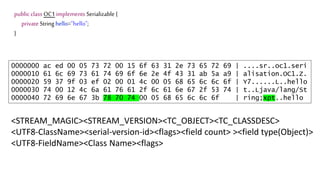
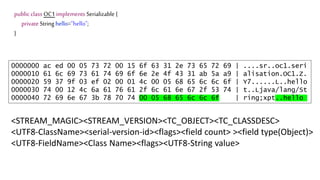
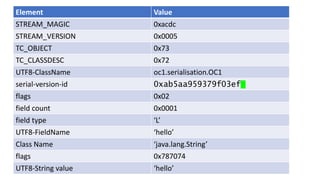
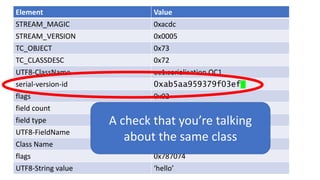
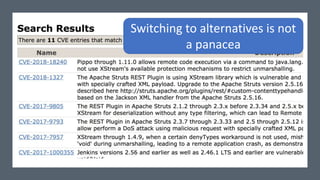
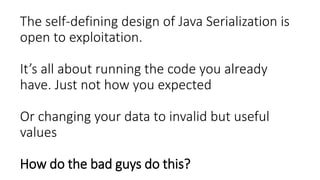
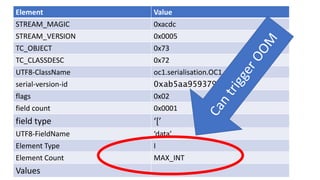
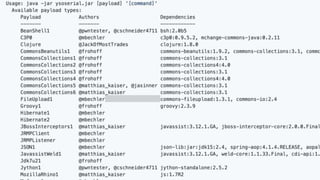
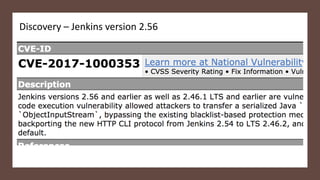
The document discusses Java serialization and its flaws. It begins by explaining common uses of serialization and how easy it is to implement. However, it notes that the built-in design has security issues, as serialization data can contain sensitive object details. It also explains that serialization is exploited in attacks and discusses how to mitigate risks from Java and alternative serialization formats.











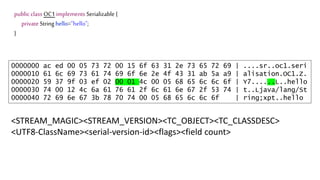
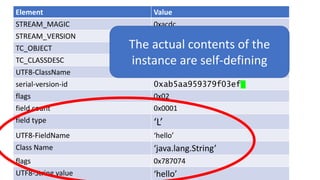

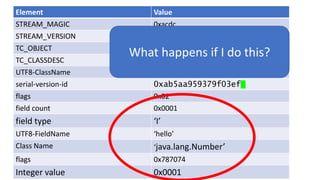


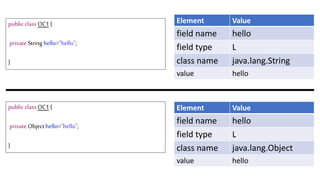
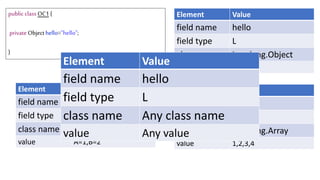

