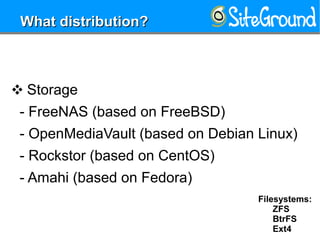
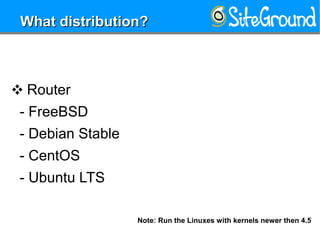
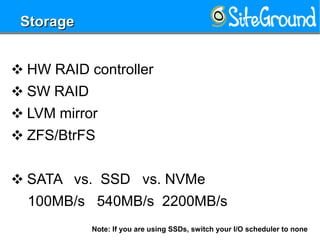
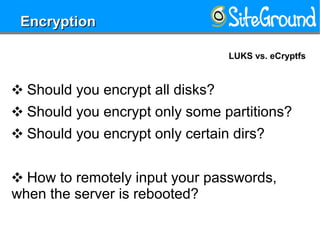
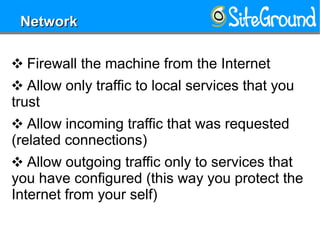
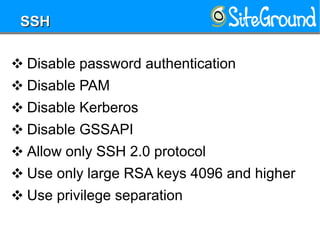
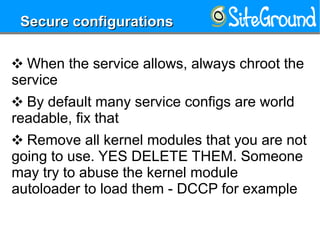
This document provides guidance on setting up a Linux server at home. It discusses reasons you may need a home server, such as for storage, routing, or hosting personal projects. It then offers recommendations for hardware, distributions, partitioning, encryption, disabling unnecessary services, software updates, logging, security practices, network configuration, SSH hardening, configuration security, user setup, and kernel settings. The goal is to have a secure home server for various uses.