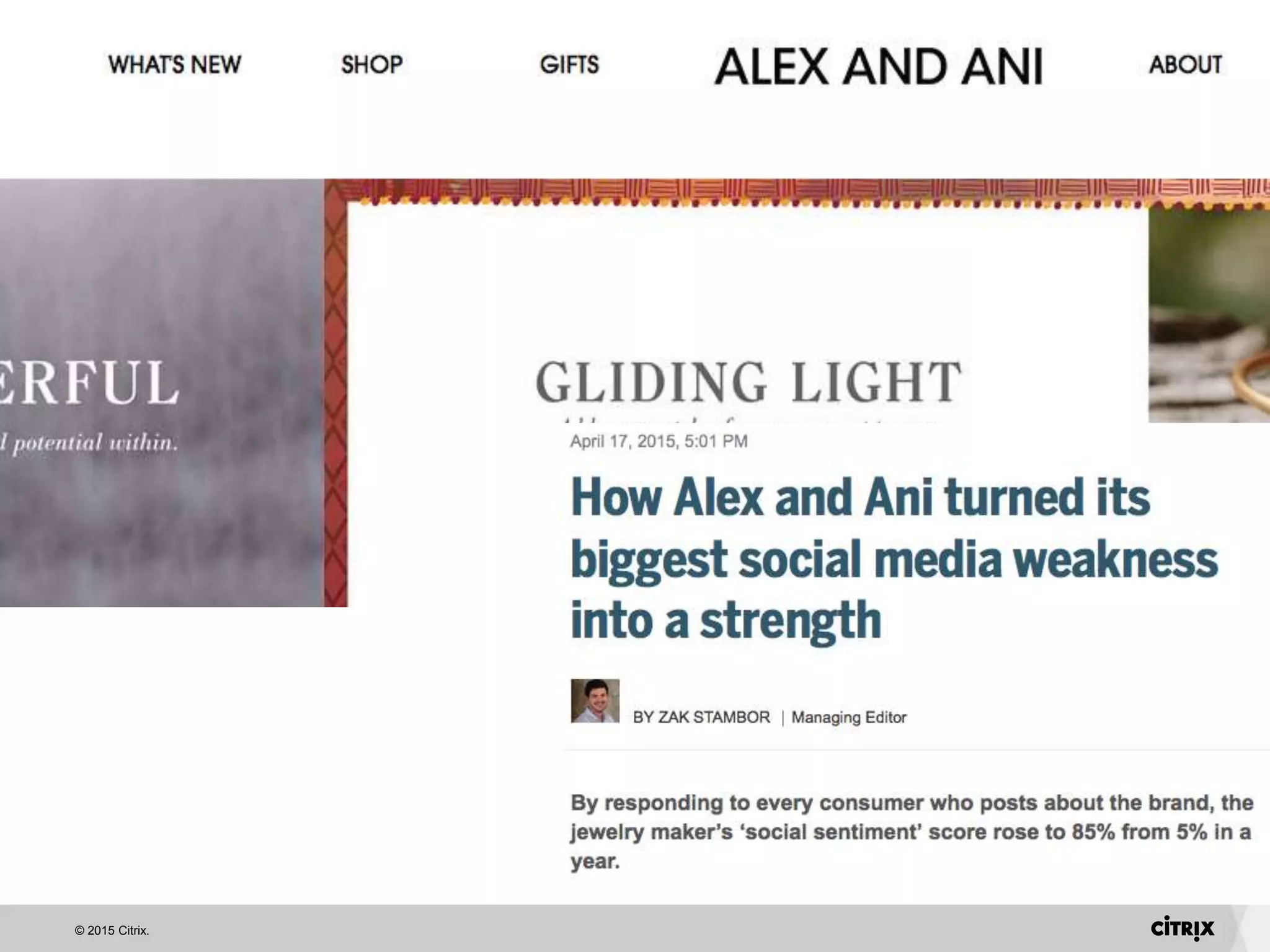
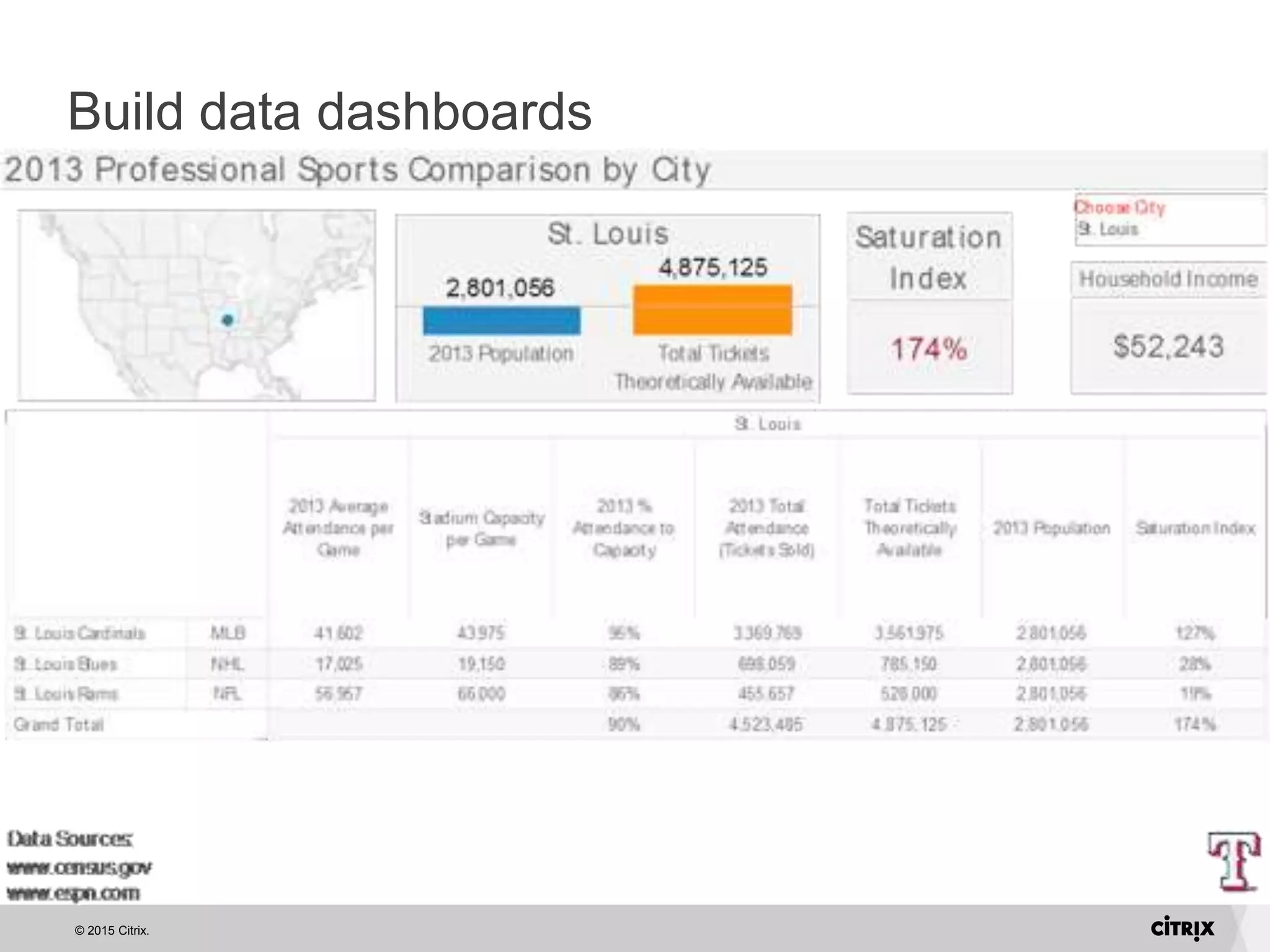
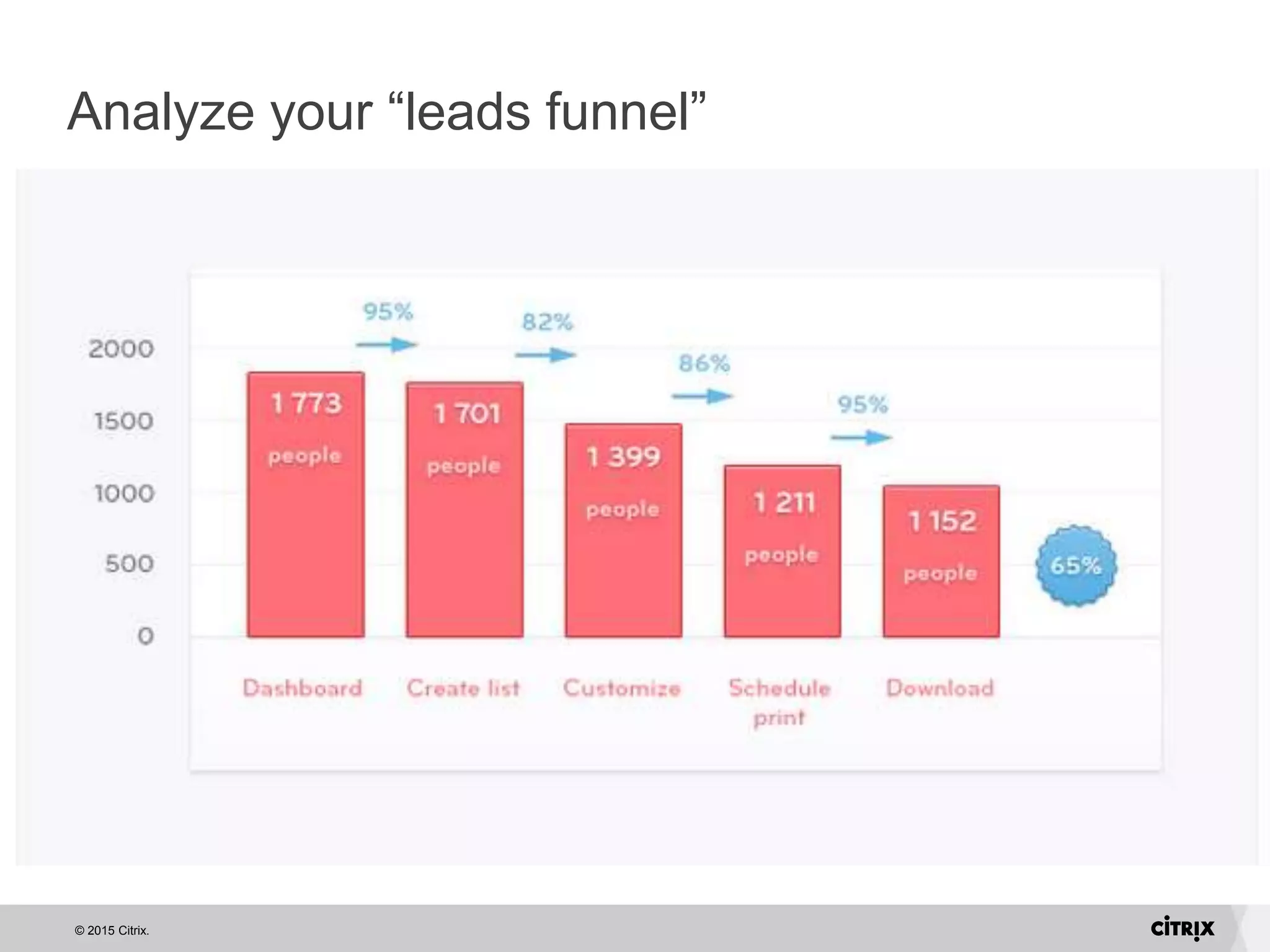
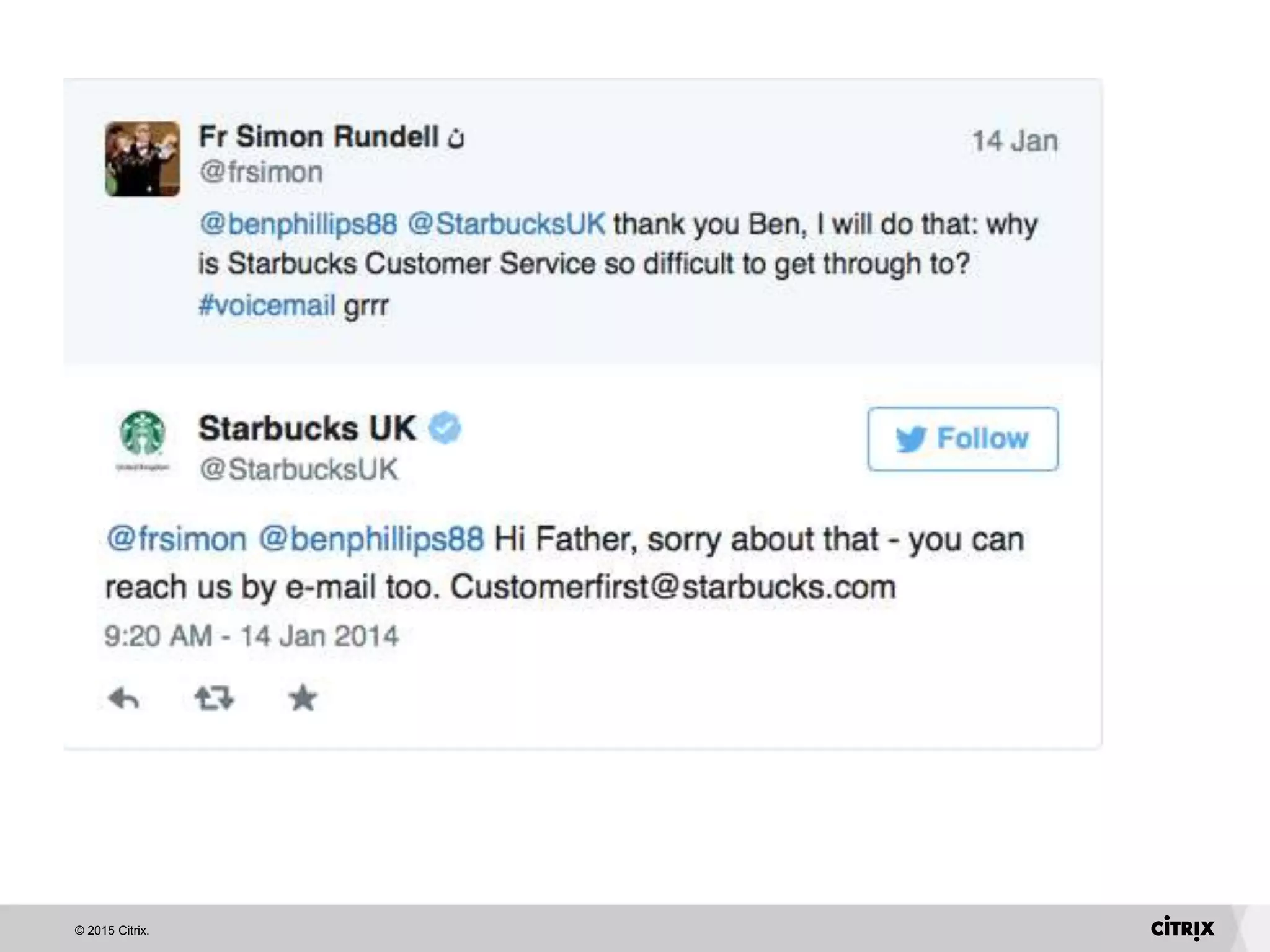
David Strom discusses essential lessons for IT from customer support experiences, emphasizing the importance of listening to customers and asking the right questions. He highlights the need for honesty in communication, proactive engagement, and careful recruitment of brand ambassadors. Additionally, he recommends using data dashboards to track customer sentiment and analyzing the leads funnel to improve retention.