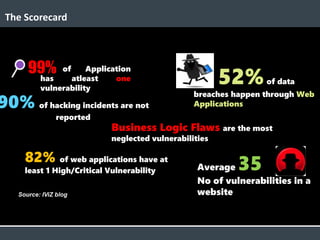
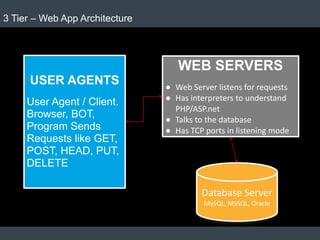
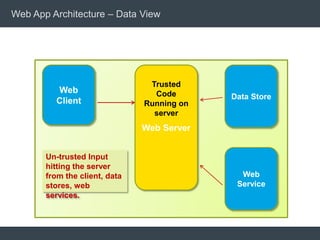
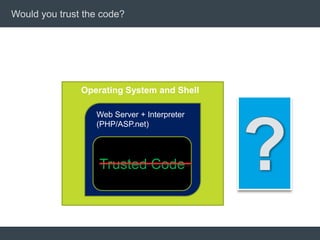
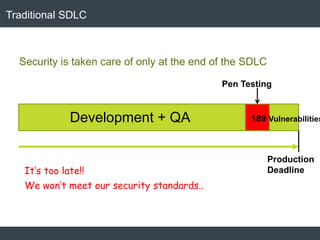
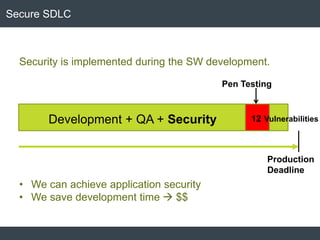
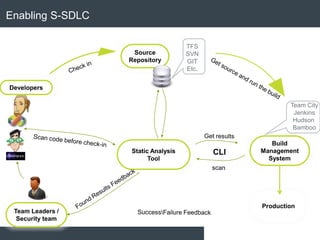
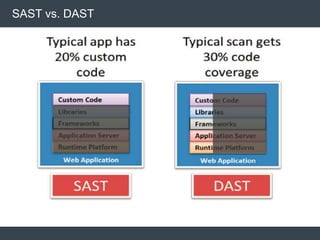
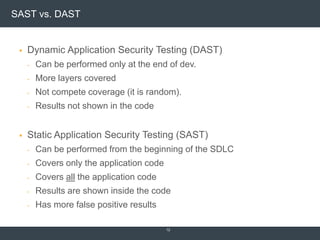
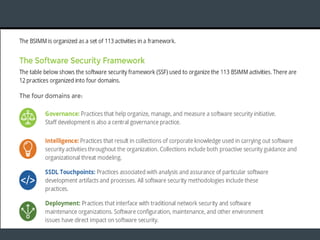
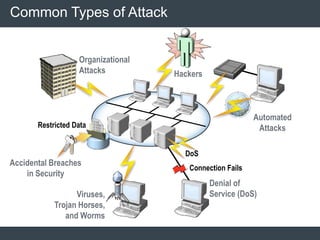
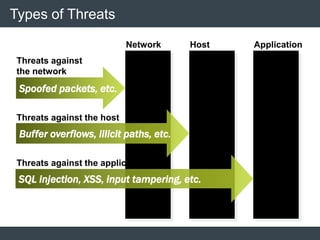
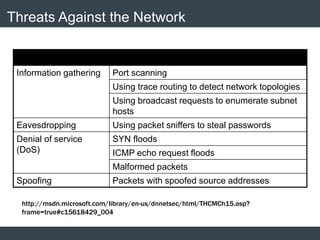
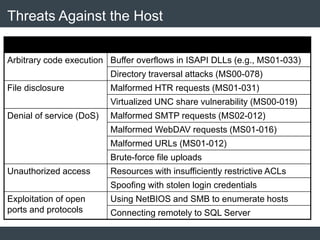
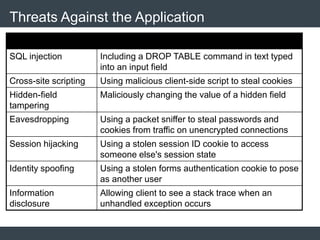
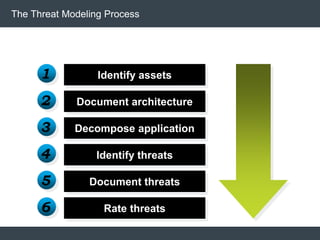
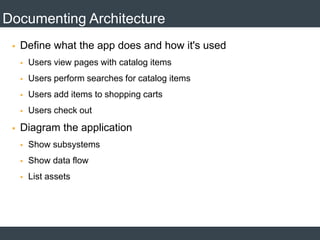
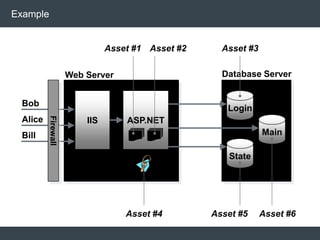
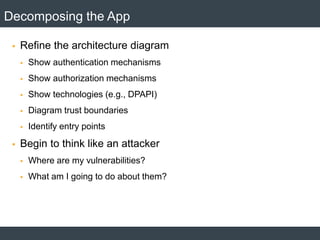
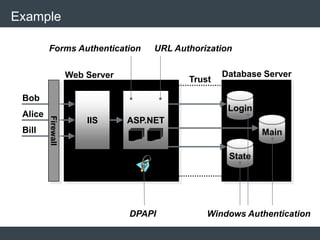
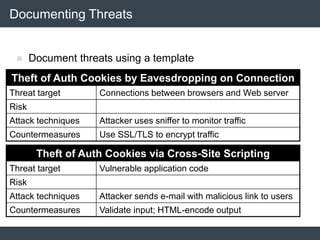
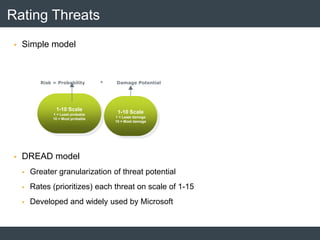
