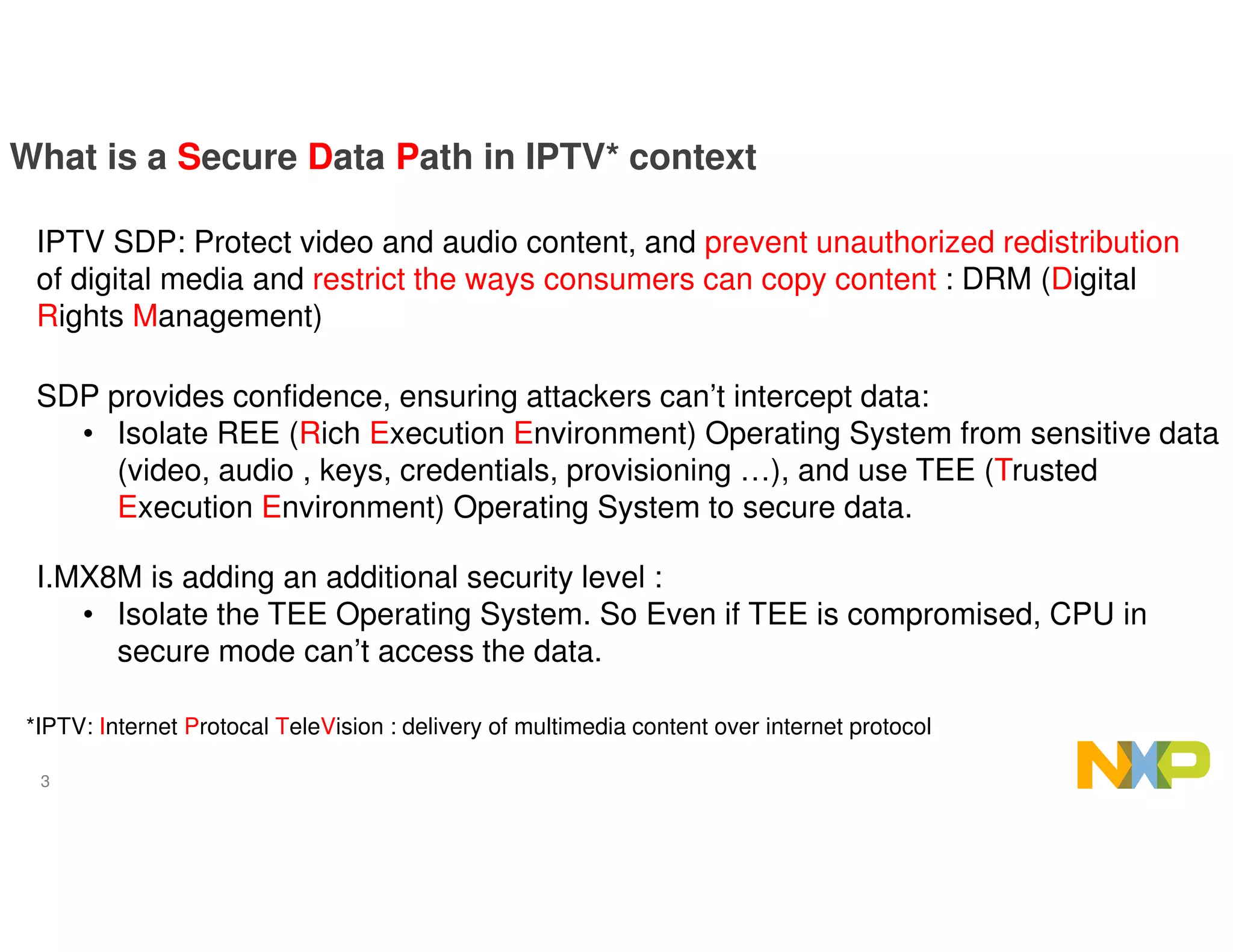
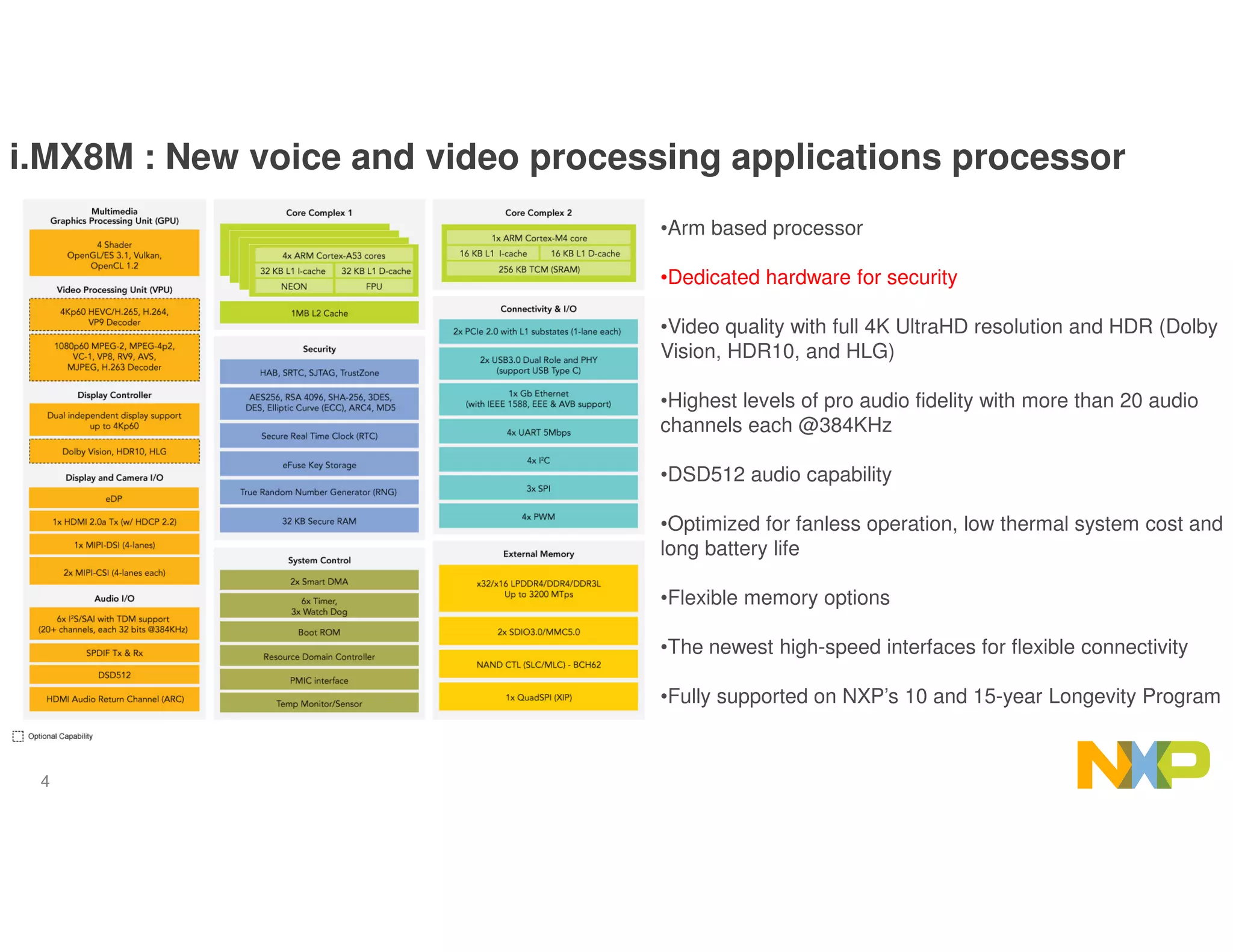
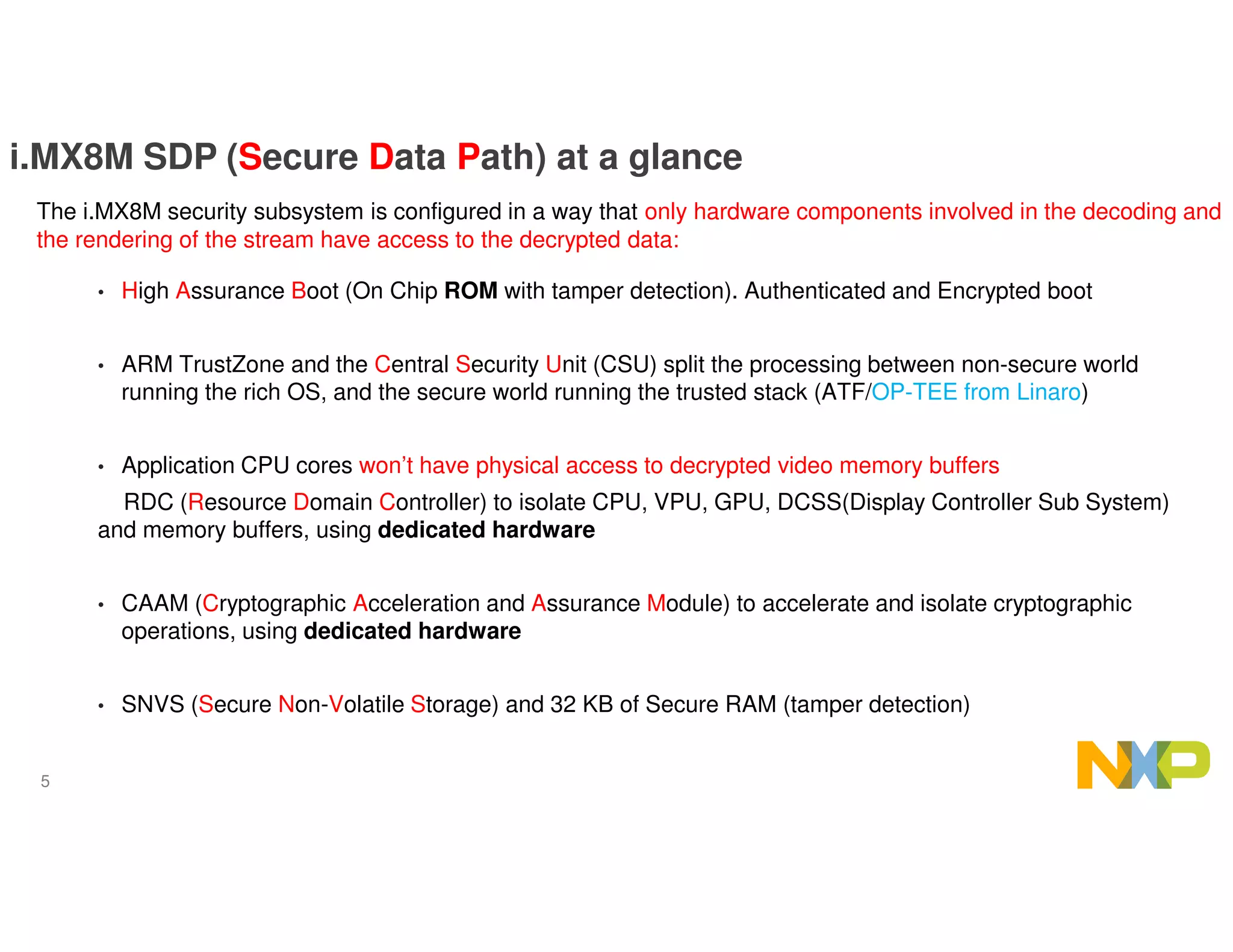