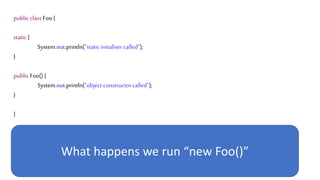


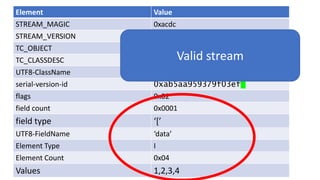
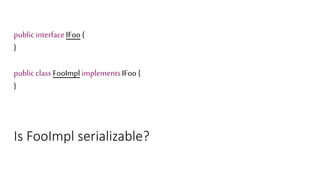
![We’ve just learnt that constructors do not get
called during deserialization
public class Foo implements Serializable{
private int data[];
public Foo() {
data=new int[] {1,2,3,4};
}
public int size() {
return data.length;
}
What happens here?](https://image.slidesharecdn.com/serializationfairytale-181029085606/85/A-Modern-Fairy-Tale-Java-Serialization-42-320.jpg)
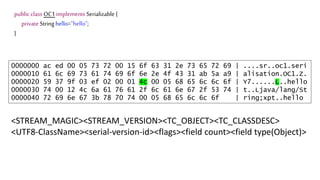
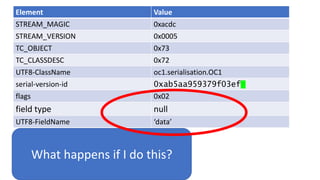
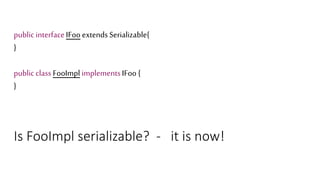
![We’ve just learnt that constructors do not get
called during deserialization
public class Foo implements Serializable{
private int data[];
public Foo() {
data=new int[] {1,2,3,4};
}
public int size() {
return data.length;
}
The answer is 4?](https://image.slidesharecdn.com/serializationfairytale-181029085606/85/A-Modern-Fairy-Tale-Java-Serialization-44-320.jpg)
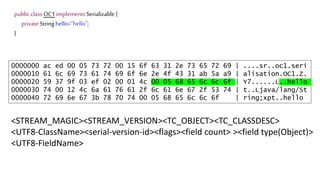
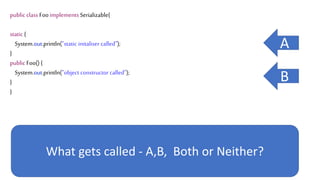
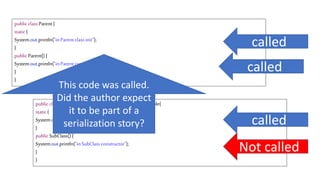
![We’ve just learnt that constructors do not get
called during deserialization
public class Foo implements Serializable{
private int data[];
public Foo() {
data=new int[] {1,2,3,4};
}
public int size() {
return data.length;
}
Code here never
Gets called](https://image.slidesharecdn.com/serializationfairytale-181029085606/85/A-Modern-Fairy-Tale-Java-Serialization-46-320.jpg)
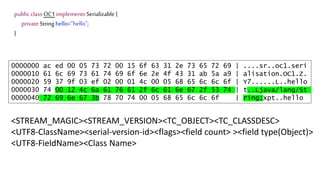
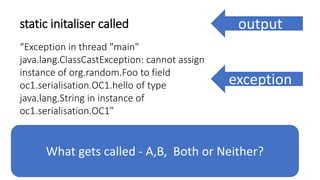
![We’ve just learnt that constructors do not get
called during deserialization
public class Foo implements Serializable{
private int data[];
public Foo() {
data=new int[] {1,2,3,4};
}
public int size() {
return data.length;
}
So NPE!](https://image.slidesharecdn.com/serializationfairytale-181029085606/85/A-Modern-Fairy-Tale-Java-Serialization-47-320.jpg)





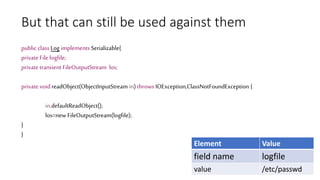
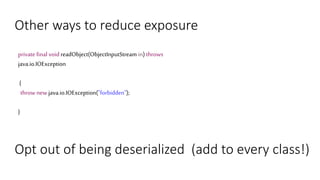

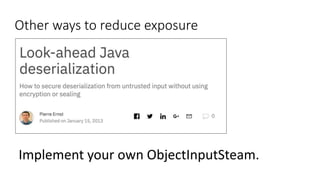

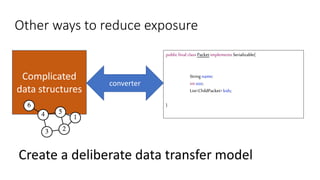
![Other ways to reduce exposure
And maybe stop using native serialization at all
{
"name" : "foobar" ,
"size" : 1 ,
"kids" : [ { } , {} ]
}
Complicated
data structures
converter](https://image.slidesharecdn.com/serializationfairytale-181029085606/85/A-Modern-Fairy-Tale-Java-Serialization-65-320.jpg)















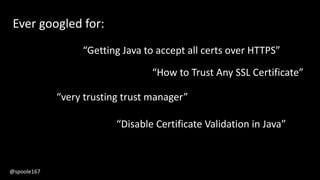
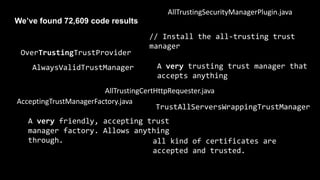
![TrustManager[] trustAllCerts = new TrustManager[]{
new X509TrustManager() {
public X509Certificate[] getAcceptedIssuers() {
return null;
}
public void checkClientTrusted(
X509Certificate[] certs, String authType) {
}
public void checkServerTrusted(
X509Certificate[] certs, String authType) {
}
public boolean isClientTrusted( X509Certificate[] cert) {
return true;
}
public boolean isServerTrusted( X509Certificate[] cert) {
return true;
}
}}
Ever written
something
like this?
@spoole167](https://image.slidesharecdn.com/serializationfairytale-181029085606/85/A-Modern-Fairy-Tale-Java-Serialization-91-320.jpg)