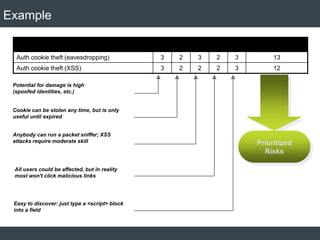
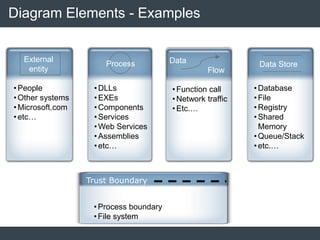
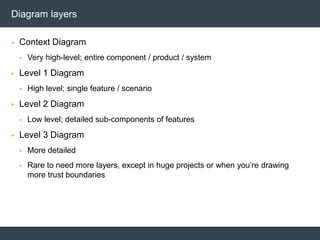
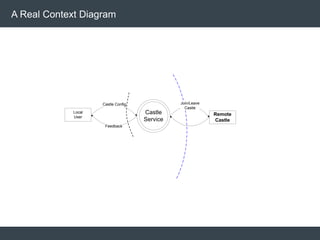
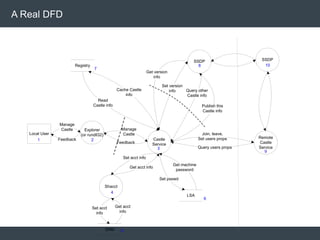
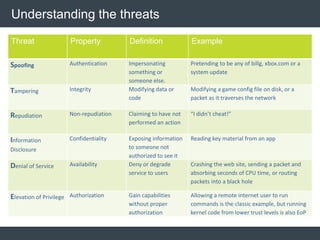
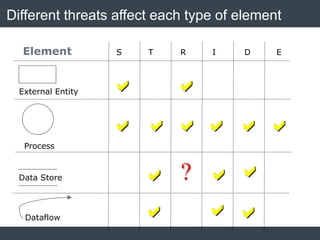
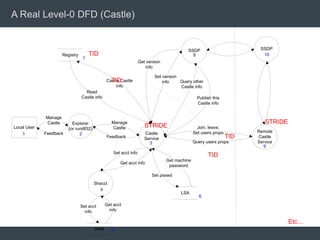
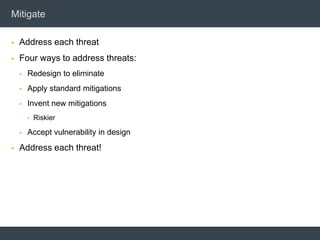
The document discusses security architecture and threat modeling, emphasizing that 95% of attacks target web servers and applications, with average vulnerabilities per website being 35. It highlights the importance of integrating security measures throughout the software development life cycle (SDLC) to significantly reduce vulnerabilities. The text also covers threat modeling methodologies, the types of attacks faced, and provides a structured approach to identifying and addressing security threats.