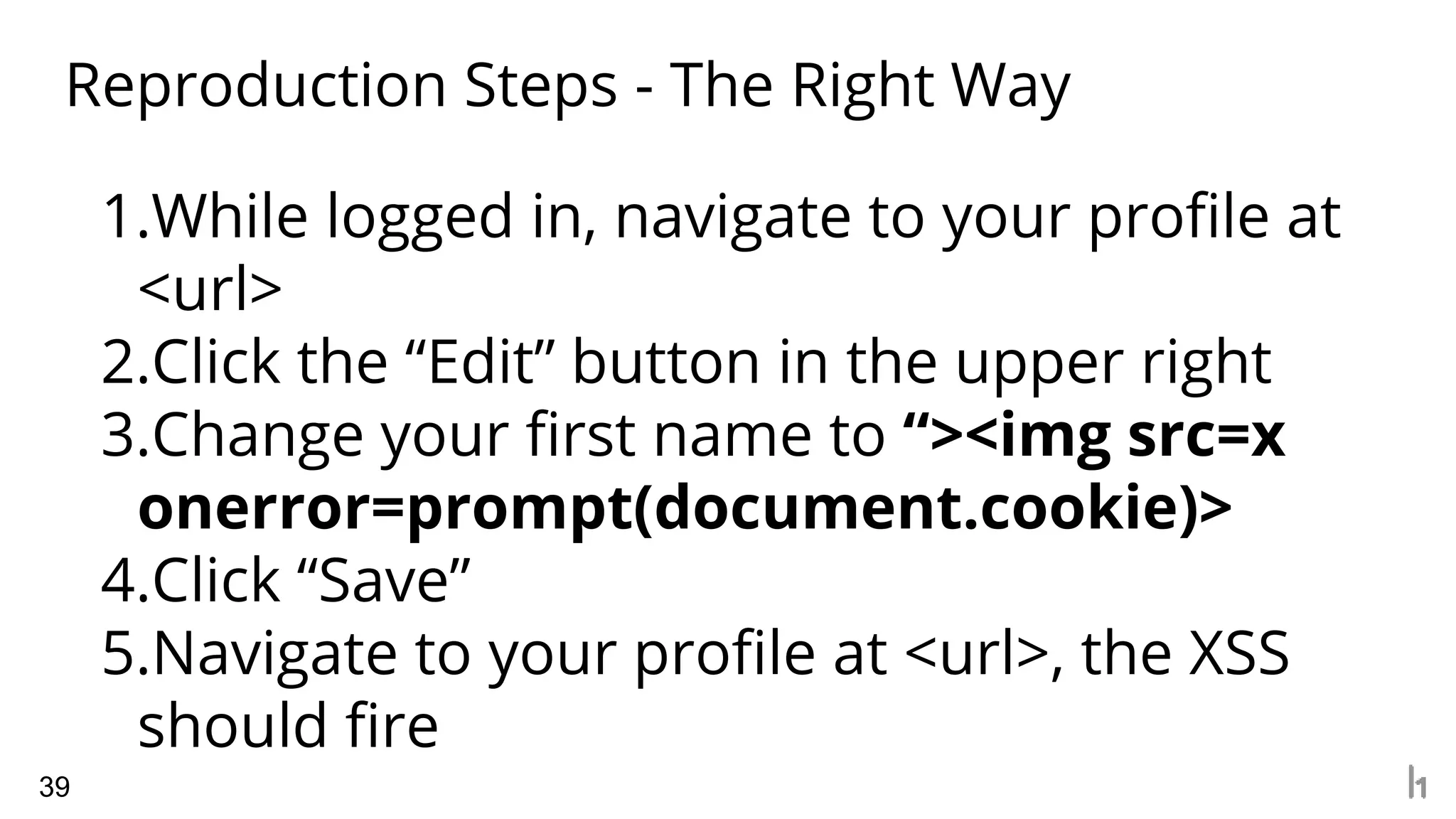
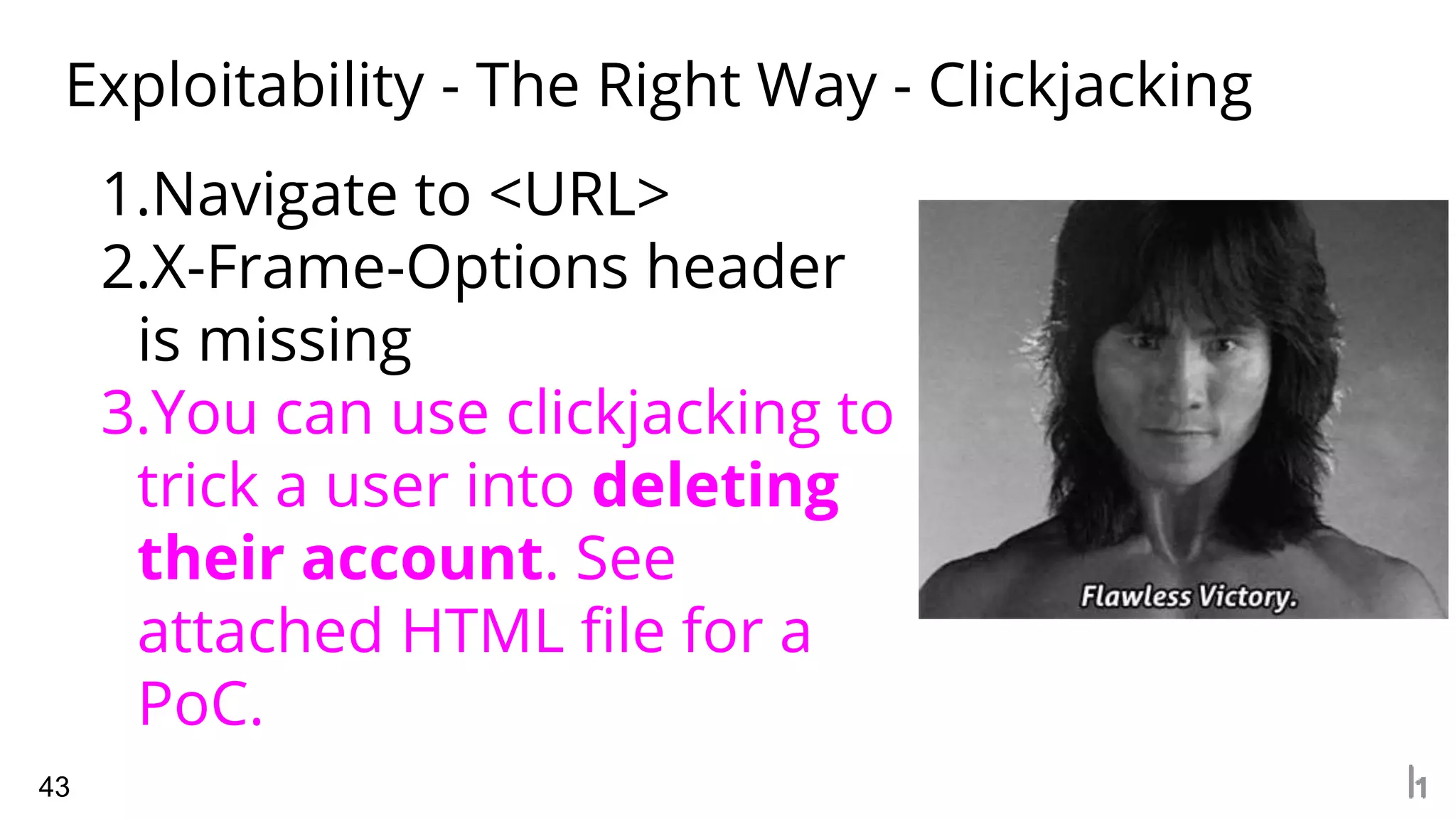
1. The document discusses how to write effective bug bounty reports by understanding what security teams look for in reports. It emphasizes providing detailed reproduction steps, analyzing exploitability and potential impact, and considering the perspective of the security team.
