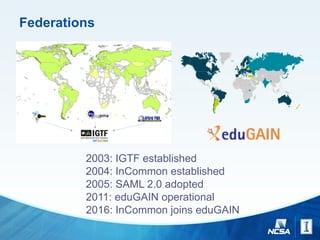
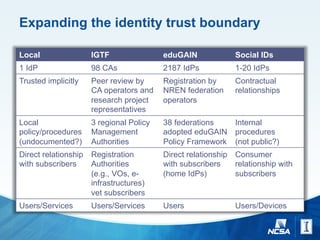
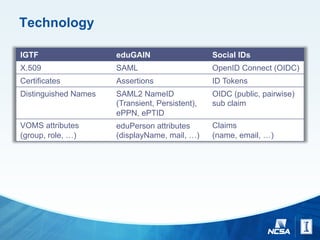
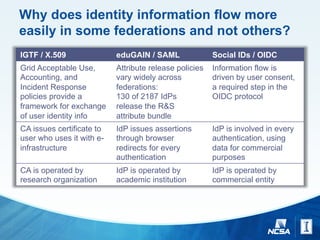
The document discusses challenges and strategies for managing identity and access on a global scale for research collaborations, emphasizing the importance of trust in external identity providers. It addresses operational gaps, unique needs for e-science identity management, and the necessity for scaling up from a few to thousands of identity providers while ensuring security and interoperability. Additionally, it explores identity assurance frameworks and the need for better practices in federating services across diverse institutions and commercial providers.