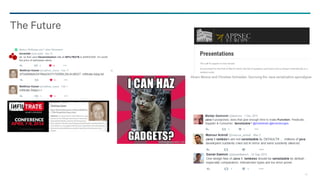
The document is a presentation on Java's object serialization and deserialization, detailing the processes, APIs, and potential vulnerabilities associated with them. It explains how serialized objects are transformed into a flat data stream for storage or transmission, the structure of serialized data, and the security risks of deserialization attacks. Additionally, it explores the use of gadget chains in exploiting improper deserialization, which can lead to code execution vulnerabilities.





![8
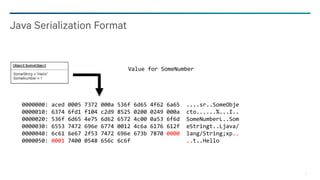
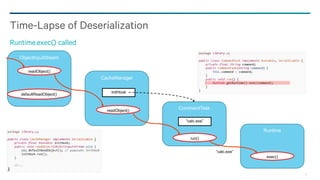
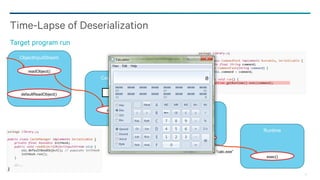
Java Serialized Form
Uncustomized, default, simple (de)serialization
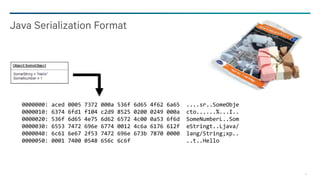
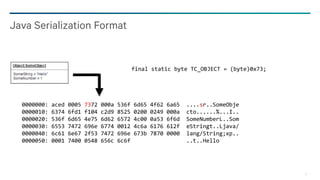
Object serialized form:
− TC_OBJECT (byte, 0x73)
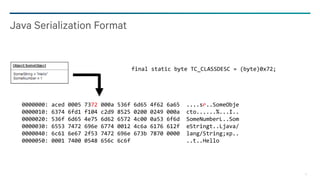
− Class Description (or ref)
− TC_CLASSDESC (byte, 0x72)
− Class Name (String)
− Serial Version UID (long)
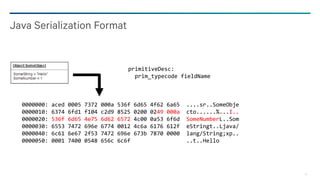
− Field Descriptions*
− Field Type Code (byte)
− Field Name (String)
− Field Type (String, for non-primitive)
− Field values*
− [Primitive serialized form] | [Object serialized form] | ref
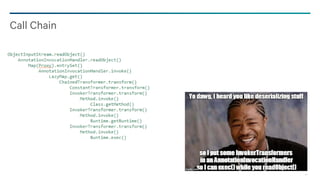
− Causes recursive calls to writeObject()/readObject() or read*()/write*()
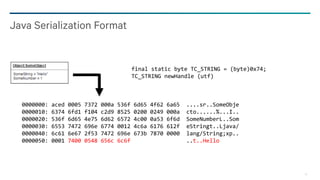
• Refs: Later representations of
same object substituted with
incrementing “handles” to save
space and preserve referential
relationships
• TC_REFERENCE (byte, 0x71)
• Handle number (int)
• > 0x7e0000
• Field Type Codes:
'B'=byte, 'C'=char, 'D'=double,
'F'=float, 'I'=int, 'J'=long,
'L'=class/interface, 'S'=short,
'Z'=boolean, '['=array,](https://image.slidesharecdn.com/deserializemyshorts-160321174335/85/OWASP-SD-Deserialize-My-Shorts-Or-How-I-Learned-To-Start-Worrying-and-Hate-Java-Object-Deserialization-8-320.jpg)










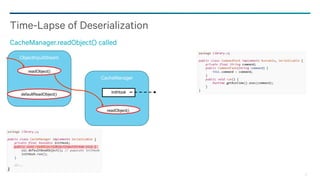
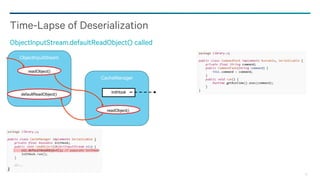
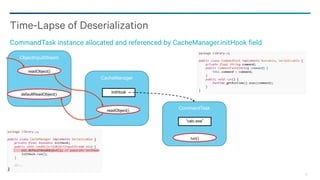
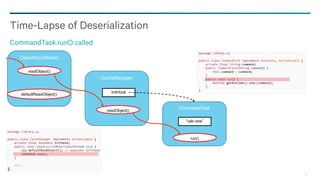





































![85
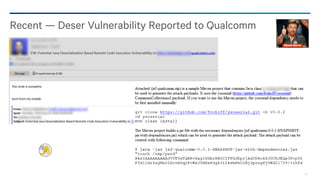
$ java -jar target/ysoserial-0.0.5-SNAPSHOT-all.jar
Y SO SERIAL?
Usage: java -jar ysoserial-[version]-all.jar [payload type] '[command to execute]'
Available payload types:
BeanShell1
C3P0
CommonsBeanutils1
CommonsCollections1
CommonsCollections2
CommonsCollections3
CommonsCollections4
CommonsCollections5
FileUpload1
Groovy1
Hibernate1
Hibernate2
JRMPClient
JRMPListener
JSON1
Jdk7u21
Jython1
Myfaces1
Myfaces2
ROME
Spring1
Spring2
Recent — ysoserial dev activity picking up](https://image.slidesharecdn.com/deserializemyshorts-160321174335/85/OWASP-SD-Deserialize-My-Shorts-Or-How-I-Learned-To-Start-Worrying-and-Hate-Java-Object-Deserialization-85-320.jpg)