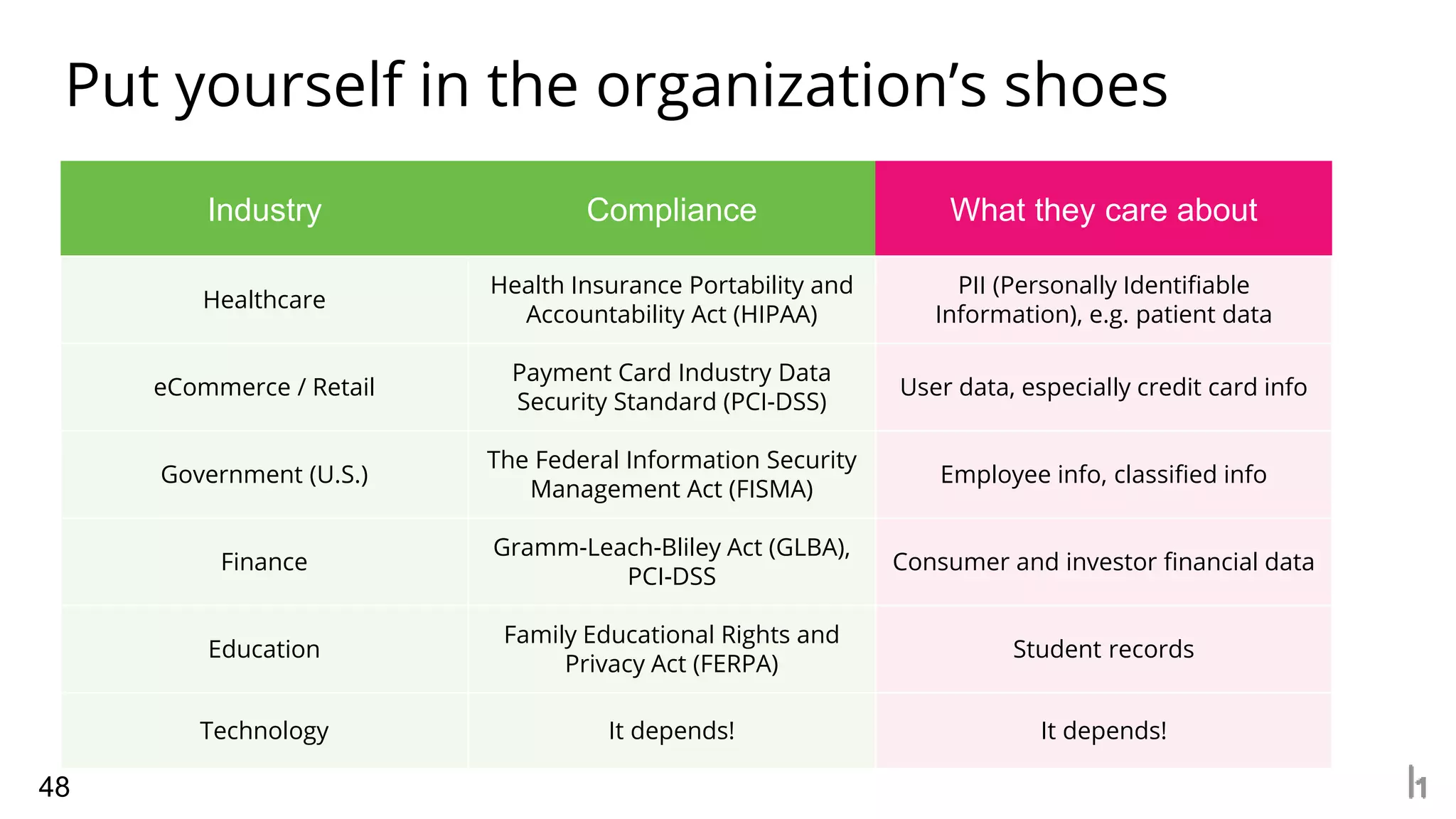
2. Common elements of an effective report include clear reproduction steps, analysis of how an attack could actually work in the real world, and understanding what types of vulnerabilities are important to the specific organization based on their industry and needs.
