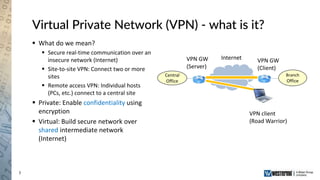
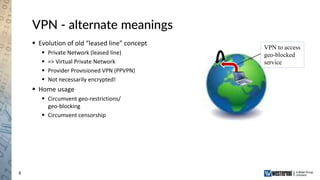
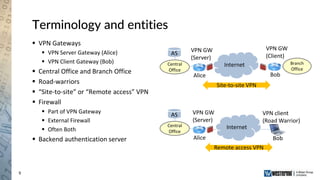
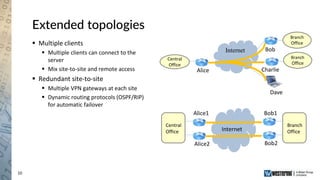
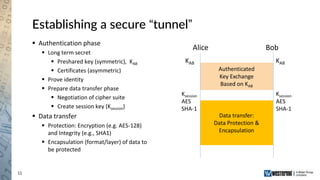
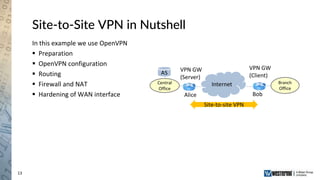
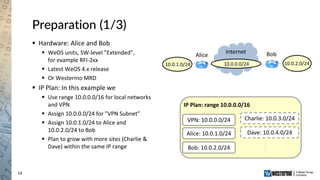
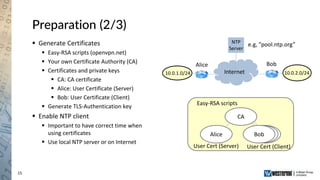
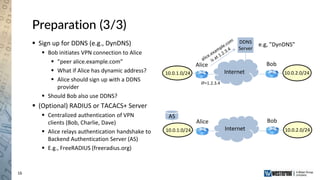
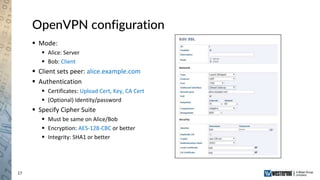
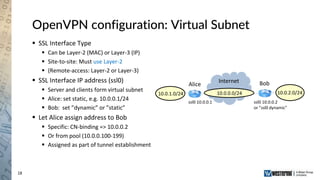
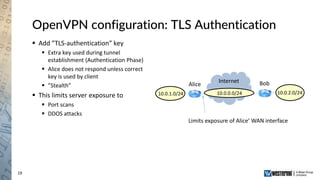
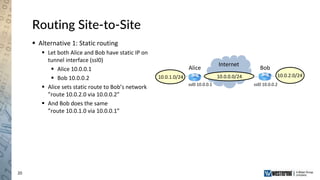
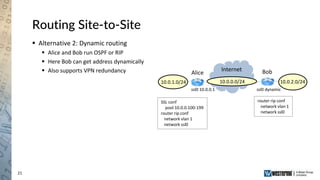
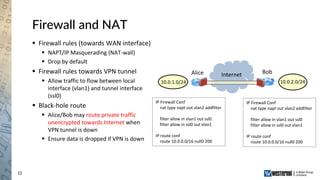
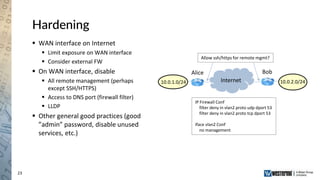
The document provides an overview of a Westermo webinar focused on network-to-network protection using VPNs, detailing concepts like VPN types, security protocols, and configuration processes. It outlines various methods for establishing secure connections between sites, including the preparation needed for setup and best practices for maintaining network security. The presentation also highlights upcoming webinars related to network segmentation and perimeter protection strategies.