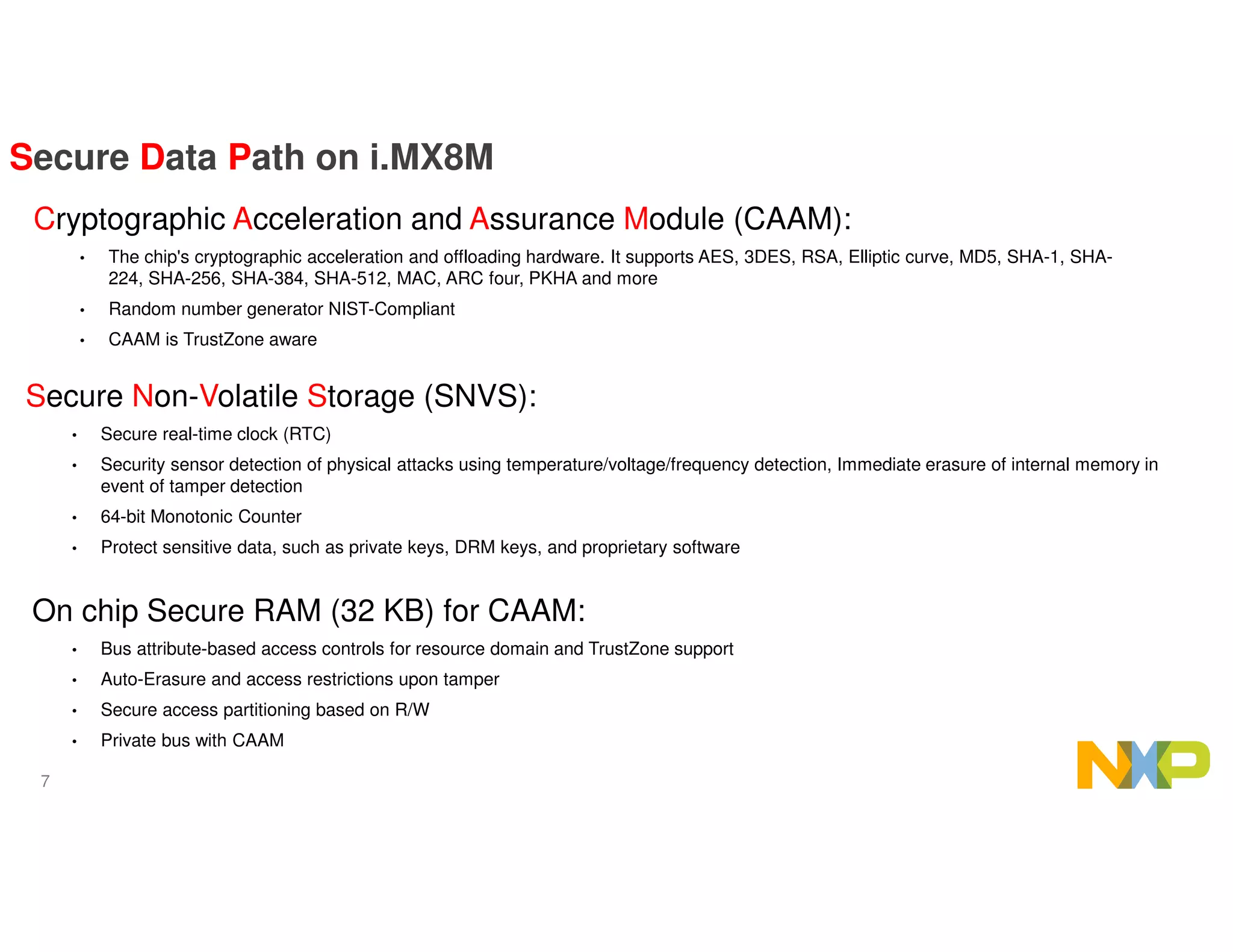
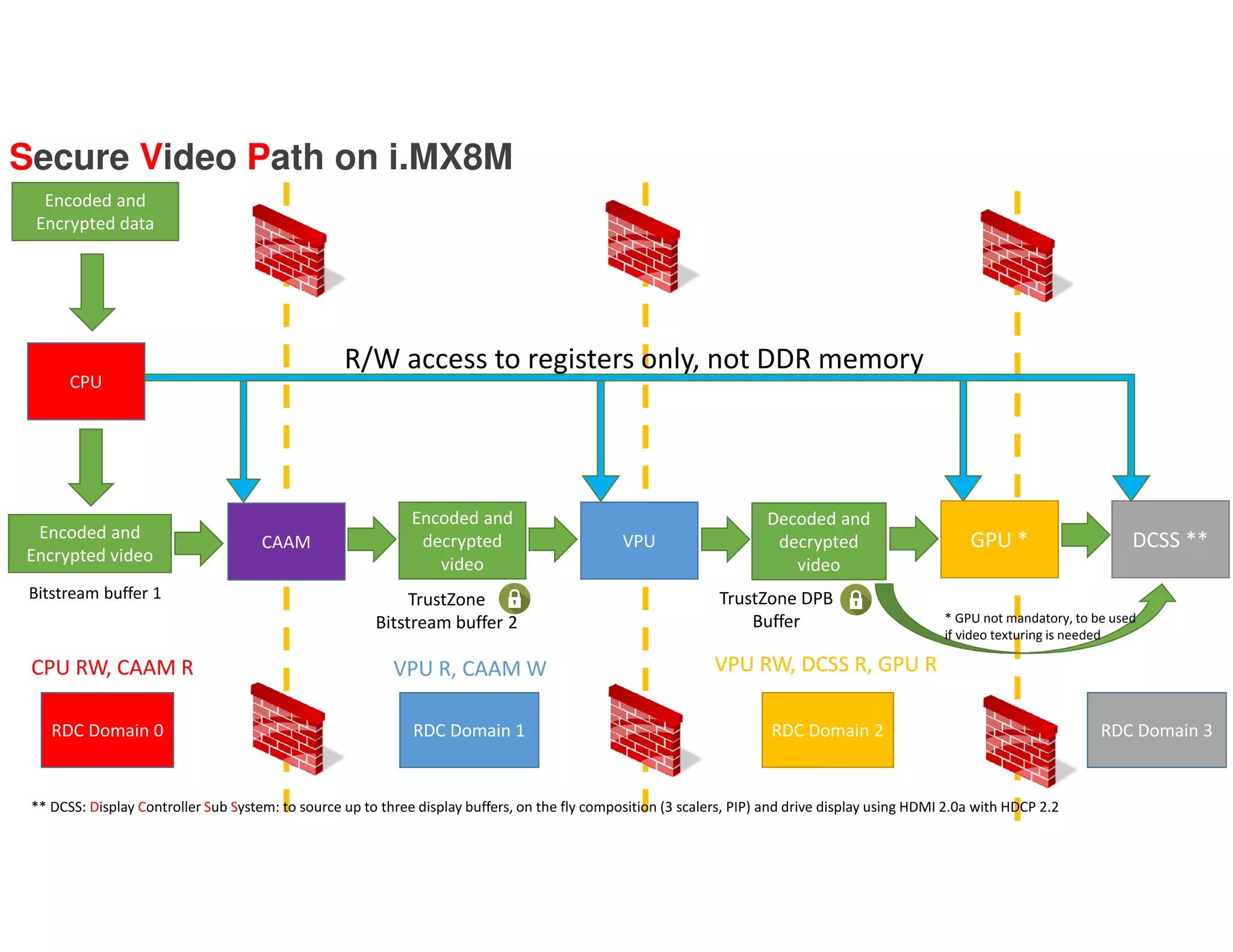
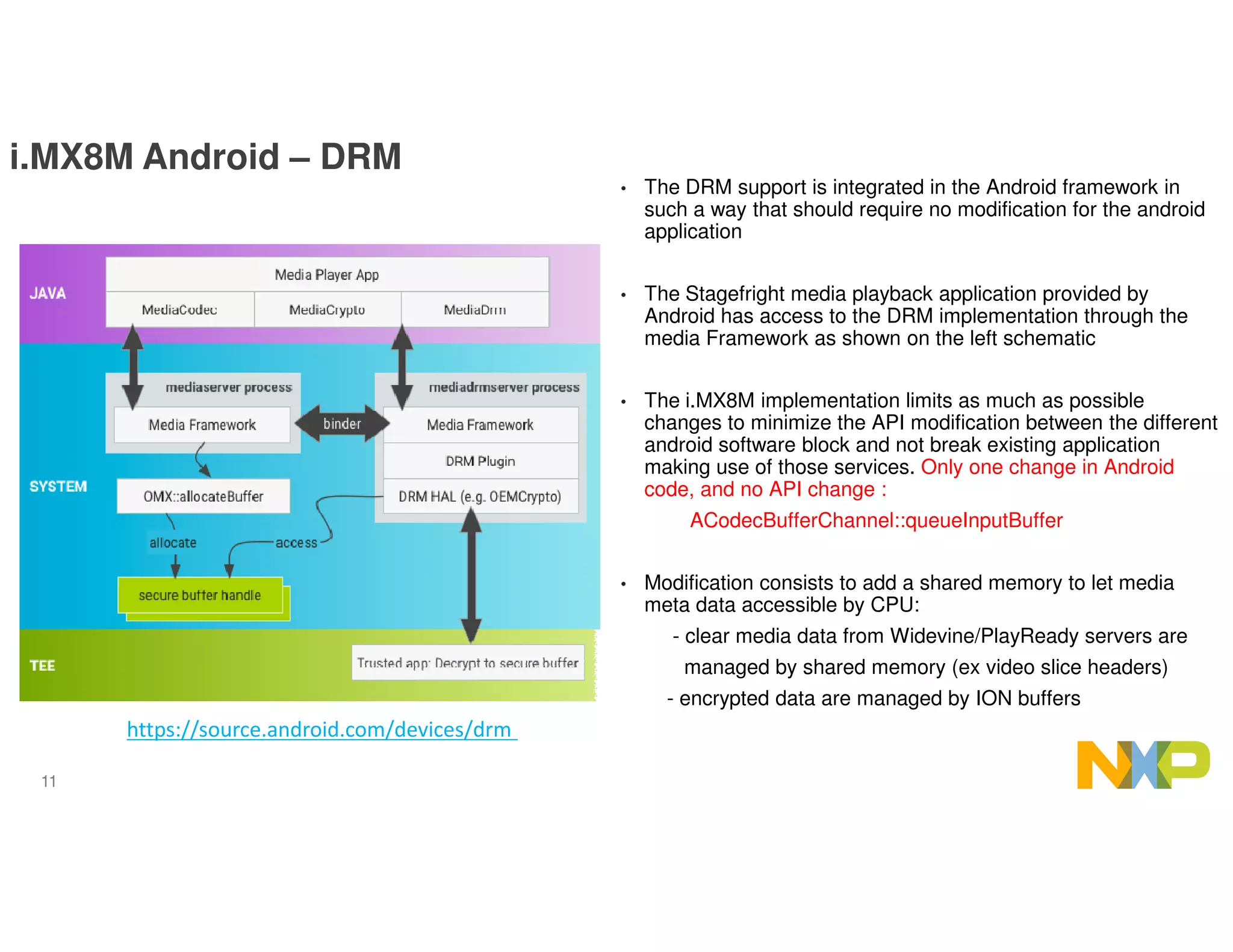
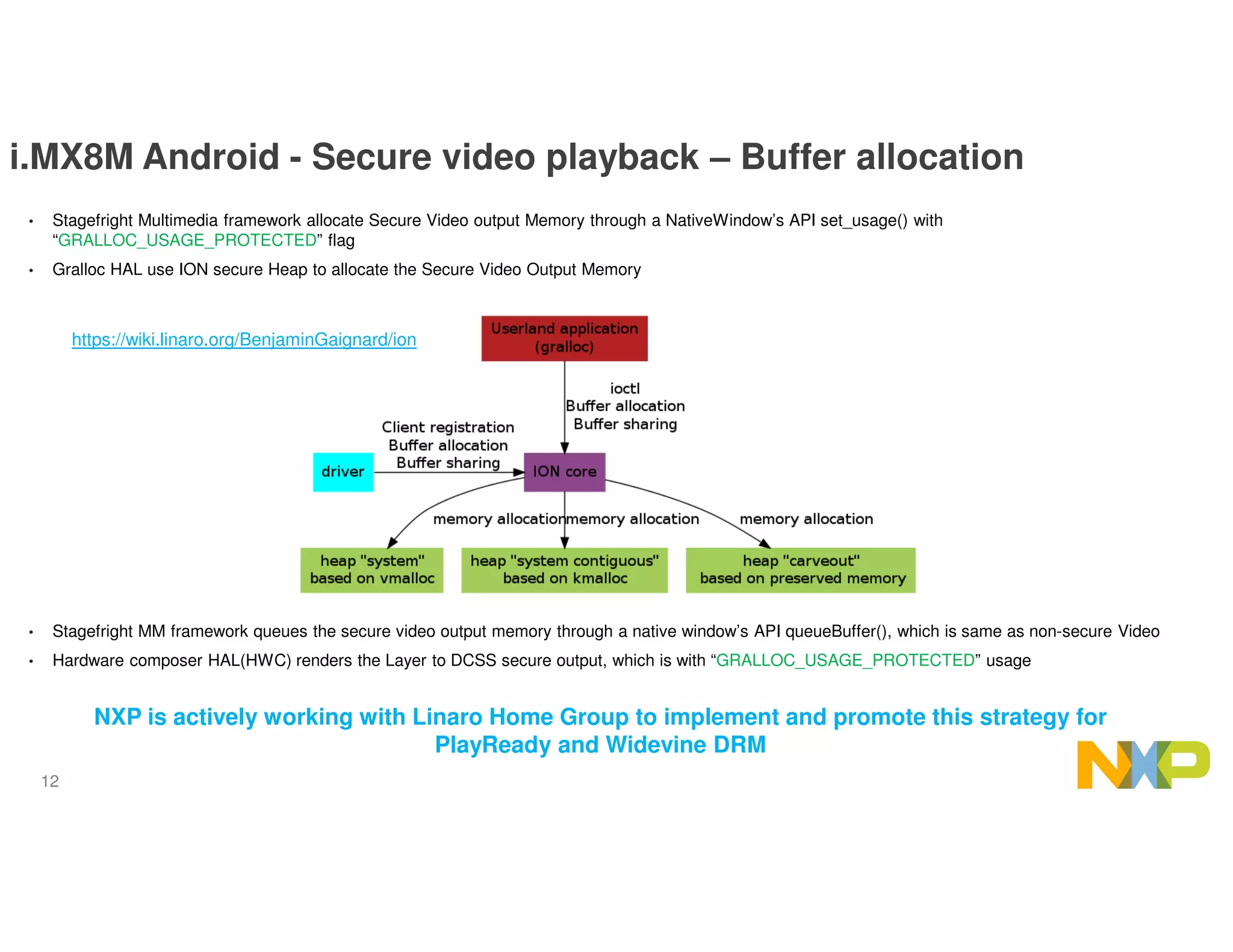
