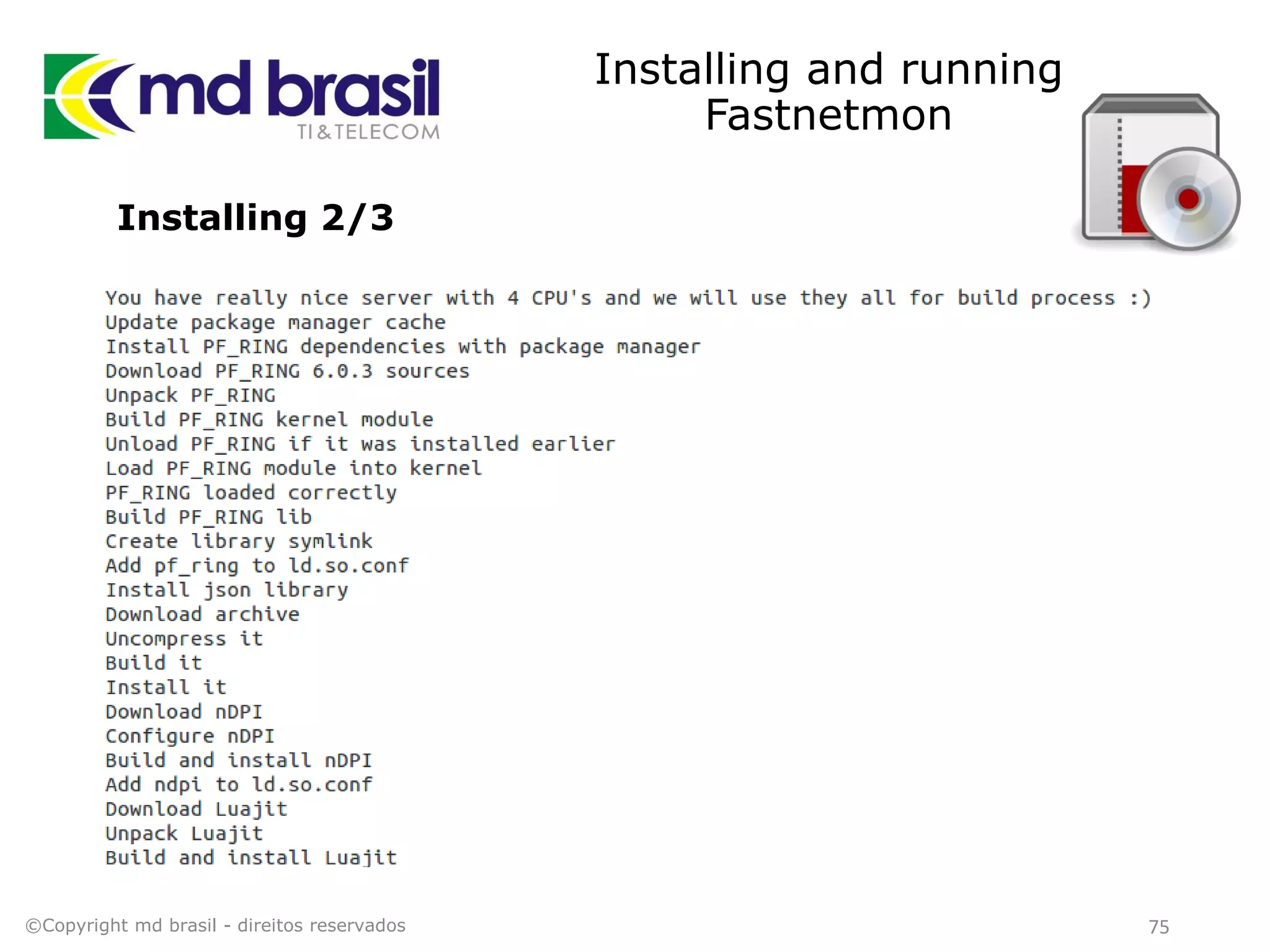
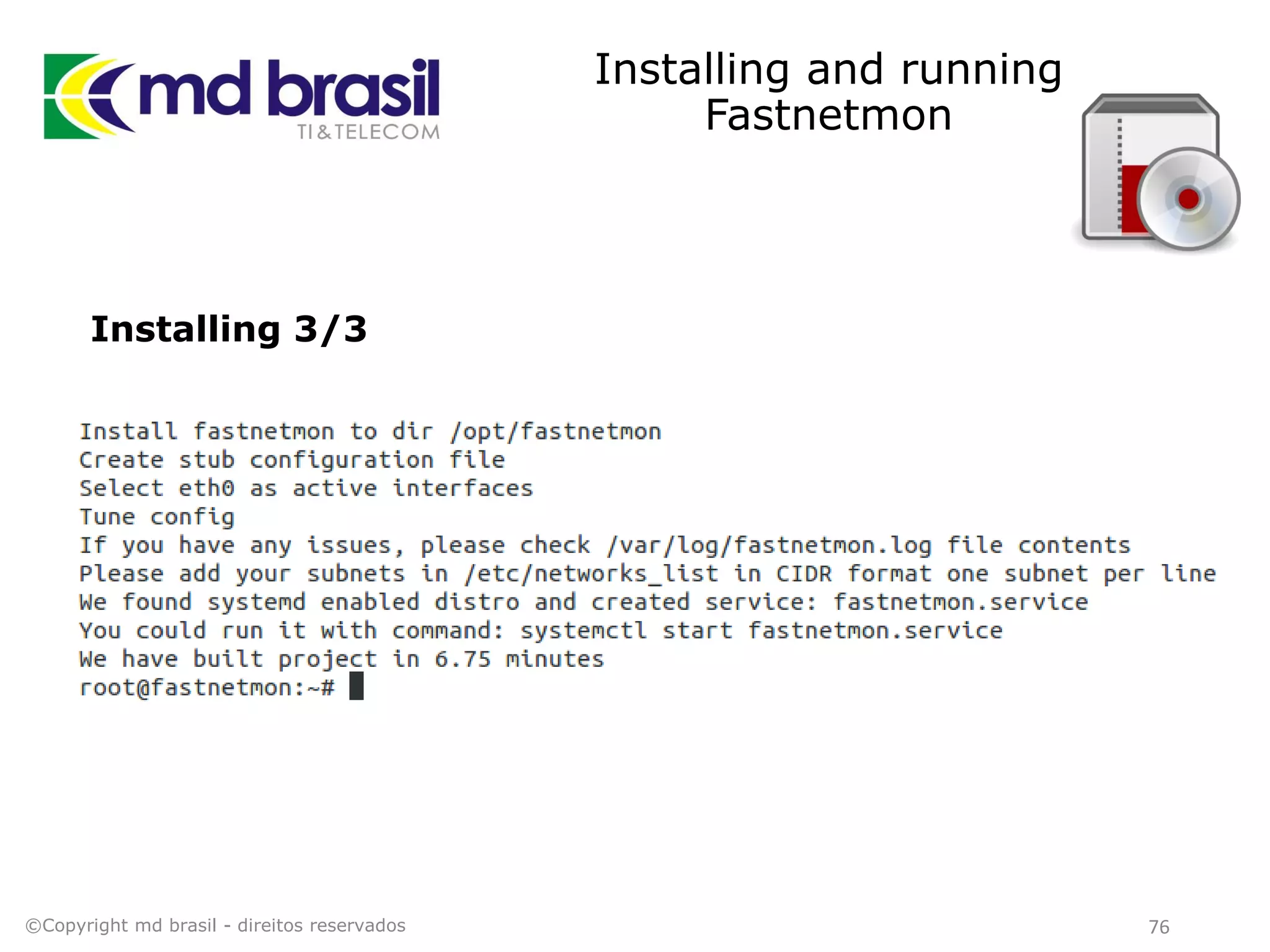
This document discusses distributed denial of service (DDoS) attacks, detection, and mitigation. It provides background on DDoS including components and architecture. It explains why small and medium internet service providers should care about DDoS attacks. The presentation aims to show how an ISP can implement an automated solution for DDoS mitigation using Mikrotik Traffic Flow, Fastnetmon for detection, and ExaBGP for route announcements. Detection and mitigation techniques are discussed such as remote triggered blackholing, mitigation at a cloud scrubbing center, and using the Cymru Unwanted Traffic Removal Service.