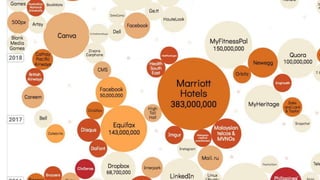
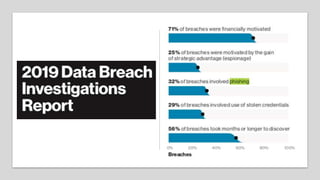
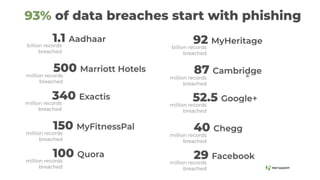
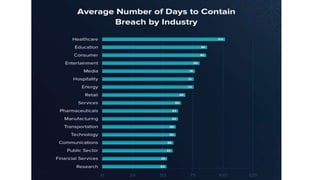
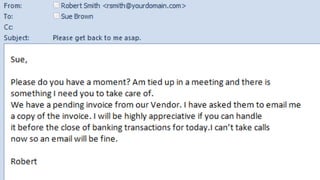
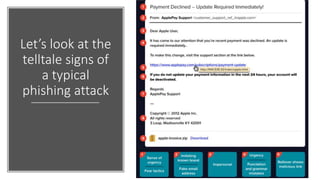
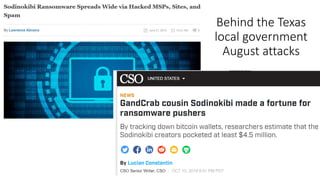
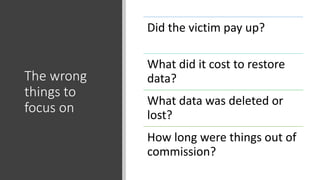
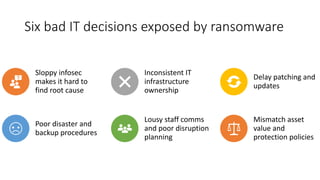
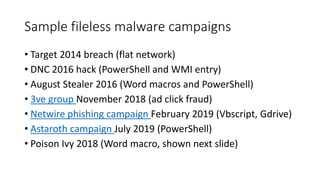
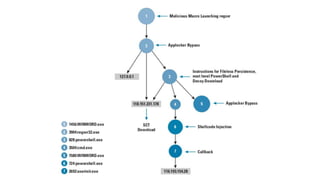
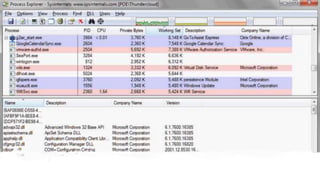
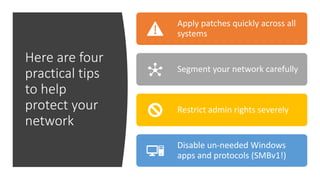
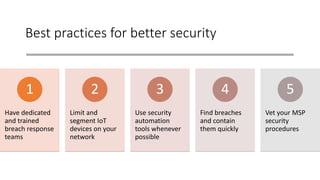
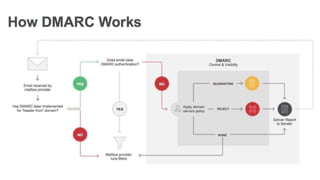
The document summarizes the current state of IT security based on a presentation given at an annual security conference. It discusses the typical stages of a cyber attack including phishing, ransomware, and lateral movement with fileless malware. Examples are provided of detection delays for major data breaches. Recommendations are made for improving security posture such as applying patches quickly, segmenting networks, restricting admin rights, and disabling unneeded protocols. Best practices discussed include having dedicated breach response teams, limiting IoT devices, using security automation, and vetting managed service providers. The use of SPF, DKIM, and DMARC protocols for email authentication is also recommended.