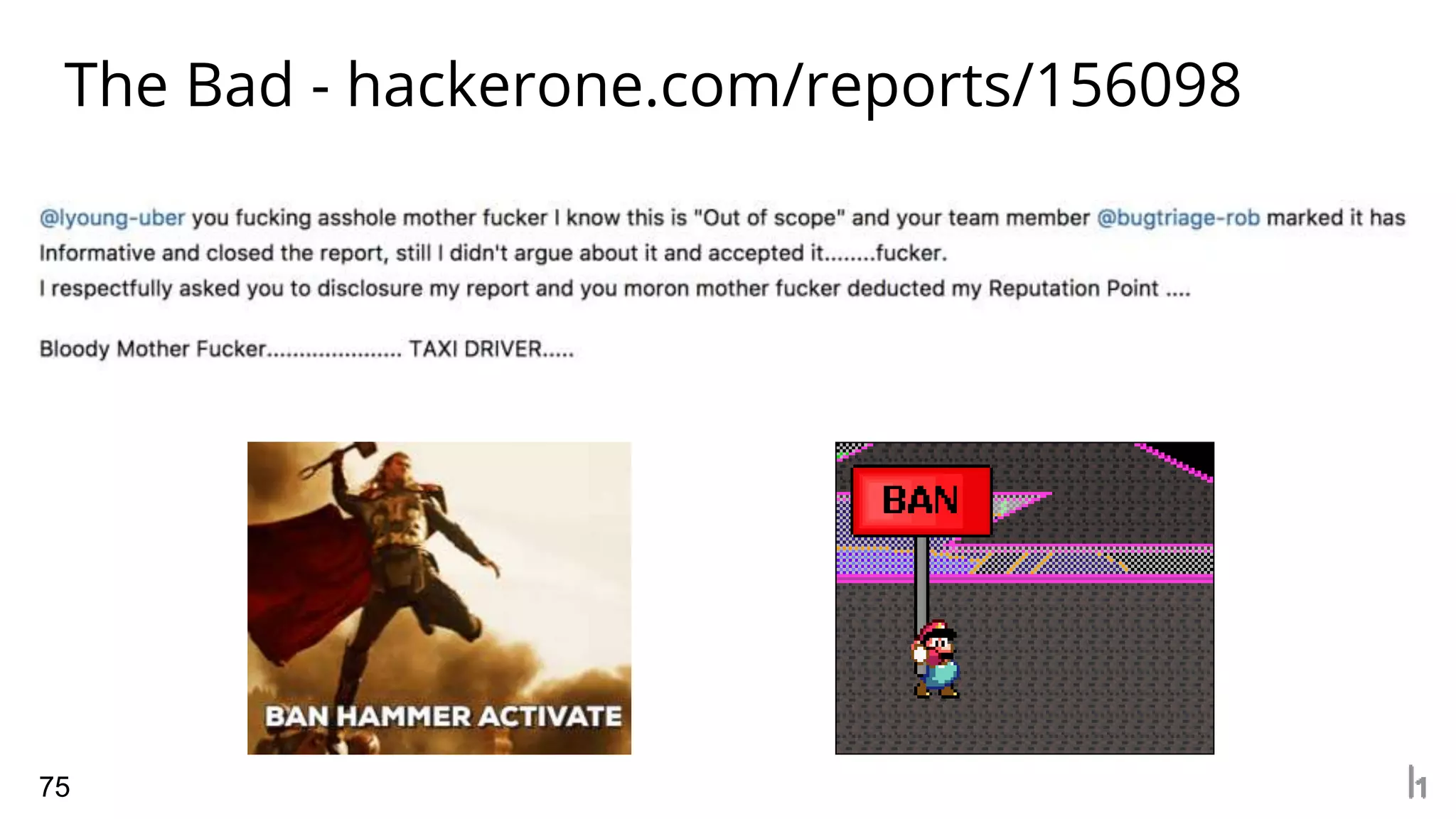
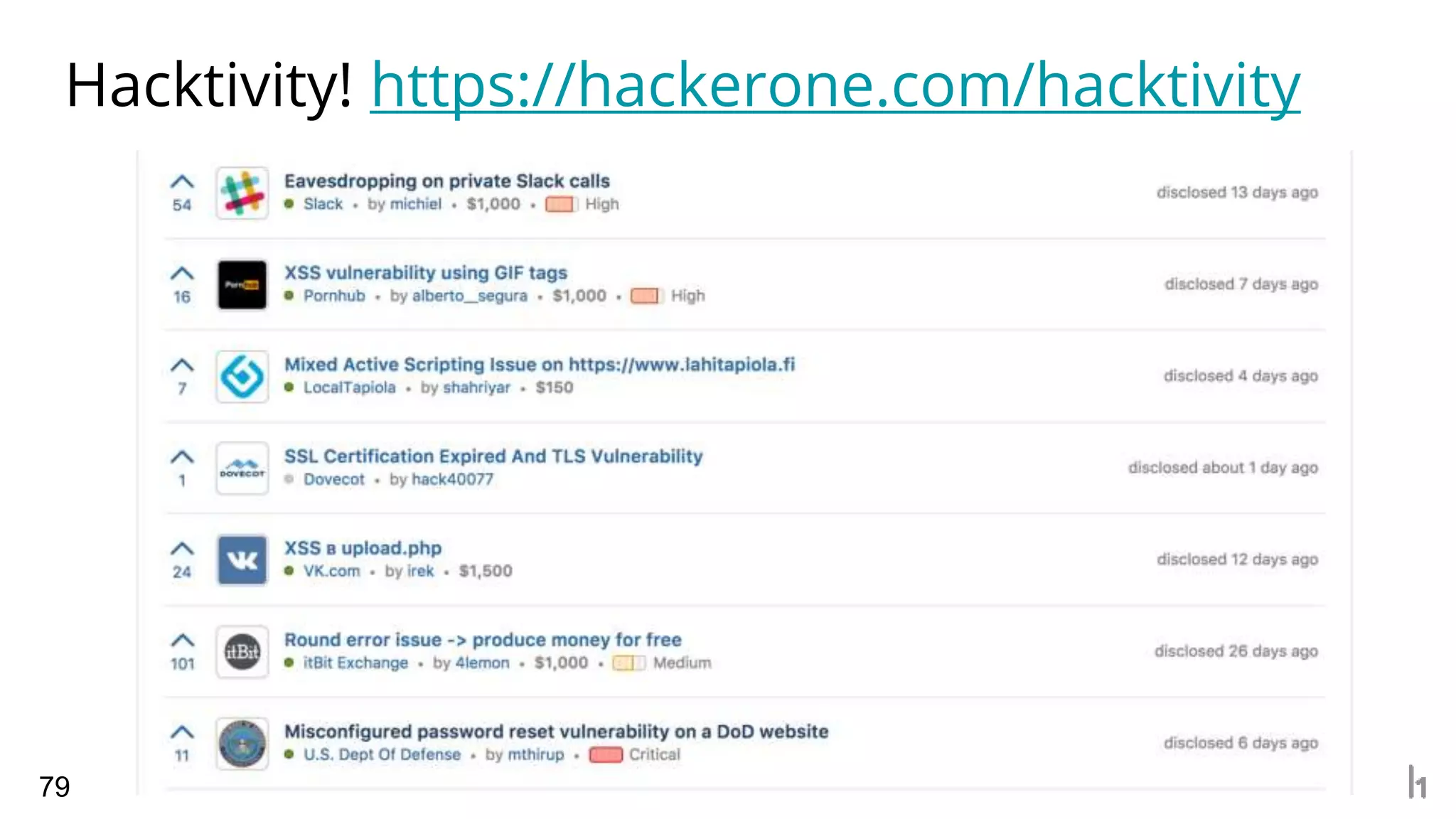
3. The presentation provides examples of good and bad reports, outlines typical service level agreements, and emphasizes asking questions to understand the priorities and scope of individual security programs.