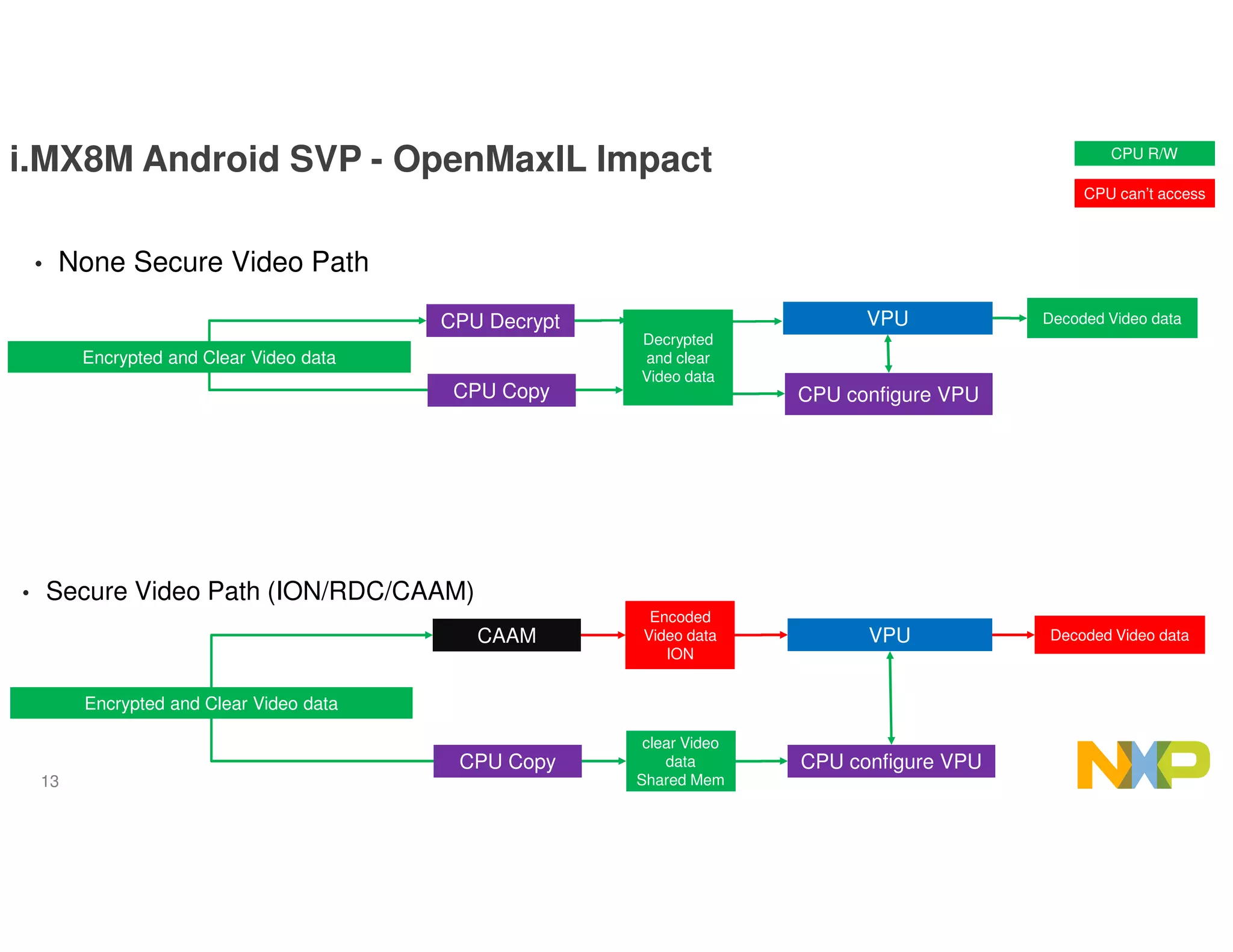
The document outlines the secure data path (SDP) features of the i.MX8M processor designed for IPTV, emphasizing its abilities to protect video and audio content through hardware-based security measures. It describes the architecture, which isolates processing environments, and includes components such as the cryptographic acceleration and assurance module (CAAM) and resource domain controller (RDC) to manage access to sensitive data. The integration of DRM support within Android without significant modifications to existing applications is also highlighted, ensuring secure video playback and management of encrypted content.




![14
i.MX8M Android SVP – Crypto PlugIn impact
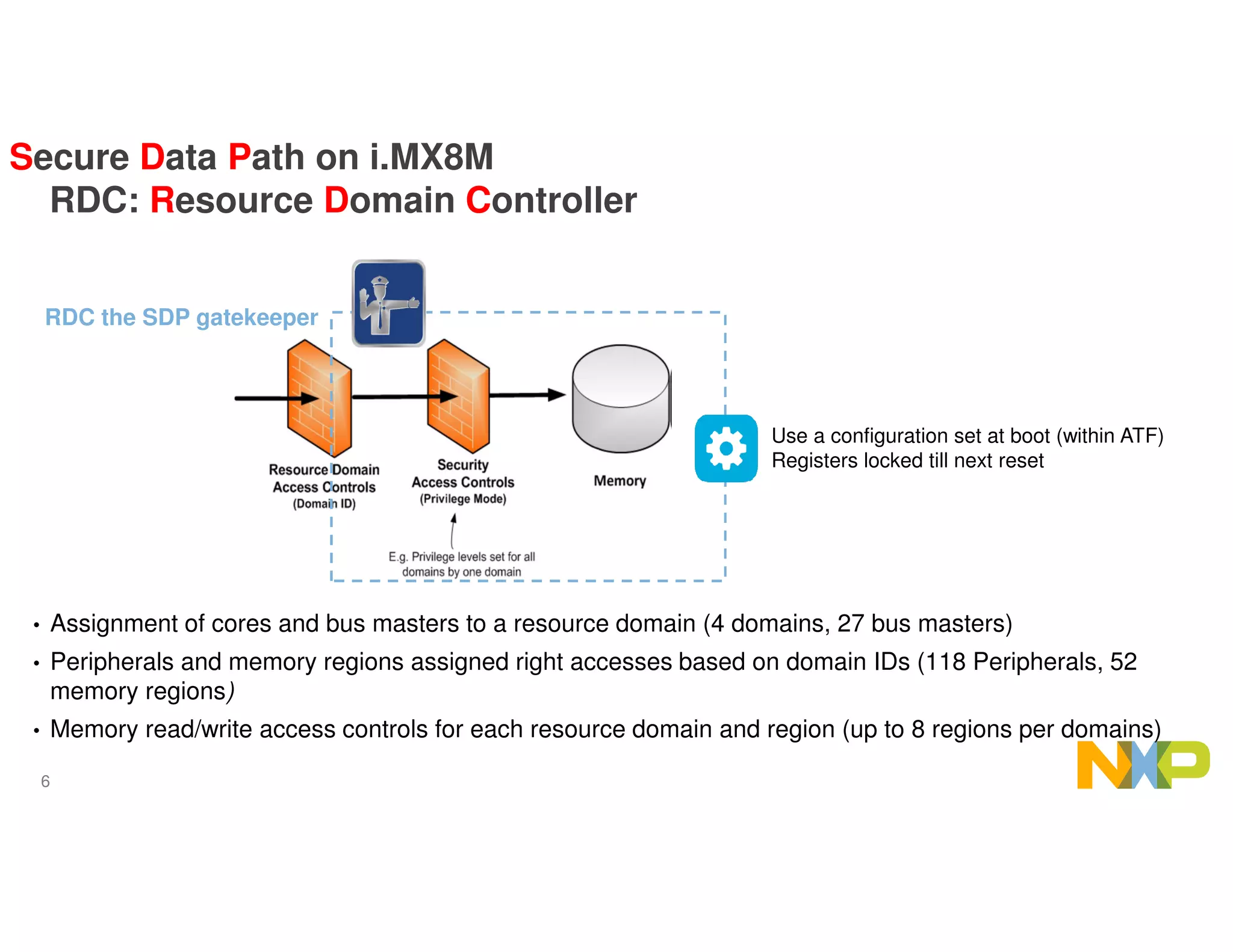
Shared Memory R&W by CPU
Decrypted data ION buffer heap 4, RDC protected, CPU can’t read
VPU
CPU
Decoded data
ION buffer heap 2.
RDC protected CPU can’t access.
SubSample 1 SubSample n
Decrypted and Clear data, free CPU access
Num of
Bytes
Clear
Num of
Bytes
Crypted
Num of
Bytes
Clear
Num of
Bytes
Crypted
Num of
Bytes
Clear
Num of
Bytes
Crypted
SubSample 1
clear data
SubSample 2 …
SubSample 2
clear data
SubSample n
clear data
SubSample 1
decrypted data
SubSample 2
decrypted data
SubSample n
decrypted data
Configure VPU Driver
ssize_t PlayReadyCryptoPlugin::decrypt(
bool secure, // secure=1 use Secure Data Path
const uint8_t key[16], const uint8_t iv[16],
Mode mode, // kMode_Unencrypted or not
const Pattern &,
const void *srcPtr,
const SubSample * subSamples, size_t numSubSamples,
void *dstPtr,
AString * errorDetailMsg)
Free cpu access
SubSample 1
clear data
Image Boundary/slice header: https://yumichan.net/video-processing/video-compression/introduction-to-h264-nal-unit/
copy
decrypt](https://image.slidesharecdn.com/sdpimx8m-linaro-hongkongconnect2018-v1-180404153742/75/HKG18-113-Secure-Data-Path-work-with-i-MX8M-14-2048.jpg)
